Today, patch management best practices are crucial. They are critical for safeguarding your cybersecurity infrastructure. Cyber threats are evolving. As such, staying updated with the latest patches can mean the difference between a secure network and a disastrous data breach.
This guide aims to unlock the essentials of effective patch management. That will help you with the complexities of keeping your systems secure.
Why Patch Management is Crucial for Cybersecurity
Patch management plays a pivotal role in fortifying cybersecurity . It requires measures for both enterprises and individual users. It serves as the first line of defense against a myriad of vulnerabilities that can compromise system integrity. By regularly updating software and fixing security loopholes, patch management helps in thwarting unauthorized access, data breaches, and cyberattacks.
Today, cyber threats are increasingly sophisticated. The absence of timely patches can leave systems susceptible to exploits. These vulnerabilities can lead to unauthorized data access, financial loss, and even reputational damage. Therefore, patch management is more than a best practice.
The Evolution of Patch Management: A Brief History
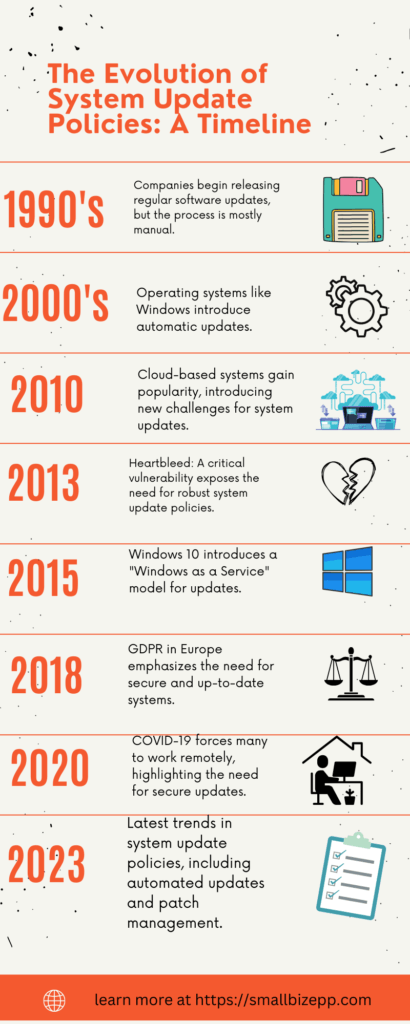
Understanding the history of patch management provides valuable insights into its current significance. Our infographic timeline captures key milestones that have shaped this crucial aspect of cybersecurity.
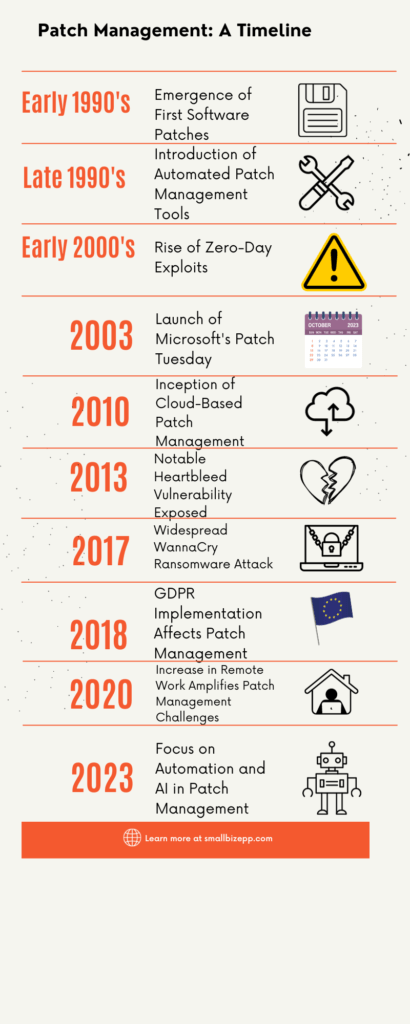
Early 1990s: The Birth of Software Patches 💾
The early ’90s marked the emergence of the first software patches. These initial fixes laid the foundation for what would become a critical cybersecurity practice.
Late 1990s: Automated Tools Take Over 🛠️
By the late ’90s, automated patch management tools started to appear, streamlining the process and making it more efficient.
Early 2000s: The Rise of Zero-Day Exploits ⚠️
The early 2000s saw a surge in zero-day exploits, vulnerabilities exploited before a patch becomes available, highlighting the urgent need for timely updates.
2003: Microsoft’s Patch Tuesday 📅
In 2003, Microsoft introduced its “Patch Tuesday,” a monthly security update program that has since become an industry standard.
2010: Cloud-Based Solutions Emerge ☁️
Around 2010, cloud-based patch management solutions started to gain traction, offering scalability and remote management capabilities.
2013: Heartbleed Exposes Risks 💔
The Heartbleed vulnerability exposed in 2013 served as a wake-up call, emphasizing the critical importance of timely patching.
2017: The WannaCry Wake-Up Call 🔒
The WannaCry ransomware attack in 2017 further underscored the need for effective patch management to secure systems against such large-scale attacks.
2018: GDPR Changes the Game 🇪🇺
The implementation of the General Data Protection Regulation (GDPR) in 2018 had a significant impact on patch management, especially concerning data protection.
2020: Remote Work Challenges 🏠
The COVID-19 pandemic led to a surge in remote work, amplifying the challenges associated with patch management.
2023: The Age of Automation and AI 🤖
Today, the focus is increasingly shifting towards automation and AI to enhance patch management practices.
Patch Management vs. Vulnerability Management: Know the Difference
It is true that both patch management and vulnerability management aim to fortify cybersecurity. However, they are distinct practices with unique objectives and processes. Our infographic timeline serves as a backdrop to understand how patch management has evolved. Still, go deeper into how patch management differs from vulnerability management.
Patch Management 🛠️
Patch management focuses on identifying, acquiring, and installing updates or ‘patches’ for software and systems. Its primary goal is to fix security loopholes and improve functionality. It’s a reactive approach, often triggered by the discovery of vulnerabilities or the release of new updates.
Vulnerability Management ⚠️
On the other hand, vulnerability management is a proactive, ongoing process that involves identifying, classifying, and mitigating security vulnerabilities. It goes beyond just applying patches to include risk assessments and long-term planning.
Key Differences 🔑
- Scope: Patch management is a subset of vulnerability management. While patch management deals with applying fixes, vulnerability management involves a broader range of activities, including risk assessment and mitigation strategies.
- Approach: Patch management is generally reactive, responding to known issues. Vulnerability management is proactive, seeking to identify potential weaknesses before they can be exploited.
- Tools: Different sets of tools are used for each. Patch management tools focus on distributing and installing updates, whereas vulnerability management tools are designed for scanning and assessing potential risks.
- Timeframe: Patch management is often event-driven, occurring in response to the discovery of a specific vulnerability or the release of a new update. Vulnerability management is an ongoing process that requires continuous monitoring and assessment.
The 8-Step Guide to Effective Patch Management
Implementing a robust patch management strategy is crucial for maintaining a secure and efficient network. Our flowchart provides a visual guide to the process, but let’s delve deeper into each step for a comprehensive understanding.
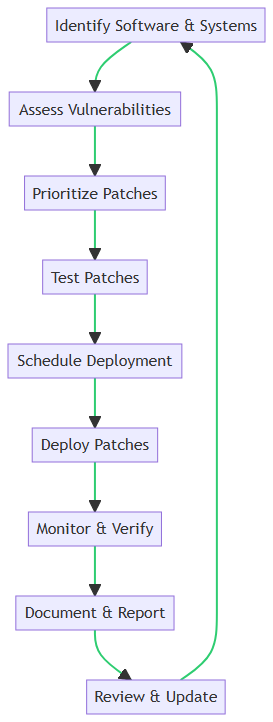
1. Identify Software & Systems 📋
Start by creating an inventory of all software, systems, and applications in your network. Knowing what you have is the first step in knowing what needs to be patched.
2. Assess Vulnerabilities 🔍
Use vulnerability assessment tools to scan your network for known security issues. This will help you understand the vulnerabilities that exist within your software and systems.
3. Prioritize Patches ⚖️
Not all patches are created equal. Prioritize them based on the severity of the vulnerability and the importance of the affected system. Critical systems and high-risk vulnerabilities should be addressed first.
4. Test Patches 🧪
Before deploying any patches, test them in a controlled environment. This ensures that they won’t cause additional issues like system crashes or application failures.
5. Schedule Deployment 🗓️
Plan the deployment of patches carefully to minimize disruption. This could mean deploying patches during off-hours or scheduling them in batches.
6. Deploy Patches 🚀
Once tested and scheduled, proceed with the deployment. Use automated tools to roll out patches across multiple systems for efficiency.
7. Monitor & Verify 🖥️
After deployment, monitor the systems for any issues. Verify that the patches have been applied successfully and are functioning as intended.
8. Document & Report 📊
Maintain detailed records of all patching activities. Document what was patched, when, and any issues that arose. This is crucial for compliance and future audits.
9. Review & Update 🔄
Regularly review your patch management process. Update it as needed to adapt to new vulnerabilities and changes in your network environment.
Asset Management: The Foundation
Asset management serves as the bedrock of any effective patch management strategy. Without a comprehensive understanding of the assets within your network, it’s nearly impossible to implement a robust patching process. Let’s explore why asset management is foundational.
Why It’s Crucial 🌟
Asset management allows you to identify all hardware and software components in your network. This identification is essential for assessing vulnerabilities and prioritizing patches effectively.
Inventory Management 📦
Maintaining an up-to-date inventory is key. This includes not just software but also hardware like servers, workstations, and network devices. Automated tools can help keep this inventory current.
Categorization 🏷️
Once you have an inventory, categorize assets based on their function, criticality, and vulnerability. This categorization aids in prioritizing patches and allocating resources where they are most needed.
Lifecycle Management 🔄
Understand the lifecycle of each asset. Knowing when software is nearing its end-of-life can help you plan for updates or replacements, ensuring that you’re not patching obsolete systems.
Compliance and Auditing 📑
Asset management isn’t just about security; it’s also about compliance. Detailed asset records can simplify the auditing process, making it easier to demonstrate compliance with various regulations.
Prioritizing Vulnerabilities: The Art of Triage
Effective patch management isn’t about fixing vulnerabilities. It is also about knowing which to fix first. This is where the art of triage comes in.
Risk Assessment 🔍
Evaluate the risk level of each vulnerability. Consider factors like exploitability and potential impact on your network.
Severity Levels ⚖️
Assign severity levels to vulnerabilities. High-severity issues need immediate attention, while low-severity ones can wait.
Business Impact 📈
Factor in the business impact. A vulnerability in a critical business application takes precedence over a less crucial system.
Time Sensitivity ⏳
Some vulnerabilities are time-sensitive, especially if they’re being actively exploited. Prioritize these.
Remediation: The Action Plan
Once vulnerabilities are identified and prioritized, the next step is remediation. This is where you take action to mitigate risks and fortify your network.
Patch Deployment 🚀
Deploy the prioritized patches. Use automated tools to streamline this process, ensuring that patches are applied across all relevant systems.
Alternative Measures 🔄
Sometimes, a patch may not be available or feasible. In such cases, consider alternative measures like isolating affected systems or implementing additional security controls.
Verification ✅
After deployment, verify that the patches or alternative measures have been effective in mitigating the vulnerabilities.
Rollback Plans 🚫
Always have a rollback plan in case a patch causes issues. This ensures you can quickly revert changes and minimize disruptions.
Measuring Success: KPIs to Watch
After implementing your patch management strategy, it’s crucial to measure its effectiveness. Key Performance Indicators (KPIs) offer valuable insights. Key Performance Indicators (KPIs) are quantifiable metrics used to evaluate the success of a strategy or process. In the context of patch management, KPIs help you assess the effectiveness of your remediation efforts.
Patch Coverage 📈
Measure the percentage of systems that have been successfully patched. Aim for as close to 100% as possible.
Time-to-Patch ⏳
Track the average time it takes to deploy a patch after a vulnerability is identified. Shorter times are generally better.
Compliance Rates 📑
Monitor how well your patching aligns with compliance standards. High compliance rates indicate a successful strategy.
Incident Reduction 🛡️
A decrease in security incidents post-patching is a strong indicator of success.
By keeping an eye on these KPIs, you can gauge the effectiveness of your patch management strategy. These metrics provide a quantitative way to measure success and identify areas for improvement.
Automation in Patch Management: A 2024 Perspective
Automation is increasingly becoming the linchpin of effective patch management, especially as we move further into the digital age. Let’s explore why automation is not just a luxury but a necessity in 2024.
Why Automation? 🌟
Automation streamlines the patch management process, reducing the manual effort required. It allows for quicker identification of vulnerabilities and faster deployment of patches, minimizing the window of exposure.
Efficiency and Speed ⚡
Automated tools can scan your entire network for vulnerabilities in a fraction of the time it would take manually. They can also deploy patches to multiple systems simultaneously, significantly speeding up the process.
Consistency and Accuracy 🎯
Automation eliminates human error, ensuring that patches are applied consistently across all systems. This is crucial for maintaining a secure network environment.
Scalability 📈
As your network grows, so does the complexity of your patch management needs. Automation allows you to scale your efforts without a proportional increase in resources or complexity.
Future-Proofing 🔮
With cyber threats evolving rapidly, automation provides the agility to adapt. Automated systems can be updated more easily to tackle new kinds of vulnerabilities, making your patch management strategy more resilient.
Real-World Case Studies: Patch Management Success and Failures
Understanding the importance of patch management becomes clearer when we examine real-world examples. These case studies highlight the outcomes of both effective and failed patch management strategies.
Heartbleed: A Success Story 🌟
In 2014, the Heartbleed bug posed a massive threat to internet security, affecting millions of websites. Organizations that promptly patched their systems were able to prevent the infection, safeguarding their data and customer trust. The key takeaway here is that timely patching can avert security disasters.
Experian Hack: A Cautionary Tale ⚠️
Contrastingly, the Experian hack of 2015 resulted from a failure to apply necessary patches. This negligence led to a massive data breach, affecting 15 million customers and causing irreparable damage to the company’s reputation. The key takeaway is that negligence in patch management can lead to catastrophic outcomes.
Best Practices for Patch Management in 2024
As we navigate through the digital landscape of 2024, adhering to best practices in patch management is more crucial than ever. Here’s what you need to know to stay ahead.
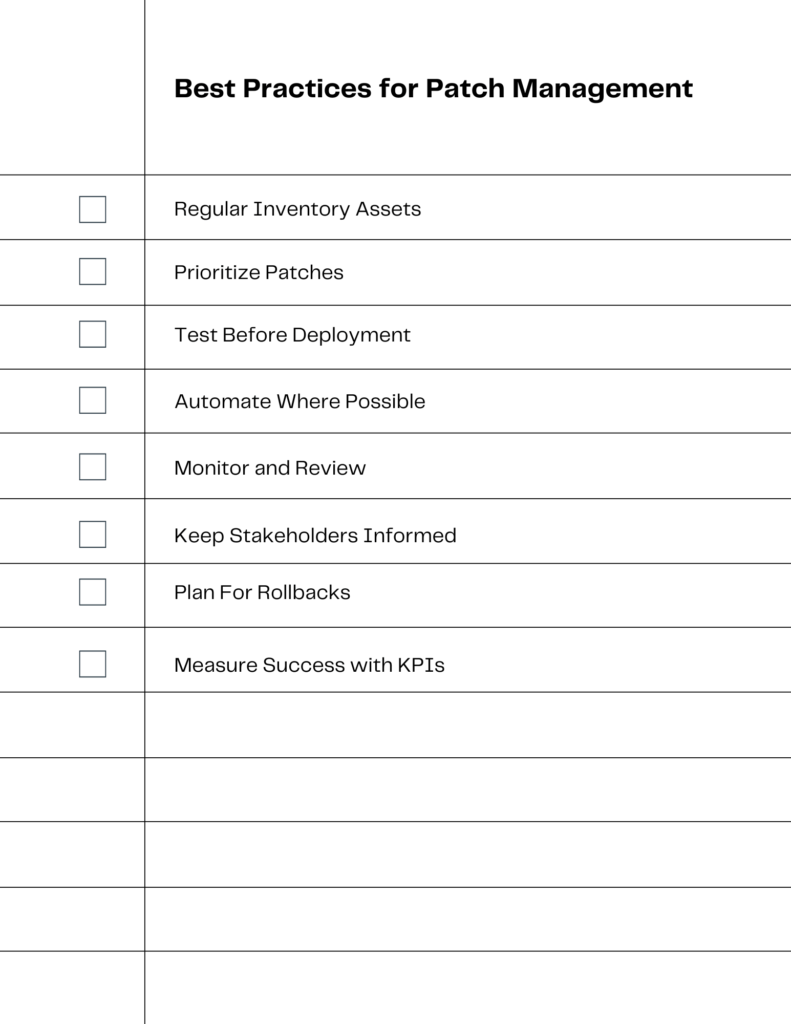
Regularly Inventory Assets 📋
Knowing what you have is the first step in knowing what to patch. Maintain an up-to-date inventory of all hardware and software assets.
Prioritize Patches 🎯
Not all patches are created equal. Prioritize them based on the criticality of the vulnerabilities they address and the importance of the affected systems.
Test Before Deployment 🧪
Always test patches in a controlled environment before rolling them out network-wide to avoid unexpected disruptions.
Automate Where Possible 🤖
As discussed earlier, automation can significantly streamline the patch management process, making it more efficient and error-free.
Monitor and Review 📊
Continuously monitor the network for vulnerabilities and review the effectiveness of existing patches. Make adjustments as needed.
Keep Stakeholders Informed 👥
Communication is key. Keep all relevant parties, from IT staff to upper management, informed about patching schedules and any potential impact.
Plan for Rollbacks ⏮️
Sometimes patches can cause issues. Have a rollback plan in place to quickly revert changes if needed.
Measure Success with KPIs 📈
As mentioned in a previous section, KPIs can help you gauge the effectiveness of your patch management strategy.
Common Pitfalls and How to Avoid Them
Even with the best intentions, patch management can go awry if you’re not careful. Here are some common pitfalls and how to steer clear of them:
Ignoring Non-Critical Patches 🛑
Pitfall: Many organizations focus solely on critical patches, ignoring those deemed less important.
Avoidance: Treat all patches seriously. Even non-critical patches can become entry points for attackers.
Inadequate Testing 🧪
Pitfall: Rushing to deploy patches without adequate testing can lead to system disruptions.
Avoidance: Always test patches in a controlled environment before full deployment.
Poor Communication 🗨️
Pitfall: Lack of communication between IT teams and management can lead to delays or skipped patches.
Avoidance: Keep all stakeholders informed about patch schedules, risks, and impacts.
Manual Processes 🤲
Pitfall: Relying too much on manual processes can lead to errors and inefficiencies.
Avoidance: Automate patch management where possible, as discussed in a previous section.
No Rollback Plan 🔄
Pitfall: Failing to have a rollback plan can make it difficult to recover from a bad patch.
Avoidance: Always have a rollback strategy in place for quick recovery.
Ignoring Third-Party Software 📦
Pitfall: Focusing only on operating system patches and ignoring third-party software can leave vulnerabilities.
Avoidance: Include all software in your patch management strategy, not just the OS.
Inconsistent Monitoring 📉
Pitfall: Sporadic or inconsistent monitoring can lead to overlooked vulnerabilities.
Avoidance: Implement continuous monitoring and regular audits to catch any lapses.
Conclusion: The Future of Patch Management
In summary, patch management is an indispensable component of a robust cybersecurity strategy. From understanding its history and differentiating it from vulnerability management to implementing an 8-step guide for effectiveness, we’ve covered a lot of ground. Real-world case studies and best practices for 2024 further emphasize its critical role. However, even the best strategies can fall prey to common pitfalls, so awareness and continuous improvement are key.
Looking ahead, automation will continue to play a significant role in patch management. As cyber threats evolve, so too will the tools and strategies to combat them. Keeping abreast of these changes is not just advisable—it’s essential.
We’d love to hear from you. What challenges have you faced in patch management? What strategies have worked for you? Share your experiences and insights in the comments section below.
Frequently Asked Questions
What is patch management in cybersecurity?
Patch management is the process of identifying, acquiring, testing, and installing software updates (patches) to fix vulnerabilities and improve system functionality. It’s crucial for maintaining a secure IT environment.
Why is patch management important for businesses?
Patch management is vital for businesses as it helps prevent cyberattacks by closing security loopholes. Regular patching ensures systems are protected from exploits, reducing the risk of data breaches and financial losses..
How often should patch management be performed?
Patch management should be performed regularly, ideally monthly. However, critical patches should be applied immediately to address urgent vulnerabilities and protect against active threats.
What are the key steps in the patch management process?
The key steps in patch management include identifying software and systems, assessing vulnerabilities, prioritizing patches, testing patches in a controlled environment, scheduling deployment, deploying patches, monitoring, and documenting the process.
How can automation improve patch management?
Automation streamlines patch management by quickly identifying and deploying patches, reducing manual errors, and ensuring consistent updates across all systems. This improves efficiency and minimizes the risk of security breaches..
What are common challenges in patch management?
Common challenges in patch management include keeping track of all software assets, testing patches without disrupting operations, prioritizing patches based on risk, and ensuring timely deployment. Effective asset management and automated tools can help overcome these challenges.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!