
Introduction
In today’s digital age, the significance of robust cybersecurity for small and medium-sized businesses (SMBs) is more crucial than ever. The surge in cyber threats and attacks is relentless. These threats target businesses of all sizes, with SMBs often being the most vulnerable. The necessity for advanced, reliable security solutions is not just a luxury. It is a fundamental need to safeguard sensitive data and maintain business continuity. And so, we will explore the benefits of Security as a Service as a solution to this problem.
Security as a Service (SECaaS) emerges as a pivotal solution in this scenario. It offers a comprehensive range of security services via the cloud. SECaaS provides businesses with access to cutting-edge security tools, expert personnel, and continuous monitoring. These tools are all aimed at fortifying business’ defense mechanisms against the myriad of cyber threats lurking in the digital landscape. SECaaS is not merely a security solution. It is also a strategic approach to ensuring the resilience and protection of business operations. This is especially true for those with limited resources and cybersecurity expertise.
By embracing SECaaS, small businesses can navigate the complexities of the cyber world more efficiently. Instead. they can focus on their core operations while leaving security concerns to the experts. It aligns seamlessly with the unique needs and constraints of SMBs. SECaaS offers a cost-effective, scalable, and flexible solution to their security woes.
For a deeper understanding of the importance of cybersecurity and how to protect your business, explore our detailed guides on cybersecurity essentials and endpoint protection.
The Evolution of Security Needs for SMBs
Small and medium-sized businesses (SMBs) find themselves in a constant battle against emerging cybersecurity threats. The journey is depicted in our infographic. The infographic reveals a relentless progression of cyber threats. Each threat evolves over time to be more sophisticated and damaging than its predecessor. This forces SMBs to continually adapt and fortify their defenses. Note that the years are approximate and are used for illustrative purposes. Here is one source for further details.
The 2000s: Threats and Solutions
In the early 2000s, the digital realm witnessed the rise of viruses and worms. This compelled businesses to equip themselves with basic antivirus software and firewalls. As we moved into the mid-2000s, the surge in phishing attacks and spyware occurred. This necessitated the implementation of email filtering and anti-spyware tools, marking the beginning of a more proactive approach to cybersecurity. The late 2000s brought forth advanced persistent threats (APTs) and more targeted attacks. This further pushed SMBs towards the deployment of intrusion detection and prevention systems.
The 2010s: Threats and Solutions
The early 2010s saw the escalation of ransomware attacks. This led to the development of robust data backup strategies and advanced malware protection to safeguard critical information. With the expansion of cloud services in the mid-2010s, cloud security threats emerged. This prompted the adoption of specialized cloud security solutions and policies. The proliferation of Internet of Things (IoT) devices in the late 2010s introduced new vulnerabilities. This necessitated the implementation of stringent IoT security measures and network segmentation.
Today and Tomorrow: Threats and Solutions
Now, in 2023, we are witnessing the sophistication of cyber-attacks utilizing AI and machine learning. This requires the integration of AI-driven security solutions and enhanced threat intelligence. The anticipation of evolving threats exploiting emerging technologies has led to the strategic adoption of SECaaS for comprehensive, advanced protection.
Managing security in-house has become increasingly complex due to these evolving threats and technologies. SMBs are often constrained by limited resources and expertise. They struggle to keep up with the rapid advancements in cybersecurity. Thus, making the adoption of outsourced security solutions like SECaaS more relevant and crucial than ever.
By understanding this evolution, SMBs can better appreciate the imperative nature of advanced, continuous security measures. They can also appreciate the value of embracing solutions like SECaaS in navigating the intricate and dynamic terrain of cybersecurity.

Defining Security as a Service (SECaaS)
Security as a Service (SECaaS) is a comprehensive and holistic security solution. It is designed to provide continuous and advanced protection to businesses operating in the digital realm. As depicted in our infographic, SECaaS is not a singular service. SECaaS is a suite of security components working in tandem to safeguard every facet of a business’s digital presence.
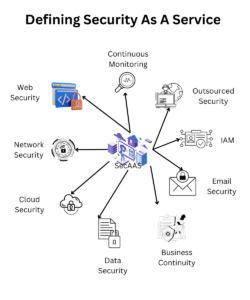
Defining SECaaS
SECaaS is an outsourced security service. It allows businesses to access top-notch security solutions without the need to manage them in-house. It operates on a subscription-based model. This model offers flexibility and scalability to businesses. This is especially true for small and medium-sized enterprises (SMEs) with limited resources and expertise in cybersecurity.
How Security As A Service Operates and Benefits Small Businesses
At its core, SECaaS integrates seamlessly with a business’s existing infrastructure, providing a layer of protection across various domains. It offers continuous monitoring, ensuring real-time detection and response to any security threats or anomalies. The operational flow of SECaaS, as illustrated in the infographic, is a testament to its comprehensive approach to security. SECaaS covers multiple components and ensuring no vulnerability is left unaddressed.
Range of Solutions Offered by SECaaS
- Web Security: SECaaS protects against threats targeting web-based services, ensuring safe and secure online operations.
- Cloud Security: It safeguards cloud-based services and data, addressing the unique security challenges posed by cloud computing.
- Network Security: SECaaS fortifies network infrastructure, preventing unauthorized access and attacks on network resources.
- Data Security: It provides robust protection for data at rest and in transit, preventing data breaches and leaks.
- Email Security: SECaaS secures email communication, filtering malicious content and protecting against phishing attacks.
- Identity and Access Management (IAM): It manages user access and verifies user identity. Thus, ensuring only authorized individuals can access sensitive resources.
- Business Continuity: SECaaS ensures the uninterrupted continuation of business operations, even in the event of a security incident.
- Outsourced Security: By outsourcing security services, businesses can focus on their core operations while experts manage their security needs.
Conclusion
Security as a Service is a pivotal solution for businesses seeking advanced, continuous, and comprehensive security measures. It addresses the multifaceted security needs of businesses, offering a range of solutions from web security to business continuity. By adopting SECaaS, businesses, especially SMBs, can navigate the complexities of cybersecurity. Thus, ensuring the resilience and protection of their operations in the face of evolving threats.
For a more in-depth understanding of SECaaS and its components, refer to our detailed post on cybersecurity as a service.
Why Security As A Service Benefits are a Game-Changer for Small Businesses
In the realm of cybersecurity, small businesses often grapple with numerous challenges. Many of these challenges stem from limited resources, lack of expertise, and the ever-evolving nature of cyber threats. Security as a Service (SECaaS) emerges as a game-changer in this scenario. It addresses the specific pain points faced by small businesses. In doing so, it offers solutions that are not just effective but also efficient and scalable.
Addressing Small Business Challenges
Small businesses, often operating with constrained budgets and manpower, find it daunting to allocate significant resources to manage security internally. The table below illustrates the stark contrast in resource allocation and security management between scenarios with and without SECaaS.
Comparative Table: Benefits With and Without Security As A Service
| Aspect | Without SECaaS | With SECaaS |
|---|---|---|
| Security Management | In-house team manages all security aspects | Outsourced to experts, ensuring professional management |
| Resource Allocation | Significant resources allocated to security management | Resources are freed up, allowing focus on core business activities |
| Cost | High upfront costs for security infrastructure and personnel | Subscription-based model, reducing upfront costs |
| Expertise | Requires in-house expertise in cybersecurity | Access to specialized expertise and advanced solutions |
| Scalability | Limited by in-house resources and budget | Highly scalable, adapting to business needs and growth |
| Response Time | Dependent on the availability and capability of in-house team | Rapid and professional response to security incidents |
| Technology Updates | Regular updates and upgrades required, can be time-consuming | Automatic updates and access to the latest security technologies |
| Compliance Management | Managed internally, can be complex and challenging | Assisted compliance management, reducing complexity |
| Risk Management | Dependent on internal risk assessment capabilities | Enhanced risk management with expert assessments |
| Business Continuity | Requires development of internal continuity plans | Integrated business continuity solutions |
As depicted, without SECaaS, small businesses are burdened with the responsibility of managing all security aspects in-house. Thus, requiring substantial resources and expertise in cybersecurity. This approach is cost-intensive due to high upfront costs for security infrastructure and personnel. In addition, the approach also limits scalability and responsiveness to security incidents.
Security As A Service Benefits: The Advantage
SECaaS, on the other hand, transforms the security landscape for small businesses. By outsourcing security management to experts, businesses can ensure professional and rapid response to security threats. Doing so frees up valuable resources to focus on core business activities. The subscription-based model of SECaaS reduces upfront costs, providing access to specialized expertise and advanced security solutions.
To delve deeper into how Cyber Security as a Service can be synergized with Endpoint Security to provide a more robust and comprehensive security solution, especially for small businesses, explore our detailed post on Endpoint Security and Cyber Security as a Service. This post provides insights into the escalating cyber threats and how integrating Endpoint Security with Cyber Security as a Service can act as a formidable shield, protecting your business from the myriad of cyber threats lurking in the digital world.
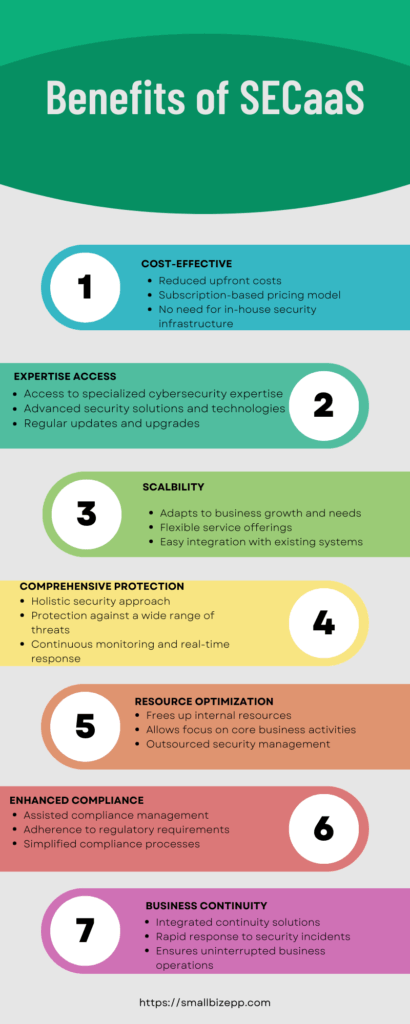
Cost-Effectiveness and Resource Optimization
The cost-effectiveness of SECaaS is unparalleled, especially for small businesses operating on tight budgets. It eliminates the need for substantial investments in security infrastructure and personnel, allowing businesses to allocate their resources more optimally. Implementing automatic updates and access to the latest security technologies are important. They ensure that businesses are always protected against the latest threats without the need for constant upgrades and updates.
Enhanced Risk and Compliance Management
SECaaS also aids in risk management by offering expert risk assessments, enabling businesses to identify and mitigate risks proactively. Compliance management is often a complex and challenging task. It can be simplified with assisted compliance management services offered by SECaaS. Thus, reducing the complexity and ensuring adherence to regulatory requirements.
Conclusion
Security as a Service is indeed a revolutionary solution for small businesses with all of its benefits. It addresses their unique challenges in cybersecurity. It offers a cost-effective, resource-optimized, and scalable approach to security management. Thus, allowing small businesses to navigate the cybersecurity landscape with ease and confidence.
By adopting Security As A Service, small businesses can reap benefits by fortifying their defenses against cyber threats. Also, they can foster growth and innovation without being hindered by security concerns.
Diving into the Benefits of Security as a Service
In a world where the digital landscape is constantly evolving, the significance of robust cybersecurity cannot be overstated. Security as a Service (SECaaS) emerges as a beacon of hope. This is especially true for small and medium-sized businesses striving to safeguard their digital assets. It offers a myriad of benefits tailored to meet the unique needs and challenges faced by them.
This section delves deep into the transformative benefits of SECaaS. It explores how SECaaS stands as a cost-effective security solution. It also explains how the continuous monitoring inherent in its model provides enhanced protection against the ever-growing spectrum of cyber threats. By understanding these benefits, businesses can make informed decisions. Thus, optimizing their security posture while navigating the intricate tapestry of the digital realm.
Enhanced Protection with Continuous Monitoring
In an era where cyber threats are incessantly evolving and becoming increasingly sophisticated, the need for proactive and robust security measures is paramount. Security as a Service (SECaaS) rises to this challenge by offering enhanced protection through continuous monitoring. Thus, ensuring that threats are identified and mitigated in real-time, safeguarding the integrity of business operations.
Proactive Threat Identification
Continuous monitoring is a one of the biggest of the benefits of Security As A Service. It is the cornerstone of the SECaaS model. It operates relentlessly, scanning the digital environment for any signs of malicious activity or potential vulnerabilities. This proactive approach to threat identification allows for the immediate detection of anomalies. Thus, enabling swift response actions to prevent any compromise to the system’s security.
Real-Time Response
The real-time response capability inherent in continuous monitoring is crucial in minimizing the impact of a security incident. The moment a threat is detected, SECaaS solutions initiate predefined response protocols, isolating the threat and mitigating its effects. This rapid response ensures that any potential damage is contained, and business operations can continue uninterrupted.
Comprehensive Security Coverage
The continuous monitoring provided by SECaaS offers comprehensive security coverage. This can protect systems against a wide array of cyber threats, from malware and phishing attacks to data breaches and DDoS attacks. It extends its protective umbrella across the entire digital landscape of a business. This landscape includes networks, applications, data, and endpoints, ensuring holistic security.
Peace of Mind for Businesses
For small businesses, the enhanced protection and continuous monitoring offered by SECaaS translate to peace of mind. Business owners and IT personnel can focus on their core responsibilities. Thus, they can be confident in the knowledge that their cybersecurity is in expert hands. The assurance of having continuous, expert-backed monitoring alleviates the stress associated with managing cybersecurity risks. In doing so, it allows businesses to operate with increased security and reduced anxiety.
Conclusion
Continuous monitoring under Security as a Service is invaluable for businesses operating in today’s cyber-centric world. It provides enhanced protection. It also provides a fortified defense line against the myriad of cyber threats lurking in the digital shadows, As such, ensuring that businesses can thrive and innovate without the constant fear of cyber compromise.
Cost-Effective Security Solution
In the intricate landscape of cybersecurity, small businesses often find themselves navigating through substantial financial commitments. Traditional security solutions demand hefty upfront investments in infrastructure, personnel, and ongoing maintenance. This creates a financial burden for businesses operating with limited resources. However, Security as a Service (SECaaS) emerges as a beacon of financial relief in this scenario. SECaaS offers a cost-effective alternative that significantly reduces the financial strain on small businesses.
As illustrated in the infographic, one of the paramount benefits of adopting SECaaS is its cost-effective nature. Unlike traditional models, SECaaS operates on a subscription-based pricing model, eliminating the need for substantial upfront investments. This model not only reduces initial costs but also provides financial predictability, aiding in more accurate budgeting and resource allocation.
Reduced Financial Burden
The financial advantages of SECaaS extend beyond mere cost reductions. By outsourcing security services, small businesses can avoid the financial and operational burden of managing security in-house. This means no investments in security infrastructure, no hiring of specialized personnel, and no concerns about the ongoing costs of updates and upgrades. The financial relief provided by SECaaS allows small businesses to allocate their resources more effectively. As such, small businesses can focus on their core business activities and fostering innovation and growth.
Access to Expertise without the Price Tag
Beyond financial considerations, SECaaS provides small businesses with access to specialized cybersecurity expertise and advanced security solutions. These options would be prohibitively expensive to acquire independently. This access ensures that small businesses can avail themselves of the latest and most effective security technologies. Thus, receiving regular updates and upgrades without additional costs.
Conclusion
The cost-effective nature of Security as a Service is a transformative advantage for small businesses. It allows them to secure their digital presence without breaking the bank. SECaaS also reduces the financial burden traditionally associated with cybersecurity. Thus, enabling businesses to optimize their resources and focus on what they do best. It does this all while ensuring comprehensive protection against cyber threats.
Real-World Impact: Stories of SECaaS in Action
Cyber threats lurk in every corner. The transformative power of Security as a Service (SECaaS) shines brightly, bringing forth stories of resilience, protection, and innovation. By exploring real-world impacts, we can glean insights into the tangible benefits and the profound difference SECaaS makes for small businesses navigating the cyber seas.
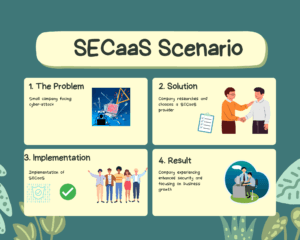
Our illustrative storyboard unfolds the journey of a hypothetical small retail business, SmallShop. We find it grappling with the daunting challenges of cyber threats and finds solace and strength in SECaaS.
SmallBiz Solutions: A Journey from Vulnerability to Security
SmallShop operates in the competitive retail industry. It found itself ensnared in the web of relentless cyber-attacks, suffering data breaches and financial losses. It had limited IT resources and a lack of cybersecurity expertise. As such, the business was at a crossroads, searching for a beacon of hope to secure its digital frontier.
Embracing SECaaS: A Beacon of Hope
In the quest for robust cybersecurity, SmallShop turned to SECaaS, seeking to fortify its defenses without overstretching its resources. The decision to embrace SECaaS was a pivotal moment. It marked the beginning of a transformative journey towards enhanced cybersecurity and operational resilience.
The Transformation: Enhanced Protection and Operational Efficiency
The adoption of SECaaS brought a wave of transformation for SmallShop. It provided a shield against the onslaught of cyber threats. Thus, reducing the frequency of security incidents and enabling the business to operate with enhanced efficiency. The secure environment fostered by SECaaS allowed SmallShop to redirect its focus towards its core business activities, fostering growth and innovation.
The Outcome: Security, Peace of Mind, and Business Growth
With SECaaS as its guardian, SmallBiz Solutions experienced not only heightened security but also peace of mind. The business could flourish and expand its horizons, unburdened by the shadows of cyber threats. The story of SmallShop is a testament to the empowering impact of SECaaS, illustrating how it can be the catalyst for positive change and success for small businesses.
Conclusion
The story of SmallShop illuminates the transformative potential of Security as a Service. It is a reflection of the real-world impact SECaaS can have, offering a glimpse into a future where small businesses can thrive in a secure and supportive digital ecosystem. By understanding and embracing the benefits of SECaaS, small businesses can write their own success stories, turning the tides in the battle against cyber threats.
How to Choose the Right SECaaS Provider
Selecting the right Security as a Service (SECaaS) provider is a pivotal decision that can significantly impact the security posture and operational resilience of a business. It requires meticulous consideration of various factors to ensure that the chosen provider aligns with the business’s needs, goals, and values.
As depicted in the infographic above, several key considerations and criteria are paramount in selecting a suitable SECaaS provider. Here, we delve deeper into some of these critical factors, emphasizing interoperability, total cost of ownership, and effective reporting mechanisms.
Interoperability
In today’s diverse technological landscape, businesses utilize a myriad of systems, applications, and platforms. It is crucial to choose a SECaaS provider that offers interoperability, ensuring seamless integration with the existing technology stack. Interoperability eliminates compatibility issues, facilitates smooth operations, and enhances the overall efficiency of security management.
Total Cost of Ownership
While SECaaS is renowned for being a cost-effective security solution, it is vital to consider the total cost of ownership when selecting a provider. This includes not only subscription fees but also any additional costs associated with implementation, customization, and support. A transparent and comprehensive understanding of costs enables businesses to make informed decisions and avoid unforeseen financial burdens.
Effective Reporting Mechanisms
Effective reporting mechanisms are the linchpin of successful security management. They provide insights into security performance, incident occurrences, and response actions. When choosing a SECaaS provider, prioritize those offering detailed, clear, and actionable reports, enabling informed decision-making and continuous improvement of security strategies.
Conclusion
Choosing the right SECaaS provider is a nuanced process, requiring a balanced consideration of various factors. By focusing on interoperability, total cost of ownership, and effective reporting mechanisms, businesses can select a provider that not only meets their security needs but also aligns with their operational dynamics and financial capabilities.

Aligning SECaaS with Your Business Goals
In the dynamic landscape of business operations, aligning Security as a Service (SECaaS) with your business goals is pivotal. It’s not just about implementing advanced security solutions; it’s about weaving them seamlessly into the fabric of your business, ensuring they resonate with your objectives and operational ethos.
Identifying Your Business Goals and Security Needs
Start by delineating your business goals and pinpointing your security needs. It’s crucial to understand what you aim to achieve and what security requisites are essential to safeguard your business assets. This step lays the foundation for selecting the most suitable SECaaS provider and customizing the solutions to align with your unique needs.
Selecting the Right SECaaS Provider
Once your goals and needs are clear, embark on the journey to find a SECaaS provider that mirrors your business aspirations. Scrutinize the providers based on their ability to meet your security requirements and their compatibility with your business goals. The right provider is not just a vendor but a partner in your journey towards enhanced security and business growth.
Customizing SECaaS Solutions
After selecting a provider, tailor the SECaaS solutions to fit the contours of your business operations. Customize the services to address your specific security needs and to resonate with your business objectives. This step ensures that the SECaaS solutions are not just added layers but integral components of your business ecosystem.
Integrating SECaaS with Business Operations
With customized solutions at hand, integrate SECaaS seamlessly into your business operations. This integration should be smooth, with the solutions complementing your operational processes and enhancing your security posture without disrupting the workflow. It’s about creating a symbiotic relationship between SECaaS and your business activities.
Monitoring and Optimizing
Post-integration, maintain a vigilant eye on the performance of the SECaaS solutions. Regularly monitor and optimize the services to ensure they are delivering optimal results. Make sure they are in sync with your evolving business goals and operational dynamics. This ongoing process is key to sustaining enhanced security and operational efficiency.
Achieving Enhanced Security and Business Growth
By effectively integrating SECaaS, you pave the way for enhanced security and business growth. The synergy between advanced security solutions and your business operations empowers you to achieve your business goals. At the same time, you are fostering a secure and resilient operational environment.
Conclusion
Aligning Security as a Service with your business goals is a strategic endeavor. It requires thoughtful consideration, meticulous planning, and seamless execution. Follow the outlined steps and integrating SECaaS effectively. Doing so, you can transform your security landscape, aligning it with your business aspirations and operational needs, and propelling your business towards new horizons of success and resilience.

Conclusion: Elevate Your Business with SECaaS
In the ever-evolving realm of cybersecurity, small and medium-sized businesses find themselves in a constant battle to safeguard their assets. Security as a Service (SECaaS) emerges as a beacon of hope. It offers advanced, cost-effective security solutions tailored to the unique needs of smaller enterprises.
We’ve traversed the landscape of SECaaS, exploring its evolution, defining its components, and diving deep into its myriad benefits. We’ve seen how it stands as a game-changer for small businesses, addressing specific challenges and optimizing resources. Through real-world impacts and practical advice, we’ve illustrated how integrating SECaaS can align seamlessly with your business goals, enhancing both security and operational efficiency.
SECaaS is more than a security solution. It is also a strategic partner, enabling small businesses to fortify their defenses while concentrating on their core competencies and business growth. It offers a pathway to navigate the complexities of cybersecurity, allowing businesses to thrive in a secure and resilient environment.
We encourage small businesses to contemplate the adoption of SECaaS. Doing so, they can bolster their security posture and to focus more on their core business activities. It’s time to embrace the enhanced protection and peace of mind that SECaaS bring. Thus, allowing you to venture forth with confidence in the competitive business landscape.
We invite our readers to engage in fruitful discussions, share their insights and experiences, and delve deeper into the wealth of resources available on our website. Let’s foster a community where knowledge is shared, experiences are valued, and security is a shared endeavor.
Explore, learn, and secure your business with Security as a Service, and let’s build a safer, more secure business world together.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!

