
Why End User Security Awareness Training is Essential
End User Cyber Security Awareness Training is no longer optional; it’s a must. This ongoing education equips your team with the skills for Cyber Threat Mitigation. The digital landscape is a breeding ground for evolving Cyber Attacks, making continuous Employee Cyber Education vital.
Key Takeaways
- Essential for Cyber Threat Mitigation: Continuous training equips teams to handle evolving threats.
- Builds Strong Security Culture: Training helps recognize and reduce human error, a major security risk.
- Dynamic and Up-to-date: Regular updates ensure the program remains relevant against new threats.
- Supports Organizational Policies: Adhering to frameworks like NIST standardizes and improves training effectiveness.
Establishing a Strong Security Culture: Why It Matters
Creating a strong Security Culture goes beyond installing firewalls. It involves Security Training Programs that teach employees to recognize Human Risk and act proactively. For instance, Human Error was the real culprit behind the Freeport LNG incident, highlighting the need for robust Organizational Security Policies.
Building a cybersecurity culture is fundamental for organizations to safeguard their assets. This initiative goes beyond merely having security systems in place. Besides that, it involves fostering a mindset among employees to be vigilant and proactive in identifying and mitigating security risks.
End user training is a pivotal aspect of this culture. The training equips individuals with the knowledge and skills necessary to recognize and respond to security threats.
Similarly, numerous major corporations have suffered data breaches due to human error. For instance, a data breach case involved human error allowing attackers to access encrypted channels. This demonstrates the extent to which human error can compromise even the most secure channels. This is what will happen if individuals are not adequately trained.
Crafting a Robust End User Cyber Security Training Program
Building a strong cybersecurity posture isn’t just about tech solutions. It’s about training employees in end user security best practices. A robust Security Awareness Training Program is essential for safeguarding your organization.
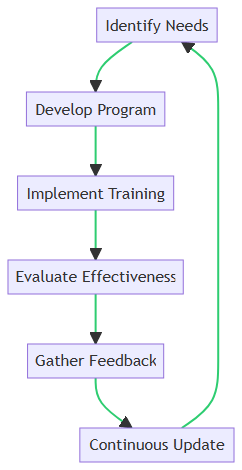
The above diagram provides a step-by-step guide to developing and maintaining an effective program, illustrated by the following process flow:
1. Identify Needs
Start by identifying the specific security needs of your organization. Conduct a thorough assessment to understand the unique challenges and vulnerabilities that your team faces. This initial step is crucial for tailoring the training program to address real-world threats.
2. Develop Program
Once the needs are identified, develop a comprehensive training program. This program should cover a wide range of topics, including phishing attacks, password management, data protection, and more. Be sure to tailor Cybersecurity Training Modules to your company’s needs. Ensure that the content is engaging and accessible to all employees, regardless of their technical expertise. Use real-world examples like Phishing Scams and Social Engineering to make the training impactful.
3. Implement Training
With the program in place, the next step is implementation. Use a mix of training methods such as online modules, interactive workshops, and hands-on exercises to cater to different learning styles. Consistent and periodic training sessions help reinforce the importance of cybersecurity practices.
4. Evaluate Effectiveness
After implementing the training, evaluate its effectiveness. This can be done through quizzes, simulations, and feedback surveys. Monitoring key metrics like incident reports and employee performance in simulated attacks provides valuable insights into the program’s impact.
5. Gather Feedback
Feedback from participants is vital for continuous improvement. Encourage employees to share their experiences and suggestions. This feedback helps identify gaps in the training and areas that need enhancement.
6. Continuous Update
Cyber threats are constantly evolving, so your training program should too. Regularly update the content to reflect the latest threats and best practices. Continuous improvement ensures that your team remains vigilant and well-prepared against emerging cyber risks.
By following this structured approach, you can create a dynamic and effective Security Awareness Training Program that adapts to the changing cyber environment and enhances your organization’s security posture.
Embracing the NIST Guidelines
The NIST Cybersecurity Framework offers a structured approach for Cybersecurity Risk Management. It helps you:
- Standardize: Cover all the basics of Information Security.
- Customize: Adapt the framework to safeguard Sensitive Information specific to your business.
- Measure Success: Use NIST to evaluate the effectiveness of your Employee Security Education.
Relevance of the NIST Guidelines
The relevance of NIST guidelines in structuring a solid training program is manifold:
- Standardization: The NIST guidelines provide a standard structure for cybersecurity training. Thus, ensuring that core principles are covered comprehensively, thereby enhancing the organization’s cybersecurity posture.
- Customization: The NIST framework is flexible despite being a standard. This framework allows organizations to tailor it according to their specific needs and risk profiles. Doing so facilitates a more effective and relevant training program.
- Benchmarking: Adhering to NIST guidelines allows for benchmarking and continuous improvement, as they provide metrics and benchmarks against which the effectiveness of the training program can be measured.
- Budget Optimization: The structured approach of NIST aids in budget management by delineating each phase of the program, thereby ensuring resources are aptly allocated and utilized efficiently, which is essential for maintaining a favorable cost-benefit ratio in training initiatives.
Benefits of the NIST Guidelines
Adherence to the NIST guidelines has proven beneficial for a variety of organizations across different sectors. For instance:
- Saudi Aramco, a critical infrastructure entity, and the Government of Bermuda are among the international bodies that have reaped the benefits of aligning with NIST guidelines, as documented in NIST’s Success Stories catalog.
- Moreover, academic institutions like the University of Kansas Medical Center and University of Pittsburgh, and IT and workforce training organizations like ISACA, have also utilized the NIST framework to bolster their cybersecurity measures, showcasing the broad applicability and effectiveness of the NIST guidelines.
The above examples underscore the instrumental role NIST guidelines play in fortifying the cybersecurity training landscape, making it a worthy investment for organizations aiming to enhance their security posture while being mindful of budget constraints.
Interactive Learning: The Future of End User Cyber Security Training
In a world where cyber threats keep changing, ongoing learning is key. Interactive learning is a game-changer here. It makes Cybersecurity Awareness Training more engaging and effective. Here’s how:
Create Fun and Engaging Modules
- Gamified Learning: Turn learning into a game with rewards and points. It makes Security Training Programs fun and competitive.
- Quizzes: These aren’t just tests; they help you understand how well you’ve grasped Employee Security Education concepts.
- Real-World Scenarios: Practice making quick decisions in a safe, online environment. It’s great for Cyber Threat Mitigation.
Promote Community Learning
- Forums and Groups: Share experiences and solve problems together. It boosts collective intelligence and Company Wide cybersecurity.
Interactive learning goes beyond memorization. It turns you into an active part of your own Cybersecurity Risk Management. Plus, the community aspect adds a layer of shared responsibility.
Technological Aids for Enhanced Learning
Tech plays a big role in modern Employee Cyber Education. Here are some tools that make training better:
- Learning Management Systems (LMS): Think of it as the control center for your Security Awareness Course. It tracks progress and makes sure the training aligns with your Organizational Security Policies.
- Virtual Labs: These are risk-free spaces where you can practice what you’ve learned. They’re perfect for understanding how to protect against Phishing Attacks and safeguard Sensitive Information.
By using these tech tools, you’re not just learning; you’re applying what you’ve learned in a practical way. This makes your Security Awareness Training Program more effective and engaging.
Comparison of the Different Learning Aids
This table delineates the distinctive features and capabilities of Learning Management Systems (LMS) and Virtual Labs, shedding light on their respective strengths in fostering a conducive learning environment. While LMS provides a structured, centralized platform for training delivery and progress tracking, Virtual Labs excel in offering real-world simulation and hands-on experience, which are crucial for practical skill development in cybersecurity training.
| Feature | Learning Management Systems (LMS) | Virtual Labs |
|---|---|---|
| Centralized Training Platform | Yes | No |
| Real-world Simulation | No | Yes |
| Progress Tracking | Yes | Depends on Integration |
| Interactive Learning | Yes (Through Modules) | Yes (Through Hands-on Exercises) |
| Customized Content Delivery | Yes | Yes |
| Analytics and Reporting | Yes | Depends on Integration |
| Scalability | Yes | Yes |
| Assessment Capabilities | Yes | Yes (Through Scenario Evaluations) |
| Collaborative Learning | Yes (Through Forums, etc.) | Yes (Through Shared Environments) |
Addressing the Human Firewall: From Awareness to Action
The “Human Firewall” concept highlights the role each person plays in Company Wide security. The goal is to turn Cybersecurity Awareness into actionable steps. Here’s how:
Phishing Simulations:
- Real Scenarios: Use real-life examples to train on Phishing Attacks. It improves the ability to spot and handle these threats.
- Instant Feedback: Learn from mistakes right away to improve future responses.
- Performance Metrics: Track improvements over time to measure the effectiveness of your Security Awareness Training Program.
Social Engineering Awareness:
- Workshops: Host sessions to educate on Social Engineering tactics and risks.
- Real-world Cases: Share actual incidents to make the threat real and encourage proactive measures.
- Interactive Modules: Use engaging content to teach how to recognize and prevent Social Engineering attacks.
Both Phishing Simulations and Social Engineering Awareness aim to empower individuals to act, not just be aware. Through ongoing education and hands-on exercises, you’re building a strong line of defense, enhancing your overall Cybersecurity Risk Management.
Staying Ahead: Continuous Update and Evaluation
Cybersecurity is ever-changing. Keeping your Training Employees updated isn’t optional; it’s a must. Here’s how:
Incorporate Security Continuous Updates Into Your Training
- Threat Intelligence: Keep the training current with the latest threats.
- Regulatory Updates: Make sure your training meets legal and industry standards.
- Expert Advice: Consult with cybersecurity experts to keep your training cutting-edge.
Have an Evaluation Process For Your Training
- Feedback: Collect input to understand what’s working and what needs improvement in your Security Awareness Course.
- Testing: Regular assessments measure how well the training is sticking.
- Metrics Analysis: Look at data like response times to Phishing Scams to gauge the training’s impact.
Build a Continuous Improvement Program for your Training
- Adaptive Learning: Use tailored paths to improve individual performance.
- Regular Reviews: Keep the training aligned with your Organizational Security Policies.
- Invest in Tools: Use advanced tools to make your training more effective against current Cyber Threats.
By keeping your training updated and continuously evaluating its effectiveness, you’re ensuring resilience against evolving Cyber Attacks. This proactive approach keeps your Human Firewall ready to counter ongoing threats.
Real-world Impact: Success Stories and Case Studies
The effectiveness of cybersecurity training in bolstering organizational security is well-illustrated through various real-world examples and case studies. Here are some instances where training has significantly contributed to thwarting cyber attacks:
- Hawthorn Community Primary School: This school utilized an autonomous cybersecurity training platform. This led to an increase in phishing detection rates among employees from 15% to 95% within a year.
- Saudi Aramco: Saudi Aramco adopted NIST’s Cybersecurity Framework. They demonstrated how a structured approach to cybersecurity can significantly enhance organizational security.
These examples underscore the substantial improvement in cybersecurity posture that organizations can achieve through effective training programs. It’s clear from these success stories that a well-structured and continuous training regimen can equip employees with the necessary skills to identify and thwart cyber threats. Thus, substantially lowering the risk of successful cyber-attacks.
Where to go from here
The landscape of cyber threats is always changing, targeting any weak spots. The key to a strong defense is a well-trained team. Through End User Cyber Security Training, your team becomes a human firewall, ready to fend off various cyber attacks.
This training starts with content tailored to your specific needs, promotes ongoing learning, and includes hands-on practice. Following NIST guidelines ensures a standardized approach to Cybersecurity Awareness.
Tech tools like Learning Management Systems and Virtual Labs make the training engaging and effective. Interactive modules and community discussions turn awareness into action.
Keeping the training updated is crucial to stay ahead of new threats. This investment not only builds a proactive security culture but also lowers the risk of incidents, protecting your valuable assets.
As cyber threats evolve, the need for strong training grows. The payoff is clear: a team that’s ready to tackle any cyber challenge. So, why wait? Dive into End User Cyber Security Training now and strengthen your human firewall.
Got questions? Feel free to ask in the comments below.
Questions? We Have Answers.
Get answers to a list of the most Frequently Asked Questions.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
