Understanding Endpoint Encryption: The First Line of Data Defense
Safeguarding sensitive information has become critical for businesses of all sizes. At the forefront of this protective shield is endpoint encryption. This is a critical component in a robust security strategy. But what exactly is endpoint encryption, and how does it function as a cornerstone in safeguarding your business’s precious data? Let’s start by diving into the concept of encryption.
Key Takeaways:
- Endpoint encryption protects sensitive data on devices by encoding it, preventing unauthorized access.
- Essential for compliance with data protection regulations, safeguarding business and customer information.
- Functions seamlessly in the background, requiring minimal user intervention.
- Provides robust security even if a device is lost or stolen, ensuring data remains inaccessible.
- Integral to a comprehensive cybersecurity strategy, enhancing overall data protection efforts.
The Necessity of Encryption in Modern Business
But what exactly is endpoint encryption, and how does it function as a cornerstone in safeguarding your business’s precious data? Endpoint encryption is the process of encoding or scrambling data stored on various devices. People often refer to these devices as ‘endpoints’. They include such devices as laptops, smartphones, and USB drives. This encryption ensures that the data remains inaccessible to unauthorized individuals. If someone loses or steals a device, the encrypted data on it remains secure. Decrypting it without the correct key is an arduous, if not impossible, task. This level of security is crucial. This is especially true considering the portable nature of these devices which makes them vulnerable to theft or loss.
Endpoint encryption works by using algorithms to transform readable data into an unreadable format unless you have a specific key or code. This key is the only way to decrypt the data and access the original, readable information. The beauty of endpoint encryption lies in its simplicity and effectiveness. Endpoint encryption doesn’t require the end user to take any complicated steps. Once set up to encrypt the data, the encryption runs seamlessly in the background, providing continuous protection.
The significance of endpoint encryption extends beyond just protecting data from external threats. It also plays a vital role in compliance with data protection regulations. Many industries mandate the encryption of sensitive data to prevent unauthorized access. Thus, making endpoint encryption not just a security measure, but also a compliance necessity.
Glossary of Encryption Terms
Encryption, while a powerful tool for data protection, comes with its own set of jargon that can be daunting for those unfamiliar with the subject. To make the topic more approachable and to ensure clarity, we’ve compiled a glossary of key encryption terms. This glossary serves as a quick reference guide, helping readers understand the fundamental concepts associated with encryption.

Refer to the infographic for a visual representation of the key terms associated with encryption.
Key Terms:
- Encryption: The process of converting data into a code to prevent unauthorized access.
- Decryption: The process of converting encrypted data back to its original form.
- Cipher: An algorithm used for performing encryption or decryption.
- Public Key: A cryptographic key that can be publicly shared and is used to encrypt data.
- Private Key: A secret cryptographic key used for decryption. Paired with a public key in asymmetric encryption.
- Symmetric Encryption: Encryption where the same key is used for both encryption and decryption.
- Asymmetric Encryption: Encryption where different keys (public and private) are used for encryption and decryption respectively.
- Key Rotation: The practice of periodically changing encryption keys to enhance security.
Understanding these terms is crucial for anyone looking to delve deeper into the world of encryption and cybersecurity. Whether you’re a small business manager or an IT professional, having a grasp of these fundamental concepts will empower you to make informed decisions regarding data protection and security.
Why Endpoint Encryption Matters
As 2023 unfolds, the digital world continues to evolve at a breathtaking pace. This evolution, however, brings with it an escalated landscape of cyber threats, particularly targeting small businesses. Many perceive small businesses as softer targets due to their limited cybersecurity defenses. They are increasingly vulnerable to sophisticated cybercriminals who exploit vulnerabilities to breach systems.
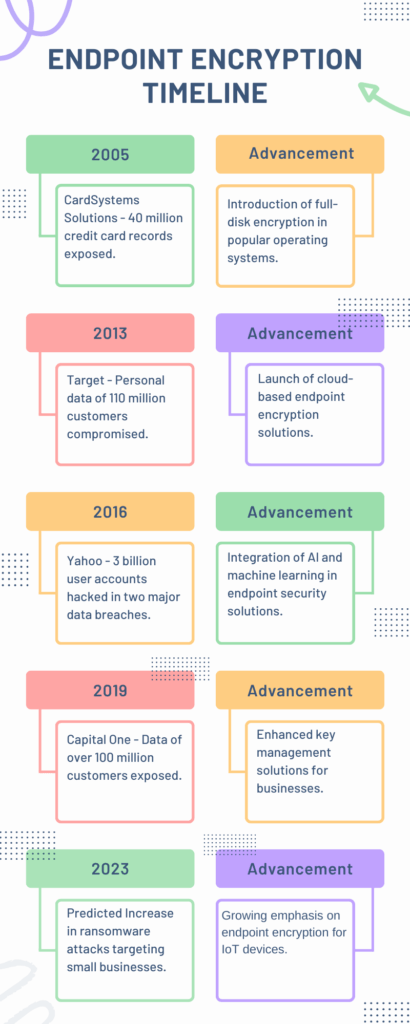
A Decade of Data Breaches: Lessons Learned
The infographic below highlights major data breaches over the years. Starting from the CardSystems Solutions incident in 2005, affecting 40 million credit card records. Continuing to the staggering Yahoo breach in 2016 that compromised 3 billion user accounts. These breaches underscore the growing scale and impact of cyber incidents. Predictions for 2023 suggest an uptick in ransomware attacks. Small businesses being the prime targets due to their typically weaker endpoint security.
The Rising Significance of Encryption in Data Protection
In the face of these daunting challenges, encryption emerges as a critical line of defense. For instance, consider the 2017 Equifax breach that exposed the personal information of 147 million people. If this data had been encrypted, the hackers would have encountered a significant barrier, likely rendering the stolen data useless.
The Capital One breach in 2019 similarly exposed over 100 million customers’ data. This highlights the urgent need for robust endpoint encryption. Endpoint encryption is not just a protective measure. Endpoint encryption is a necessity to protect data stored on endpoints in an era where data breaches are inevitable. It acts like a resilient fortress, securing encrypted data even when other defenses fail. In 2023, as the cyber threat landscape continues to evolve, the importance of endpoint encryption becomes increasingly clear. It’s an indispensable tool. Encryption is especially crucial for small businesses seeking to safeguard sensitive corporate data and protect themselves from the catastrophic impacts of data breaches.
As we progress through 2023, the role of endpoint encryption in data security becomes ever more critical. For small businesses looking to thrive in this digital age, integrating strong endpoint encryption strategies into their security framework is not just important—it’s essential. It’s a key component in their defense against the rising tide of digital threats.
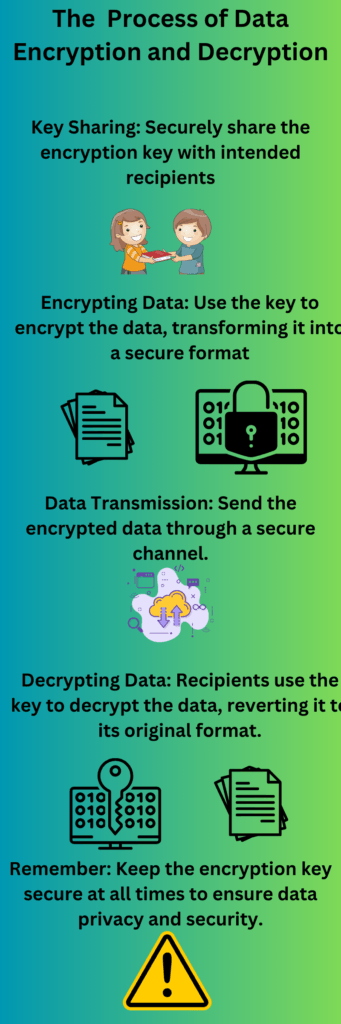
The Mechanics of Endpoint Encryption: How It Works
Delving into the mechanics of endpoint encryption illuminates how this technology not only protects data but also forms an integral part of your business’s security strategy. Understanding this process is key to appreciating the full spectrum of endpoint encryption’s capabilities and its critical role in data security.
Encrypting Data: The Core Process
Endpoint encryption starts with the fundamental process of encrypting, or encoding, the data stored on an endpoint device. This includes everything from text documents and emails to photos and software-based encryption solutions. Encrypting data transforms it into a format unreadable to anyone without the encryption key. This key, a string of characters, acts as a cipher, unlocking the data and converting it back into its original, readable form.
Encryption can occur in various forms, including full-disk encryption (FDE) and file-level encryption. Full-disk encryption secures all data on the hard drive, encrypting the entire disk. This means encrypting everything from the operating system to the applications and all files. On the other hand, file-level encryption allows more control by encrypting specific files or folders.
Decrypting Data: Accessing Encrypted Information
The counterpart to encryption is decryption. Decrypting data is the process of transforming encrypted, unreadable data back into its original form. Achieving this requires using one key to encrypt and a corresponding key to decrypt. The organization’s IT department or sometimes the user themselves typically control and manage these keys. Without this key, individuals cannot access the data, making encryption a robust barrier against unauthorized access.
Key Components of Endpoint Encryption
At the heart of endpoint encryption are its essential components: encryption algorithms, keys, and their management.
- Encryption Algorithms: Complex mathematical formulas are used to encrypt and decrypt data. Examples include the Advanced Encryption Standard (AES), a federal information processing standard known widely for its strength and efficiency. The choice of encryption algorithm plays a crucial role in the strength of the encryption.
- Encryption Keys: These are the ‘passwords’ that lock and unlock encrypted data. Often measured in bits, the strength of an encryption key increases with its length—the longer the key, the more secure the encryption. Key management, encompassing the generation, distribution, storage, and destruction of keys, plays a vital role in endpoint encryption.
- Key Management: Effective key management is essential for maintaining the security of encrypted data. This includes not only the secure generation and storage of keys but also their timely revocation and replacement. Poor key management can undermine the effectiveness of an encryption solution, making it a critical focus for businesses implementing endpoint encryption.
Understanding these components and their interplay is crucial for any business considering deploying endpoint encryption as part of its data security strategy. By grasping how encryption and decryption work, along with the critical role of encryption algorithms and keys, businesses can make more informed decisions about their endpoint security solutions.
The Role of Encryption Algorithms in Data Security
Encryption algorithms are the backbone of endpoint encryption, serving as the mathematical instructions that transform plain data into an encrypted, secure format. Understanding the variety and significance of these algorithms is essential for comprehending their role in data security.
Advanced Encryption Standard (AES)
Widely regarded as one of the most secure encryption algorithms, AES is a symmetric key algorithm commonly used in various security protocols and systems. It’s known for its efficiency in both software and hardware implementations and is often the first choice for encrypting data on endpoints. AES can use key sizes of 128, 192, or 256 bits, with Advanced Encryption Standard-256 being the most robust option, providing strong protection against brute force attacks.
Triple Data Encryption Standard (TripleDES)
This algorithm is an evolution of the original Data Encryption Standard (DES). TripleDES applies the DES cipher algorithm three times to each data block, significantly increasing the security over the original DES. It’s more secure than DES but slower than AES, making it less favorable for some modern applications but still relevant in certain environments.
RSA (Rivest-Shamir-Adleman)
RSA is a widely used asymmetric encryption algorithm, particularly important for secure data transmission. Unlike symmetric algorithms like AES, RSA uses two keys – a public key for encryption and a private key for decryption. This feature makes RSA ideal for scenarios where secure key exchange is challenging.
Blowfish and Twofish
Blowfish is a symmetric block cipher that divides data into blocks and encrypts them individually. It’s known for its speed and effectiveness, particularly in software applications. Twofish, a successor to Blowfish, is also a symmetric block cipher but with additional complexity, offering a higher level of security.
Each of these algorithms plays a distinct role in data security. The algorithms used to encrypt data depend on various factors such as the nature of the data, the required level of security, and the operational environment. For instance, AES might be preferred for its balance of speed and security for endpoint encryption, while RSA might be chosen for secure communications.
In the context of endpoint encryption, the right algorithm ensures that sensitive data, whether at rest on a device or in transit from one endpoint to another, is protected against unauthorized access. The robustness of these algorithms against modern cryptographic attacks makes them a key defense against data theft and loss, solidifying their role as pillars of data security in today’s digital world.
Types of Endpoint Encryption: Full-Disk vs. File Encryption
Endpoint encryption can be broadly categorized into two main types: full-disk encryption and file encryption. Both play pivotal roles in securing data but differ in their approach and application. Understanding these differences is crucial for businesses to choose the right encryption solution that aligns with their security needs and operational practices.
| Feature | Full-Disk Encryption (FDE) | File Encryption |
|---|---|---|
| Scope of Encryption | Encrypts the entire hard drive, including the operating system, applications, and all files. | Encrypts specific files or folders, allowing for targeted protection. |
| Method of Protection | Protects all data on the drive automatically upon booting the device. | Protects individual files/folders, even when the device is in use. |
| Key Management | Typically uses a single key to encrypt the entire drive. | May use different keys for different files or folders for enhanced security. |
| Performance Impact | Can slow down the system during the initial encryption process and at boot time. | Minimal impact on system performance as it only encrypts selected files/folders. |
| Access Control | Requires authentication (e.g., password) at startup to decrypt the entire drive. | Allows for more granular control over who can access specific data. |
| Ease of Sharing Data | More challenging to share specific data securely as the entire disk is encrypted. | Easier to share encrypted files/folders individually with intended recipients. |
| Best Use Cases | Ideal for devices with a mixture of sensitive and non-sensitive data. | Best for scenarios where only certain data requires high-level security. |
| Recovery Options | If key is lost, recovering data can be challenging as the entire drive is encrypted. | Loss of key affects only the encrypted files/folders, not the entire system. |
| Compliance and Regulations | Often preferred or required by certain regulations for comprehensive data protection. | May be used to meet specific compliance needs for protecting particular data types. |
Full-Disk Encryption: An Overview
Full-disk encryption (FDE) or drive encryption is a method of encrypting the entire disk of a device. This means that all data stored on the disk, including the operating system, applications, and personal files, are encrypted. The primary advantage of full disk encryption is its comprehensiveness; it ensures that every bit of data on the disk is secured. When a device is powered on, the user must provide the correct encryption key (typically in the form of a password) to boot and locate the encryption driver to unlock and decrypt the drive. This process ensures that if the device is lost or stolen, the data remains inaccessible without the key.
FDE is most effective in scenarios where the entire drive needs protection, such as in laptops or external hard drives that might contain a mix of sensitive and non-sensitive data. It’s also a key defense strategy for organizations that require encryption for compliance reasons. However, one limitation of full-disk encryption is that it only protects data at rest. Once the device is authenticated and unlocked, the encryption does not protect data from threats that bypass user authentication.
File Encryption: Securing Data at the File Level
File encryption, on the other hand, offers a more targeted approach by encrypting individual files or folders. Unlike full-disk encryption, which encrypts everything on the drive, file encryption allows users to selectively protect specific files and folders. This means that only the encrypted files require decryption for access. Each file can be done independently of the others. File encryption is particularly useful when dealing with highly sensitive information that needs to be secured separately from other data on the device.
One of the key advantages of file encryption is its flexibility. It allows for the secure sharing of encrypted files, as each file or folder can be encrypted with a different key. This feature is especially beneficial in collaborative environments where sensitive data needs to be transmitted or shared securely. File encryption is also useful when certain types of data require higher levels of security or different encryption standards.
Each type of encryption—full-disk and file—has its own set of use cases and benefits. Full-disk encryption offers a broad, comprehensive security solution ideal for devices containing a mixture of sensitive and non-sensitive data. File encryption provides targeted security for specific data sets, offering flexibility and control over how data is secured. The choice between the two should be based on the specific security needs, compliance requirements, and operational practices of the organization.
Implementing Endpoint Encryption Strategies in Your Business
Implementing an endpoint encryption strategy is a crucial step in fortifying your business’s data security. This process involves several actionable steps that ensure the encryption is not only effective but also aligns with your business operations and security objectives.
- Assess Your Data Security Needs: Begin by evaluating what data needs protection. Identify the sensitive or confidential data stored on various endpoints, like laptops, mobile devices, and removable media.
- Choose the Right Type of Encryption: Decide between full-disk encryption and file encryption based on your assessment and the specific data you want to encrypt. Consider using full-disk encryption for devices with a mix of sensitive and non-sensitive data, and file encryption for highly sensitive or specific data sets.
- Select an Encryption Solution: Choose an encryption software or tool that offers strong encryption and suits your business needs. Consider factors like ease of use, compatibility with existing systems, and the strength of encryption offered.
- Develop an Implementation Plan: Create a plan for deploying the encryption solution across your organization. This should include a timeline, resource allocation, and a process for addressing potential challenges.
- Train Your Staff: Educate your employees about the new encryption measures. Ensure they understand the importance of encryption and how to use the technology correctly.
- Monitor and Maintain: Continuously monitor the encryption solution for effectiveness and compliance with your organization’s policies. Regularly update the software to protect against new threats.

Best Practices for Managing Endpoint Encryption
Once you have implemented endpoint encryption, managing it effectively is crucial for maintaining the integrity and security of your encrypted data. Here are some best practices:
- Regularly Update Encryption Software: Keep your encryption software up-to-date to ensure it remains effective against evolving cyber threats.
- Effective Key Management: Securely manage the encryption keys. This includes secure generation, storage, and destruction of keys, and ensuring only authorized personnel have access to them.
- Enforce Strong Password Policies: Use strong, complex passwords for decrypting devices. Educate employees on creating and maintaining strong passwords.
- Backup Encrypted Data: Regularly backup encrypted data to prevent data loss. Ensure backups are also encrypted for maximum security.
- Policy Enforcement and Compliance: Develop and enforce robust encryption policies regarding the use and management of encrypted devices, ensuring comprehensive coverage and consistency in your security approach.
- Regular Audits and Reviews: Conduct regular audits to ensure the encryption strategy is functioning as intended. Review policies and practices periodically and update them as needed.
By following these actionable steps and best practices, businesses can effectively integrate and manage endpoint encryption in their security strategy, ensuring robust protection of sensitive data against unauthorized access and cyber threats.
The Importance of Endpoint Encryption in a Comprehensive Security Strategy
In today’s digital age, where data breaches and cyber threats are increasingly common, endpoint encryption emerges as a vital component in a comprehensive security strategy. Its role extends far beyond just encrypting data; it fortifies the overall security posture of a business, safeguarding it against a myriad of cyber threats.
Endpoint encryption acts as a critical layer of defense to protect the data, securing sensitive information stored on various devices, including laptops, smartphones, and USB drives. It’s particularly crucial in scenarios where devices might be lost or stolen, ensuring that sensitive information remains secure and inaccessible to unauthorized individuals. Moreover, in an era where data privacy regulations are becoming more stringent, endpoint encryption helps businesses comply with legal requirements, thus avoiding hefty fines and reputational damage.
Beyond its direct benefits, endpoint encryption also enhances the overall effectiveness of a business’s security infrastructure. It serves as a key defense against data theft and loss, a concern that has grown with the increase in remote work and mobile device usage, enhancing overall endpoint protection. By encrypting data at the endpoint, businesses ensure that their most vulnerable points are secured against unauthorized access, making it a foundational component of any robust data security strategy.
How Endpoint Encryption Complements Other Security Measures
Encryption protects data even when used in conjunction with other security measures. It forms part of a multi-layered security approach that includes various tools and practices, each addressing different aspects of cybersecurity.
- Firewalls: While firewalls protect against unauthorized access to a network, endpoint encryption secures the data on devices within that network. This combination ensures both internal and external security barriers.
- Antivirus Software: Antivirus software protects against malware and viruses, while endpoint encryption safeguards the data those malicious entities might target. Together, they provide comprehensive protection against various forms of cyberattacks.
- Secure Access Protocols: Protocols like VPNs (Virtual Private Networks) secure data transmission across networks. Endpoint encryption complements this by securing the data on devices, ensuring end-to-end data protection.
- Regular Software Updates and Patch Management: Keeping software up-to-date helps protect against vulnerabilities that could be exploited by cybercriminals. Endpoint encryption adds an extra layer of security, ensuring that even if a breach occurs, the data remains protected.
- User Authentication and Access Controls: Strong user authentication methods, like multi-factor authentication, control who can access the network and the data within it. Endpoint encryption ensures that even if unauthorized access occurs, the data remains unreadable and secure.
By integrating endpoint encryption into the broader security infrastructure, businesses can create a resilient shield against a wide range of cyber threats. It’s not just an isolated tool but a significant component of a holistic security strategy, essential for protecting sensitive data in today’s interconnected world.
Conclusion: Why Your Business Should Use Endpoint Encryption
In today’s digital age, where data breaches and cyber threats are increasingly common, endpoint encryption emerges as a vital component in a comprehensive security strategy. Its role extends far beyond just encrypting data; it fortifies the overall security posture of a business, safeguarding it against a myriad of cyber threats.
Strengthening Business Defenses with Endpoint Encryption
Endpoint encryption acts as a critical layer of defense, protecting sensitive data stored on various devices, from laptops and smartphones to USB drives and other removable media. By encrypting this data, businesses ensure that even if a device falls into the wrong hands, the information it holds remains secure and inaccessible. This level of security is vital, not just for safeguarding business secrets and customer data but also for complying with growing data protection regulations.
Whether dealing with structured or unstructured data, endpoint encryption enhances the overall effectiveness of a business’s security infrastructure. It serves as a key defense against data theft and loss, a concern that has grown with the increase in remote work and mobile device usage. By encrypting data at the endpoint, businesses ensure that their most vulnerable points are secured against unauthorized access, making it a foundational component of any robust data security strategy.
For businesses of all sizes, integrating endpoint encryption into their security strategy is no longer an option but a necessity. It’s a proactive step towards ensuring that their data, one of their most valuable assets, is well-protected. Whether you’re a small startup or a large corporation, the message is clear: securing your endpoints is a critical component of safeguarding your business’s future.
In conclusion, we encourage all businesses to consider the critical role of endpoint encryption and the strategic use of encryption in their security measures. By adopting this powerful tool, you’re not just protecting data; you’re fortifying your entire business against the growing tide of digital threats. In the journey towards a secure and resilient digital presence, endpoint encryption is an indispensable ally.
Frequently Asked Questions
What is endpoint encryption?
Endpoint encryption encodes data on devices to prevent unauthorized access, ensuring data security..
Why is endpoint encryption important for businesses?
It protects sensitive data from unauthorized access and helps comply with data protection regulations.
How does endpoint encryption work?
It uses algorithms to transform readable data into an unreadable format, accessible only with a specific decryption key.
What are the benefits of using endpoint encryption?
It secures data on portable devices, prevents unauthorized access, and ensures compliance with regulations.
Can endpoint encryption protect against data breaches?
Yes, by rendering stolen data unreadable without the decryption key, it mitigates the impact of data breaches.
What are the key types of endpoint encryption?
Full-disk encryption secures all data on a device, while file encryption targets specific files or folders for protection.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!

