In today’s rapidly evolving digital landscape, understanding the threats that lurk in the shadows is paramount. One such threat that has been gaining traction is fileless malware. Unlike its more conventional counterparts, fileless malware doesn’t rely on traditional files to wreak havoc. Instead, it cleverly operates within a computer’s memory, leaving minimal traces and often evading standard detection methods. For small business managers and the dedicated IT personnel supporting them, this presents a unique challenge.
As cyber adversaries become more sophisticated, the significance of fileless malware in the cybersecurity realm cannot be understated. It’s a silent, yet potent threat, and being aware is the first step to fortification.
But what IS fileless malware??
Key Takeaways
- Memory-based Threat: Fileless malware operates in computer memory, making it harder to detect than traditional file-based malware.
- Sophisticated Attacks: Utilizes legitimate system tools like PowerShell, increasing the difficulty of detection and removal.
- Evasion Techniques: Evades standard antivirus solutions by not leaving traditional file traces.
- Business Vulnerability: Small businesses, often with limited cybersecurity resources, are prime targets.
- Multi-Layered Defense: Protecting against fileless malware requires advanced endpoint protection, regular updates, and employee education.
What is Fileless Malware? Understanding the Threat
In the vast realm of cybersecurity threats, fileless malware stands out as a particularly elusive adversary. But what exactly is fileless malware? At its core, it is a type of malicious software that doesn’t rely on traditional files to carry out its nefarious activities. Instead, it operates directly within a computer’s memory, making it significantly harder to detect and remove.
To truly grasp the contrast between fileless malware and its traditional counterpart, let’s delve into a comparative table that highlights their distinct attributes:
| Feature/Attribute | Fileless Malware | Traditional Malware |
|---|---|---|
| Storage Location | Resides in memory (RAM) | Stored on disk (e.g., executable files) |
| Detection Difficulty | Harder to detect; evades many antivirus solutions | Easier to detect with standard antivirus |
| Infection Method | Exploits vulnerabilities, scripts, or legitimate tools | Uses malicious files or attachments |
| Persistence | Uses legitimate processes for persistence | Often creates files or registry changes |
| Visibility | Operates stealthily with minimal traces | Leaves a digital footprint on the system |
As illustrated in the table above, traditional malware typically leaves a tangible footprint on a system, such as files or registry changes. This makes it relatively easier for standard antivirus software to detect and remove. On the other hand, fileless malware is like a phantom, operating stealthily within the system’s memory and often using legitimate processes to persist. This not only makes it harder to detect but also poses unique challenges for IT personnel and small business managers aiming to safeguard their digital assets.
Understanding these differences is crucial. As cyber threats evolve, so must our strategies to counteract them. By being informed about the intricacies of fileless malware, businesses can better equip themselves against this emerging and potent threat.
So here are the differences, but how does Fileless Malware work?
How Fileless Malware Works
The digital battleground of cybersecurity is ever-evolving, with adversaries constantly innovating to bypass defenses. One of the most significant shifts in this landscape is the rise of fileless malware, which operates fundamentally differently from traditional malware. But how exactly do these two differ?
Memory-Based Operations: Traditional malware, as the name suggests, relies on files. When it infects a system, it typically leaves a file or multiple files on the disk. These files serve as the malware’s footprint, and they execute the malicious operations. In contrast, fileless malware doesn’t need to store files on the disk. Instead, it operates directly within the computer’s memory (RAM). By leveraging legitimate system tools and processes, it can execute commands. Then it can move laterally across networks, and even exfiltrate data. All of this without ever writing a file to the system’s storage. This memory-based operation is what makes it so challenging to detect and counteract.
Stealthy Nature: Fileless malware’s modus operandi is stealth. By not relying on traditional files, it avoids leaving the usual traces that antivirus software typically scans for. Moreover, since it often uses legitimate system processes to carry out its activities, distinguishing between genuine operations and malicious ones becomes a daunting task. This inherent stealthiness allows fileless malware to persist on infected systems for extended periods without detection, granting cyber adversaries ample time to achieve their objectives.
Fileless Malware poses a significant threat due to its stealthy nature. It operates within a computer’s memory, using legitimate tools and services within the system to carry out its malicious activities. This makes it incredibly difficult to detect and remove, allowing it to cause significant damage before it’s even discovered.
Moreover, real-world examples of attacks include major ransomware outbreaks like Petya and WannaCry. These attacks caused significant disruption and financial losses for businesses worldwide, highlighting the serious threat posed by fileless malware.
To put it in perspective, let’s revisit the table from the previous section.
| Feature/Attribute | Fileless Malware | Traditional Malware |
|---|---|---|
| Storage Location | Resides in memory (RAM) | Stored on disk (e.g., executable files) |
| Detection Difficulty | Harder to detect; evades many antivirus solutions | Easier to detect with standard antivirus |
| Infection Method | Exploits vulnerabilities, scripts, or legitimate tools | Uses malicious files or attachments |
| Persistence | Uses legitimate processes for persistence. | Often creates files or registry changes |
| Visibility | Operates stealthily with minimal traces. | Leaves a digital footprint on the system |
As highlighted, the differences between traditional and fileless malware are stark. For small business managers and IT personnel, understanding these distinctions is paramount. It’s not just about knowing the enemy but adapting defenses to counteract this new breed of cyber threat effectively.
Common Methods of Infiltration: The Threat to Small Businesses
Small businesses are often seen as easy targets by cybercriminals. The reason? They typically have fewer resources dedicated to cybersecurity compared to larger enterprises. This makes them particularly vulnerable to fileless malware attacks.
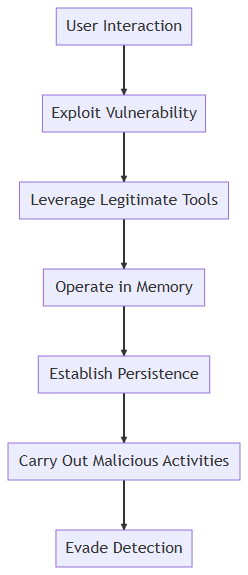
Here is a general flow for the attack as visualized in the flow diagram.
- User Interaction: This is often the initial point of contact, where the user might click on a malicious link or open a compromised attachment.
- Exploit Vulnerability: Fileless malware begins its infiltration by exploiting a known software or OS vulnerability.
- Leverage Legitimate Tools: Instead of using malicious files, it leverages legitimate system tools (like PowerShell) to execute commands.
- Operate in Memory: This malware that operates in RAM, avoiding disk writing.
- Establish Persistence: It manipulates system processes or the registry to remain active even after system reboots.
- Carry Out Malicious Activities: With its foothold, the malware carries out activities like data exfiltration or lateral movement.
- Evade Detection: Throughout its lifecycle, the malware aims to remain undetected, leveraging its stealthy nature and the system’s legitimate processes.
Fileless Malware can infiltrate a system many ways. Here, we will discuss the three key ones here.
PowerShell Script Attacks
Fileless malware often exploits legitimate tools like PowerShell, which is built into Windows. Attackers can execute malicious code directly in memory, bypassing the need for files. For instance:
- PowerShell Empire: Attackers may use this framework to create and execute scripts, enabling remote control of infected systems. The malware operates entirely in memory, making it hard to detect.
- Reflective DLL Injection: Malicious PowerShell scripts can inject code into a running process without using traditional files, leveraging the existing infrastructure of the host system.
Social Engineering and Phishing Emails
Attackers will commonly employ social engineering to trick users into running malicious scripts. They can send phishing emails, disguising them as legitimate messages.
Two common scenarios used are:
- Fake Software Updates: Users are prompted to download and run an attachment, which appears as a legitimate software update. Instead of an update, it is actually a script that initiates the malware. Usually comes from a fake email address that appears to come from IT or the software manufacture.
- Urgent Requests: Attackers impersonate trusted entities, sending emails that create a sense of urgency. Thus, compelling victims to click on links or open attachments. These links or attachments can then execute fileless malware. Typically, this will appear to come from their manager, a higher up manager in the company, or perhaps law enforcement.
Living Off the Land Techniques
Fileless malware can take advantage of legitimate system tools and processes. This is a concept known as “living off the land.” Examples include:
- Windows Management Instrumentation (WMI): Malicious scripts may use WMI to execute commands stealthily. Thus, evading detection by appearing as legitimate system activity.
- Scheduled Tasks: Attackers can create scheduled tasks to run scripts at specified times. Since this is a common system function, it often goes unnoticed.
Technical Aspects of Fileless Malware
Process Hollowing Techniques
Process hollowing is a stealthy technique commonly employed in fileless malware attacks. It involves creating a legitimate process in a targeted system’s memory, only to hollow it out and replace its content with malicious code. This technique allows attackers to camouflage their activities. They leverage trusted system processes to execute their malicious payloads. Thus, making detection challenging. Once the malicious code is injected, it can perform a wide range of malicious actions, such as data theft or system compromise. As the fileless malware operates solely in memory, without leaving files on disk, process hollowing is a key component of fileless malware’s ability to evade traditional security measures.
Code Execution in the operating system
Fileless malware employs sophisticated code execution techniques to infiltrate and compromise systems without leaving a trace of files on disk. These techniques often exploit trusted system processes or scripts like PowerShell or WMI to run malicious code directly in memory. By leveraging legitimate components, fileless malware evades traditional antivirus software and security measures. Common code execution methods include reflective DLL injection, process hollowing, and script-based attacks. These techniques allow fileless malware to execute malicious instructions stealthily, making detection and mitigation challenging. At the same time, they enable actions like data theft, lateral movement, and system compromise.
Malicious Activity in the Windows Registry
Fileless malware often utilizes the Windows Registry to carry out malicious activities discreetly. This technique involves manipulating registry keys and values to execute and persistently maintain malicious code within the system. Attackers can create or modify registry entries to initiate processes during system startup, granting them persistence and control. By residing in the registry, fileless malware avoids traditional file-based detection methods, making it challenging to detect and remove. Malicious registry activities can include running malicious scripts, loading malicious DLLs, and altering system configurations, all of which enable attackers to maintain a hidden presence and execute various harmful actions on the compromised system.
How Fileless Malware Evades Detection
Challenges in detection: Why it’s difficult to detect
This threat presents a unique challenge to traditional antivirus software. This is primarily because it operates within a system’s memory or registry keys. It does this rather than relying on files stored on the hard drive. This method of operation allows it to remain virtually invisible, leaving no footprint for antivirus scanners to detect.
For instance, consider a scenario where an attack is launched using PowerShell scripts. These scripts are legitimate tools within the Windows operating system, making it difficult for antivirus software to flag them as malicious. The malware can execute its malicious code within the memory space of these script. In doing so, it is effectively hiding its activities from traditional detection methods.
Furthermore, it can hide its malicious code execution without creating a malicious file. This means that even if an antivirus software is scanning for suspicious files, it may not detect the threat. This stealthy approach makes this a formidable threat that requires advanced detection methods to counter.
Different methods of Detection
Here we are going over 8 different methods of Fileless Malware Detection. The table below gives a comparison of the effectiveness of each method.
| Detection Method | Effectiveness | Pros | Cons |
|---|---|---|---|
| Signature-Based | Low | Identifies known malware patterns | Ineffective against new or custom variants |
| Heuristic/Behavioral | Moderate | Detects unusual behavior and anomalies | May generate false positives |
| Anomaly Detection | Moderate to High | Identifies deviations from typical activity | Requires baseline behavior for accuracy |
| Machine Learning | High | Adapts to evolving threats | Requires continuous training and updates |
| Endpoint Detection and Response (EDR) | High | Offers real-time monitoring and response | Can be resource-intensive |
| Sandboxing | High | Isolates and analyzes suspicious activity | May be bypassed by advanced malware |
| User Training and Awareness | Moderate | Empowers users to recognize phishing emails | Limited effectiveness against zero-day attacks |
| Network Traffic Analysis | Moderate | Identifies suspicious traffic patterns | May miss host-based fileless malware |
Note that the effectiveness of each method can vary depending on the specific implementation, the sophistication of the fileless malware, and the ability to adapt to emerging threats. Organizations often use a combination of these methods to create a layered security approach that provides a higher level of protection against fileless malware attacks.
Signature Based Detection
This method relies on pre-defined signatures or patterns of known fileless malware. When a file or script matches a signature in the database, it triggers an alert. However, this approach is limited to detecting previously identified threats and may not be effective against new or customized variants.
Heuristic/Behavioral Detection
Heuristic and behavioral detection methods focus on identifying suspicious behavior rather than relying on specific signatures. They analyze the actions of running processes, looking for atypical or malicious activities. While effective at catching previously unseen threats, they can produce false positives due to the complexity of user and system behavior.
Anomaly Detection
Anomaly detection establishes a baseline of typical system behavior and identifies deviations from this baseline. When a process exhibits behavior that significantly differs from the norm, it raises an alert. However, anomaly detection requires continuous learning and tuning to distinguish between legitimate and malicious deviations accurately.
Machine Learning
Machine learning models leverage algorithms to learn from large datasets and identify patterns associated with fileless malware. These models adapt to evolving threats by continuously analyzing new data and adjusting detection criteria. They excel at detecting novel malware strains but require regular updates and training.
Endpoint Detection and Response (EDR)
EDR solutions provide real-time monitoring and response capabilities. They collect and analyze data from endpoints, looking for suspicious activities like code execution in memory. EDR tools offer the advantage of swift response actions, such as isolating compromised devices or terminating malicious processes.
Sandboxing
Sandboxing involves isolating suspicious files or scripts in a controlled environment to observe their behavior. If the script attempts malicious actions, the sandbox detects them, helping security teams understand the threat’s nature. Some advanced malware may, however, detect and evade sandboxes.
User Training and Awareness
User training focuses on educating employees to recognize phishing emails and suspicious requests. While this method empowers users to be the first line of defense, it primarily addresses the social engineering aspect of fileless malware attacks and may not prevent all forms of infiltration.
Network Traffic Analysis
Network traffic analysis monitors data flows within a network for signs of suspicious activity, such as unusual data transfers or communication patterns. While it can identify certain fileless malware techniques, it may not catch host-based fileless attacks that don’t involve network traffic.
Role of antivirus software and endpoint security
Antivirus software and endpoint security play a crucial role in fileless malware detection. They provide a proactive defense against these stealthy threats. They employ a combination of signature-based detection, heuristics, behavior analysis, and machine learning to identify malicious activities in real-time.
These tools can monitor system processes and behaviors. In doing so, they can look for anomalies and known patterns associated with fileless attacks. By continuously scanning and analyzing the activities of running processes and network communications, antivirus software and endpoint security solutions help detect and mitigate fileless malware. And so they can enhance the overall system security and minimizing the risk of compromise.
Importance of monitoring command lines and detecting unusual patterns
Monitoring command lines and detecting unusual patterns is crucial for fileless malware detection. This processing allows security systems to scrutinize the core of system activity. Fileless malware often operates through legitimate processes, utilizing command-line interfaces like PowerShell to execute malicious actions.
By analyzing command-line activities for deviations from expected behavior, security solutions can flag suspicious processes, script executions, or command sequences. This proactive approach enables the early detection of fileless malware. Thus, preventing it from establishing a foothold and minimizing potential damage. In doing so, monitoring can become an essential component of robust cybersecurity strategies.
Protecting Your Business Against Fileless Malware
Protecting against fileless malware requires a multi-faceted approach that combines robust cybersecurity practices with employee education. Here are the top practices for safeguarding systems:
- Advanced Endpoint Protection: Invest in advanced endpoint security solutions that employ heuristic analysis, behavior monitoring, and machine learning to detect and mitigate fileless malware. These tools can identify suspicious activities and block malicious scripts before they cause harm.
- Regular System Audits and Updates: Conduct regular system audits to identify vulnerabilities and weaknesses that fileless malware could exploit. Keep all software, including the operating system and applications, up to date with the latest security patches. This helps close known vulnerabilities that attackers might target.
- Employee Education: Employees should be educated about social engineering threats, as many fileless malware attacks begin with phishing emails or deceptive tactics. Train employees to recognize phishing attempts, avoid clicking on suspicious links or downloading unknown attachments, and report any unusual or unexpected requests.
Regular system audits and updates play a critical role in maintaining the security posture of an organization. These measures help patch known vulnerabilities and ensure that security controls are effective against evolving threats. Additionally, educating employees about social engineering threats empowers them to be vigilant and proactive in defending against fileless malware, making them an essential part of the overall security strategy.
Responding to a Fileless Malware Attack
If your business falls victim to a fileless malware attack, immediate action is crucial. First, isolate the affected systems to prevent the spread of the malware. This could mean disconnecting the infected computers from the network.
Next, engage a cybersecurity expert to help identify the extent of the breach. They can help determine which tools or scripts the malware used, such as PowerShell scripts or Windows Management Instrumentation (WMI). Understanding the attack’s specifics can guide the cleanup process and help prevent future breaches.
After identifying the malware, the next step is to remove it. This process can be complex, as fileless malware resides in the system’s memory or registry keys, not in a specific file. Specialized antivirus software or endpoint security solutions may be necessary to fully remove the threat.
Finally, after the threat is neutralized, assess the damage. Did the attackers gain access to sensitive data? If so, you may need to notify affected parties and take steps to mitigate potential harm.
Throughout this process, it’s important to document everything. This documentation can be invaluable for understanding how the breach occurred. Thus, informing a response to any regulatory inquiries, and planning preventative measures for the future.
Conclusion
In the ever-evolving world of cybersecurity, fileless malware poses a significant threat to small businesses. Understanding its workings, detecting its presence, and knowing how to respond to an attack are crucial steps in protecting your business. By staying informed and implementing robust endpoint security measures, you can safeguard your business against this stealthy cyber threat.
Remember, the key to effective cybersecurity is not just responding to threats, but proactively preparing for them. Stay vigilant, stay updated, and ensure your business remains a tough target for any cybercriminal.
Frequently Asked Questions
What is a fileless malware attack?
A fileless malware attack is a type of cyber attack where the malware operates within a computer’s memory. It hides by using legitimate tools and services within the system to carry out its malicious activities..
What is a real-world example of fileless malware?
Real-world examples of attacks include major ransomware outbreaks like Petya and WannaCry, which utilized fileless techniques in their kill chains..
What is the difference between file and fileless malware?
Unlike traditional file-based malware, this threat operates within a system’s memory or registry keys, making it harder to detect and remove.
How common is fileless malware?
Fileless malware has seen a substantial increase in recent years, with malicious PowerShell scripts, a key component of fileless malware attacks, experiencing a surge of attacks.
How can I protect my business from fileless malware?
Protecting your business from fileless malware involves keeping your operating system and applications updated, implementing robust endpoint security solutions, and educating employees about the risks of phishing emails and social engineering.
What are the signs of a fileless malware infection?
Signs of a fileless malware infection include unusual system behavior such as slow performance, frequent crashes, unauthorized access attempts, and unexpected network activity. Since fileless malware operates in memory, traditional antivirus programs may not detect it, making these behavioral indicators crucial for early detection.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!