Introduction
In the dynamic world of cybersecurity, the role of machine learning endpoint security has become paramount. As we navigate through 2023, businesses, both large and small, are facing an increasingly sophisticated array of cyber threats. Traditional security measures, while essential, often fall short in addressing these evolving challenges.
Enter machine learning—a game-changer in the realm of endpoint security. This technology not only promises faster threat detection but also offers predictive insights, ensuring businesses stay one step ahead of potential breaches. In this article, we’ll delve deep into the transformative impact of machine learning on endpoint security, shedding light on its significance in today’s digital landscape.
The Evolving Landscape of Endpoint Security
As we progress through 2023, the digital realm is witnessing an unprecedented surge in cyber threats. These aren’t just your run-of-the-mill malware or phishing attempts; we’re talking about sophisticated, multi-faceted attacks that can cripple entire networks in minutes.
Recent reports suggest that ransomware attacks have seen a staggering 150% increase in the first half of the year alone, with small to medium-sized businesses being the most targeted. Additionally, the rise of IoT (Internet of Things) devices has opened up a new frontier for cybercriminals, with a predicted 20% increase in attacks targeting these devices.
In the face of such daunting challenges, it’s evident that traditional security measures are no longer sufficient. This is where technology steps in, offering a beacon of hope. Advanced technologies, especially machine learning and artificial intelligence, are at the forefront of this battle against cyber adversaries. These tools not only detect threats but also learn from them, constantly evolving to offer more robust protection. The increasing integration of these technologies into endpoint security solutions underscores their critical role in safeguarding our digital assets in these turbulent times.
Demystifying Machine Learning in Endpoint Security
What is Machine Learning?
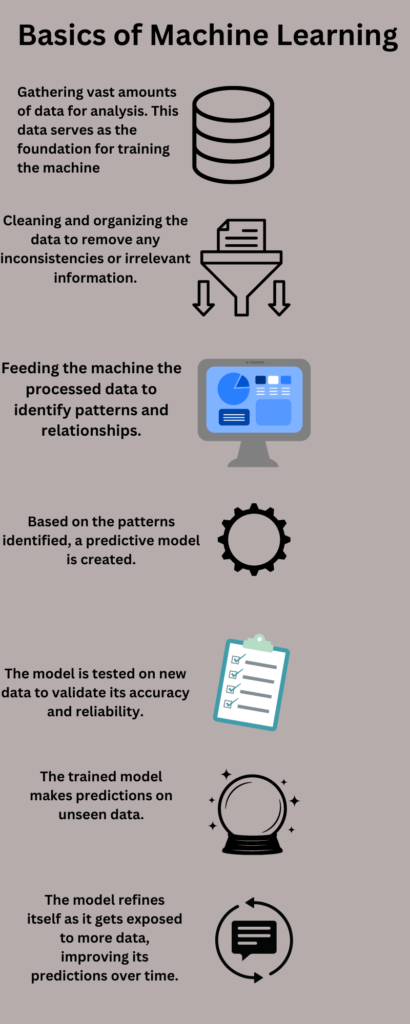
Machine learning, often abbreviated as ML, is a subset of artificial intelligence (AI) that enables computers to learn and make decisions without being explicitly programmed. In essence, it’s the process by which machines analyze vast amounts of data, identify patterns, and then use this knowledge to predict future outcomes or make informed decisions.
To break it down further:
- Training: At the heart of machine learning is the concept of training. This involves feeding the machine a large dataset, known as the training data. This data contains examples, and the machine tries to find patterns or relationships within it. For example, consider an email spam filter. By training on thousands of emails labeled as ‘spam’ or ‘not spam’, the machine learns the common characteristics of spam emails.
- Prediction: Once trained, the machine can then make predictions on new, unseen data. It uses the patterns it identified during training to make these predictions. For example, after the spam filter is trained, it can predict whether a new incoming email is spam or not based on its learned characteristics.
- Continuous Learning: One of the beauties of machine learning is its ability to continuously learn. As it gets exposed to more data, it refines its models, making its predictions more accurate over time.
In the context of endpoint security, machine learning can be a game-changer. For instance, by analyzing historical data on cyber threats, a machine learning model can predict potential future threats or vulnerabilities, enabling proactive defense measures.
Why Machine Learning Matters in Endpoint Security
In the vast and intricate landscape of cybersecurity, endpoint security stands out as a particularly challenging domain. Endpoints, which include devices like computers, smartphones, and tablets, are often the primary targets for cyberattacks. As businesses grow and evolve, so does the number of endpoints they utilize, making the task of securing them increasingly complex.
Unique Challenges in Endpoint Security:
- Diverse Threat Landscape: Every day, thousands of new malware variants emerge, each designed to bypass traditional security measures. Keeping up with this ever-evolving threat landscape is a monumental task.
- Increased Endpoint Complexity: With the rise of IoT devices, BYOD (Bring Your Own Device) policies, and remote work, the variety and number of endpoints have skyrocketed.
- Rapid Response Requirement: In the face of a cyberattack, every second counts. Traditional security measures often lack the speed required to detect and respond to threats in real-time.
Machine learning comes into play as a powerful tool to address these challenges. Here’s how:
Real-world Implications and Benefits for Businesses
Proactive Threat Detection
Instead of reacting to threats after they’ve occurred, ML-driven endpoint security can predict and identify potential threats based on historical data. For example, a business might receive an email that seems benign but has patterns similar to a previously identified phishing attempt. An ML-driven system can flag this email before any user interacts with it.
Adaptive Learning
As new threats emerge, machine learning models continuously learn and adapt, ensuring that the security measures are always a step ahead. For example, an e-commerce site experiences a new type of DDoS attack. After thwarting it, the ML system learns from this attack, making the site more resilient against future similar threats.
Reduced False Positives
One of the significant challenges in cybersecurity is the high rate of false positives, which can divert attention from real threats. Machine learning can refine its detection algorithms to reduce these, ensuring that IT teams focus on genuine threats. For example, graphic design firm frequently shares large files. Traditional systems might flag this as suspicious data transfer, but an ML system, understanding the business’s nature, recognizes it as a regular activity.
Efficient Resource Allocation
With machine learning automating the threat detection process, businesses can allocate their IT resources more efficiently, focusing on strategy and other critical tasks. For example, a small business with a limited IT team can rely on ML-driven security to handle routine threat detection, allowing the team to focus on improving the company’s overall IT infrastructure.
In essence, machine learning is not just a fancy add-on in the realm of endpoint security. It’s a necessity, a game-changer that offers businesses a fighting chance in the relentless battle against cyber threats.
Diving Deep: How Machine Learning Enhances Endpoint Security
The Mechanics of ML in Security
Machine learning, at its core, is driven by algorithms—sets of rules and patterns that a machine follows to make decisions. But how do these algorithms function in the context of security, and what kind of data fuels them? Let’s delve into the mechanics.
How Algorithms Work
- Training Phase: Before an algorithm can detect threats, it needs to be trained. This involves feeding it a vast amount of data, both benign and malicious. The algorithm processes this data, identifying patterns and behaviors associated with each type.
- Feature Extraction: Features are specific characteristics or patterns in the data that the algorithm identifies as significant. For instance, in the context of endpoint security, features might include patterns of system calls, file activities, or network connections.
- Model Creation: Once the algorithm understands the features, it creates a model—a representation of the data and its patterns. This model is what the system uses to make predictions about new, unseen data.
- Validation and Testing: After the model is created, it’s tested on a separate set of data (not used in the training phase) to validate its accuracy. This ensures that the model can generalize its predictions to new data and not just memorize the training data.
- Deployment: Once validated, the model is deployed in real-world scenarios, where it begins to monitor and analyze data in real-time, making predictions and flagging potential threats.
Types of Data Required
- Historical Threat Data: This includes data on past cyberattacks, malware signatures, and other threat indicators. It provides the algorithm with a foundation, helping it understand what malicious activity looks like.
- Behavioral Data: This pertains to how software, systems, and users typically behave. Any deviation from this norm can be a potential sign of a threat.
- Network Traffic: Analyzing the flow of data in and out of a network can reveal patterns associated with cyberattacks, such as DDoS attacks or data breaches.
- System Logs: Logs provide a chronological record of events on a system. They can reveal suspicious activities, like unauthorized access attempts or changes to system configurations.
- External Threat Intelligence: Information from external sources, like threat intelligence feeds or cybersecurity forums, can provide insights into emerging threats and vulnerabilities.
In conclusion, the power of machine learning in security lies in its ability to process vast amounts of data, learn from it, and make real-time decisions. The algorithms, fueled by diverse and comprehensive data, offer a dynamic and adaptive approach to endpoint security, ensuring that businesses remain resilient in the face of evolving cyber threats.
Benefits of Machine Learning in Endpoint Defense
In an era where cyber threats are not only increasing in number but also in sophistication, the need for advanced defense mechanisms has never been more critical. Machine learning, with its data-driven approach, offers a suite of benefits that traditional security measures often struggle to provide. Let’s explore some of these advantages.
Faster Threat Detection and Real-time Responses
Traditional security systems often rely on predefined rules and signatures to detect threats. While this approach can be effective against known threats, it often falls short when faced with new, unknown cyberattacks. Machine learning, on the other hand, doesn’t just rely on predefined rules. By analyzing vast amounts of data, it identifies patterns and anomalies, enabling it to detect threats at an unprecedented speed. Moreover, once a potential threat is identified, machine learning models can initiate real-time responses, mitigating the threat before it can cause significant damage. For businesses, this means reduced downtime, safeguarded data, and enhanced overall security.
Predictive Analysis and Proactive Defense Mechanisms
One of the standout features of machine learning is its ability to predict future events based on historical data. In the context of endpoint security, this predictive capability is invaluable. Instead of merely reacting to threats after they’ve occurred, machine learning allows security systems to anticipate them. By analyzing past cyberattacks, system behaviors, and network traffic, ML models can forecast potential vulnerabilities or attack vectors. This proactive approach enables businesses to fortify their defenses in advance, often preventing cyberattacks from occurring in the first place. For instance, if a machine learning model identifies a pattern of increasing unauthorized login attempts from a specific IP range, it can proactively block access, preventing a potential breach.
In conclusion, the integration of machine learning into endpoint security isn’t just a technological upgrade; it’s a paradigm shift. By offering faster threat detection and a proactive defense stance, machine learning ensures that businesses are not just responding to the cyber threat landscape but actively shaping it in their favor.
Limitations and Challenges
While machine learning has undoubtedly revolutionized endpoint security, it’s essential to recognize that it’s not a silver bullet. Like any technology, it comes with its own set of limitations and challenges that need to be addressed to harness its full potential.
Potential Vulnerabilities
Machine learning models, especially in security, are trained on vast amounts of data. However, if threat actors gain knowledge about the specifics of these models, they can craft inputs (known as adversarial examples) designed to deceive them. These deceptive inputs can cause the model to misclassify malicious activities as benign, allowing threats to bypass security measures. Additionally, machine learning models can be susceptible to “poisoning attacks,” where threat actors introduce malicious data into the training set, causing the model to make incorrect predictions.
Importance of a Multi-layered Approach
Given these vulnerabilities, it’s crucial to not rely solely on machine learning for endpoint security. A multi-layered approach, which combines traditional signature-based detection with machine learning and other advanced techniques, offers a more robust defense. This layered strategy ensures that even if one layer is compromised or fails to detect a threat, the other layers can provide backup, ensuring continuous protection.
Addressing False Positives and Ensuring Accuracy
One of the challenges with machine learning in security is the issue of false positives—where benign activities are mistakenly flagged as threats. High rates of false positives can lead to “alert fatigue” among IT teams, causing them to overlook genuine threats. To address this:
- Continuous Training: Regularly updating and training the machine learning model with new data ensures that it remains relevant and reduces the chances of misclassification.
- Feedback Loops: Implementing feedback mechanisms where false positives are reported and analyzed can help refine the model. Over time, this iterative process improves the model’s accuracy.
- Hybrid Models: Combining machine learning with rule-based systems can help in validating threats. If both systems flag an activity as malicious, it’s more likely to be a genuine threat.
In summary, while machine learning offers transformative benefits in endpoint security, it’s essential to be aware of its limitations. By understanding these challenges and implementing strategies to address them, businesses can harness the power of machine learning while ensuring a comprehensive and resilient security posture.
Comparing Traditional and ML-Driven Endpoint Security
What Traditional Endpoint Security Misses
Traditional endpoint security, while foundational, has been built around a set of predefined rules and known threat signatures. While effective against threats of the past, the rapidly evolving cyber landscape has exposed several gaps and vulnerabilities in these conventional methods.
Gaps in Traditional Endpoint Security
- Reactive Nature: Traditional systems primarily operate on a reactive basis. They respond to threats based on known signatures. This means that they’re often ill-equipped to handle new, unknown threats or zero-day exploits until an update or patch is released.
- Limited Scope: Conventional methods rely on a database of known threats. If a threat hasn’t been previously identified and added to this database, the system might fail to recognize it.
- Inefficient Against Polymorphic Malware: Modern malware often changes its code or appearance to evade detection. Traditional systems, which rely on fixed signatures, struggle to detect such polymorphic threats.
- High False Positive Rates: Due to their reliance on fixed rules, traditional systems can often misidentify benign activities as threats, leading to unnecessary alerts and potential disruptions.
How Machine Learning Addresses These Gaps
- Proactive Detection: Instead of waiting for a threat to match a known signature, ML-driven systems analyze patterns and behaviors. This allows them to identify and respond to novel threats in real-time.
- Adaptive Learning: Machine learning models continuously learn from new data. As they’re exposed to more threats, they adapt and refine their detection mechanisms, ensuring they remain effective against evolving threats.
- Efficiency Against Advanced Threats: ML systems are better equipped to handle advanced threats like polymorphic malware. By analyzing the behavior rather than just the appearance of files, they can detect malicious activities even if the code changes.
- Reduced False Positives: With their ability to analyze vast amounts of data and identify subtle patterns, ML-driven systems can differentiate between genuine threats and benign activities with higher accuracy.
In essence, while traditional endpoint security methods have served us well in the past, the modern threat landscape demands a more dynamic and adaptive approach. Machine learning, with its data-driven insights and continuous learning capabilities, offers a robust solution to the limitations of conventional security measures.
The Edge Machine Learning Provides
In the ever-evolving realm of cybersecurity, the distinction between traditional and ML-driven endpoint security becomes increasingly pronounced. While both have their merits, machine learning offers a set of advantages that make it a formidable force against modern cyber threats. Let’s delve into a comparative analysis to understand the edge machine learning provides.
| Feature | Traditional | ML-Driven |
|---|---|---|
| Dynamic Threat Detection | Relies on a database of known threat signatures. New threats often go undetected. | Analyzes behavior and patterns, detecting anomalies and potential threats, even if they’re new. |
| Adaptability | Static in nature. Needs manual updates for new threats. | Continuously learns from new data, refining its detection mechanisms in real-time. |
| Response Time | Often slower, especially if a threat is new or not in its database. | Offers real-time threat detection and response. |
| Handling Advanced Threats | Struggles against advanced threats like polymorphic malware or zero-day exploits. | Effectively detects advanced threats by analyzing behavior, not just appearance. |
| False Positives | Higher rates due to fixed rules, leading to “alert fatigue.” | Analyzes vast data to discern subtle patterns, reducing false positives. |
| Predictive Capabilities | Lacks the ability to predict future threats or vulnerabilities. | Uses historical data to forecast potential future threats, enabling a proactive defense stance. |
In conclusion, while traditional endpoint security has its place and continues to offer valuable protection, machine learning provides an edge that’s hard to overlook. Its dynamic, adaptive, and predictive capabilities make ML-driven solutions a necessity for businesses aiming to stay ahead in the cybersecurity game.
Real-world Applications and Success Stories
Businesses Transformed by ML Endpoint Security
In the contemporary digital landscape, the integration of Machine Learning (ML) into endpoint security has revolutionized the way businesses safeguard their assets. Several case studies underscore the transformative power of ML in bolstering cybersecurity measures.
Case 1: SMS Scams
One notable instance is the rise of SMS scams, especially during the pandemic era. With a significant portion of the global workforce transitioning to remote work, text messages became a primary communication channel, not just among colleagues but also among students and educators. This shift presented an opportunity for cybercriminals, who began deploying phishing schemes under the guise of COVID-19-related information. However, the implementation of the Mobile Threat Defense System, powered by ML, proved to be a game-changer. These advanced ML models were adept at distinguishing between genuine COVID-19 informational messages and deceptive phishing attempts, ensuring the security of countless users.
Case 2: Mobile Endpoint Security
Another transformative application of ML can be observed in the realm of mobile endpoint security. As mobile devices became ubiquitous, they also emerged as prime targets for cyber threats. Recognizing this challenge, tech giants like Google began harnessing the power of ML to fortify mobile device security. One cybersecurity leader, Wandera, leveraged its ML algorithms to detect an astounding 500 ransomware strains across various corporate mobile devices. Such proactive detection mechanisms underscore the unparalleled efficacy of ML-driven solutions in preempting and neutralizing threats.
Case 3: Cybersecurity Analysis
Lastly, the realm of cybersecurity analysis witnessed a paradigm shift with the advent of ML. Traditional methods of threat detection often resembled searching for a needle in a haystack, given the sheer volume of data. However, MIT’s introduction of the AI2 system, an adaptive ML security platform, revolutionized this process. AI2 was not only capable of sifting through millions of daily actions to isolate malicious activities but also succeeded in reducing the threat rate by a staggering 85%. This case underscores the unmatched precision and efficiency of ML in enhancing human analysis and safeguarding against potential errors.
These case studies serve as testament to the transformative potential of Machine Learning in redefining endpoint security, offering businesses a robust shield against the ever-evolving landscape of cyber threats.
Expert Insights on the Future of Endpoint Security
As we navigate the intricate web of digital transformation, the intersection of Machine Learning (ML) and endpoint security emerges as a focal point of innovation and evolution. Leading experts in the field have weighed in on the trajectory of this convergence, offering insights that paint a vivid picture of the future. Here are some of the most compelling predictions and trends for the coming years.
Proliferation of Self-Learning Systems
The next generation of endpoint security solutions will be characterized by their ability to learn autonomously. Instead of relying solely on predefined algorithms, these systems will adapt and evolve based on the threats they encounter, ensuring that they remain a step ahead of cyber adversaries.
Enhanced Integration of AI and ML
While ML has already made significant inroads into endpoint security, the future will witness a deeper integration with Artificial Intelligence (AI). This synergy will result in smarter threat detection mechanisms, capable of understanding the intent behind malicious activities, not just the actions themselves.
Proactive Threat Hunting
The reactive model of cybersecurity, where threats are addressed after they manifest, will give way to a proactive approach. ML-driven systems will not only detect threats but will also predict and neutralize them before they can inflict damage, ushering in an era of proactive threat hunting.
Reduction in Human Intervention
As ML models become more sophisticated, the need for human intervention in threat detection and response will diminish. Automated systems will handle the majority of threats, allowing human experts to focus on more complex and nuanced cybersecurity challenges.
Quantum Computing and Cybersecurity
The advent of quantum computing presents both opportunities and challenges for endpoint security. On one hand, quantum computers can enhance the capabilities of ML models, making them faster and more accurate. On the other, they introduce new vulnerabilities that cybercriminals can exploit. The cybersecurity community will need to strike a balance, harnessing the power of quantum computing while safeguarding against its potential threats.
Ethical Considerations in ML-driven Security
As ML models gain the ability to make autonomous decisions, ethical considerations will come to the forefront. The industry will grapple with questions about accountability, transparency, and the potential biases of these systems.
Evolution of Cyber Threats
Just as security systems evolve, so too will cyber threats. We can anticipate a new breed of malware and cyberattacks specifically designed to target and deceive ML-driven security systems. This cat-and-mouse game will necessitate continuous innovation and adaptation on the part of cybersecurity professionals.
In conclusion, the future of endpoint security, underpinned by Machine Learning, promises to be dynamic, challenging, and transformative. As technology continues to advance at a breakneck pace, the onus will be on businesses and cybersecurity experts to stay informed, agile, and prepared for the challenges and opportunities that lie ahead.
Conclusion: Share Your Thoughts and Experiences
The digital landscape is in a state of constant flux, with the convergence of Machine Learning and endpoint security standing at the forefront of this evolution. As we’ve explored in this article, ML offers transformative benefits, from dynamic threat detection to proactive defense mechanisms. However, it’s not without its challenges, necessitating a multi-layered approach to truly harness its potential.
The real-world applications and success stories underscore the tangible impact of ML-driven solutions, while expert insights provide a glimpse into a future filled with promise and challenges. As cyber threats continue to evolve, so too must our defenses, making the integration of ML in endpoint security not just a luxury, but a necessity.
We invite you, our readers, to be a part of this ongoing conversation. Whether you have insights to share, challenges you’ve faced, or questions about the intricacies of machine learning in endpoint security, your perspective is invaluable. Together, by sharing knowledge and experiences, we can shape the future of cybersecurity and ensure a safer digital world for all.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


