Introduction
Threat hunting is a proactive security approach. Existing tools aim to uncover malicious, suspicious, or risky activities. The reasoning behind threat hunting is the assumption that a breach may have already occurred or will occur. Thus, leading security personnel to actively search for threats in their environment rather than relying solely on deploying new tools.
Threat hunting is something you should have as part of your overall cyber security program.
Understanding the Importance of Threat Hunting
Cyber security is no longer a luxury but a necessity for businesses of all sizes. Perceived lack of robust security measures often makes small businesses a target.
Threat hunting is crucial due to the ability of sophisticated threats to evade automated cyber security measures. Automated tools and SOC analysts can handle most threats. However, the remaining threats often include sophisticated threats that can cause significant damage. These threats can remain undetected for up to 280 days on average, causing significant damage to an organization.
The Role of Cyber Threat Hunting in Small Businesses
One proactive approach to enhancing your business’s cyber security posture is through threat hunting. The expected output of threat hunting is the reduction of the time from intrusion to discovery. Thus, minimizing the damage caused by attackers.
The process of threat hunting will actively search for hidden cyber threats within a network. By doing so, threat hunting aims to identify malicious actors that bypass initial security measures and operate undetected. Successful threat hunting can lead to the detection of potential incidents or ongoing threats, thereby strengthening the organization’s cyber security posture.
This guide will walk you through the process of creating and managing a threat hunting program tailored for small businesses.
Step 0: Know the Assets You Want To Protect
Before you can look for threats you have to know where to look! You would be surprised the number of companies out there who do not have a complete list of assets. When they go through this exercise, they discover that there are assets that they didn’t know existed. Now they need to protect them.
Why is this? First, there are multiple teams at most companies deploying assets. These teams could include developers, testers, demo environments, people running servers in the production environment to collect or analyze data. This server was setup unknown to production.
Further, one might discover a development server that it has a two-way interface with a production database for testing. No protection on the server because you didn’t know about it. Easy path for a hacker to get into your production environment!
In that same vein, you also want to know what paths there are between systems.
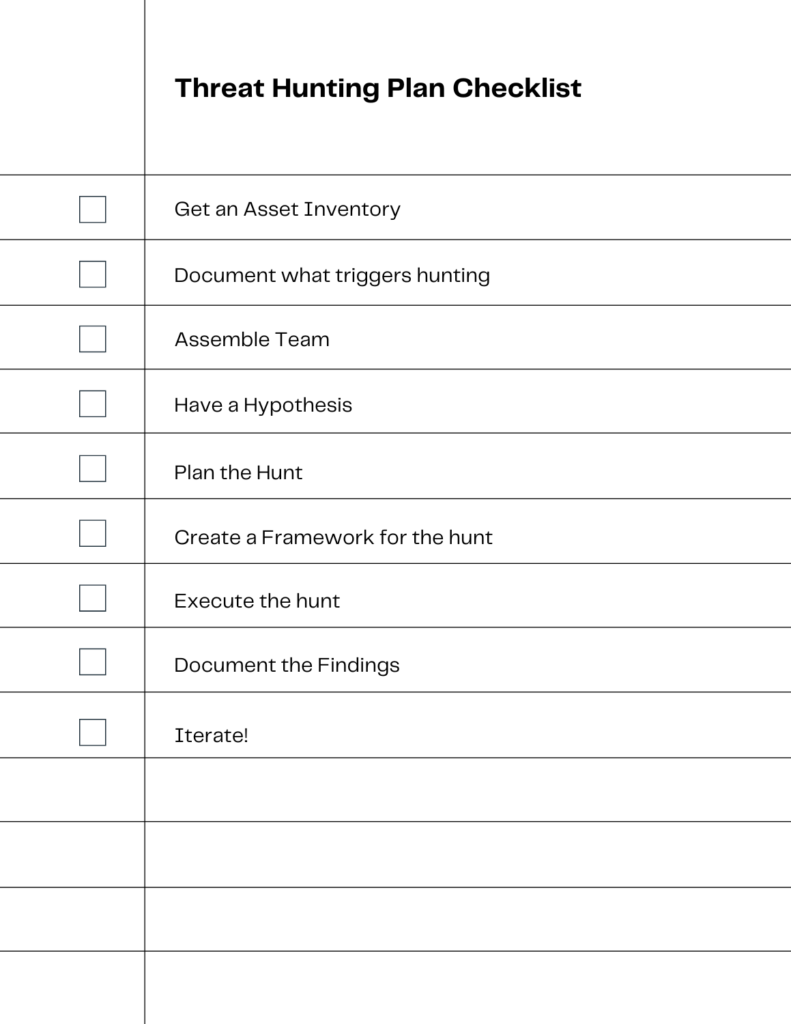
Step 1: An Event Occurs That triggers a Threat Hunting Exercise
You need to be aware of what could trigger a threat hunting exercise. That means you need to be monitoring your system and when you see an indicator, be able to react.
Detection of Unusual Network Traffic
If network monitoring tools detect unusual traffic patterns or data transfers, this could indicate a potential breach. This scenario would trigger an exercise to identify the source and nature of the unusual activity.
Discovery of a Zero-Day Vulnerability
One may initiate threat hunting when we discover a new vulnerability in a software or system. One may initiate this process to determine if someone exploited the vulnerability before we patched it. An example of this is the Microsoft Office and Windows HTML Remote Code Execution Vulnerability, CVE-2023-36884.
Evidence of Advanced Persistent Threats (APTs)
One may initiate an exercise when we see signs of an APT. These are signs such as persistent attempts to gain access to the network or unusual activity from a user account. At that point it is advisable to initiate an exercise. Doing so would allow you to identify and neutralize the threat.
Indications of a Potential Insider Threat
You might discover a user accessing sensitive data they usually don’t need for their job or working at unusual hours. If this happens, it may be an insider threat. We should then initiate an exercise to investigate the activity and determine if it’s a threat.
After a Major Security Incident
One may choose to initiate a threat hunting exercise following a major security incident. One would do this to ensure that you have identified and neutralized all aspects of the threat. One would also do this to identify any potential weaknesses that someone could exploit in the future.
Step 2: Build the Right Team for Threat Hunting
Identifying the Right Team Members
The first step in creating a threat hunting program is assembling the right team. This team should ideally consist of IT professionals who are familiar with your business’s computer and information systems. The team’s size and composition may vary depending on the size of your business and the complexity of your IT infrastructure.
In some cases, it may be advisable to bring in outside consultants. This is especially true if the trigger is due to something that employees of the company are not familiar with.
Defining a Timeline for the Threat Hunt
Depending on the team’s bandwidth, set a timeline for the threat hunting exercise. This will help manage resources effectively and ensure that the process is thorough and not rushed.
Step 3: Formulating a Threat Hunting Hypothesis
Understanding the Hypothesis-Driven Approach
Based on threat intelligence, security research, or the hunter’s experience, formulate hypotheses about potential threats. These hypotheses are educated guesses about tactics, techniques, or procedures that threat actors might use.
Examples of Potential Hypotheses
Here are three hypotheses that could drive a threat hunt and the corresponding responses. In all these scenarios, the threat hunting process is proactive.
The hunt process relies on the threat hunter’s ability to form educated guesses about potential threats. At that point, the threat hunter can use data to confirm or refute these hypotheses. The goal is to identify and neutralize threats before they can cause significant damage.
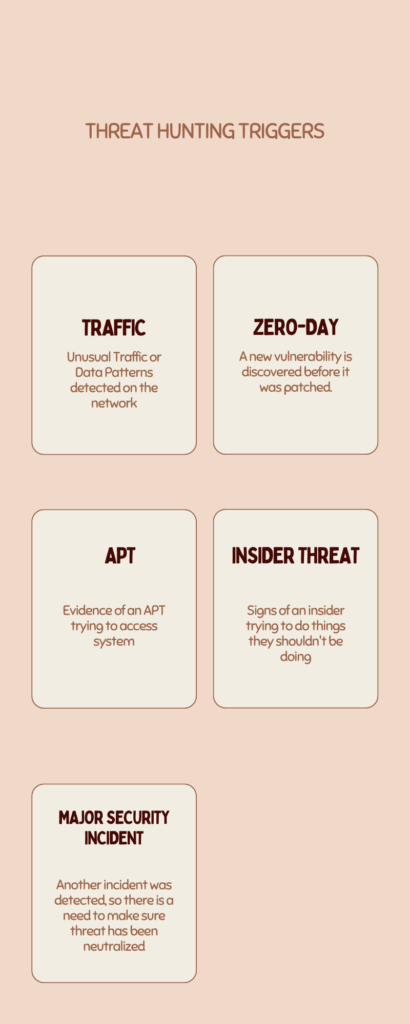
Data Exfiltration Through a Specific Port
One would detect a sudden increase in traffic through a specific port. At that point, one could hypothesize that an adversary is causing the increase by exfiltrating data through that port. In response, a threat hunter would monitor and analyze the traffic through that port.
The threat hunter could then transfer the identified data. After which, the hunter would be able to trace the source and destination of the traffic. If one confirms the hypothesis, the threat hunter would work with the incident response team. They would then collaborate to block the port and remove the threat.
Malware and Command Server Compromise
The threat hunter would look for signs of malware activity or communication with a known command and control server. From that, one could hypothesize that an adversary has compromised systems and is controlling them remotely. In response, a threat hunter would analyze network traffic and system logs to identify the compromised systems.
One could isolate the identified systems from the network. Finally, they could remove the malware. The threat hunter would also investigate how the adversary compromised the systems to prevent future attacks.
Advanced Persistent Threat (APT) Activity
The threat hunter would look for some indication of an APT. These are signs of persistent attempts to gain access to the network or unusual activity from a user account. Based on that, we could hypothesize that an APT is targeting the organization.
In response, a threat hunter would monitor the suspicious activity. Once one identifies the source, one could determine if it is a legitimate user or an adversary.
If the team confirms the hypothesis, the threat hunter would work with the incident response team. The team could then remove the threat and strengthen defenses to prevent future attacks.
Step 4: Planning Your Threat Hunt
Research and Planning Before Diving into the Data
With your team assembled and your hypothesis in place, you can now start planning your threat hunt. This involves determining what data you will need, how you will collect it, and how you will analyze it. For example, you might decide to use a Group Policy in Windows to manage device installation on the computers you oversee [3].
Importance of Careful Planning and Attention to Detail
Step 5: Implementing a Threat Hunting Framework
Designing a Data-Driven Framework
Implementing a threat hunting framework involves setting up the systems and processes that will guide your activities. This could involve using specific software or tools, such as a CRM system. These tools could track customer data.
Another method for building a framework is to adopt a specific methodology. An example of this is the Getting Things Done (GTD) system for task management.
Understanding Tactics, Techniques, and Procedures (TTPs)
Step 6: Starting the Threat Hunt
Actively Searching for Hidden Cyber Threats
Once your framework is in place, you can start the actual threat hunt. This involves actively searching for signs of potential cyber threats within your IT systems. For example, you might look for unusual patterns of data access or transfer that could indicate a cyber threat.
This step in the process is a critical phase that involves collecting relevant data from various sources. Analysts can analyze the collected data to identify potential threats.
Identify Relevant Data Sources
The first step is to identify the data sources that will be most useful for your threat hunt. This could include network logs, system logs, application logs, and other relevant data. The data sources chosen will depend on the hypotheses you are testing.
Data Collection
After identifying the data sources, the next step is to collect the data. This is a systematic process that involves gathering observations or measurements from the identified sources. The data collection process should be planned carefully. This ensures the collection of all relevant and accurate data.
Data Cleaning
After the data has been collected, it needs to be cleaned. This involves removing any errors or inconsistencies in the data that could affect the analysis. Data cleaning is a crucial step in the data analysis process as it ensures that the data is accurate and reliable.
Data Analysis
Once the data has been cleaned, it can be analyzed. This involves studying the data to identify patterns, trends, and anomalies that could indicate a potential threat. Analysts can use various techniques, including statistical analysis and behavioral analysis, to analyze the data.
The goal of the data analysis is to extract actionable insights from the data. Insights that can be used to identify potential threats.
Interpretation of Results
Analysts need to interpret the analyzed data results. This involves making sense of the data and drawing conclusions about potential threats. The interpretation of the results should be based on the data analysis and should be objective and unbiased.
Throughout this process, various tools can be used to assist with data collection and analysis. For example, analysts can use Security Information and Event Management (SIEM) systems to collect and analyze log data from various sources. Additionally, data analysis tools can be used to clean and analyze the data, making the process more efficient and accurate.
Examining Known Indicators of Compromise or Attack
“Known indicators of compromise or attack” (IOCs) are pieces of forensic data. IOCs can signal potential intrusions or malicious activities on a system or network. They are used by information security professionals to identify intrusion attempts. Once identified, they can be analyzed using malware technique, and detect potential breaches in an endpoint or network.
Here are some techniques for examining and/or looking for these indicators.
Network Traffic Analysis
Unusual network traffic can be an indicator of a compromise. This could be outbound traffic to unknown IP addresses or traffic through unusual ports. Network traffic analysis tools can be used to monitor network traffic and identify any unusual patterns.
Log Analysis
Logs from systems, applications, and security devices can contain valuable information about potential threats. Log analysis tools can be used to sift through large volumes of log data. This can be used to identify suspicious activities. Activities such as these could be considered suspicious:
- unknown files and processes
- suspicious activities in privileged accounts
- irregular activities from unexpected countries
File Analysis
The presence of unknown or unexpected files on a system can be an indicator of a compromise. File analysis tools can be used to scan the system for unknown files and analyze them for potential threats.
Behavioral Analysis
Behavioral analysis involves monitoring the behavior of users and systems to identify any unusual or suspicious activities. This can include things like dubious logins, anomalous spikes in file access, or unusual activities from unexpected countries.
Threat Intelligence Sharing
By sharing threat intelligence and IOCs with other organizations, you can enhance your ability to detect and respond to threats. This can involve participating in threat intelligence sharing platforms or working with cyber security vendors that provide threat intelligence services.
Step 7: Documenting and Reviewing Your Findings
Importance of Documentation Throughout the Process
As you conduct your threat hunt, it’s important to document your findings. This provides a record of what you’ve done. It can also help you identify patterns and trends that could inform future threat hunts.
Step 8: Iterating and Improving Your Threat Hunting Program
Understanding Threat Hunting as a Continuous Process
Threat hunting is not a one-time activity, but an ongoing process. After each threat hunt, take the time to reflect on what worked well and what could be improved.
Once your threat hunt is complete, take the time to review your findings. Then you can assess the effectiveness of your threat hunting program.
By conducting this step, you can expect to gain valuable insights into the effectiveness of your threat hunting process. You’ll be able to:
- identify areas for improvement
- optimize your methods
- ultimately enhance the overall efficiency and effectiveness of your threat hunting efforts
Investigate Findings
Any anomalies or potential threats found during the hunt should be thoroughly investigated. This could involve tracing the source of the threat, identifying the systems affected, and understanding the nature of the threat.
Resolution
Once the threats have been identified and investigated, work towards resolving them. This could involve removing the threat, patching vulnerabilities, and strengthening defenses to prevent future attacks.
Evaluate the Hypothesis
Reflect on the hypothesis you started with. This evaluation will help you refine the process of forming hypotheses in future hunts.
- Was it appropriate for the hunt?
- Did it guide you towards meaningful data and potential threats?
- Did it lead you down a path with little to no significant findings?
Assess the Scope
Consider whether the scope of your hunt was too broad or too narrow. A broad scope might lead to an overwhelming amount of data. On the other hand, too narrow a scope might cause you to miss significant indicators. This assessment will help you better define the scope in future hunts.
Review the Collected Intelligence
Reflect on the intelligence you collected. Was it helpful? Could some processes be done differently to yield more valuable data? This review will help you optimize your data collection methods.
Evaluate the Tools Used
Did you have the right tools for the hunt? Were there any tools that didn’t contribute significantly to the hunt? This evaluation will help you optimize your toolset for future hunts.
Process Adherence
Did everyone follow the plan and process? Were there any deviations that led to inefficiencies or missed opportunities? This reflection will help you ensure better adherence to the plan in future hunts.
Leadership Empowerment
Did leadership feel empowered to address questions along the way, and did they have access to all the needed information? This consideration will help you ensure that leadership is appropriately involved and informed in future hunts.
Regularly Reassessing and Improving Your Program
Use these insights to iterate and improve your threat hunting program over time.
After the threat hunt, review the process and the findings. Use this information to improve future exercises and to enhance the organization’s overall cyber security defenses.
This step in a threat hunting program is a crucial phase. It focuses on assessing the current state of the program and identifying areas for enhancement. This step is about learning from past experiences, refining methodologies, and improving the effectiveness of the threat hunting program. Here’s how you can reassess and improve your threat hunting program:
Evaluate the current state of your threat hunting program. This includes reviewing your existing processes, methodologies, and documentation. Identify what’s working well and what needs improvement. This assessment should be thorough and honest to ensure that all areas of the program are adequately evaluated.
Assessing Existing Processes and Documentation
By following these steps, you can expect to have a more robust and effective threat hunting program. You’ll be better equipped to detect and respond to threats, thereby enhancing your organization’s overall security posture.
Setting Goals
Define clear and measurable goals for your threat hunting program. These goals should align with your organization’s overall security objectives. They serve as a guide for your threat hunting activities and provide a benchmark for measuring the program’s success.
Attack Surface Identification and Management
Understand your organization’s attack surface. This includes identifying all assets, systems, and data that could be targeted by attackers. Regularly update this information to reflect changes in your organization’s infrastructure and threat landscape.
Frameworks and Methodologies
Use established frameworks and methodologies to guide your threat hunting activities. These can provide a structured approach to threat hunting and ensure that all potential threats are adequately addressed.
Continuous Learning and Improvement
Threat hunting is a continuous process. Regularly review and update your threat hunting program to reflect new threats, technologies, and best practices. This includes training your team on new techniques, investing in new tools, and refining your methodologies.
Conclusion
Creating and managing this kind of program is a significant undertaking. However, it’s one that can greatly enhance your business’s cyber security posture. You should consider forming your own program. Lacking the resources to do so, consider engaging a consultant to do so if one or more triggering events happen.
Follow the steps outlined in this guide! Then, you can create a robust and effective program that is tailored to your business’s specific needs.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!