
An Introduction to IoT Security: Why It Matters Today
In today’s technology-driven era, the Internet of Things (IoT) has become a pivotal part of our everyday lives. This innovative concept has transformed the way we interact with the world around us, integrating the internet into physical objects and creating a network of interconnected devices. From smart home appliances to sophisticated industrial machinery, IoT has paved the way for a more connected and efficient society. However, as we increasingly rely on these interconnected systems, the importance of IoT security becomes paramount. This post will be an introduction to IoT security, what it means, and how to approach it.
IoT security, the practice of safeguarding connected devices and the networks they inhabit, is crucial not only for the functionality and efficiency of these devices but also for the protection of personal and business-related information. As IoT devices permeate every aspect of our personal and professional lives, they bring forth unique security issues. The vulnerability of these IoT devices often can lead to significant risks, including the potential for personal data breaches, disruption of business operations, and even threats to physical safety.
This article delves into the crucial world of IoT security, highlighting the importance of protecting interconnected devices in our increasingly digital world. It discusses the diverse range of IoT devices and their unique security challenges, emphasizing the need for robust security measures to safeguard against cyber threats. Real-world examples, like the casino fish tank breach, illustrate the potential consequences of security lapses. The piece explores emerging trends, such as AI and blockchain in IoT security, and offers practical tips for creating a secure IoT environment. Emphasizing regular updates, strong authentication, and proactive measures, it calls for continuous vigilance and adaptation to secure our digital and physical spaces in the IoT era.
Understanding IoT Devices and Their Security Needs
IoT devices encompass a vast array of interconnected gadgets and systems that communicate via the internet. From wearable fitness trackers to complex industrial automation systems, these devices collect, transmit, and process data, making everyday tasks more efficient. However, this convenience comes with its own set of challenges.
The unique security challenges of IoT devices stem from their diverse nature and extensive connectivity. Many IoT devices are continuously connected to the internet, making them potential targets for cyberattacks. Moreover, these devices often lack standardization in security protocols, leaving them vulnerable. The limited processing power and storage capacity of some IoT devices further complicates the implementation of robust security measures.
Securing IoT devices is crucial because a single compromised device can pose a threat to the entire network it’s connected to. For individuals, this could mean a breach of personal and sensitive information. For businesses, the stakes are even higher, as a single vulnerability can lead to significant financial losses, operational disruptions, and damage to brand reputation.
The Vulnerability Landscape of IoT Systems
IoT systems are susceptible to a range of vulnerabilities, from weak passwords to unsecured network connections. These vulnerabilities can be exploited to gain unauthorized access, intercept data, or disrupt device functionality.
The Mirai Botnet Attack A real-life example of a significant IoT security breach is the Mirai botnet attack in 2016. This attack involved a malware strain that infected IoT devices like digital cameras and DVR players. The malware turned these devices into a botnet to launch a massive Distributed Denial of Service (DDoS) attack, which disrupted internet services across the United States by targeting major DNS provider Dyn.
Smart Home Device Hacks Another example involves the hacking of smart home devices. In several incidents, hackers have gained access to smart home systems, including security cameras and thermostats. In one instance, hackers communicated with residents through hacked devices, causing distress and violating personal privacy. These cases highlight the potential risks posed by unsecured IoT devices in homes.
These real-world examples emphasize the importance of prioritizing security in the design and use of IoT devices. By understanding and addressing these vulnerabilities, we can mitigate the risks and ensure a safer, more secure IoT ecosystem.

Key IoT Security Challenges and How to Address Them
The realm of IoT security is fraught with challenges that stem from the inherent characteristics of these devices and their networked nature. A primary challenge is the vast and diverse range of IoT devices, each with varying levels of security capabilities. This diversity makes it difficult to apply a one-size-fits-all security solution. Additionally, the interconnectedness of these devices means that compromising one device can potentially threaten the entire network.
A significant challenge in IoT security is ensuring the regular update and patching of devices. Many IoT devices are not routinely updated, leaving them vulnerable to known exploits. The integration of IoT devices in critical infrastructure and personal spaces also raises the stakes, as breaches can have severe implications.
To mitigate these challenges, a multi-layered security approach is essential. This should include the deployment of network security measures like firewalls and intrusion detection systems to monitor and protect network traffic. Regular software and firmware updates are crucial to address known vulnerabilities and ensure secure network access for every IoT device. Additionally, manufacturers and users must prioritize security in the design and deployment of IoT devices, considering security at every stage of the device’s lifecycle.
The flowchart below shows steps that will help to address IoT security challenges:
Implementing Robust Security in IoT Devices
In today’s digital age, the Internet of Things (IoT) has become an integral part of many businesses, offering unparalleled convenience and efficiency. However, with this convenience comes the responsibility of ensuring that these devices are secure. For small businesses, this is especially crucial as a single breach can have devastating consequences. By referring to our workflow diagram, let’s delve into the practical steps you can take to fortify your IoT infrastructure.
Best Practice Recommendations
To enhance the security of IoT devices, several best practices should be adopted:
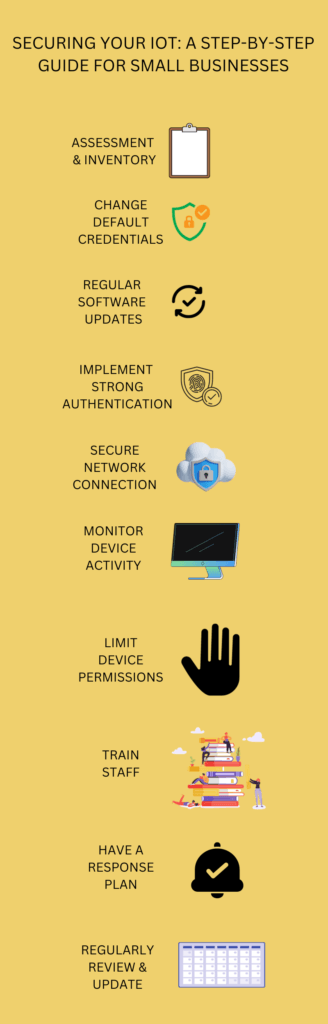
- Assessment and Inventory: Regularly take stock of all IoT devices in your business.
- Change Default Credentials: A fundamental step in IoT security is changing the default usernames and passwords that come with your devices. These credentials are often easily accessible online, making devices that still use them low-hanging fruit for cybercriminals.
- Regular Software Updates: Ensure that IoT devices receive timely updates to patch vulnerabilities and enhance security features.
- Implement Strong Authentication: Multi-factor authentication (MFA) is a method that requires users to provide two or more verification factors to gain access to a resource. Implementing MFA ensures that even if a password is compromised, the attacker still can’t access the device or network without the second verification factor.
- Secure Network Connections: Employ strong encryption methods for data transmission to prevent interception and ensure data integrity.
- Monitor Device Activity: Keeping an eye on your IoT devices’ activity can help you spot any unusual patterns, which could indicate a security breach or malfunction. Regular monitoring can help you catch potential threats before they escalate.
- Limit Device Permissions: Not every device needs to access every part of your network. By limiting permissions, you ensure that even if a device is compromised, the damage it can do is contained.
- User Awareness and Training: Alert users about the importance of security practices, such as changing default passwords and recognizing phishing attempts.
- Have a Response Plan: Despite your best efforts, breaches can still occur. Having a clear plan in place ensures that you can respond quickly and effectively, minimizing damage.
- Review and Update: Regular reviews of your security measures can ensure that you’re prepared for new threats and that your devices are as secure as possible.
By implementing these measures, businesses and individuals can significantly enhance the security of their IoT systems, protecting them from a wide range of cyber threats. Regular updates and security patches, in particular, are a fundamental aspect of this protective strategy, ensuring that IoT devices and systems remain resilient against evolving cyber threats.
The Impact of Security Breaches on IoT Systems
The consequences of security breaches in IoT systems can be far-reaching and multifaceted, affecting not only the digital realm but also having tangible impacts in the physical world. These breaches can range from personal data theft to severe disruptions in critical services and infrastructure.
One striking example of the real-world implications of an IoT security breach occurred in a casino. Hackers were able to access the casino’s high-roller database through an internet-connected thermometer in a fish tank. This seemingly innocuous device served as a gateway to the casino’s broader network, demonstrating how even the most unexpected IoT device can be a security risk.
Another notable instance is the disruption of critical services. In healthcare, for instance, IoT devices like patient monitors and medication dispensers are integral to patient care. A breach in these systems can lead to incorrect medication dispensation or loss of crucial patient data, potentially endangering lives.
These examples underscore the significant consequences that can arise from IoT security breaches. They highlight the necessity of robust security measures to protect not just data but also the physical well-being of individuals and the smooth operation of essential services.
Future of IoT Security: Trends and Predictions
As the Internet of Things continues to expand and evolve, so too does the landscape of IoT security. Understanding emerging trends and making informed predictions about future developments are essential for staying ahead of potential threats.
Emerging Trends in IoT Security:
- Increased Use of Artificial Intelligence and Machine Learning: AI and machine learning are becoming crucial in detecting and responding to security threats in real-time. Using machine learning and AI enable the analysis of vast amounts of data generated by IoT devices, helping to identify patterns indicative of a security breach.
- Blockchain for Enhanced Security: Blockchain technology is gaining traction in IoT security for its ability to provide decentralized and tamper-resistant record-keeping. This can be particularly effective in ensuring the integrity of device firmware and in secure, automated transactions between devices.
- Focus on Edge Computing Security: As IoT devices generate enormous amounts of data, there’s a shift towards processing this data at the edge of the network. Securing these edge computing environments is becoming a priority, as they often serve as the first line of defense against cyber attacks.
Predictions for the Evolution of IoT Security:
- Standardization of IoT Security Protocols: There is likely to be a move towards standardizing IoT security protocols to address the current fragmentation in the market. This could involve developing universal security standards applicable across various devices and industries.
- Enhanced Security for Consumer IoT Devices: Consumer awareness of IoT security risks is rising, driving demand for more secure products. This may lead to enhanced security features becoming a standard offering in consumer IoT devices, rather than a premium add-on.
Building a Secure IoT Environment
Creating a secure IoT environment is crucial for both individuals and businesses. Here are key strategies:
- Select Secure Devices: Choose IoT devices with strong security features and a history of regular updates.
- Control Access: Use robust passwords and implement access control policies to restrict who can interact with your IoT devices.
- Monitor and Audit: Regularly check your IoT devices and network traffic for unusual activities to promptly identify and address potential threats.
- Stay Informed: Keep up-to-date with the latest cybersecurity threats and trends to enhance your defenses proactively.
- Have a Response Plan: Prepare a clear plan for dealing with security breaches, including steps for containment and recovery.
In summary, prioritizing IoT security is essential in safeguarding our interconnected world. By adopting these proactive measures, we can create a more secure and reliable IoT environment.
Securing the Future: Key Takeaways in IoT Security and Beyond
In this exploration of IoT security, we’ve underscored its critical importance in our increasingly connected world. From individual smart devices to vast industrial systems, the need for robust security in the IoT sphere is paramount.
We’ve identified key challenges in IoT security, such as the diverse range of devices and their inherent vulnerabilities. Real-world breaches, like the casino fish tank incident, illustrate the consequences of security lapses. Addressing these vulnerabilities requires a multi-faceted approach, including regular updates, strong authentication, and encryption.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


Excellent post! Very insightful and well-written. Thanks for sharing this valuable information!
Yes IoT devices are almost by their nature, a weakness because they are built to be small and inexpensive and security is always a second thought. One must be aware of this and either get better devices or bury them behind firewalls.