How To Stay Ahead of Hackers: The Ultimate Threat Hunting Tutorial
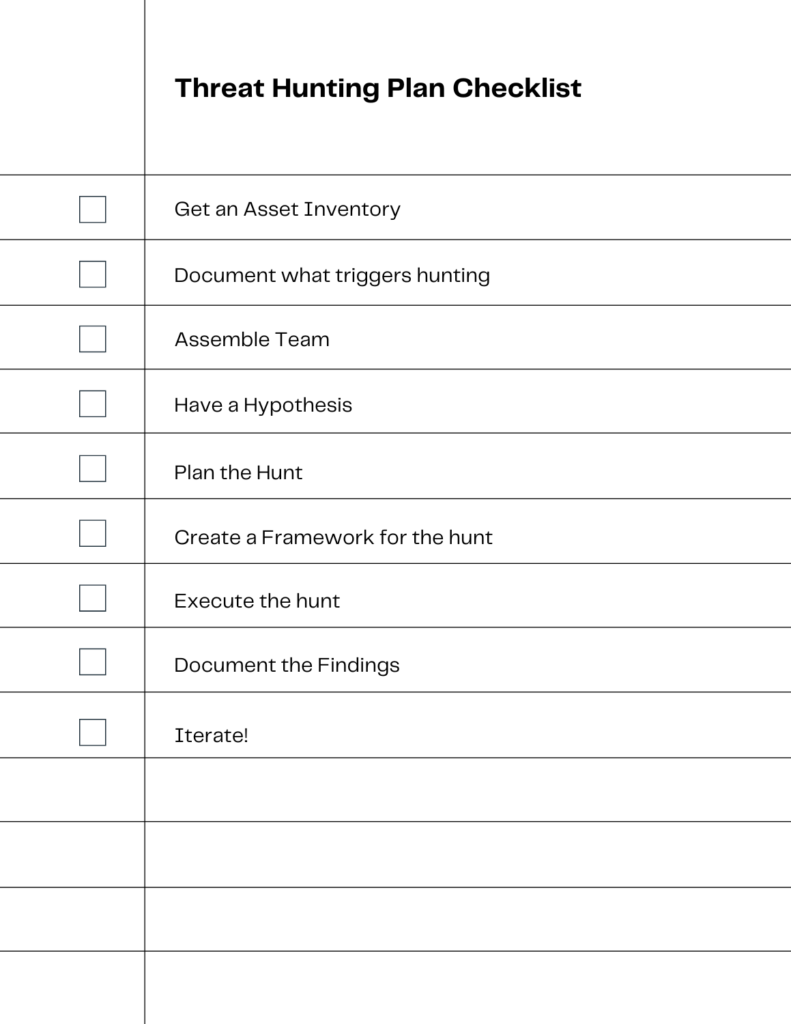
Introduction Threat hunting is a proactive security approach. Existing tools aim to uncover malicious, suspicious, or risky activities. The reasoning behind threat hunting is the assumption that a breach may have already occurred or will occur. Thus, leading security personnel to actively search for threats in their environment rather than relying solely on deploying new […]
How To Stay Ahead of Hackers: The Ultimate Threat Hunting Tutorial Read More »