How to protect API Endpoints?
– To protect API endpoints, prioritize robust authentication and authorization mechanisms like OAuth.
– Employ API gateways for request routing and rate limiting, but don’t solely rely on them.
– Be vigilant against common threats like Man-in-the-Middle and DDoS attacks by using encrypted protocols and monitoring traffic.
– Regularly audit your APIs and implement features like Web Application Firewalls and JSON Web Tokens for added security. Stay updated on the latest threats and solutions to maintain a secure digital environment.
As businesses increasingly rely on technology to drive growth and efficiency, the security of these systems becomes paramount. One critical area that often goes overlooked is the security of API endpoints. APIs, or Application Programming Interfaces, act as bridges between different software applications, allowing them to communicate and share data. They play a pivotal role in modern business operations, from managing customer data to facilitating online transactions.
With the rise of cyber threats, it’s crucial for businesses, especially small ones, to understand how to protect these vital communication channels. This article aims to demystify the concept of API security, highlight its importance, and provide actionable steps for small business managers to ensure their API endpoints are secure. By the end of this read, you’ll have a clear understanding of API security risks and best practices to mitigate them. In a world where data breaches are becoming all too common, can you afford not to be informed?
What is API Security?
Application Programming Interfaces (APIs) have become the linchpins that connect diverse software systems, enabling them to share data and functionalities seamlessly. But what exactly is API security?
API security is the shield that protects these vital connectors from malicious threats aiming to steal data or disrupt services. It’s not just about blocking unauthorized access; it’s about ensuring that the data transmitted is safeguarded and that potential attacks, such as denial-of-service, injection, and man-in-the-middle attacks, are mitigated.
APIs act as intermediaries, setting the rules of communication between different software components. They’re like the unsung heroes in the background, ensuring that when you use a weather app, for instance, you get real-time data from an external source. The very nature of APIs, which often make them accessible through public networks, makes them attractive targets for cybercriminals.
Common threats to APIs include data breaches due to weak authentication measures, injection attacks, and Denial of Service (DoS) attacks that aim to overwhelm APIs with a flood of requests.
In essence, as the digital landscape evolves, ensuring robust API security isn’t just a technical necessity—it’s a business imperative.
Why is Knowing How to Protect API Endpoints Important?
In today’s digital age, businesses are increasingly shifting towards cloud computing and microservices. Cloud computing refers to the delivery of computing services over the internet, allowing businesses to scale, innovate, and reduce costs. On the other hand, microservices involve breaking down large software projects into smaller, modular units that communicate through APIs, offering agility and flexibility in software development.
APIs, acting as intermediaries, play a pivotal role in this landscape. They facilitate communication and data exchange between these modular units, ensuring seamless operation. If APIs are not secured properly, they can become the weakest link in the chain.
Imagine the consequences if an unauthorized person gains access to your business’s cloud applications through a vulnerable API. This could lead to:
- Data breaches, where sensitive information, such as customer details or financial records, is exposed.
- Financial losses, as cybercriminals exploit API vulnerabilities to commit fraud or theft.
- Reputation damage, where customers lose trust in your business due to security lapses.
Moreover, with the rise of cloud-native APIs, which are often exposed to the internet, the risk of attacks increases, making API security even more paramount.
Understanding the Biggest API Security Risks
In today’s interconnected digital world, APIs serve as the backbone for many business operations. However, with their increasing prominence comes a surge in potential security risks. From the stealthy Man in the Middle attacks to the overwhelming Distributed Denial of Service onslaughts, the threats are diverse and evolving. Moreover, the public nature of some APIs presents its own set of challenges, exposing critical business data to potential breaches. Dive into this section to unravel the most pressing API security risks and arm yourself with the knowledge to fortify your business against them.
The Diverse Nature of API Endpoints
APIs, or Application Programming Interfaces, serve as the backbone of modern digital interactions. Unlike traditional web servers that deliver entire web pages, APIs send specific data in response to requests. For instance, when you check the weather on an app, it’s an API fetching the data, not a web server presenting a full page.
This distinction brings unique security challenges. Web servers primarily focus on delivering content securely to web browsers. In contrast, APIs interact with multiple endpoints, from mobile apps to other servers, each posing potential security risks. Consider a scenario where a retail app uses an API to fetch product prices. If not secured, malicious actors could manipulate the API calls, leading to incorrect pricing or even data breaches.
Furthermore, the diverse nature of API endpoints means they’re exposed to a wider range of threats. For example, a web server might only need to guard against website defacement or DDoS attacks. An API, however, must also defend against unauthorized data access, man-in-the-middle attacks, and more.
Potential Threats to API Security
As businesses increasingly rely on APIs to streamline operations and enhance user experiences, they become attractive targets for cybercriminals.
Man-in-the-Middle (MITM) Attacks
Man-in-the-Middle attacks occur when malicious actors secretly intercept and relay communication between two parties. Essentially, they eavesdrop or even manipulate data being transferred. This type of attack is often triggered when users connect to insecure public Wi-Fi networks or fall victim to phishing schemes. Detection can be challenging, but one might notice unusual certificate warnings or unexpected application behaviors. To prevent MITM attacks, always use encrypted protocols like HTTPS, employ certificate pinning, and educate users about the risks of unsecured networks and the importance of validating digital certificates.
Distributed Denial of Service (DDoS) Attacks
DDoS attacks involve overwhelming an API with a flood of requests, rendering it unavailable. These attacks are triggered by multiple systems, often part of a botnet, simultaneously sending a massive number of requests. Monitoring traffic patterns can help in detecting unusual spikes in requests. Prevention involves implementing rate limiting, using DDoS protection services, and regularly monitoring traffic for anomalies.
Data Breaches
Data breaches result from unauthorized access to data, leading to its exposure. Often, weak security configurations or vulnerabilities in the API are the culprits. Regular security audits and monitoring access logs can help detect suspicious activities. To prevent data breaches, ensure robust authentication mechanisms, encrypt sensitive data, and conduct regular security assessments.
Injection Attacks
In injection attacks, malicious data is sent as input, tricking the API into executing unintended commands. These attacks are triggered when user inputs are not properly sanitized. Detecting them involves monitoring for unusual system behaviors or unexpected database queries. Prevention requires rigorous input validation, using parameterized queries, and employing security tools that scan for vulnerabilities.
Inadequate Rate Limiting
Without proper rate limiting, APIs can be bombarded with excessive requests, leading to overloads. This vulnerability is exploited by attackers sending rapid sequences of requests. Detection involves monitoring for unusually high request rates from single sources. Implementing strict rate limiting and using tools that monitor API traffic can prevent such attacks.
Broken Authentication
When API authentication mechanisms are flawed, attackers can impersonate legitimate users. This is often triggered by weak passwords or poorly implemented authentication processes. Monitoring access logs for unusual access patterns can help in detection. Employing multi-factor authentication and ensuring secure token management can prevent these attacks.
Exposure of Sensitive Data
APIs might unintentionally reveal sensitive data if not properly configured. This exposure can be triggered by misconfigurations or overlooked security settings. Regularly reviewing API responses can help detect unintentional data exposures. To prevent this, always minimize the data returned by APIs and employ strict access controls.
Rogue APIs
Rogue APIs, often undocumented or old, can be exploited by attackers. These vulnerabilities arise from overlooked or forgotten endpoints. Regularly auditing and documenting all APIs can help in detection. Decommissioning unused APIs and ensuring all endpoints are documented and monitored can prevent potential breaches.
Lack of Encryption
Transmitting data without encryption exposes it to eavesdropping. This vulnerability is often due to overlooked security configurations. Monitoring for unencrypted data transmissions can help detect this issue. Always use encrypted protocols like HTTPS and employ tools that enforce encryption to prevent such exposures.
API Phishing
API phishing involves creating fake API endpoints to capture data. These attacks are triggered when clients are deceived into interacting with malicious endpoints. Monitoring for unexpected or unusual API calls can help in detection. Educating developers about the risks and ensuring strict validation of API endpoints can prevent these attacks.
Delving into Security Best Practices to Protect API Endpoints
In today’s interconnected digital ecosystem, the safety of your data hinges on robust API security practices. As the backbone of modern software communication, APIs are both a boon and a potential vulnerability for businesses. But how do you ensure that this vital bridge between applications remains secure? This section unravels the intricacies of API best security practices, offering insights into features and strategies that can shield your business from potential cyber threats. From understanding the pivotal role of rate limiting to the nuances of authentication mechanisms, we’ll guide you through the labyrinth of API security. Moreover, the emphasis on continuous API discovery and inventorying underscores the dynamic nature of this domain. If you’re keen on fortifying your business’s digital defenses and staying a step ahead of cyber adversaries, this section is your roadmap.
Rate Limiting: A Shield Against Abuse.
Rate limiting serves as your first line of defense against API abuse. By restricting the number of API calls a user can make within a set time frame, you not only mitigate the risk of DDoS attacks but also ensure equitable API usage. There are various methods to implement rate limiting, such as user-level, IP-level, and service-level restrictions. Popular tools and libraries can assist in setting this up seamlessly. Monitoring is equally crucial; keeping an eye on usage patterns allows for timely adjustments to rate limits. For instance, if an e-commerce site limits a user to 100 product searches per minute, it can deter bots from overwhelming the system, thus maintaining a smooth user experience.
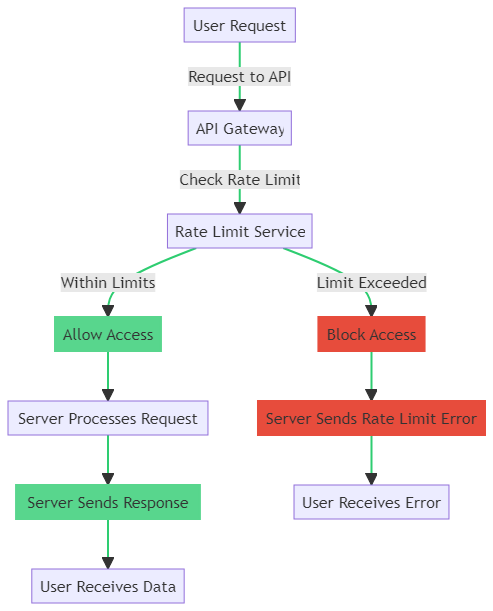
The flowchart above visualizes the journey of a user request as it encounters rate limiting. Here’s how it works:
- User Request: It all starts when a user sends a request to your API.
- API Gateway: The request first reaches the API Gateway, which acts as the doorman.
- Rate Limit Check: The API Gateway consults the Rate Limit Service to check if the user has exceeded their quota of requests.
- Decision Point:
- If the user is within the limits, the gateway allows the request to proceed.
- If the user has exceeded the limit, the gateway blocks the request.
- Server Response:
- For allowed requests, the server processes them and sends back the required data.
- For blocked requests, the server sends a rate limit error message.
- User Receives:
- A successful response with the data requested, or
- An error message indicating that the rate limit has been exceeded.
This flowchart helps in understanding the critical role rate limiting plays in API security and user experience. By implementing such a system, you ensure that your API’s resources are used judiciously, preventing abuse and maintaining service availability for all users.
API Keys
API keys are more than just random strings; they’re unique identifiers that authenticate users making API calls. Generating API keys through your service is the first step, but secure storage is equally important. Options like environment variables or secure key management services can be considered. Regular key rotation enhances security, making it harder for unauthorized users to gain access.
HTTPS: The Guardian of Data Integrity
In today’s digital age, HTTPS is non-negotiable for secure data transmission. It encrypts the data between the user and the server, thwarting any man-in-the-middle attacks. Implementing HTTPS involves obtaining and installing SSL/TLS certificates. For an added layer of security, consider implementing HTTP Strict Transport Security (HSTS), which enforces secure connections.
The Role of API Gateways
API gateways play a pivotal role in modern digital infrastructures. At its core, an API gateway acts as a gatekeeper, regulating API calls by ensuring they meet certain criteria before reaching their destination. This intermediary layer is responsible for request routing, composition, and rate limiting, making it an essential component in API security.
The importance of API gateways in security cannot be understated. They offer features like rate limiting, which prevents any single user or entity from overloading the system. Additionally, they handle authentication and authorization, ensuring that only valid users can access certain data or functionalities. For instance, in a banking app, an API gateway might ensure that only authenticated users can check their account balances or make transfers.
However, while API gateways offer a robust first line of defense, relying solely on them can be perilous. One significant limitation is their visibility and control over the entire API architecture. This means they might not detect misconfigured or rogue APIs, leaving them exposed to potential attackers. Moreover, they often can’t differentiate between human users and sophisticated bot activity. In a scenario where a business relies only on an API gateway for security, a sophisticated bot could potentially mimic human behavior, bypassing rate limits and accessing sensitive data.
Furthermore, while API gateways can handle a wide range of threats, they lack defense against advanced multi-vector DDoS attacks. Such attacks can overwhelm a system, causing service disruptions or even complete shutdowns.
Key Features to Protect Your API Endpoints
In the realm of digital business, ensuring the security of your API endpoints is paramount. As small business managers navigate the complexities of modern technology, understanding key protective features becomes essential. Here are some pivotal features to consider:
Authenticate and Authorize Mechanisms
Authentication and authorization are twin pillars in API security. While authentication confirms the identity of a user, authorization determines what actions they’re permitted to perform.
OAuth: The Protocol for Modern Web Security
OAuth is an open-standard authorization protocol that allows users to approve one application interacting with another on their behalf without giving away their password. It’s widely adopted for its flexibility and security, providing tokens instead of credentials and offering various levels of granularity for access.
OAuth in Action:
- Delegated Access: OAuth allows users to grant third-party applications limited access to their server resources without exposing their credentials. For instance, allowing a photo printing service access to your photo storage without the need to reveal your login details.
- Tokens Over Credentials: Instead of using credentials, OAuth uses access tokens provided by the authorization server. These tokens grant permissions to the client application to act on behalf of the user.
Enhancing API Security with OAuth:
- Scope Definition: OAuth enables the definition of scopes, which precisely outline the level of actions that third-party applications can perform.
- Revocable Access: Users can revoke the access of applications at any time, providing a flexible and user-centric approach to security.
Basic Authentication: The Simple Yet Robust Approach
Basic Authentication is a method for an HTTP user agent to provide a user name and password when making a request. It’s a part of the HTTP protocol and is supported by most browsers and server-side applications.
Basic Authentication Explained:
- Base64 Encoding: Credentials are encoded in Base64 and passed along with the request header. It’s simple to implement but should always be used in conjunction with HTTPS to ensure the encoded information is not intercepted in transit.
- Stateless Protocol: Basic Authentication is stateless; it does not require cookies or sessions. Each request must contain the credentials, making it straightforward but also necessitating caution with every request.
Securing Endpoints with Basic Authentication:
- Always Use HTTPS: To prevent credentials from being compromised, Basic Authentication should only be used over HTTPS.
- Password Management: Strong password policies and regular updates are critical to maintaining the integrity of Basic Authentication.
Continuous API Discovery and Inventorying
In a dynamic digital landscape, APIs evolve rapidly. Continuous API discovery and inventorying ensure you’re always aware of the APIs in use, their versions, and potential vulnerabilities. Think of it as a regular health check-up for your APIs, ensuring they remain in optimal condition and free from potential threats.
SOAP vs. REST API: A Brief Overview
Two dominant protocols have emerged: Simple Object Access Protocol (SOAP) and Representational State Transfer (REST). Both serve as communication methods, but they differ in design, functionality, and use cases.
While SOAP offers a more standardized and secure approach, it can be heavyweight due to its extensive XML formatting. REST, with its flexibility and use of JSON, is often faster and more suitable for mobile and web applications. For instance, if a financial institution is looking for a protocol with rigorous security standards for its transactions, SOAP might be the go-to. However, a startup aiming to develop a lightweight mobile app might opt for REST for its simplicity and speed.
In conclusion, the choice between SOAP and REST largely depends on the specific needs and use cases of the application in question.
SOAP: A Standardized Protocol
SOAP is known for its robustness and security features. It uses XML for message formatting and relies on other application layer protocols, often HTTP and SMTP, for message negotiation and transmission. One of SOAP’s standout features is its built-in error handling. If there’s a problem with a request, SOAP will return a standardized error message. This protocol also boasts the WS-Security standard, which deploys XML Encryption, XML Signature, and SAML tokens for transactional messaging security. Organizations requiring heightened security and compliance often lean towards SOAP.
REST: A Flexible Approach
REST, on the other hand, is an architectural style rather than a strict protocol. It employs HTTP for data retrieval and remote system operations, making it more straightforward and flexible than SOAP. RESTful APIs use standard HTTP methods, like GET, POST, and DELETE. They’re stateless, meaning each request from a client contains all the information needed for processing. Security in REST is ensured through SSL authentication and HTTPS support, providing a secure communication channel. Due to its simplicity and scalability, many modern web applications prefer REST.
Essential Security Measures for APIs
In the realm of API security, understanding and implementing essential measures is crucial for safeguarding your business’s data and operations.
JSON Web Tokens and OpenID Connect
JSON Web Tokens (JWT) and OpenID Connect play pivotal roles in ensuring secure data transmission. JWT is a compact, URL-safe means of representing claims to be transferred between two parties. It’s widely used for authentication and authorization purposes. On the other hand, OpenID Connect is a simple identity layer built on top of the OAuth 2.0 protocol, allowing clients to verify users’ identities based on authentication performed by an authorization server.
Web Application Firewalls (WAF)
A Web Application Firewall (WAF) acts as a shield between your API server and the data connection, analyzing and filtering out malicious web traffic. By utilizing a WAF, businesses can prevent SQL injection, cross-site scripting, and other web-based threats. For instance, an e-commerce site can use a WAF to block suspicious traffic patterns during online transactions. Similarly, a content management system might deploy a WAF to prevent unauthorized content changes[4].
Access Control and API Keys
Implementing robust access control measures ensures that only authorized individuals can access specific API endpoints. This involves setting permissions based on roles or user types. API keys, on the other hand, are like digital passwords, allowing applications to communicate with each other securely. They ensure that the API requests are coming from a trusted source.
Addressing Threats
Rogue APIs and sophisticated bot activities are emerging threats in the digital landscape. Rogue APIs, unauthorized API endpoints, can expose sensitive data if not detected. Sophisticated bot activity, on the other hand, can mimic human behavior, making traditional detection methods ineffective. Businesses must continuously monitor their API traffic patterns and employ advanced threat detection mechanisms to counter these risks.
Conclusion
Embracing a Proactive Approach
Small businesses, often seen as easy targets by cybercriminals, must prioritize protecting their API endpoints. This isn’t just about safeguarding data; it’s about preserving trust, ensuring uninterrupted operations, and maintaining a competitive edge in the market.
Staying updated with the latest threats is not optional—it’s a necessity. The cyber threat landscape is dynamic, with new vulnerabilities emerging daily. By keeping abreast of the latest security solutions and potential risks, businesses can preemptively address vulnerabilities before they become gaping holes.
Moreover, leveraging educational resources and industry updates can empower businesses to make informed decisions. Remember, in the realm of cybersecurity, knowledge truly is power. By adopting a proactive stance, businesses can not only defend against threats but also pave the way for growth and innovation in a secure digital environment.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
