Data breaches can cripple businesses and tarnish reputations overnight. Understanding the relationship between advanced persistent threats (APTs) to social engineering is crucial.
These cyber threats are not the work of chance actors. They are the calculated moves of adversaries. These adversaries aim to stay hidden within your network. They are silently exfiltrating sensitive data over time. Social engineering adds a layer of complexity. It exploits human vulnerabilities to bypass even the most sophisticated technical defenses.
For small business managers and IT personnel, the stakes are high. This is particularly true of those with limited cybersecurity knowledge. APTs can lead to significant financial losses, legal repercussions, and damage to customer trust.
Try to grasp the depth of these threats. Then you can develop a proactive stance and fortify your organization’s defenses. You can educate your team to recognize and respond to potential breaches effectively.
In the coming sections, we’ll dissect the anatomy of APTs. Then we will unveil the tactics of social engineering. Then we provide actionable insights to turn knowledge into a powerful defense mechanism.
Key Takeaways
- APTs and social engineering pose significant risks to businesses of all sizes
- A multi-layered defense strategy is needed. This strategy combines technical measures with employee education. This is crucial for protecting against these sophisticated cyber threats.
To defend against APT attacks that utilize social engineering:
- Prioritize cybersecurity education for all team members. Be sure to emphasize phishing and other deceptive tactics.
- Implement stringent security policies
- enforce multi-factor authentication
- maintain regular software updates to close potential vulnerabilities
- Utilize advanced endpoint security solutions with real-time threat detection and response capabilities.
- Establish strict access controls and network segmentation to limit the spread of any breach.
Additionally, develop a robust incident response plan to quickly address any intrusions. Foster a culture of security awareness and deploying layered technical defenses. Then, organizations can significantly strengthen their resilience against these sophisticated threats.
The Insidious Nature of Advanced Persistent Threats
Advanced Persistent Threats (APTs) are a cybercriminal’s masterstroke, embodying stealth and resilience. These threats are long-term operations. They are often state-sponsored or launched by high-level organized crime groups. They are created with the intent to steal, manipulate, or destroy data over extended periods. Unlike other cyber threats that seek quick payoffs, APTs are characterized by their persistence. They have the goal to maintain ongoing access to the victim’s network without being detected.
APTs are insidious. This lies in their ability to use a combination of techniques. These techniques include malware, zero-day vulnerabilities, and other sophisticated techniques. This allows them to gain entry and establish a foothold in a network.
Once inside, they try to move laterally. As they move, they try to escalate privileges. By doing so, they expand their control over critical systems and data.
This slow and methodical approach is what sets APTs apart. It’s what makes them particularly dangerous.
Understanding the signature strategies of APTs is essential for small businesses. It’s about having the right tools. But it’s also about recognizing the signs of an infiltration, understanding the tactics used, and knowing how to respond. This knowledge is a powerful tool in the cybersecurity arsenal. Knowledge that can be used to make the difference between a minor incident and a catastrophic breach.
The Human Element: Social Engineering in APTs
APTs are a technological menace. However, their most unpredictable aspect is the human element—social engineering. This psychological manipulation leverages human error. APTs use this to gain access to confidential information and secure systems.
The flowchart we’ve created delineates the critical role social engineering plays at each stage of an APT attack.
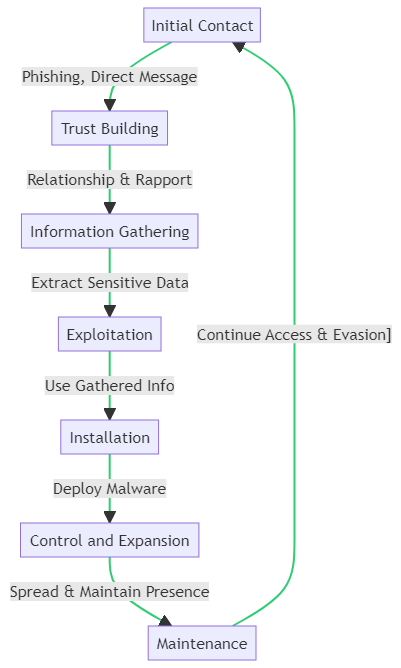
Initial Contact
The first step is often a seemingly innocuous communication, like a phishing email. It is designed to pique the recipient’s curiosity or invoke urgency. Here, the attacker’s goal is to establish a point of entry without raising alarms.
Trust Building
Once contact is made, the attacker cultivates a relationship to build trust. They may impersonate a colleague or a figure of authority. This will lower the target’s defenses and gather more information.
Information Gathering
With trust established, the attacker exploits the relationship to extract sensitive information. This could be:
- login credentials
- access protocols
- insider knowledge about the network’s security setup.
Exploitation
Armed with information, the attacker exploits the gathered intelligence to breach the system. This could involve using stolen credentials to access restricted areas. It could also involve convincing the target to bypass security protocols.
Installation
After gaining entry, the attacker discreetly installs malicious software to create backdoors. Thus, allowing for persistent access and control over the network, often going undetected.
Control and Expansion
With the malware installed, the attacker can control the system. After that, it can expand its reach within the network. Finally, the attacker can execute their agenda. This agenda could be data theft, espionage, or sabotage.
Maintenance
The final step in the social engineering process is maintaining control. The attacker continues to manipulate the human targets as needed. It does this to retain access and avoid detection. Thus, ensuring the longevity of the APT.
Understanding each of these steps. By doing so, one can better anticipate and recognize the signs of social engineering within their organizations. This knowledge is crucial for preemptive training.
It also helps in the development of security protocols. These protocols are designed to counteract these human-centric attacks.
Prime Targets: Who is at Risk?
When it comes to APTs, the prime targets are often perceived as high-value entities. These can be government agencies and large multinational corporations. These institutions are treasure troves of sensitive data, intellectual property, and state secrets. This makes them attractive targets for APT campaigns. The attackers behind APTs invest considerable resources and time. Their goal is to breach these fortified entities. The APTs motives are rooted in espionage or large-scale financial gain.
However, this focus on high-profile targets obscures a critical and often overlooked risk. The risk to small businesses. Small and medium-sized enterprises (SMEs) may not consider themselves as potential targets.
However, their defenses are usually less robust, making them low-hanging fruit for attackers. SMEs can be a stepping stone to larger networks. They can provide access to larger supply chains. Worse, they hold valuable data that is easier to access than that of larger organizations.
So there is a misconception that small businesses are not at risk. This can lead to inadequate security measures. Thus, making them particularly vulnerable to social engineering tactics.
These businesses may lack the cybersecurity infrastructure. They also lack the personnel training necessary to identify and respond to sophisticated APTs. As a result, they can suffer disproportionate damage from an attack. This in turn can be devastating to their operations and reputation.
Recognize the risk and understand that no organization is too small to be targeted. These are the first steps in fortifying defenses against APTs.
This means small businesses need to invest in cybersecurity. This includes education and implementing robust security protocols. Further, understand the importance of endpoint security. This serves protect against both APTs and the social engineering tactics that often accompany them.
The Anatomy of an APT Attack: Understanding the Cyber Kill Chain Model
The concept of a “kill chain” is a military term adapted for cybersecurity to describe the stages of an APT attack. This model helps us understand the systematic approach attackers use to infiltrate and exploit a network. Let’s break down the typical anatomy of an APT attack using the kill chain framework.
Reconnaissance: The first link in the chain is reconnaissance. Reconnaissance is where attackers identify targets and gather intelligence on vulnerabilities. Regardless of whether the vulnerabilities whether technical or human. This phase often involves meticulous planning and may last for weeks or months.
Weaponization: Next, attackers create the tools needed for the breach. Tools such as malware or exploit kits, tailored to the vulnerabilities they’ve discovered.
Delivery: The weaponized tools are then delivered to the target. This could be through email attachments, compromised websites, or direct network breaches.
Exploitation: Once the malicious payload is delivered, it exploits the identified vulnerabilities. This allows them to gain entry into the network.
Installation: After a successful exploitation, attackers install additional tools or backdoors. This allows them to maintain control over the network and ensure persistent access.
Command and Control (C2): Now the malware is installed. Once that happens, the network communicates back to the attacker’s command and control servers. This allows the attackers to steer the attack and move to the next phase.
Actions on Objectives: This is the final stage where attackers achieve their primary goal. Whether it’s data exfiltration, asset destruction, or establishing long-term espionage.
For small businesses, understanding each stage of the kill chain is vital. It provides multiple opportunities to detect and disrupt the attack before it reaches its objectives.
Implement layered defenses and educate employees on the signs of each stage. This is especially important in the early stages. This is where social engineering plays a key role. In these early stages, businesses can significantly reduce their risk of falling victim to an APT.
Social Engineering Tactics in APTs: The Art of Deception
Social engineering remains one of the most effective tactics in the arsenal of APTs. They exploit the one vulnerability that cannot be patched. They exploit human nature.
These tactics are insidiously designed to trick individuals. They trick them into granting access or divulging sensitive information. Information that can compromise an entire organization.
Some of the most common social engineering tactics used in conjunction with APTs are:
Spear Phishing: Unlike broad phishing attempts, spear phishing is highly targeted. Attackers craft convincing messages. These messages often use personal information. They can lure individuals into clicking on malicious links or attachments.
Baiting: Similar to phishing, baiting involves offering something enticing to the target. For example, a free download or a request for help. Once the bait is taken, malware is deployed.
Pretexting: Here, attackers fabricate scenarios to obtain privileged data. They might impersonate co-workers, police, bank officials, or other persons. These are persons with right-to-know authority. This creates a compelling story for why they need access to sensitive information.
Quid Pro Quo: Attackers promise a benefit in exchange for information. This could be as simple as offering technical support in exchange for login credentials.
Tailgating: An attacker may seek physical access to a location. They do this by following an authorized person into a restricted area. They do this under the pretext of being a fellow employee or a maintenance worker.
Diversion Theft: Cybercriminals may divert a courier or transport company. They convince them to reroute deliveries to a different address. Thus, gaining physical access to hardware or information.
Incorporating defenses against these tactics is crucial. This is especially for small businesses that may not have extensive security training programs.
Defenses can be used like regular training sessions, simulated attacks, and a culture of security. These defenses can help inoculate an organization against the manipulative strategies employed by APT actors.
It’s about creating an environment where security is everyone’s responsibility. Also, where questioning and verifying unusual requests becomes the norm.
Endpoint Security: Your First Line of Defense
Endpoint security stands as the vanguard in the battle against APTs. It’s the critical armor in safeguarding the entry points of end-user devices. These are devices such as desktops, laptops, and mobile devices. Endpoint security prevents these devices from being exploited by malicious actors. Here’s why endpoint security is indispensable in mitigating APTs:
Detecting Anomalies: Modern endpoint security solutions are equipped with behavioral analysis. This is a technology that detects unusual activity. Activity which could indicate the presence of an APT.
Preventing Execution: Endpoint security can block the execution of suspicious programs. By doing so, they prevent the initial stages of an APT from taking hold.
Limiting Spread: Should an APT breach occur, endpoint security helps contain the threat. Thus, preventing it from moving laterally across the network.
Providing Insights: These solutions offer valuable insights into threat patterns. These patterns help to fortify defenses against future attacks.
Small businesses should look for endpoint security solutions. that offer:
- Comprehensive Coverage: Protection that covers all types of devices and operating systems.
- Real-Time Protection: Solutions that offer real-time scanning and monitoring. This will help catch threats as they emerge.
- Integrated Firewalls: Firewalls control incoming and outgoing network traffic. They do this based on an applied rule set.
- Sandboxing: The ability to isolate and test suspicious programs in a secure environment.
- Automated Responses: Automated processes that react to detected threats quickly. Doing so without the need for human intervention.
Prioritize endpoint security. By doing so, businesses create a robust foundation to defend against the sophisticated and stealthy nature of APTs. It’s more than a security measure. Endpoint security is an investment in the continuity and resilience of the business.
Real-world Examples of APTs and Social Engineering
The theoretical understanding of advanced persistent threats (APTs) and social engineering is crucial. However, examining real-world examples provides a tangible context for these concepts. Here are two case studies of APT campaigns. Both of these leveraged social engineering. Both case studies demonstrate the sophistication and potential impact of these threats.
The Stuxnet Worm: A Game Changer in Cyber Warfare
Stuxnet is a notorious example of an APT that targeted Iran’s nuclear program. Discovered in 2010, it was a highly sophisticated worm that used social engineering to spread. Stuxnet used USB drives and zero-day exploits. The worm subtly altered the speed of centrifuges in nuclear facilities. This caused physical damage while reporting normal operation. This cyber-physical attack marked a significant moment in cyber warfare. It illustrates the potential for APTs to cause real-world damage.
The Carbanak Bank Heist: Social Engineering Meets Financial Fraud
Carbanak was an APT-style campaign that targeted over 100 financial institutions worldwide. It lead to the theft of over $1 billion. The attackers used spear-phishing emails with malicious attachments to infiltrate banking systems. Once inside, they gained control of the banks’ own systems. Then they were able to dispense cash from ATMs and transfer millions into their accounts. This case study underscores the financial devastation that APTs can inflict when combined with social engineering.
These case studies exemplify the dual threat of APTs and social engineering. They show that no sector is immune to these attacks.
These cases highlight the need for robust security measures that go beyond just technology. It needs to include employee education and awareness.
Learn from these incidents. Then businesses can better prepare and protect themselves from similar sophisticated attacks.
How to Defend Against APTs and Social Engineering
Defending against APTs and social engineering requires a multi-layered strategy. This strategy encompasses both technical measures and human factors.
Here’s how businesses can fortify their defenses:
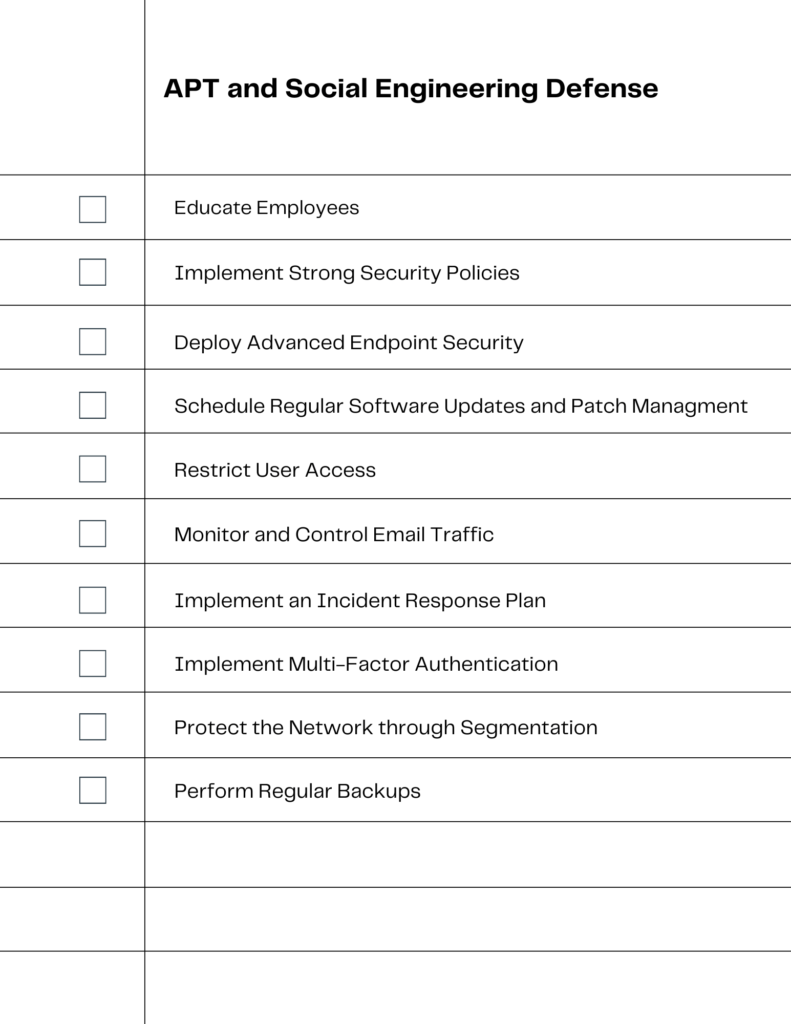
Employee Education and Awareness. Conduct regular training sessions on cybersecurity best practices and social engineering tactics. This can empower employees to become the first line of defense.
Implement Strong Security Policies. Establish and enforce comprehensive security policies. These include password management, incident response, and regular audits.
Deploy Advanced Endpoint Security. Utilize endpoint security solutions with:
- real-time monitoring
- behavioral analysis
- automatic threat response capabilities
Regular Software Updates and Patch Management. Keep all systems updated with the latest security patches. This will close off vulnerabilities that could be exploited by APTs.
Restrict User Access. Apply the principle of least privilege. Ensure that users have only the access necessary to perform their jobs.
Monitor and Control Email Traffic. Use email filtering solutions to detect phishing attempts. Block suspicious emails from reaching end-users.
Incident Response Planning. Develop and regularly update an incident response plan. This will ensure a swift and effective response to any security breaches.
Multi-Factor Authentication (MFA). Implement MFA. This will add an extra layer of security for accessing sensitive systems and information.
Network Segmentation. Divide the network into segments to contain breaches. This will prevent lateral movement of APTs within the network.
Regular Backups. Maintain regular backups of critical data. This will ensure data is stored securely and can be restored quickly.
Integrate these defensive strategies. Then, businesses can create a robust security posture. A posture that deters APTs and social engineering attacks. Further, it also minimizes the impact should a breach occur.
Conclusion: Staying One Step Ahead
APTs and social engineering represent a sophisticated blend of technical prowess and psychological manipulation. It targets organizations of all sizes.
We’ve explored the insidious nature of APTs. Including the human vulnerabilities they exploit. Also explored the critical role of endpoint security as a primary defense mechanism.
Real-world examples have illustrated the tangible impacts of these threats. We’ve outlined a comprehensive strategy to defend against them.
Key points to remember are:
- the importance of employee education
- the implementation of strong security policies
- the necessity of advanced endpoint security solutions
- the value of regular system updates and network segmentation
- vigilant monitoring
- response planning
These measures form the cornerstone of a resilient cybersecurity posture.
Community engagement and knowledge sharing is invaluable.
Join the discussion on our platform to share experiences, strategies, and insights:
- For strategies on defense, visit Defend Against APT Attacks.
- To deepen your understanding of APTs, read What is an Advanced Persistent Threat?.
- Explore Endpoint Security as a Service for solutions tailored to your business needs.
Together, we can build a community that stands resilient in the face of evolving cyber threats. Share your thoughts and ask questions. Let’s bolster our collective defense against APTs and social engineering.
Questions? We Have Answers.
Get answers to a list of the most Frequently Asked Questions.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


