
Introduction to Data Security and Privacy for Small Businesses
Understanding how to secure data is more crucial than ever. With the rapid evolution of technology, personal information is constantly at risk. This makes it imperative for businesses of all sizes to prioritize data security. As we delve deeper into the realm of cybersecurity, we’ll uncover the importance of safeguarding personal information and why it’s a cornerstone for building trust with your clientele.
However, navigating the world of data security isn’t always straightforward, especially for small businesses. Many fall victim to myths and misconceptions, believing they’re immune to the threats that larger corporations face. As we transition into our discussion, we’ll debunk some of these myths, shedding light on the realities of data security in the modern business landscape. Armed with this knowledge, you’ll be better equipped to protect your business and its most valuable assets.
Why Every Small Business Must Prioritize Personal Data Protection
In today’s digital age, the importance of safeguarding personal information cannot be overstated. For small business owners and IT personnel with limited knowledge of cybersecurity, understanding the significance of this task is paramount. As the digital landscape continues to evolve, so do the threats that lurk within it. Small businesses, with their unique vulnerabilities, must prioritize personal data protection to safeguard their assets, reputation, and future.
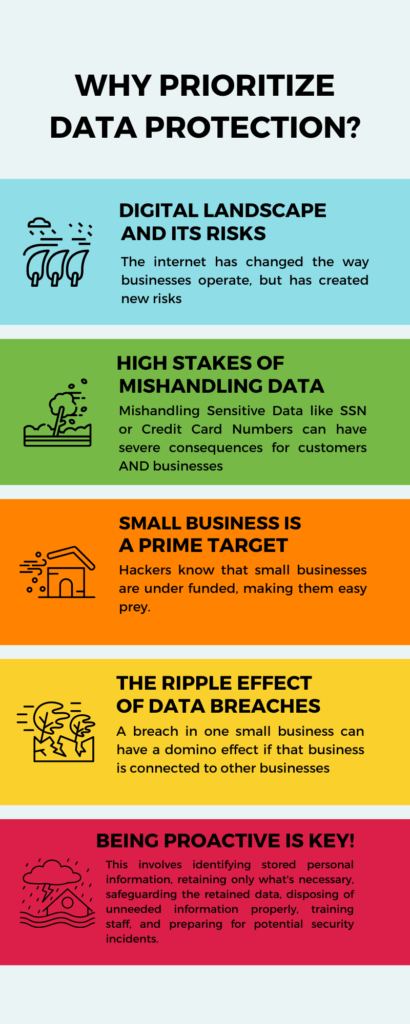
1. The Digital Landscape and Its Risks
The Internet has revolutionized the way businesses operate, offering opportunities for market expansion and the adoption of efficient tools. However, with these benefits come risks. Digital theft has now surpassed physical theft as the most reported form of fraud. This shift underscores the urgency of building a security culture within businesses to maintain customer confidence.
2. The High Stakes of Mishandling Personal Data
Companies, regardless of size, store sensitive personal data such as names, Social Security Numbers, and credit card information, which are vital for various operations like orders and payroll. Mishandling this data can lead to severe consequences like fraud, identity theft, and even legal battles. Such incidents not only harm the trust customers place in businesses but can also result in significant financial losses.
3. Small Businesses: A Prime Target
Contrary to popular belief, small businesses are often the primary targets for cyberattacks. This vulnerability arises because they typically have fewer resources dedicated to cybersecurity, making them easier prey for hackers. If large corporations, with their vast resources, can fall victim to breaches, small businesses with limited protection are even more at risk.
4. The Ripple Effect of Data Breaches
A breach in one small business can have a domino effect. Cyberattacks can extend to interconnected companies in supply chains, amplifying the damage. Moreover, the misuse of sensitive corporate and customer data by hackers poses grave risks, potentially leading to the downfall of a business.
5. Proactive Measures are the Key
To combat these threats, businesses must be proactive. This involves identifying stored personal information, retaining only what’s necessary, safeguarding the retained data, disposing of unneeded information properly, and preparing for potential security incidents. Additionally, training staff in security principles, using strong passwords, and protecting data are essential steps every business should take.
Busting Myths: Data Security Misconceptions in Small Businesses
Small businesses often fall prey to several myths surrounding data security. Let’s debunk some of these misconceptions:
- “We’re too small to be a target.” Cybercriminals often target small businesses, believing they lack robust security measures. Every business, regardless of size, holds valuable personal information.
- “Encrypting data is only for big corporations.” Encrypting data adds an additional layer of security, making it harder for unauthorized access. Every business should consider it, big or small.
- “Data breaches only concern digital data.” Printed sensitive information, like invoices or employee records, can also be at risk. Protecting data means safeguarding both digital and physical forms.
- “We have a password; that’s enough security.” While passwords are a fundamental security measure, they’re often not enough. Multi-factor authentication offers an extra layer of protection against unauthorized access.
- “Data loss mainly occurs due to cyberattacks.” Human error, such as accidentally deleting files or misplacing devices, is a significant cause of data loss. Regular data backups can mitigate such risks.
- “Only IT needs to worry about data security.” Every employee plays a role in data protection. Simple actions, like not opening suspicious text messages or using strong password management practices, can make a difference.
- “All our data is stored safely in the cloud.” While cloud storage offers convenience, it’s essential to ensure providers have robust security measures. Always restrict access and only authorize trusted individuals.
By understanding and addressing these misconceptions, small businesses can take proactive steps towards a more secure data environment. Remember, it’s not just about preventing data breaches but also about building trust with your customers and stakeholders.

Fortifying Your Business: Data Security as the Ultimate Shield Against Intruders
Encryption: The Invisible Armor for Your Data
Encryption transforms your business’s sensitive information into a code, ensuring that only those with the correct key can decipher it. Imagine sending a sealed letter where only the intended recipient knows how to open it. This is what encryption does for your digital data, making it unreadable to prying eyes. For instance, when a customer enters their credit card details on your website, encryption ensures that hackers can’t easily intercept and read this sensitive information.
Multi-Factor Authentication (MFA): The Double-Check System
Ever used a safety deposit box? You’d need both a key and a code. Similarly, MFA requires users to provide two or more verification methods before granting access.
This could be something they know (password), something they have (a phone or token), or something they are (fingerprint). By requiring multiple forms of verification, MFA ensures that even if a hacker steals a password, they still can’t access sensitive data without the other factors.
For example, an employee might receive a text message with a code when trying to log into a company system from a new device. This additional layer of security ensures that even if their password is compromised, unauthorized access is still prevented.
Layered Security: Not Just One, But Multiple Lines of Defense
Think of layered security like a castle with moats, walls, and guards. Each layer is designed to stop different types of threats. In the digital realm, this might include firewalls to block malicious traffic, intrusion detection systems to monitor and alert on suspicious activity, and regular software updates to patch vulnerabilities.
By employing a multi-layered approach, businesses ensure that even if one security measure fails, others are in place to protect data. For instance, if a hacker manages to bypass a firewall, they’d still have to contend with encrypted data and MFA challenges.
In today’s digital age, where data breaches and cyberattacks are rampant, it’s crucial for small business owners and IT personnel to understand the importance of robust data security measures. By implementing encryption, multi-factor authentication, and a layered security approach, businesses can significantly reduce the risk of unauthorized access and ensure that their sensitive information remains protected. Remember, in the realm of cybersecurity, it’s always better to be proactive than reactive.
Preventing Data Loss and Ensuring Continuity
Data Loss Prevention, or DLP, is a set of strategies aimed at ensuring that sensitive information doesn’t leave your business unintentionally. Whether it’s due to human error, data breaches, or other unforeseen events, DLP helps protect your data from unauthorized access and potential loss.
Essential DLP Strategies for Small Businesses
For small business owners and IT personnel, understanding and implementing DLP strategies is crucial. By taking proactive measures, such as effective password management and regular data backups, businesses can significantly reduce the risk of data loss and ensure that their sensitive information remains protected. Remember, in the digital age, protecting data is not just an IT concern; it’s a business imperative.
Password Management: The First Line of Defense
Password management involves creating, storing, and updating strong, unique passwords for all business accounts and systems. If an outside entity gains access to a user’s password, they could get access to any data tied to that user.
For example, imagine an employee uses the same password for multiple platforms. If a hacker cracks this password on a less secure site, they could gain unauthorized access to more critical business systems. By using a password manager, each account has a unique, strong password, reducing this risk.
Regular Data Backups: Your Safety Net
Data backups involve creating copies of your business data and storing them in a separate location. So a recent version can be restored, ensuring that in the event of data loss. For example, a local store’s computer system crashes, erasing the month’s sales data. The store can restore this data from the most recent backup, minimizing disruption and financial loss.
Restricting Access to Sensitive Data
By ensuring that only authorized personnel can access sensitive information the risk of data breach is reduced. For example, a small clinic stores patient record digitally. If they restrict access to the doctors and authorized staff, this ensures patient privacy and reduces the risk of unauthorized access.
Regular Training and Awareness Programs
Educating employees about the importance of data security and the potential risks of human error can significantly reduce unintentional data breaches. For example, an employee receives an email that looks like it’s from the company’s IT department, asking for login details. The employee recognizes this as a phishing attempt and doesn’t provide the information, preventing potential data loss.
Why Data Retention Matters for Small Businesses
For small businesses, having a well-defined data retention policy is a necessity. It ensures that you’re protecting sensitive information, optimizing storage, and staying compliant. By understanding the unique needs of your data and weighing the pros and cons of retention durations, you can craft a policy that’s both efficient and effective.
But not all data is created equal. Some data might be crucial for business operations, while others might be redundant or obsolete. Here’s where a data retention policy steps in! It provides a clear guideline on how long specific data should be kept and when it should be disposed of.
It’s essential to understand the nature and significance of each data type. Personal information might need to be retained for a specific period due to legal requirements. On the other hand, text messages between employees might not have a long shelf life.
By tailoring your data retention policies, you ensure that you’re not only compliant with regulations but also efficient in data management.
Weighing the Pros and Cons of Data Retention Durations
Pros of Longer Data Retention:
- Backup and Recovery: In case of data loss, having older data can be a lifesaver. It acts as an additional layer of security.
- Historical Analysis: Older data can provide insights into business trends, helping in strategic decision-making.
- Legal Compliance: Some regulations might require businesses to retain certain data for extended periods.
Cons of Longer Data Retention:
- Increased Storage Costs: Storing data, especially if it’s vast, can be expensive. Over time, these costs add up.
- Management Challenges: The more data you have, the harder it becomes to manage, leading to potential human error.
- Security Risks: Holding onto data for longer periods increases the risk of unauthorized access and potential data breaches.
Securing Your Business’s Future: The Final Word on Data Protection
Data security isn’t just about putting up barriers against unauthorized access. It’s about creating a holistic environment where personal information is safeguarded, sensitive information remains confidential, and business operations continue without hitches. Implementing features like encryption and multi-factor authentication adds an additional layer of security, ensuring that your business’s data remains in trusted hands.
Moreover, understanding the nuances of data retention and disposal is crucial. As we’ve seen, not all data is equal. Tailoring your retention policies based on the nature of the data not only ensures compliance but also optimizes storage and management. Whether you choose a longer or shorter data retention duration, being aware of the pros and cons helps in making informed decisions.
However, the journey doesn’t end here. Protecting data is an ongoing process. As threats evolve, so should your security measures. Regularly updating your knowledge, staying aware of potential risks, and being proactive in implementing security measures are the keys to success.
We encourage you to take the insights from this article to heart and embark on your data protection journey. And remember, we’re here to help. Share your thoughts, questions, or experiences in the comments below. Your feedback not only enriches this discussion but also aids others in their quest for better data security.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


