
Endpoint security is no longer a luxury but a necessity for small businesses. Today, cyber threats are evolving rapidly and the stakes for protection have never been higher.
Why Endpoint Security is Crucial for Small Businesses
In today’s interconnected world, endpoint security for small business isn’t just an IT concern—it’s a business imperative. Small businesses, often perceived as soft targets by cybercriminals, are facing an unprecedented surge in cyber threats. Ransomware attacks can cripple operations overnight. Sophisticated phishing schemes can compromise sensitive data. In the face of all of this, the digital dangers are real and relentless.
But why is this surge happening? The digital transformation has opened doors to incredible opportunities for growth and efficiency. However, with every new device connected to a network, a potential entry point for cyber attackers emerges. Small businesses can have limited IT resources. Because of this, they often find it challenging to keep up with the ever-evolving threat landscape, making them particularly vulnerable.
Endpoint security steps in as the first line of defense. It goes beyond the traditional antivirus solutions. Endpoint security offers a holistic approach to protect every endpoint from potential threats. This is true whether the endpoint is a laptop, mobile device, or even a printer. For small businesses, this means not safeguarding their data. It also ensures uninterrupted operations. This maintains customer trust, andhelps to stay ahead in a competitive market.
In essence, as cyber threats are growing in complexity and frequency. Because of this, endpoint security for small businesses stands as the guardian. It ensures that the digital doors to potential threats remain firmly shut.
The answer lies in endpoint security for small business. But what is it, and why is it so important? Let’s dive in.
Understanding Endpoint Security: Beyond Traditional Antivirus
Endpoint security is often mistaken for just another antivirus solution, but it’s so much more. Traditional antivirus software focuses primarily on detecting and removing malicious software from individual devices. On the other hand, endpoint security offers a broader, more holistic approach to cyber protection.
At its core, endpoint security encompasses a suite of tools and technologies. These tools and technologies are designed to safeguard all endpoints or devices connected to a network. This includes not just computers and laptops, but also smartphones, tablets, and even Internet of Things (IoT) devices. As the name suggests, it’s about securing every ‘endpoint’ that could be a potential entry for cyber threats.
So, how does it differ from the traditional antivirus?
- Scope: While antivirus solutions are typically device-centric, endpoint security is network-centric. It monitors and manages the entire network, ensuring that all connected devices adhere to the set security protocols.
- Proactive Defense: Instead of just reacting to known threats like most antivirus software, endpoint security proactively monitors for suspicious activities, potentially stopping threats even before they manifest.
- Centralized Management: Endpoint security solutions often come with a centralized management console, allowing IT teams to deploy updates, monitor threats, and enforce policies across all devices seamlessly.
- Integration with Other Security Tools: Endpoint security can integrate with other security tools like firewalls, intrusion detection systems, and more, offering a layered defense strategy.
- Advanced Threat Intelligence: Modern endpoint security solutions are equipped with advanced threat intelligence capabilities, constantly updating themselves with the latest threat data, ensuring timely detection and response.
In a nutshell, traditional antivirus solutions offer a line of defense only against known malware. On the other hand, endpoint security provides a comprehensive shield. It guards against a wider range of threats and offers tools for both detection and prevention.
Traditional Antivirus vs Endpoint Security: A comparison
To further elucidate the distinction between traditional antivirus and endpoint security, let’s delve into a side-by-side comparison of their features. While traditional antivirus primarily focuses on known malware detection for individual devices, endpoint security offers a comprehensive, network-wide protection strategy. This encompasses proactive threat monitoring, centralized management, and integration with a myriad of other security tools. The table below encapsulates these differences. It paints a clearer picture of why endpoint security stands out as the superior choice for holistic cyber protection.
| Features | Traditional Antivirus | Endpoint Security |
|---|---|---|
| Scope | Device-centric | Network-centric |
| Defense Mechanism | Reactive | Proactive (monitors for suspicious activities) |
| Management | Individual Device | Centralized Management Console |
| Integration with Other Tools | Limited | Integrates with firewalls, intrusion detection systems, etc. |
| Threat Intelligence | Basic | Advanced (constantly updates with latest threat data) |
| Coverage | Computers and laptops | All endpoints (including mobile devices, IoT, etc.) |
| Response to Unknown Threats | Limited | Detects and responds to unknown threats |
Key Features of Modern Endpoint Security Solutions
In the evolving landscape of cyber threats, it’s imperative for businesses to be equipped with the most advanced and robust security tools. Modern endpoint security solutions have come a long way from their predecessors. These solutions offer a plethora of features tailored to combat the multifaceted challenges of today’s digital world. In this section, we’ll delve into a detailed breakdown of these essential features. Hopefully, shedding light on what makes a truly comprehensive endpoint security solution stand out from the rest.
Centralized Management: The Heart of Endpoint Security
The heart of any endpoint security system is the endpoint security console. But what is it, and why is it so important?
In the vast digital expanse of a modern business, devices range from desktops to mobile phones and even IoT gadgets. In this environment, managing security can seem like a Herculean task. Enter centralized management, the linchpin of modern endpoint security solutions.
Centralized management serves as the command center for all things security. Imagine having a bird’s-eye view of every device connected to your network, being able to monitor their status, deploy security updates, or even enforce security protocols—all from a single dashboard. This is the power of centralized management.
Here’s why it’s indispensable:
- Unified View: With devices often spread across different locations, a centralized system offers a unified view, making it easier to spot anomalies or potential threats.
- Efficient Updates: Deploying security patches or updates becomes a breeze. Instead of manually updating each device, updates can be rolled out simultaneously across the board.
- Consistent Policies: Ensuring consistent security policies across devices is crucial. Centralized management allows for uniform enforcement, ensuring no device is left vulnerable due to outdated or lax security settings.
- Real-time Monitoring: Instant alerts on suspicious activities, potential breaches, or even failed update deployments. Real-time monitoring ensures that threats are nipped in the bud.
- Ease of Use: For IT personnel, especially in small businesses with limited resources, a centralized system simplifies the otherwise complex task of managing security across myriad devices.
In essence, centralized management is not just a feature—it’s the backbone of endpoint security. It streamlines operations, enhances security posture, and most importantly, provides peace of mind. At the end you will know that every device, every endpoint, is under vigilant watch.
Real-Time Threat Detection and Response
In the blink of an eye, a cyber threat can infiltrate a network. Doing so, it can compromise data, and wreak havoc on a business’s operations. In this swift and relentless digital age, waiting for periodic security scans or manual threat assessments is no longer viable. The need of the hour is real-time threat detection and response.
So, why is real-time so crucial?
- Immediate Threat Identification: Cyber threats don’t wait. The moment a malicious entity tries to breach the system, real-time detection flags it, ensuring immediate action.
- Minimized Damage: The faster a threat is detected, the quicker it can be contained. This reduces potential damage, be it data loss or operational disruption.
- Adaptive Security Posture: Real-time solutions continuously learn from the threats they encounter. This means they adapt and evolve, offering enhanced protection against new and emerging threats.
- Enhanced User Confidence: Knowing that the system is always on the lookout boosts confidence among employees and stakeholders. It assures them that their data and operations are secure.
- Staying Ahead of Attackers: Cybercriminals are constantly innovating. Real-time detection ensures businesses stay one step ahead, preemptively countering malicious tactics.
In today’s world, cyber threats are not just frequent but also rapidly evolving. Thus, real-time threat detection and response isn’t just a feature—it’s a necessity. It embodies the proactive approach businesses must adopt. This approach will safeguard their digital assets in today’s fast-paced cyber threat landscape.
Protecting Diverse Operating Systems: Windows, Mac, Linux
In the diverse digital ecosystem of a modern business, it’s not uncommon to find a medley of operating systems coexisting. From the ubiquity of Windows to the design-centric Mac and the robust Linux, each OS brings its unique strengths to the table. But with diversity comes complexity, especially when it comes to security.
Why is it vital for endpoint security solutions to cater to all these operating systems?
- Unified Security Posture: A business’s security is only as strong as its weakest link. Ensuring consistent protection across all operating systems is paramount to maintaining a robust defense against threats.
- Tailored Threat Detection: Each operating system has its vulnerabilities and threat vectors. A comprehensive endpoint security solution recognizes these nuances, offering tailored protection for each OS.
- Ease of Management: For IT teams, managing security protocols for different operating systems can be a challenge. A solution that caters to all ensures streamlined operations and consistent policy enforcement.
- Cost Efficiency: Investing in multiple security solutions for different operating systems can be costly. A unified solution offers better cost efficiency and resource optimization.
- Future-Proofing: As businesses evolve, they might adopt new operating systems or diversify their existing ones. A versatile endpoint security solution ensures that businesses are future-proofed against such changes.
In conclusion, in a world where flexibility and adaptability are key, endpoint security solutions must reflect this ethos. Protecting diverse operating systems isn’t just about comprehensive coverage; it’s about ensuring seamless, efficient, and future-ready cyber defense for businesses.
The Role of Mobile Devices in Endpoint Security
In today’s digital age, mobile devices have become an integral part of the business ecosystem. From smartphones to tablets, these devices enable employees to work remotely. These devices allow employees to access company data on the go, and stay connected with colleagues and clients. The Pew Research Center’s Internet & American Life Project reveals that 85% of Americans own a smartphone, and about half own a tablet computer. With such widespread adoption, it’s no surprise that businesses, especially small ones, are integrating these devices into their daily operations.
Challenges with Protecting Mobile Devices using Endpoint Security
However, the increasing use of mobile devices in businesses brings unique challenges to the forefront:
- Diverse Operating Systems: Unlike traditional workstations that primarily run on Windows, mobile devices have a variety of operating systems, including Android, iOS, and others. This diversity requires endpoint security solutions that can cater to different OS architectures and their specific vulnerabilities.
- Lost or Stolen Devices: Mobile devices are more prone to being lost or stolen compared to desktop computers. A misplaced device can potentially give unauthorized individuals access to sensitive company data.
- Unsecured Networks: Employees often connect their mobile devices to public Wi-Fi networks, which may not be secure. This exposes the device and the data it contains to potential cyber threats.
- App Vulnerabilities: The plethora of apps available for mobile devices can be a double-edged sword. Many apps increase productivity. But they can also introduce vulnerabilities if they are not properly vetted or if they come from untrusted sources.
- Device Mismanagement: Without centralized management, it’s challenging to ensure that all mobile devices adhere to company security policies. Some employees might disable security features for convenience, leaving their devices unprotected.
In conclusion, while mobile devices offer numerous benefits to businesses, they also introduce a set of unique security challenges. It’s crucial for small business managers and IT personnel to recognize these challenges. Then, implement robust endpoint security measures tailored for mobile devices. This not only protects the company’s data but also ensures that employees can use their devices safely and efficiently.
Case Study: A Small Business’s Battle with Ransomware
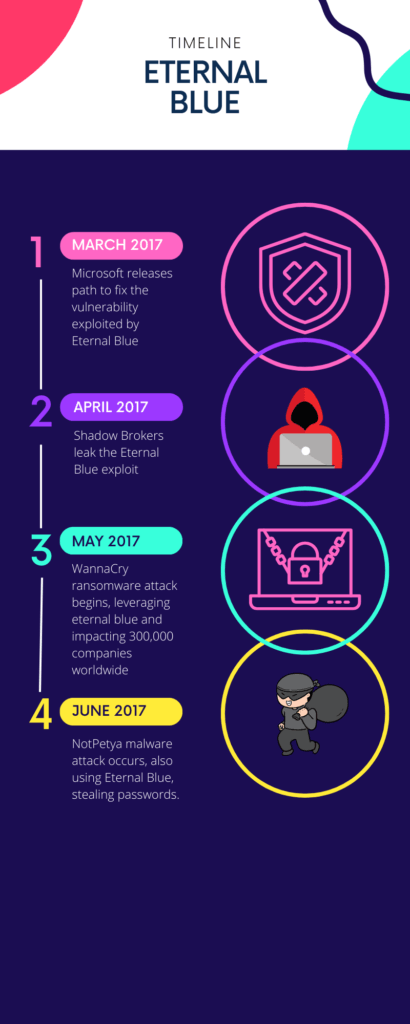
One of the most notorious vulnerabilities that wreaked havoc in recent years is EternalBlue. This malware affects Microsoft Server Message Block (SMB). This vulnerability was allegedly developed by the US National Security Agency (NSA). It was and was exposed to the public in April 2017 by the hacking group, the Shadow Brokers. The list of attacks facilitated by this vulnerability is extensive.
The most infamous exploit of EternalBlue was the WannaCry ransomware attack. This attack impacted over 300,000 companies globally, resulting in damages estimated around $4 billion. Just a month later, the malware NotPetya emerged, leveraging the same vulnerability to infiltrate systems, stealing passwords to gain control over networks.
But it wasn’t just about ransomware. Shortly after the WannaCry onslaught, a malware named Adylkuzz appeared, utilizing EternalBlue to inject commands into compromised computers. These commands were then employed to mine and extract cryptocurrencies.
Another ransomware, Bad Rabbit, shared many code elements with NotPetya. However, it exploited a different vulnerability, also developed by the NSA and also in SMB, named EternalRomance. This attack predominantly affected users in Eastern Europe and Russia.
The most alarming aspect of these attacks? Patches for these vulnerabilities were available months before the incidents occurred. Yet, many organizations struggled with applying the right patches or lacked patching policies, leaving these vulnerabilities unaddressed. Even today, EternalBlue continues to pose a threat to unpatched systems.
The lesson from these incidents is clear: the importance of timely patch management and the adoption of robust endpoint security solutions cannot be overstated.
Endpoint Security Solutions: Making the Right Choice
Endpoint security solutions have evolved significantly over the years. It adapted to the changing threat landscape and the diverse needs of businesses. These solutions now offer a plethora of features, from real-time threat detection to centralized management. But with so many options available, how does a small business make the right choice? For a comprehensive understanding and to make an informed decision, we recommend referring to our detailed article on Understanding Endpoint Security Solutions. It delves deeper into the importance of endpoint security, its key features, and guidelines on choosing the right solution for your business.
Evaluating Unknown Threats and Advanced Threat Intelligence
In the ever-evolving world of cybersecurity, new threats emerge daily. Traditional security solutions that rely solely on known threat databases can fall short in detecting these novel threats. This is where the importance of advanced threat intelligence comes into play. Modern endpoint security solutions are equipped with capabilities to evaluate and detect unknown threats, often referred to as “zero-day threats.” By analyzing patterns, behaviors, and employing advanced algorithms, these solutions can proactively identify and mitigate threats even before they are formally recognized. For small businesses, this means enhanced protection against the latest cyberattacks, ensuring that their data and operations remain uninterrupted.
The Role of Patch Management and Encryption
In the digital age, the security of business data is paramount. Two critical components that play an indispensable role in this are patch management and encryption.
Patch Management: Regular software updates, or patches, are essential to fix vulnerabilities that can be exploited by cybercriminals. A glaring example of the consequences of neglecting patch management is the EternalBlue vulnerability as described above. This vulnerability in Microsoft’s Server Message Block (SMB) protocol was exploited by the WannaCry ransomware attack, impacting over 300,000 companies worldwide and causing damages estimated around $4 billion. The most alarming aspect? Patches for this vulnerability were available months before the attack, but many organizations failed to apply them in time, leaving their systems exposed.
Encryption: Encryption converts data into a code to prevent unauthorized access. It ensures that even if cybercriminals manage to breach a system, the data they access remains unreadable and useless to them. Without encryption, sensitive business data, from financial records to customer information, is left vulnerable to theft and misuse.
In essence, while patch management ensures that potential entry points for cyberattacks are sealed off, encryption ensures that even if a breach occurs, the data remains protected. Together, they form a formidable defense strategy against the myriad of cyber threats businesses face today.
Conclusion: Securing Your Business with Endpoint Security
In today’s interconnected world, the digital landscape is rife with threats that evolve at an unprecedented pace. As businesses increasingly rely on technology for their operations, the importance of endpoint security becomes not just a technical necessity but a business imperative. It’s not merely about protecting data; it’s about safeguarding the very essence of a business, its reputation, and its relationship with customers.
Endpoint security is more than just a line of defense; it’s a proactive approach to ensure that businesses remain resilient in the face of cyber threats. By understanding its nuances and implementing robust solutions, businesses can not only defend against current threats but also anticipate and mitigate future ones.
As we move forward in this digital age, the call to action for businesses is clear: take proactive measures, prioritize endpoint security, and ensure that your business remains a fortress in the face of cyber adversaries. The future of your business may very well depend on the security choices you make today.
We’d love to hear your experiences and thoughts on endpoint security. Leave a comment below and explore other resources on our website for more insights into endpoint security for small businesses.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


