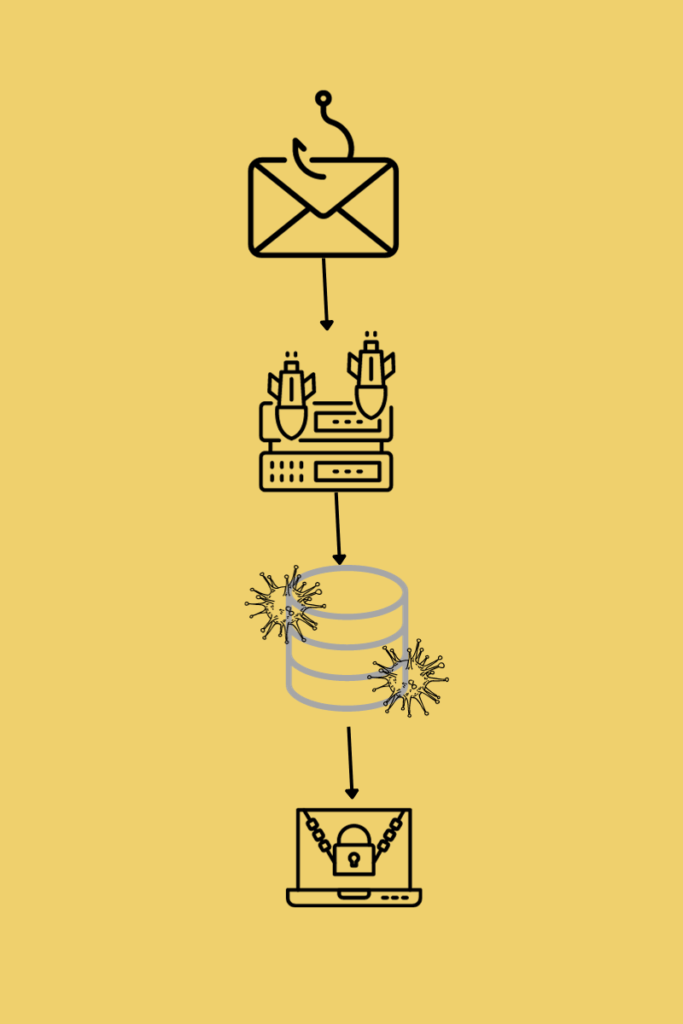
Understanding the Top 13 Types of Phishing Attacks and How to Avoid Them
Phishing attacks are a major cyber threat. Understanding types like email, spear, and whaling phishing is crucial. Recognize signs and implement preventive measures to safeguard your data.
Understanding the Top 13 Types of Phishing Attacks and How to Avoid Them Read More »