
Introduction: The Evolution of Anomaly Detection
In the vast expanse of the digital universe, where data flows like a ceaseless river, anomalies are the subtle ripples that often go unnoticed. But as we stand at the threshold of 2023, these ripples can no longer be ignored. Anomaly detection, once a niche concept in the realm of data science, has now become a frontline defender in the world of cybersecurity.
From its humble beginnings, where manual scrutiny was the norm, to today’s sophisticated machine learning-driven systems, anomaly detection has undergone a transformative journey. As cyber threats evolve, becoming more covert and unpredictable, the importance of spotting the “odd one out” has never been more paramount. This article delves deep into the world of anomaly detection, exploring its evolution, its current significance, and why, in 2023, it’s a topic that every business leader, IT professional, and even the everyday user should be familiar with.
So, buckle up and join us on this enlightening journey, because understanding anomaly detection might just be the key to safeguarding your digital future.
Understanding the Core: What is Anomaly Detection?
Anomaly detection, at its essence, refers to the process of identifying patterns in data that do not conform to expected behavior. These non-conforming patterns, often termed as outliers or anomalies, can be indicative of a significant event such as a system failure, a security breach, or even a potential cyber-attack.
The basic concept revolves around establishing a norm or a baseline, derived from historical data. Once this norm is set, any deviation from it, be it subtle or glaring, can be flagged as an anomaly. This is crucial because these deviations, while sometimes benign, can often signify potential threats.
This is one of many endpoint security tools one should have in their toolkit to improve a business’s defenses.
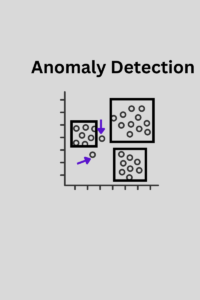
To better grasp the importance of anomaly detection, let’s delve into a few real-world use cases.
Financial Fraud Detection
Banks and financial institutions employ anomaly detection to monitor transactions. If a customer who typically makes small, local purchases suddenly makes a large international transaction, it could be flagged as anomalous, potentially indicating credit card fraud.
Network Security
In a corporate network, if there’s an unusual spike in data transfer or traffic during off-hours, anomaly detection tools can flag this activity. This could be a sign of a data breach or an unauthorized access attempt.
Intrusion Detection in IoT Devices
With the proliferation of Internet of Things (IoT) devices in homes and businesses, ensuring their security has become paramount. This underscores the need for intrusion detection systems. One type of IDS uses anomaly detection. Anomaly detection can monitor the traffic and behavior of these devices. For instance, if a smart thermostat suddenly starts sending data packets to an unfamiliar location, it could be flagged as anomalous, indicating a potential compromise or malware infection.
These use cases underscore the significance of anomaly detection. By identifying deviations from the norm, businesses and industries can proactively address potential challenges, ensuring smoother operations and enhanced security.
.
Why Anomaly Detection is Crucial in Today’s Cyber Landscape
In the ever-evolving realm of the digital world, the sophistication and complexity of cyber threats have grown exponentially. Gone are the days when simple firewalls and basic antivirus software were sufficient to ward off malicious attacks. Today’s cyber adversaries employ intricate tactics, often blending in with regular network traffic, making their detection a formidable challenge. This is where the indispensability of anomaly detection comes into play.
The Rising Complexity of Cyber Threats
Modern cyber threats are no longer just about direct attacks. They encompass a spectrum of malicious activities, from advanced persistent threats (APTs) that lurk in the shadows of a network for extended periods to ransomware that can cripple an entire organization’s operations. These threats are designed to be stealthy, evading traditional detection mechanisms and blending seamlessly with legitimate activities.
Moreover, with the proliferation of Internet of Things (IoT) devices and the increasing interconnectivity of systems, the attack surface has expanded dramatically. Each connected device or system presents a potential entry point for cyber adversaries. The sheer volume of data generated and the myriad of interactions make manual monitoring an impractical solution.
Proactive Threat Mitigation with Anomaly Detection
This is where anomaly detection shines as a beacon of hope. Instead of merely reacting to known threats, anomaly detection adopts a proactive approach. By continuously monitoring and analyzing data patterns, it identifies deviations from the norm, even if such deviations are subtle or previously unknown.
For instance, if a user who typically accesses the system during regular business hours suddenly logs in at an odd hour or downloads large volumes of data, anomaly detection systems would flag this behavior as suspicious. Such early detection allows organizations to respond swiftly, potentially halting a cyberattack in its tracks before it inflicts significant damage.
Furthermore, with the integration of machine learning and artificial intelligence, anomaly detection systems are continually evolving. They learn from new data, refining their understanding of what constitutes ‘normal’ behavior, and enhancing their ability to spot anomalies. This continuous learning ensures that as cyber threats evolve, so do the mechanisms to detect and counteract them.
In conclusion, as the cyber landscape becomes increasingly treacherous, the role of anomaly detection as a first line of defense becomes paramount. It’s not just about identifying threats; it’s about anticipating them, offering organizations a fighting chance in the relentless battle against cyber adversaries.
Diving Deeper: Types of Anomalies
In the intricate world of anomaly detection, not all anomalies are created equal. Depending on the nature, context, and data involved, anomalies can be categorized into three primary types: global, contextual, and collective outliers. Understanding these categories is crucial for effective detection and response.
- Global Outliers: These are data points that are significantly different from the rest of the data, regardless of the context. They stand out distinctly when viewed against the entire dataset.
- Example: In a company’s network traffic data, if the average data transfer is around 50GB per day and suddenly there’s a spike to 500GB on a particular day, this spike would be considered a global outlier.
- Contextual Outliers: These anomalies are context-specific. They might appear normal when viewed in isolation but become anomalous when considered within a specific context or during a particular time frame.
- Example: An IT company might see increased server activity during weekdays but low activity on weekends. If there’s a sudden spike in activity on a Sunday, it would be a contextual outlier, as it deviates from the expected behavior for that specific day.
- Collective Outliers: These anomalies involve a collection of data points that, as a group, exhibit anomalous behavior. Individually, these data points might not be anomalies, but their collective pattern is of interest.
- Example: In a secure network, a series of login attempts might be normal. However, if there’s a pattern of multiple login attempts followed by a large data download and then an external data transfer, this sequence, when viewed collectively, could indicate a potential data breach.
By distinguishing between these types of anomalies, cybersecurity professionals can tailor their detection methods and responses, ensuring that potential threats are identified with precision and addressed appropriately.
The Science Behind the Detection: Key Methodologies
In the realm of anomaly detection, the methodologies employed are as diverse as they are intricate. These algorithms and techniques are the backbone of detection systems, ensuring that anomalies are identified with precision and accuracy. Let’s delve into some of the key methodologies that power these systems.
Statistical Methods
These are foundational techniques that have been in use for a long time. They rely on statistical properties of data, such as mean, median, and standard deviation, to detect anomalies. Any data point that deviates significantly from these statistical norms can be flagged as an outlier.
Clustering-Based Methods
Clustering involves grouping data points based on similarity. In the context of anomaly detection, data points that don’t belong to any cluster or belong to small clusters can be considered anomalies. The K-means clustering algorithm is a popular example of this approach.
Density-Based Methods
These methods, like the DBSCAN algorithm, work on the principle that a data point can be considered an anomaly if the density around it is significantly lower than that of its neighbors.
Classification-Based Methods
These techniques involve training a model on a labeled dataset, where data points are marked as ‘normal’ or ‘anomalous’. Once trained, the model can classify new data points into these categories. Decision trees and neural networks are examples of classification-based methods.
The Role of Machine Learning and Artificial Intelligence:
Machine learning (ML) and artificial intelligence (AI) have revolutionized anomaly detection. Instead of relying solely on predefined rules or thresholds, ML algorithms can learn from data, adapting to new patterns and evolving threats. This adaptability ensures that detection systems remain effective even as cyber threats become more sophisticated.
AI, on the other hand, brings in advanced capabilities like deep learning, which can process vast amounts of data, recognizing complex patterns that might be missed by traditional methods. Additionally, AI can automate the process of anomaly detection, sifting through terabytes of data in real-time, ensuring timely threat identification and response.
Together, machine learning and artificial intelligence not only enhance the accuracy of anomaly detection but also ensure that systems are future-proof, ready to tackle the ever-evolving landscape of cyber threats.
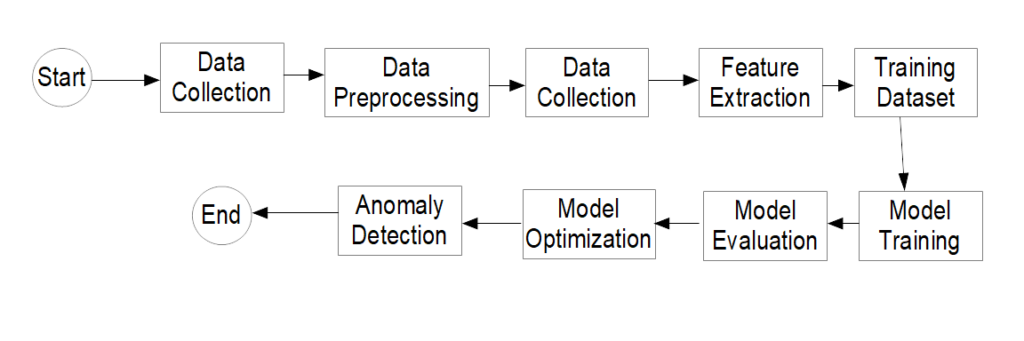
A Sample Workflow for Anomaly Detection Using Machine Learning
In our exploration of anomaly detection using machine learning, visualizing the process can be immensely beneficial. The table provided offers a structured breakdown of this intricate procedure. It commences with the collection of raw data, which then undergoes preprocessing to ensure its quality and consistency. Key features are subsequently extracted, setting the stage for the creation of training and test datasets. The heart of the process lies in the training of the machine learning model, which learns and adapts from the training data. This model is then evaluated for its accuracy and, if necessary, optimized further.
Once deemed satisfactory, the model is employed to detect anomalies in new and unseen data. This systematic approach ensures that the anomaly detection is both accurate and efficient, harnessing the full potential of machine learning techniques.
| Step Name | Description |
|---|---|
| Start | Signifies the beginning of the process. |
| Data Collection | The initial phase where raw data is collected from various sources, such as network traffic, user behavior logs, or system metrics. |
| Data Preprocessing | Involves cleaning the data, handling missing values, and normalizing it to ensure consistency. |
| Feature Extraction | Relevant features or attributes are identified and extracted from the preprocessed data. |
| Training Dataset Creation | Splitting the data into a training set (used to train the model) and a test set (used to evaluate the model). |
| Model Training | The machine learning algorithm learns from the training data, adjusting its parameters to minimize errors. |
| Model Evaluation | The trained model is tested on the test set to assess its accuracy. |
| Model Optimization | If the model’s performance is unsatisfactory, it is sent back for further optimization. |
| Anomaly Detection | If the model’s performance is satisfactory, the trained model is now used to detect anomalies in new, unseen data. |
| End | Signifies the completion of the process. |
Real-world Applications: Anomaly Detection in Action
Anomaly detection isn’t just a theoretical concept; it’s a practical tool that’s actively shaping the cybersecurity landscape. Let’s delve into some real-world applications to understand its significance.
- Network Intrusion Detection: In today’s interconnected world, networks are constantly under threat from cybercriminals. Anomaly detection plays a pivotal role in monitoring network traffic. By establishing a baseline of “normal” traffic, any deviation, such as an unexpected surge in data transfers or unauthorized access attempts, can be flagged. This is crucial for preventing potential breaches and ensuring data integrity.
- Phishing Email Detection: Phishing emails are malicious attempts to trick individuals into providing sensitive information. These emails often deviate from the norm in terms of sender details, content, or attachments. Anomaly detection can identify these outliers, flagging suspicious emails and preventing potential security breaches.
- User Behavior Analytics: Within an organization, employees have certain patterns of behavior when accessing and using IT resources. Anomaly detection can monitor these patterns. If an employee suddenly accesses sensitive data they’ve never accessed before or logs in at odd hours, it could indicate a compromised account or insider threat.
The Benefits for Small and Medium-sized Enterprises (SMEs):
For SMEs, the stakes are high. They often lack the extensive resources of larger corporations but face many of the same threats. Anomaly detection offers a cost-effective solution. Instead of investing heavily in large-scale security infrastructures, SMEs can leverage anomaly detection to provide real-time alerts for potential threats. This proactive approach ensures timely responses, minimizing potential damages. Moreover, as SMEs grow and evolve, anomaly detection systems can adapt, ensuring continuous protection. In essence, anomaly detection offers SMEs a scalable, efficient, and effective cybersecurity solution.
Challenges in Anomaly Detection: False Positives and Implementation Complexities
While anomaly detection offers a plethora of benefits in the realm of cybersecurity, it’s not without its challenges. One of the primary issues faced is the double-edged sword of advanced detection.
The Double-Edged Sword of Advanced Detection:
Advanced anomaly detection systems, especially those powered by machine learning and AI, are designed to be highly sensitive to deviations. While this sensitivity ensures that even the subtlest of threats are detected, it also means that benign activities can sometimes be flagged as anomalies. This phenomenon is known as a “false positive.”
For instance, consider an employee who typically accesses the company’s server during regular working hours. If this employee logs in late one night to meet a deadline, an advanced anomaly detection system might flag this as suspicious activity, even though it’s a legitimate action. Similarly, a sudden but legitimate spike in website traffic due to a marketing campaign might be mistaken for a DDoS attack.
Such false positives can lead to unnecessary panic, wasted resources in investigating non-issues, and even potential disruptions if legitimate activities are mistakenly blocked.
Strategies for Minimizing False Alarms:
- Continuous Model Training: Regularly update and train the machine learning models with new data to ensure they adapt to changing patterns and reduce the chances of flagging legitimate activities as anomalies.
- Contextual Analysis: Instead of relying solely on standalone data points, consider the broader context. For instance, if an unusual server access coincides with a known company event or deadline, it might be legitimate.
- Feedback Loop: Implement a feedback mechanism where false positives are reported and analyzed. This feedback can be used to refine the detection algorithms and reduce future false alarms.
- Threshold Tuning: Adjust the sensitivity of the anomaly detection system. While increasing the threshold might reduce false positives, it’s essential to strike a balance to ensure genuine threats aren’t missed.
In conclusion, while anomaly detection is a powerful tool in cybersecurity, it’s essential to be aware of its challenges. By understanding these challenges and implementing strategies to address them, organizations can harness the full potential of anomaly detection without being bogged down by false alarms.
Choosing the Right Tools: Anomaly Detection Systems in 2023
As the digital landscape evolves, so do the tools and platforms designed to safeguard it. Anomaly detection systems have seen significant advancements in recent years, with a plethora of options available in 2023. Let’s explore some of the standout tools and platforms in the market.
Elastic Stack (ELK Stack)
A powerful combination of Elasticsearch, Logstash, and Kibana, the Elastic Stack offers real-time anomaly detection, powered by machine learning. It’s particularly adept at analyzing large volumes of data, making it suitable for enterprises with extensive digital footprints.
Splunk
Renowned for its advanced data analytics capabilities, Splunk offers a dedicated solution for anomaly detection. With its intuitive interface and robust machine learning algorithms, Splunk provides actionable insights, helping businesses preempt potential threats.
Darktrace
Leveraging artificial intelligence, Darktrace offers an “Enterprise Immune System.” It learns the ‘pattern of life’ for every user and device in an organization, allowing it to detect anomalies in real-time, from subtle insider threats to more blatant cyber-attacks.
AWS GuardDuty
A cloud-centric solution, AWS GuardDuty offers intelligent threat detection for AWS environments. It continuously monitors for malicious or unauthorized behavior, ensuring that cloud resources remain secure.
Datadog
With a focus on cloud-scale monitoring, Datadog offers an anomaly detection platform that integrates seamlessly with various cloud providers. Its machine learning algorithms automatically adapt to changing patterns, ensuring accurate detection.
Factors to Consider When Selecting an Anomaly Detection Solution:
- Scalability: As your business grows, so will your data. Ensure that the chosen solution can handle increased data volumes without compromising performance.
- Integration Capabilities: The tool should seamlessly integrate with your existing infrastructure, be it on-premises, cloud, or hybrid.
- Real-time Analysis: In the world of cybersecurity, time is of the essence. Opt for solutions that offer real-time anomaly detection, ensuring timely threat identification and response.
- Customizability: Every business is unique. The chosen platform should be customizable to cater to specific business needs and requirements.
- Cost-effectiveness: While security is paramount, it’s essential to consider the total cost of ownership, including licensing, training, and maintenance costs.
In 2023, with the myriad of options available, choosing the right anomaly detection system can seem daunting. However, by understanding the leading tools in the market and considering the factors that align with your business needs, you can make an informed decision that bolsters your cybersecurity posture.
The Future of Anomaly Detection: Predictions and Trends
The realm of anomaly detection is in a constant state of evolution, driven by technological advancements and the ever-changing nature of cyber threats. As we look ahead, certain trends and predictions emerge, painting a picture of a future where anomaly detection is more sophisticated, efficient, and indispensable than ever before.
AI and Unsupervised Machine Learning: The Game Changers:
Artificial Intelligence (AI) and unsupervised machine learning are at the forefront of this evolution. Traditional anomaly detection systems relied on predefined rules and thresholds, which, while effective, had limitations in terms of adaptability and scalability. Enter AI and unsupervised machine learning.
- Adaptive Learning: Unlike supervised learning, where models are trained on labeled data, unsupervised learning operates on raw, unlabeled data. This allows the system to identify new patterns and anomalies without prior knowledge, making it adept at detecting previously unseen threats.
- Complex Pattern Recognition: AI-driven systems can process vast amounts of data, recognizing intricate patterns and correlations that might be missed by traditional methods. This not only enhances detection accuracy but also reduces false positives.
- Proactive Threat Intelligence: With AI, anomaly detection systems can predict potential threats based on emerging patterns, allowing businesses to adopt a more proactive stance in their cybersecurity efforts.
The Imperative of Real-time Detection:
As cyber-attacks grow in sophistication, the window of opportunity to detect and respond shrinks. Delayed detection can result in significant damages, both in terms of data breaches and financial implications.
- Instantaneous Response: Real-time anomaly detection ensures that threats are identified the moment they occur, allowing for immediate response measures. This is crucial in scenarios like ransomware attacks, where every second counts.
- Enhanced User Experience: For online platforms and services, real-time detection ensures that any malicious activity is swiftly dealt with, ensuring uninterrupted service and a seamless user experience.
- Operational Efficiency: With real-time insights, businesses can streamline their operations, reducing the time and resources spent on manual threat analysis and investigation.
In conclusion, the future of anomaly detection is bright, shaped by the twin pillars of AI and real-time analysis. As cyber threats continue to evolve, so will the tools and methodologies to combat them, ensuring that businesses remain one step ahead in the cybersecurity game.
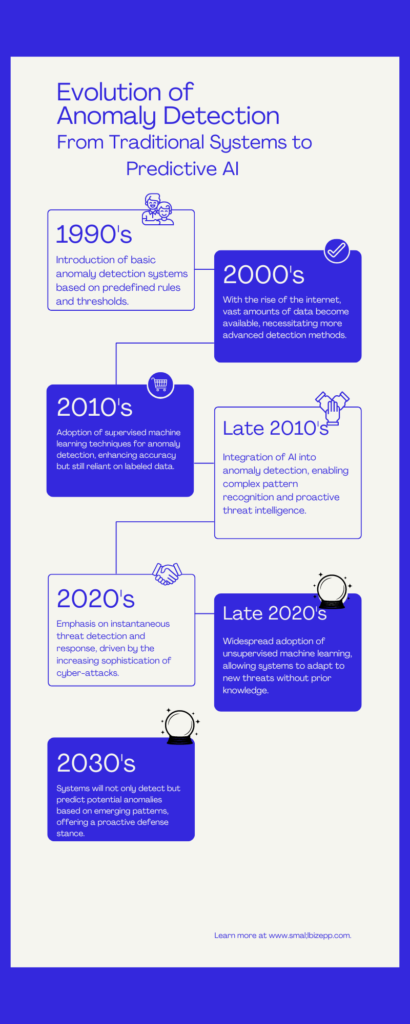
Conclusion: Preparing for a Secure Future
In our journey through the intricate world of anomaly detection, we’ve traversed its foundational concepts, delved into its methodologies, and glimpsed its future. From its humble beginnings in the late 1990s to the AI-driven, predictive systems anticipated in the 2030s, anomaly detection has proven to be a cornerstone of cybersecurity.
The digital landscape is in perpetual flux, with new threats emerging and old ones evolving. In this dynamic environment, anomaly detection stands as a sentinel, guarding businesses against unforeseen cyber challenges. Its importance cannot be overstated, especially in an era where data breaches and cyber-attacks can have monumental repercussions.
For businesses, both large and small, prioritizing anomaly detection is not just a strategic move—it’s a necessity. As we’ve seen, the tools and techniques are continually advancing, offering more robust and efficient solutions. Staying updated in this realm is not just about enhancing security; it’s about ensuring business continuity, safeguarding reputation, and fostering trust.
In conclusion, as the digital age progresses, let anomaly detection be your compass, guiding you through the murky waters of cybersecurity threats. Embrace its advancements, understand its significance, and let it fortify your business against the cyber challenges of today and tomorrow.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
