In an era where digital real estate is as valuable as its physical counterpart, safeguarding your online presence is paramount. For small businesses and IT personnel, understanding how to prevent DDoS attacks on websites is not just a technical challenge—it’s a critical business strategy. DDoS attacks, or Distributed Denial of Service, can overwhelm your site’s infrastructure, leading to significant downtime and loss of trust. As these incidents become more sophisticated, the methods to counteract them must evolve. This post delves into practical steps and best practices to help you fortify your website against this pervasive cyber threat.
This post delves into the evolving landscape of DDoS threats, with a focus on application-layer attacks that cleverly mimic legitimate traffic, making them harder to detect and mitigate. We will uncover the anatomy of these attacks, explore real-world scenarios, and present actionable strategies – including cutting-edge tools like Verified Visitors – to safeguard your online presence. By understanding and preparing for these cyber storms, you can fortify your defenses and ensure that your digital doors remain open, come what may.
Understanding the Threat of Application Layer Attacks
The threat at hand comes from what is known as Application Layer Attacks, a common vector for a DDoS attack. These attacks are especially insidious as they specifically target the layer of a network where webpages are generated and displayed, crippling the capacity to provide services. Hence, to prevent DDOS attacks on websites, one needs to be cognizant of the various attack vectors and implement best practices for safeguarding their online presence.
A noticeable feature of Application Layer Attacks is their stealthy nature that makes them harder to detect until it’s too late. It means conventional firewalls and intrusion detection systems often fail to offer adequate protection. Therefore, embracing advanced DDoS protection mechanisms is paramount to protect your website. It’s crucial to understand how DDoS attacks work and plan accordingly to counter the emerging threats in the cyberspace realm. In conjunction with this, adopting best practices can offer an additional layer of defense and ensure continued service amidst a potential DDOS onslaught.
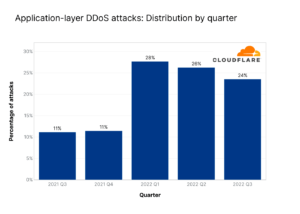
The graph below illustrates the distribution of application-layer DDoS attacks over the past year (source: Cloudflare DDoS threat report 2022 Q3). Notice the significant spike in Q2 2022, indicating a troubling trend that underscores the need for robust security measures. Businesses must remain vigilant, as these attacks represent a growing portion of cyber threats that can disrupt operations and compromise sensitive data.
Preparing for Emerging DDOS Attack Trends
In the rapidly evolving digital landscape, the imperative to stop DDoS attacks has taken precedence. Understanding the specifics of a type of DDoS attack and how a DDoS attack works is paramount for developing a competent defense strategy. Encapsulating this can drastically upsurge the capability to protect against DDoS attacks effectively. With the constant emergence of newer, more complex DDOS attack trends, fortifying your website against DDoS attacks adopts an even more critical role.
Further study reveals how applying a comprehensive DDoS protection system can help prevent DDoS attacks. The right application of security tools such as a smart firewall enhances the security fabric and holds a vital role in mitigating distributed denial of service threats effectively. These tools are designed to not only protect your website against DDoS but also keep it up and running smoothly. It’s time that prevention takes center stage and help stop the wave of mighty attacks, providing robust protection to make your online venture resilient and secure.
Learning from Real-World DDoS Attack Scenarios
In the milieu of cybersecurity, it becomes elemental to prevent DDoS attacks on websites. Through an analysis of the circumstances and outcomes of real-world DDoS attack scenarios, significant insights can be gleaned. These scenarios can guide businesses to adopt best practices, formulate an effective DDoS response, and set up robust mechanisms to protect their website.
Interpreting the common type of DDoS attack scenarios reveals crucial patterns to understand the impact of a DDoS attack. Hence, it is important to promptly deploy DDoS protection techniques when a site is under attack. The goal should be to stop a DDoS attack efficiently and ultimately prevent future incidents. Understanding the fundamental DDoS attack classification and exploring ways to prevent them will not only stop the attack but also minimize the damage inflicted by such breaches. It is through such experiential learning that businesses can fortify their security measures, keeping their digital landscapes safe from threats.
Dissecting Successful DDoS Attacks: Key Learnings
Understanding the underpinnings of a successful DDoS attack provides valuable information. Particularly, the key learnings derived can help prevent DDoS attacks on websites. One type of DDoS attack plaguing businesses is volumetric attacks. The primary goal of this type of attack is to overwhelm the bandwidth of the server, leading to a distributed denial of service.
An effective DDoS protection strategy includes the integration of a robust firewall within the network architecture. Simultaneously, a router is crucial as it acts as the first line of defense. A router configures the distribution of network traffic, mitigating the impact of a DDoS attack. Additionally, a Web Application Firewall provides specialized DDoS mitigation. This firewall inspects incoming traffic to filter out malicious data packets. Comprehending these methods ultimately bolsters efforts to mitigate DDoS attacks.
Case Studies: How Businesses Mitigated DDoS Attacks
In the face of DDOS attacks, organizations continually utilize best practices to protect their website. One such practice involves understanding traffic patterns and identifying abnormal increases in data flow. This aids in discerning real visitor traffic from malicious attacks.
Several companies have successfully thwarted DDoS attacks through the use of cloud-based DDoS protection services, illustrating the value of such systems. These layer attacks often target the website’s content delivery network to overload the web server, and, ultimately, crash the target server. However, recognizing how a successful DDoS attack works can enable businesses to devise strategies aimed at stopping these attacks. Engaging the preventive measures and constants monitoring could enhance the capability of the system to mitigate the effect of and prevent DDoS attacks on websites.
Case Study: Mitigating MySQL DDoS Attacks Using Verified Visitors
In a recent incident, MySQL servers faced a distributed denial-of-service (DDoS) attack. Traditional solutions like patching vulnerabilities are effective but not always feasible. An innovative approach involves using Verified Visitors, a cloud-based tool that enhances security in two significant ways.
Firstly, it thwarts credential stuffing, a common precursor to such attacks, by verifying each visitor’s authenticity. This process helps in identifying and blocking malicious bots that try to gain unauthorized access through stolen credentials. Secondly, Verified Visitors effectively prevents Layer 7 attacks, the type often used in DDoS scenarios. By scrutinizing traffic and discerning between legitimate users and botnet traffic, Verified Visitors maintains website accessibility even during an onslaught.
This case highlights the importance of proactive, multi-layered security measures in protecting against sophisticated cyber threats.
Lessons from Failed DDOS Attack Attempts
A crucial aspect of strengthening security measures to protect against DDoS attacks is learning from thwarted attempts. By studying the missteps in violation scenarios, enterprises can glean valuable insights, shaping defense strategies to prevent future attacks. A disseminated denial of service (dos) attack, for instance, if poorly executed or countered effectively, can provide a blueprint to safeguard a website against DDoS attacks.
Analyzing the digital footprints left in the wake of botched attacks can indicate a DDoS attack. From an influx of network traffic to the sudden drainage of server resources, these early warning signs can empower firms to formulate an effective DDoS response before the threat escalates. Furthermore, deciphering the patterns behind failed application layer attacks or protocol attacks can prove instrumental in devising protocols to block DDOS attacks. Adequate preparation can mitigate attacks, thereby helping prevent the ability of intruders to launch a DDOS attack, and protect precious server assets.
Conclusion: Developing a Comprehensive DDoS Prevention Strategy
Developing a comprehensive strategy to prevent DDoS attacks on websites requires a keen understanding of the different types of threats your network faces. The impact of a DDOS attack can be overwhelming, given the common types of DDoS attack include volumetric attacks and application-layer attacks. Both kinds require unique mitigation plans and security measures. Understanding their specific nature can greatly aid in formulating a response mechanism, thus showcasing the importance of staying updated about the different kinds of attacks.
To effectively combat these threats and stop a DDoS attack, businesses need to employ a multi-faceted approach. This often involves deploying DDoS protection both within and outside your network. A cloud-based DDoS protection service is an effective way to mitigate volumetric DDoS attacks and other attacks like application-layer attacks, which are becoming increasingly prevalent due to DDoS attackers’ evolving tactics. Furthermore, constant updates in security policies can help prevent DDOS attacks by addressing vulnerabilities, effectively narrowing down the avenues through which DDOS attacks may occur. Despite these challenges, taking steps to prevent DDoS attacks is essential for maintaining a secure online presence.
Adopting a Proactive Approach to DDOS Attack Prevention
Being forewarned is forearmed, especially when it comes to DDoS attacks. Recognizing the signs of a DDoS attack early is key to preventing serious damage. This involves closely monitoring website or application traffic to identify unusual patterns that may indicate an attack. A proactive approach also entails understanding the different types of attacks that you may face and knowing how to respond swiftly.
To protect your website against DDoS attacks, consider investing in DDoS protection services and automatic DDoS mitigation tools. These security measures are designed to detect and block attacks, providing reliable protection against threat actors who may launch a DDoS attack at any time. For optimal results, consider engaging DDoS mitigation services that offer tailor-made solutions to safeguard against the attacks that use diverse tactics. Remember, prevention is not a one-time operation – it requires continuously exploring and adopting effective ways to prevent future DDoS breaches. With the right prevention strategy and tools in place, you can strengthen your website’s resilience and thwart potential attack targets.
Creating a Customized DDoS Prevention Plan: Essential Considerations
The race to Prevent DDoS attacks on websites hinges on a customized game plan leveraging robust tools to protect. Critical as it may seem, the extent of protection against DDoS attacks depends on understanding the intricacies of various types of ddos attacks. Simultaneously, organizations must anticipate various types of attacks, emphasizing any area left vulnerable to ddos. Proactive measures should not limit to simple ddos attacks but span across complex, multi-vector network layer attacks like SYN floods and UDP floods.
Adopting a layered approach strengthens resilience against ddos attacks, heightening the barrier to launch a successful DDoS attack. Crucial to this methodology is gauging the potential impact of the attack and formulating effective threat mitigation strategies. At its core, a comprehensive coping mechanism involves studying how attacks are executed, particularly in the realm of denial of service attacks. Being fundamental ddos in nature, these attacks provide insightful cues on the strategic steps a firm can take to protect its website from a ddos attack.
Continually Updating and Enhancing DDoS Protection Efforts.
The primary goal of a DDoS attack is to overwhelm a server or network, rendering it unavailable to users. The tactics behind a DDoS may include flood attacks and pingback attacks, highlighting the importance of identifying the source of the attack for effective DDoS protection and response. This essential process enables an organization to stop the attack and restore services promptly.
In the face of this constant threat, the provision of DDoS protection techniques and immediate responses should never be a static process. Understanding DDoS attack classification and predicting potential DDoS situations are integral to combating these cyber threats. The truth is, once your site is under attack, you’re already playing catch up. Therefore, organizations must focus on continually updating and enhancing their protocols to prevent DDoS attacks on websites. The dynamic nature of cybersecurity threats calls for a fluid and responsive approach, always evolving to anticipate and mitigate risk effectively.
What is an Application Layer Attack?
An Application Layer Attack is a form of Distributed Denial of Service (DDoS) attack that targets the application layer of a network. It’s designed to overwhelm specific functions or features of a website, disrupting its normal functioning.
What are some emerging trends in DDoS attacks?
Emerging trends in DDOS attacks include increasing attacks on IoT devices, the use of new vectors such as memcached reflection, amplification attacks, and an increase in multi-vector attacks. It is also noted that the scale and frequency of attacks are growing.
Can you share some real-world examples of DDoS attack scenarios?
Due to privacy concerns, we can’t share specific details. However, scenarios can range from attacks targeting high-profile events, such as launches or holidays, to attacks aimed at causing long-term disruption for businesses.
What are some key learnings from successful DDoS attacks?
Successful DDOS attacks often highlight the need for improved security measures, the importance of regular system updates, and the value of implementing a comprehensive response plan. They also stress the need for continuous monitoring and stress-testing of networks.
How have businesses successfully mitigated DDoS attacks?
Successful mitigation strategies often include a combination of proactive measures such as traffic filtering, rate limiting, and up-to-date security systems, along with a robust response plan that includes swift identification and isolation of the attack.
What are the lessons we can learn from failed DDoS attack attempts?
Failed DDoS attacks often highlight the effectiveness of robust security measures, the importance of regular system updates, and the value of a well-practiced response plan.
How can a business develop a comprehensive DDoS prevention strategy?
A comprehensive DDoS prevention strategy involves proactive measures like investing in robust security solutions, continuous monitoring, regular system updates, and employee training. It also includes a response plan that outlines steps to quickly identify and address an attack.
What does a proactive approach to DDoS attack prevention entail?
A proactive DDoS prevention approach involves regular system updates, continuous network monitoring, regular stress-testing of networks, employee training, and the creation and implementation of a comprehensive DDoS response plan.
What are some essential considerations while creating a customized DDoS prevention plan?
Essential considerations include understanding your network’s weak points, investing in robust security solutions, allocating resources for continuous monitoring and system updates, and ensuring your team is trained to respond quickly and effectively in the event of an attack.
How can a business continually update and enhance its DDoS protection efforts?
Businesses can enhance their DDoS protection efforts by staying abreast of emerging attack trends, regularly testing and updating their security measures, investing in new security technologies, and regularly training their teams on the latest best practices in DDoS prevention.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!