IoT Security Best Practices: 2023 Guide to Safeguard Your Devices
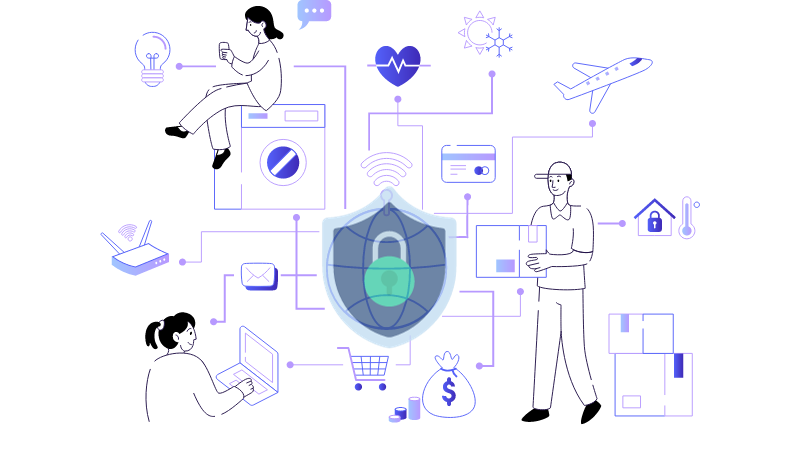
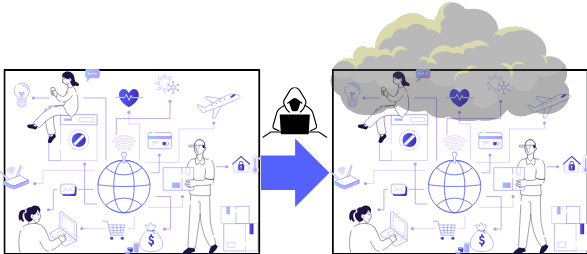
Introduction: The Rising Importance of IoT in 2023 In the digital age, the Internet of Things (IoT) has emerged as a revolutionary force, reshaping how businesses operate and individuals live. From smart thermostats regulating our home temperatures to intricate sensors optimizing supply chains, IoT devices have seamlessly woven themselves into the fabric of our daily […]
IoT Security Best Practices: 2023 Guide to Safeguard Your Devices Read More »