Introduction to Network Segmentation Basics
In the evolving landscape of modern network security, the significance of network segmentation cannot be overstated. As cyber threats grow more sophisticated, safeguarding a business’s digital infrastructure becomes not just a best practice but a necessity. Knowing the basics of network segmentation can play a pivotal role in this defense, acting as a strategic shield against potential breaches and attacks.
At its core, network segmentation is the practice of dividing a computer network into distinct parts or segments. Each segment acts like a smaller, independent network, allowing for more controlled management of network traffic and enhanced security. This process not only improves the overall network performance but also strengthens the network’s resilience against cyber threats. Think of it as organizing a large, bustling city into manageable districts, each with its own specific rules and traffic controls to ensure smoother, safer operations.
What is Network Segmentation?
For beginners, understanding network segmentation can be likened to dividing a large, open office space into several smaller rooms. Each room (or segment) can be secured individually, controlling who has access and what activities can take place. This way, if an issue arises in one room, it doesn’t necessarily impact the entire office. Similarly, in network segmentation, if a security breach occurs in one segment, it’s contained and doesn’t spread to the entire network, thereby minimizing potential damage.
This guide explores network segmentation, a crucial strategy for enhancing security and efficiency in small business networks. It illustrates the risks of flat networks and the benefits of transitioning to segmented ones, using real-world breaches as examples. The guide provides practical steps for implementing network segmentation, emphasizing its role in improving operational efficiency and security. Network segmentation not only contains cyber threats within isolated segments but also boosts overall network performance. Tailored specifically for small businesses, the guide underscores how network segmentation is integral to modern cybersecurity best practices, offering a strategic approach to protecting digital assets and ensuring a resilient, efficient network infrastructure.
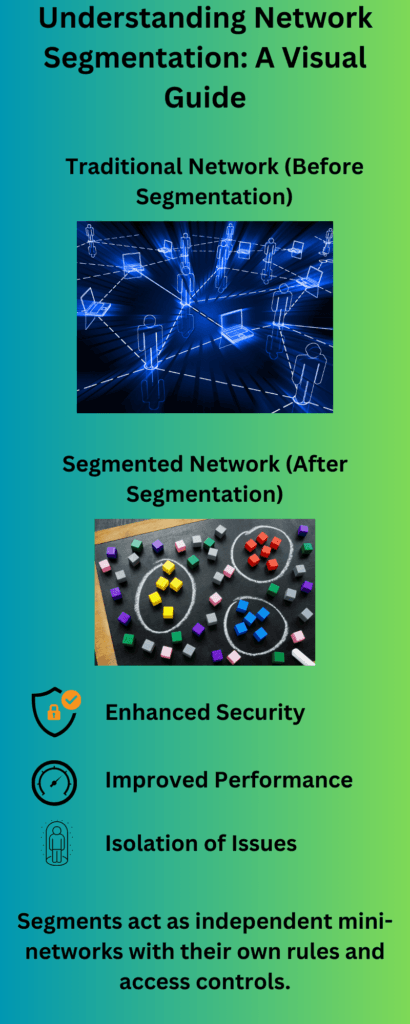
Understanding Network Segmentation: Dividing a Computer Network
Network segmentation is a critical strategy in modern cybersecurity, playing a vital role in enhancing both the security and efficiency of computer networks. By dividing a network into smaller, isolated segments, businesses can significantly bolster their defenses against cyber threats. This concept is best understood through real-world scenarios, such as the Target breach and the casino fish tank hack.
The Target breach is a prime example of the consequences of inadequate network segmentation. Hackers gained access to Target’s network using credentials stolen from a third-party HVAC vendor. This breach led to the compromise of millions of customers’ credit card details. Proper network segmentation could have isolated the HVAC system from the rest of Target’s network, potentially preventing the hackers from accessing sensitive customer data.
Similarly, a casino’s network was compromised through a seemingly innocuous internet-connected fish tank. The attackers exploited this weak link to move laterally within the network and access the high-roller database. This incident underscores the risks of a flat network, where all devices are interconnected without adequate segmentation. Proper network segmentation would have confined the breach within the segment containing the fish tank, safeguarding more critical parts of the network.
The Role of Network Segments in Effective Security
Individual network segments play crucial roles in enhancing security. By segmenting a network, each part can have specific security measures and controls, tailored to its unique risks and needs. This approach not only contains potential breaches within a single segment but also makes overall network management more efficient.
For example, in a segmented network, a breach in a less sensitive segment, such as a guest Wi-Fi network, wouldn’t automatically compromise more critical segments, like those handling sensitive financial data. Moreover, segmentation helps in better managing network traffic, reducing congestion, and minimizing the routes available for cyber-attacks.
Network segmentation, therefore, is not just about dividing a network; it’s about creating multiple layers of defense, each with its own set of security protocols and measures. This multi-layered approach significantly enhances a network’s resilience against cyber threats, protecting sensitive data and maintaining operational integrity.
Network Security: Risks of a Flat Network and the Benefits of Segmentation
In the realm of network design, a flat network refers to a network structure where all nodes, or connection points, are interconnected with minimal to no segmentation. This setup is akin to a vast open-plan office where every workstation is accessible to everyone else. While this might seem efficient, it poses significant security risks. In a flat network, once a cyber threat enters the network, it can move laterally with relative ease, accessing various parts of the network without encountering significant barriers. This vulnerability was starkly highlighted in the casino fish tank hack, where the entire network was compromised through a single, seemingly harmless entry point.
The transition to a segmented network structure is akin to introducing walls and access controls within that open-plan office, creating separate rooms with different levels of security clearance. This not only limits the movement of potential threats but also enhances the overall management of network resources. By segmenting a network, organizations can isolate sensitive data and critical systems, making it considerably more challenging for cyber threats to penetrate the entire network.

Transitioning Your Computer Network into Multiple Segments
Moving from a traditional, flat network to a segmented one requires careful planning and thorough analysis. The first step involves understanding the current network architecture, identifying which areas hold sensitive data or critical operations, and determining how the network traffic flows within the system. This assessment forms the basis for deciding how to divide the network into segments.
The next stage involves designing the segmentation. This could mean creating segments based on function, sensitivity of data, user groups, or grouping similar network resources. For instance, a segment might be dedicated to financial transactions, another for employee communications, and a third for guest internet access. Each of these segments would have its own unique security policies and access controls.
Implementing the segmentation is a meticulous process. It often involves reconfiguring network devices, setting up firewalls, and establishing clear network policies for each segment. It’s crucial to ensure minimal disruption to operations during this transition. Therefore, this process is usually done in phases, segment by segment, to allow for continuous monitoring and adjustment.
Finally, maintaining and regularly reviewing the segmented network is crucial. As business needs and cyber threats evolve, so too should the network segmentation strategy. This ongoing process ensures that the network remains both secure and efficient in the face of changing demands and potential threats.
Building a Segmented Network: A Strategic Approach to Network Segmentation
Implementing network segmentation is more than a technical exercise; it’s a strategic initiative that requires careful consideration and planning. The process begins with identifying the specific needs and vulnerabilities of the network. This involves understanding the types of data processed and stored, the nature of the transactions conducted, and the different user groups accessing the network.
Best practices in implementing network segmentation include starting with a clear and detailed map of the existing network. This map should highlight key areas like data centers, user domains, and external access points. Following this, organizations should prioritize segments based on sensitivity and risk. For example, areas dealing with sensitive customer data or critical operational functions should be segmented first.
It’s also essential to choose the right tools and technologies, such as firewall segmentation, which plays a key role in enforcing the boundaries between segments. Solutions like firewalls, virtual local area networks (VLANs), and network monitoring tools are crucial in creating and managing these segments. Firewalls enforce segmentation policies by controlling traffic between segments, while VLANs can be used to virtually divide the network without changing physical setups. These tools play a critical role in overseeing network traffic and identifying unusual patterns that could signify a breach.
Network Isolation: A Key Aspect of Network Segmentation
Network isolation is a cornerstone of effective network segmentation. It involves creating boundaries within the network, where each segment operates as a self-contained unit. This isolation is crucial for two main reasons: limiting the spread of threats and targeting security measures more precisely.
In the event of a security breach, network isolation ensures that the impact is confined to a single segment. This containment strategy, where segmentation reduces the potential impact area, is invaluable in limiting damage and facilitating quicker response and recovery. For example, if a segment dedicated to guest Wi-Fi access is compromised, the breach can be contained within that segment, protecting more critical parts of the network, such as financial data systems.
Moreover, network isolation allows for the implementation of tailored security measures. Each segment can have its own set of security policies and controls based on its specific risks and needs. This targeted approach not only enhances security but also allows for more efficient resource allocation. Instead of a one-size-fits-all security model, segments receive protection that aligns with their individual exposure to risk.
In conclusion, strategic network segmentation and effective network isolation are critical in creating a robust and resilient network infrastructure. By implementing these practices, businesses can significantly enhance their defense against a wide range of cyber threats, ensuring the security and integrity of their network and the data it holds.
Practical Steps to Divide a Computer Network
Dividing a computer network into effective segments is a structured process that requires careful planning and execution. Here’s a step-by-step guide to help businesses effectively segment their network:
- Identify Critical Assets and Data Flows: Start by identifying what needs the most protection. This could include customer data, financial information, or proprietary company data. Understanding how this data flows across your network is crucial in determining how to segment it effectively.
- Map Out Your Network Topology: Create a detailed map of your current network. This should include all network devices, such as routers, switches, and firewalls, as well as endpoints like computers and other connected devices. Understanding the physical and logical layout of your network is essential for effective segmentation.
- Define Segmentation Objectives and Requirements: Determine what you want to achieve with network segmentation. This could be improved security, better network performance, compliance with regulatory standards, or a combination of these. Your objectives will guide the design of your segmentation strategy.
- Plan Your Segments: Based on the objectives and the network map, plan how to divide the network. Consider factors like the types of users on the network, the applications used, and the sensitivity of the data being accessed. Common segmentation strategies include dividing by department, by type of user (e.g., employees, guests), or by application type.
- Set Segmentation Policies: For each segment, establish security and access policies. This includes defining who can access what resources and what level of network traffic is allowed. These policies should reflect the specific needs and risk profiles of each segment.
- Implement Segmentation Controls: Use technical controls like VLANs, firewalls, and access control lists to enforce the segmentation policies. This might involve reconfiguring existing network hardware or deploying new tools.
- Test the Segmented Network: Before fully implementing, test the segmented network to ensure it operates as intended. Check that the security measures are effective and that legitimate traffic flows correctly.
- Monitor and Adjust as Needed: Once the network segmentation is in place, continuous monitoring is essential. This helps in identifying and responding to any issues quickly. Be prepared to adjust your segmentation strategy as your business and its needs evolve.
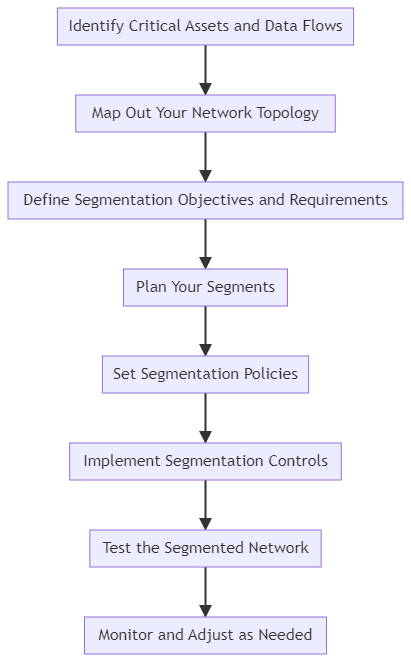
By following these steps, businesses can effectively divide their network into segments, enhancing security and operational efficiency. It’s important to remember that network segmentation is not a one-time task but an ongoing process that requires regular review and adaptation to changing needs and threats.
.
Benefits of Network Segmentation for Small Businesses
Network segmentation, while often associated with larger enterprises, offers significant advantages for small businesses as well, particularly in enhancing security and operational efficiency. This strategic approach to network management can transform how a small business protects and utilizes its digital assets.
Enhanced Security
For small businesses, security is often a top concern, especially given the limited resources for dealing with cyber threats. Network segmentation addresses this concern head-on by creating multiple, isolated segments within the network. If a cyber threat penetrates one segment, its impact is contained, preventing it from spreading to other parts of the network. This containment is crucial for small businesses, as it can significantly reduce the severity and cost of a security breach, by limiting unauthorized network access.
Moreover, segmentation allows for more focused and stringent security measures in segments that handle sensitive data, such as customer information or financial records. By applying robust security protocols to these critical segments, small businesses can better integrate network and security strategies, protecting their most valuable assets from potential threats.
Managing Network Traffic for Improved Operational Efficiency
Operational efficiency is another key area where small businesses stand to gain from network segmentation. By dividing the network into segments, businesses can ensure that network resources are allocated and utilized more effectively. This division can lead to reduced network congestion and improved speed, as each segment handles only its designated traffic.
Additionally, segmentation can simplify network management and maintenance. Issues can be isolated and addressed in specific segments without affecting the entire network, minimizing downtime and disruption to business operations. This targeted approach to network maintenance is especially beneficial for small businesses that might not have extensive IT resources.
Tailored to Business Needs
Network segmentation can be tailored to the specific needs of a small business. Whether it’s segmenting the network based on departmental needs, customer access points, or types of data processed, segmentation offers the flexibility to adapt to the unique operational requirements of a business.
Compliance and Data Protection
With increasing regulatory requirements around data protection, network segmentation can assist small businesses in maintaining compliance. By segmenting sensitive data into secure areas of the network, businesses can more easily meet industry standards and regulatory requirements, providing an added layer of protection against legal and financial repercussions.
Impact of Network Segmentation on Key Business Measures
.
| Business Measure | Improvement Through Network Segmentation |
|---|---|
| Cyber Attack Incidence | Reduced risk of widespread impact from attacks due to containment within segments. |
| Data Breach Response Time | Faster response and isolation of breaches, minimizing data loss and damage. |
| Network Downtime | Decreased downtime due to localized issues, not affecting the entire network. |
| Network Speed and Efficiency | Enhanced speed and efficiency due to reduced congestion and optimized traffic flow. |
| Compliance with Regulations | Easier compliance with data protection regulations through controlled data access and segmentation. |
| Operational Flexibility | Increased flexibility in network management and quicker adaptation to business changes. |
| Cost of Security Incidents | Lower costs associated with security breaches and incidents due to containment and quicker resolution. |
This table illustrates how specific business measures can be positively impacted by network segmentation, providing small businesses with a clear understanding of the tangible benefits they can expect.
In conclusion, network segmentation is not just a security measure; it’s a business strategy that offers numerous benefits, particularly for small businesses looking to enhance their security posture and operational efficiency. By adopting network segmentation, small businesses can protect their assets more effectively, improve their operational capabilities, and position themselves for growth and success in an increasingly digital world.
Conclusion: Embracing Network Segmentation as a Best Practice
As we’ve explored throughout this guide, network segmentation is not merely a technical endeavor; it’s a critical strategy for enhancing the cybersecurity and operational efficiency of any business, especially small businesses. Embracing network segmentation is about understanding the value of proactive defense, the importance of efficient network management, and the need for flexibility in the face of evolving cyber threats.
Key Takeaways
- Enhanced Security: Network segmentation provides a robust layer of security, containing potential breaches within isolated segments and thereby protecting the broader network.
- Operational Efficiency: By dividing the network into manageable segments, businesses can enjoy improved network performance, reduced congestion, and easier maintenance.
- Customizable to Business Needs: The flexibility of network segmentation allows it to be tailored to the specific requirements and challenges of each business.
- Compliance and Data Protection: For small businesses, network segmentation offers a practical path to complying with data protection regulations and safeguarding sensitive information.
Network segmentation has moved beyond being a recommendation to becoming a best practice in network security. It’s a proactive measure that fortifies a business against the growing sophistication of cyber threats. By implementing network segmentation best practices, businesses not only safeguard their digital assets but also enhance their network’s overall functionality and efficiency.
A Call to Action
For small business owners and managers, the message is clear: consider network segmentation as an integral part of your cybersecurity strategy. It’s an investment in the longevity and security of your business. Start by assessing your current network setup, identify the specific needs of your business, and take the strategic steps toward segmenting your network.
Remember, in the digital age, the security and efficiency of your network are crucial to the success and resilience of your business. Network segmentation is more than a security measure; it’s a foundational component of a robust digital strategy, ensuring that your business is not only protected but also positioned for growth and adaptability in a rapidly changing digital landscape.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Doubts about what?