Introduction
In the ever-evolving landscape of cybersecurity, staying ahead of threats such as APT threats is more challenging than ever. That’s where frameworks like Mitre Att&ck and D3fend mapping come into play.
These robust frameworks offer a comprehensive approach to understanding, mapping, and countering cybersecurity threats. But how do they work together? This article aims to unlock the synergy between Mitre ATT&CK and D3FEND mapping, providing you with actionable insights to fortify your cybersecurity strategy.
The synergy between Mitre ATT&CK and D3FEND mapping lies in their complementary nature, where one framework outlines offensive cybersecurity tactics and the other focuses on defensive countermeasures. Mitre ATT&CK provides a detailed matrix of cyber adversary tactics and techniques, offering insights into how attacks are structured and executed. On the flip side, D3FEND, developed by the NSA, offers a framework for counteracting these tactics with specific defensive techniques. The integration of these two frameworks allows cybersecurity professionals to create a more robust and proactive defense strategy. By understanding the methods of potential attackers (Mitre ATT&CK) and aligning them with effective countermeasures (D3FEND), organizations can enhance their security posture, anticipate threats more effectively, and respond to cyber incidents with greater precision

Why Mitre ATT&CK and D3FEND Mapping is Crucial for Endpoint Security
Endpoint security is no longer a luxury; it’s a necessity. As cyber threats become increasingly sophisticated, traditional security measures often fall short. That’s where Mitre ATT&CK and D3FEND mapping step in. These frameworks provide a structured approach to identifying vulnerabilities, understanding attack techniques, and implementing effective countermeasures. By integrating these frameworks into your cybersecurity strategy, you’re not just patching holes; you’re building a fortress.
Understanding Mitre ATT&CK
Mitre ATT&CK isn’t just another framework; it’s a knowledge base used globally by cybersecurity professionals. It outlines the tactics, techniques, and procedures (TTPs) that adversaries use to compromise, navigate, and exploit networks. By understanding these TTPs, you can better prepare your defenses and respond more effectively to security incidents.
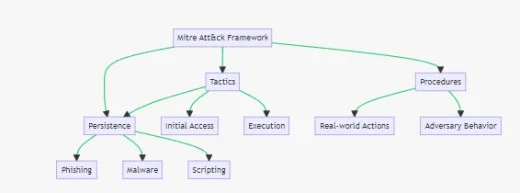
The above flowchart shows the components of the Att&ck framework:
- Tactics: The “why” of an attack, such as Initial Access, Execution, and Persistence.
- Techniques: The “how” of an attack, including methods like Phishing, Malware, and Scripting.
- Procedures: Real-world actions and adversary behavior.
Key Tactics and Techniques in Mitre Att&ck
Understanding the tactics and techniques in Mitre Att&ck is akin to knowing your enemy’s playbook. Tactics are the “why” of an attack, the objectives behind it. Techniques, on the other hand, are the “how,” the methods used to achieve these objectives. From initial access to data exfiltration, each tactic can have multiple techniques, providing a granular view of attack patterns.
Deciphering D3fend
While Mitre Att&ck outlines the offensive moves of cyber adversaries, D3fend focuses on the defense. Developed by MITRE, this framework provides countermeasures to the techniques listed in Att&ck. It’s like having a defensive playbook that complements the offensive strategies outlined in Att&ck. D3fend offers actionable guidance on how to mitigate risks and thwart attacks effectively.
D3FEND Countermeasures and Actions
The D3FEND defense framework provides a structured set of countermeasures designed to neutralize or mitigate the techniques identified in Mitre ATT&CK. These countermeasures range from simple actions like patching software vulnerabilities to more complex strategies like network segmentation. By understanding these countermeasures, you can tailor your defense mechanisms to be as robust as possible, effectively countering the tactics and techniques used by cyber adversaries.
How to Map Mitre ATT&CK Techniques to D3FEND Countermeasures
Mapping is where the magic happens. It’s the process of aligning the offensive techniques from Mitre ATT&CK with the defensive countermeasures in D3FEND. This mapping enables you to create a comprehensive cybersecurity strategy that addresses both sides of the coin. Whether you’re a small business manager or an IT professional, understanding this mapping can significantly enhance your cybersecurity posture.

Real-World Applications of Mapping
Theory is good, but practice is where the rubber meets the road. In this section, we’ll explore real-world case studies that demonstrate the effectiveness of mapping Mitre Att&ck techniques to D3fend countermeasures. From thwarting ransomware attacks to preventing data breaches, these real-life scenarios will provide you with actionable insights for your own cybersecurity strategy.
- Thwarting Ransomware Attacks: A healthcare organization used Mitre Att&ck to identify common ransomware techniques like ‘Data Encrypted for Impact.’ They then mapped these to D3fend countermeasures like ‘Data Backup and Recovery’ to successfully thwart a ransomware attack.
- Preventing Data Exfiltration: A financial institution identified ‘Exfiltration Over C2 Channel’ as a common technique used by attackers. By mapping this to D3fend’s ‘Network Segmentation,’ they were able to isolate the affected systems and prevent data loss.
- Stopping Phishing Attacks: An e-commerce company used Mitre ATT&CK to identify ‘Spearphishing Attachment’ as a frequent attack vector. They mapped this to D3fend’s ‘Email Filtering’ countermeasure to block malicious emails effectively.
- Mitigating Insider Threats: A tech company identified ‘Valid Accounts’ as a technique often used in insider threats. They mapped this to D3fend’s ‘User Behavior Analytics’ to flag unusual user activities, leading to the early detection of an insider threat.
The Synergy Between Mitre Att&ck and D3fend
When used in isolation, both Mitre Att&ck and D3fend are powerful tools. However, their true potential is unlocked when they are used in tandem. This synergy allows for a more holistic approach to cybersecurity, covering both offensive and defensive strategies. By understanding how these frameworks complement each other, you can develop a more robust and comprehensive cybersecurity strategy.
Challenges and Limitations
No framework is without its challenges. While Mitre Att&ck and D3fend offer invaluable insights, they are not a one-size-fits-all solution. This section will discuss the limitations and challenges you may encounter when implementing these frameworks, such as resource constraints, complexity, and the need for continuous updates.
Conclusion and Next Steps
Understanding and implementing Mitre Att&ck and D3fend mapping is not just a technical endeavor; it’s a strategic move that can significantly bolster your cybersecurity posture. As we’ve explored, these frameworks offer a comprehensive approach to both offense and defense, providing you with the tools you need to build a resilient cybersecurity strategy.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
