Unlocking MDM for Small Business: What you need to know
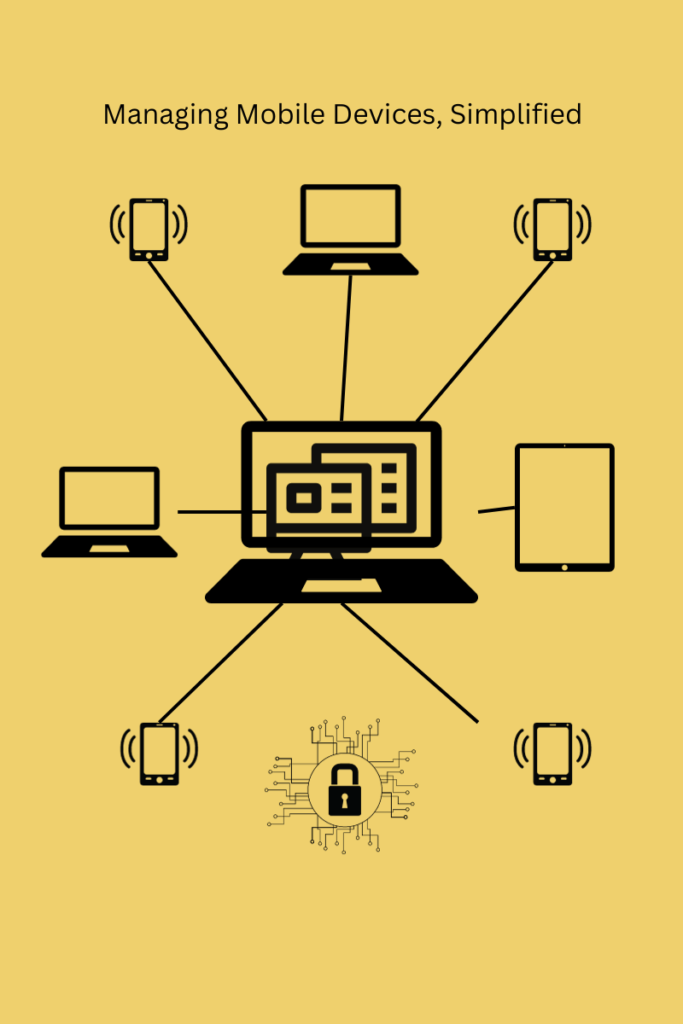
Introduction Navigating the maze of device management is a common challenge for small businesses. With a diverse range of devices—smartphones, tablets, laptops—each with its own set of applications and security settings, the task becomes increasingly complex. This is where Mobile Device Management (MDM) becomes a game-changer for small businesses. MDM streamlines the management of multiple […]
Unlocking MDM for Small Business: What you need to know Read More »