Introduction
In the digital age, every business, small or large, faces the risk of cyber threats. As a small business owner, you might think you’re not a likely target, and wouldn’t need endpoint security tools, but that’s a misconception.
In fact, small businesses are often more attractive to cybercriminals because they typically have less secure systems. This is where endpoint security tools come into play. They serve as your first line of defense, protecting your business from a wide range of cyber threats.
TLDR: Endpoint security tools are non-negotiable for small businesses. These tools serve as a shield against a myriad of cyber threats, from malware to zero-day attacks.
They offer real-time threat detection, behavioral analysis, and intrusion prevention, ensuring that all endpoints—be it computers, mobile devices, or IoT gadgets—are not exploited as entry points for cyber-attacks.
Advanced features like Endpoint Detection and Response (EDR) and behavioral analysis add layers of defense, adapting to evolving threats. A centralized management console streamlines security management, making it easier for teams to enforce policies and respond to incidents.
Investing in robust endpoint security tools is crucial for safeguarding your business assets and data.
Understanding Endpoint Security

Understanding the scope of endpoint security is crucial for effective protection. As depicted in the flowchart above, endpoint security solutions extend their shield to various types of devices connected to your network. These include:
- Computers: Traditional endpoints like desktops and laptops are safeguarded against malware and viruses.
- Mobile Devices: Security measures are in place to protect the data and applications on smartphones and tablets.
- IoT Devices: Internet of Things devices like smart thermostats and security cameras are monitored for suspicious network traffic.
By covering these diverse endpoints, endpoint security solutions ensure a holistic defense against cyber threats.
Endpoint Security Solutions
Endpoint security solutions are a type of cyber security software designed to protect various endpoints in your network. These endpoints could be computers, mobile devices, or even Internet of Things (IoT) devices. The primary goal of these solutions is to ensure that these devices do not become entry points for security threats.
Endpoint Protection Platform
An endpoint protection platform (EPP) is a unified solution that consolidates several security capabilities into one product to protect endpoints. It’s like a Swiss Army knife for cyber security. An EPP offers a range of tools from antivirus and anti-malware to firewall and intrusion prevention systems.
Endpoint security is not a one-trick pony; it’s more like a Swiss Army knife, equipped with a variety of tools to protect your business. As illustrated in the infographic, an Endpoint Protection Platform (EPP) offers multiple layers of defense:
- Antivirus: Scans and removes malicious software.
- Firewall: Blocks unauthorized access to your network.
- Data Loss Prevention: Ensures sensitive data remains secure.
- Intrusion Detection: Monitors and alerts on suspicious activities.
- VPN: Provides a secure connection for remote access.
- Encryption: Makes your data unreadable to unauthorized users.
Each tool serves a unique purpose, making the EPP a comprehensive solution for endpoint security. It’s essential to understand these features to choose the right protection for your business.

Endpoint Devices: From Mobile Devices to IoT Devices
In today’s interconnected world, an endpoint is no longer just a workstation in your office. It could be a laptop at a coffee shop, a smartphone in an employee’s pocket, or an IoT device like a smart thermostat in your office. All these devices, when connected to your business network, become potential entry points for cyber threats.
Endpoint devices are the gateways to your network, and they come in various shapes and sizes. As shown in the infographic, these can range from traditional computing devices like desktops and laptops to mobile gadgets like smartphones and tablets. Even wearables like smartwatches and Internet of Things (IoT) devices such as smart thermostats and security cameras are part of this ecosystem.
- Desktops & Laptops: The primary workstations for most businesses.
- Smartphones & Tablets: Essential for on-the-go connectivity.
- Smartwatches: Useful for quick notifications but can be a security risk.
- IoT Devices: Increasingly common in modern offices, these need special attention for security.
Understanding the diversity of endpoint devices is the first step in implementing a comprehensive endpoint security strategy. Make sure each type of device connecting to your network is adequately secured.
Key Features of Endpoint Security Tools
Choosing the right endpoint security tools involves understanding the key features that make for robust protection. Our infographic outlines the must-have features you should look for:
- Real-Time Threat Detection: Identifies and neutralizes threats as they happen.
- Behavioral Analysis: Studies patterns to detect abnormal activities.
- Intrusion Prevention: Blocks unauthorized access attempts.
- Data Encryption: Secures sensitive data.
- Firewall: Filters incoming and outgoing network traffic.
- VPN Support: Enables secure remote connections.
- Centralized Management: Simplifies security administration.
- Remote Access Control: Manages devices remotely.
- Software Updates: Keeps the security software up-to-date.
- Compliance Reporting: Helps meet regulatory requirements.
These features collectively create a strong defense mechanism, ensuring that all your endpoints are well-protected. Make sure to tick off these features when selecting your endpoint security tools.
Real-Time Threat Detection and Intrusion Prevention
Real-time threat detection and intrusion prevention are among the most critical features of endpoint security tools. These features work around the clock, continuously monitoring your network for any signs of malicious activity. They are designed to identify and neutralize threats as they occur, rather than after they have already infiltrated your network.
Consider a scenario where an employee accidentally clicks on a phishing email. The real-time threat detection feature of your tool would immediately recognize the threat. It would then isolate the affected system to prevent the malware from spreading to other parts of your network.
In another scenario, imagine a hacker trying to gain unauthorized access to your network by exploiting a software vulnerability. The intrusion prevention feature of your tool would detect this abnormal activity. It would then take immediate action to block the hacker, protecting your network from the potential breach.
These real-time capabilities are crucial in today’s fast-paced digital world. Threats evolve rapidly and can strike at any moment. Endpoint security tools detect and respond to threats in real-time. By doing so, they provide a robust defense that helps keep your business safe from cyber threats.
Behavioral Analysis: The Behavior-Based Approach to Endpoint Security
Behavioral analysis is a cutting-edge technique used by advanced endpoint security tools. These tools just don’t merely look for known threats. These tools scrutinize the behavior of files, applications, and network traffic to identify any abnormal activity that could indicate a threat.
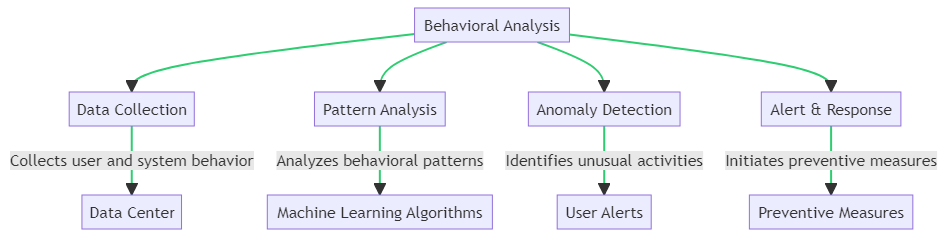
As illustrated in the flow diagram, the process involves several key steps:
- Data Collection: The system collects data on user and system behavior, storing it in a data center for analysis.
- Pattern Analysis: Machine learning algorithms analyze these behavioral patterns to establish a baseline.
- Anomaly Detection: Any deviation from the baseline is flagged as an unusual activity, triggering user alerts.
- Alert & Response: Finally, the system initiates preventive measures to mitigate the risk.
By continuously monitoring and analyzing behavior, endpoint security tools can proactively identify and respond to potential threats, enhancing your overall cybersecurity posture.
This approach is particularly effective against zero-day attacks. These attacks are new threats that haven’t been previously identified and, therefore, don’t have known signatures.
Let’s consider a use case. Suppose an employee receives an email with an attached document. The document doesn’t contain any known malware, so it passes the traditional signature-based checks.
Once the document is opened, it starts to behave suspiciously. Perhaps it tries to download a file from the internet or attempts to access sensitive system files. A behavior-based tool would identify unusual behavior when it detects it. Then it would take an appropriate action, such as blocking the document or alerting the security team.
Another use case could be an IoT device like a smart thermostat. Under normal circumstances, this device communicates with a specific set of servers to get weather updates and adjust the temperature.
For example, the device suddenly starts sending data to an unknown server. If that happens, a behavior-based tool would recognize this as atypical behavior. It could then take action to prevent potential data leakage.
In essence, behavioral analysis allows endpoint security tools to adapt to the ever-evolving threat landscape. Thus providing robust protection even against new and unknown threats.
Management Console: Centralized Control for Your Security Team
A management console in a tool serves as the central hub for your security operations. It provides a unified view of the security status across all your network endpoints. And so, making it easier for your security team to monitor and manage the overall security posture of your business.
One of the key use cases of a management console is in incident response. When a security incident occurs, the console can provide real-time alerts and detailed information about the incident. This information can be such things as the affected endpoints, the nature of the threat, and the actions taken by the tool. This allows your security team to quickly understand the situation and take appropriate actions.
Another use case is in policy management. The console allows your security team to define and enforce security policies across all endpoints. For example, they can set policies for password strength, software updates, and access controls. The console ensures these policies are consistently applied, reducing the risk of security gaps.
Finally, the management console also provides valuable insights and reports on your security status. This can help your security team identify trends, spot potential vulnerabilities, and make informed decisions to improve your security.
Device Manager: Ensuring Security Across All Devices
The device manager feature allows your security team to manage the security settings of all devices connected to your network. This includes installing updates, configuring security settings, and even remotely wiping data from lost or stolen devices.

Endpoint Detection and Response (EDR)
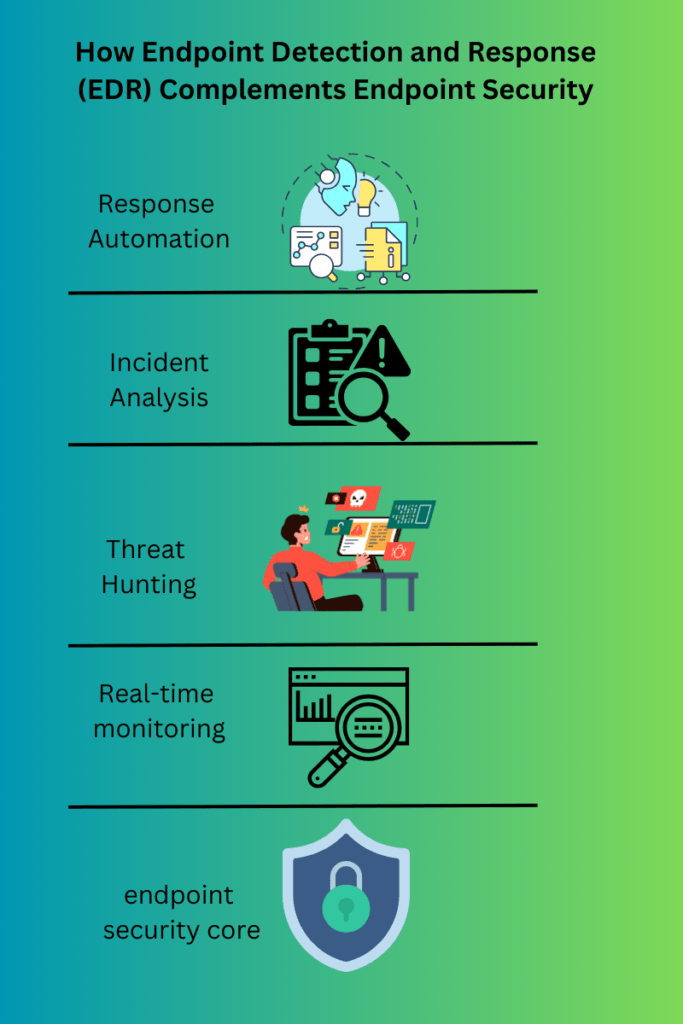
Endpoint Detection and Response (EDR) is not just an add-on but a vital layer that complements your existing endpoint security. As depicted in the infographic, EDR enhances endpoint security through:
- Real-time Monitoring: Constantly scans the endpoints for suspicious activities.
- Threat Hunting: Proactively searches for signs of compromise.
- Incident Analysis: Investigates and analyzes security incidents for root cause.
- Response Automation: Automates actions to contain and remediate threats.
By integrating EDR into your endpoint security strategy, you’re adding an extra layer of proactive defense, making it even harder for cybercriminals to penetrate your network.
Threat Intelligence and Incident Response
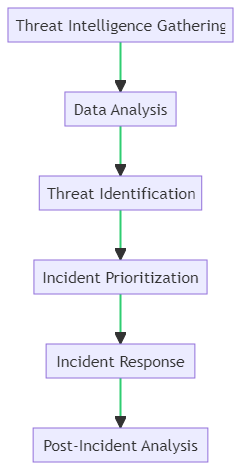
Understanding the flow from threat intelligence to incident response is crucial for effective endpoint security. As illustrated in the diagram, the process involves a series of sequential steps:
- Threat Intelligence Gathering: Collects data on potential threats from various sources.
- Data Analysis: Analyzes the gathered data to identify patterns and trends.
- Threat Identification: Flags potential threats based on the analysis.
- Incident Prioritization: Ranks the identified threats based on severity and impact.
- Incident Response: Takes appropriate actions to contain and mitigate the threats.
- Post-Incident Analysis: Reviews the incident to improve future responses.
Each step is integral to the next, creating a seamless process that ensures quick and effective response to cyber threats.
The Role of Threat Intelligence in Endpoint Protection
Threat intelligence involves gathering and analyzing information about potential or current attacks threatening the organization. These tools use this information to better identify and respond to threats, enhancing their effectiveness.
Incident Response: A Crucial Component of Endpoint Security Tools
Incident response is the process of managing and responding to a security breach. A good tool will have features to support this process. These features can be things like alerting the security team of potential breaches and providing tools to investigate and mitigate the breach.
Endpoint Security for Mobile Devices
The Importance of Securing Mobile Devices
Mobile devices are a significant part of today’s business operations. However, they also present unique security challenges. Endpoint protection tools can help secure these devices, protecting your business from threats that target mobile devices.
How Endpoint Security Tools Safeguard Mobile Devices
Tools can safeguard mobile devices by providing a range of security features, such as antivirus, anti-malware, firewall, and intrusion prevention systems. They can also enforce security policies, such as requiring a password to access the device.
Endpoint Security for IoT Devices
The Unique Challenges of Securing IoT Devices
IoT devices, like smart thermostats or security cameras, are becoming increasingly common in businesses. However, these devices often lack the built-in security features of traditional endpoints, making them a prime target for cybercriminals.
Endpoint Protection Solutions for IoT Devices
IoT devices, from smart thermostats to security cameras, are becoming increasingly common in businesses. However, these devices often lack the built-in security features of traditional endpoints, making them a prime target for cybercriminals. Endpoint protection solutions can help secure IoT devices by providing specialized security features.
For example, they can monitor network traffic to and from these devices to detect any suspicious activity. This is particularly important for devices like security cameras that are constantly connected to the internet and could be used by cybercriminals to gain access to your network.
In another use case, consider a smart thermostat in your office. While it offers convenience, it can also be exploited by a hacker to gain access to your network. Endpoint security tools can prevent this by ensuring that the thermostat is running the latest software and by monitoring its network activity for any signs of a breach.
Furthermore, in a scenario where a business uses IoT devices for inventory management, endpoint security tools can secure these devices, ensuring that inventory data remains confidential and that the devices themselves do not become entry points for cyber threats.
In essence, endpoint protection solutions offer a way to extend traditional cyber security measures to the growing number of IoT devices in the business environment. Thus ensuring comprehensive protection across all endpoints.
Choosing the Right Endpoint Security Product for Your Small Business
Factors to Consider When Selecting an Endpoint Security Tool
When selecting an endpoint security tool, consider factors like the types of devices you need to protect, the size of your business, and your budget. Also, look for a tool that offers the key features discussed earlier, such as real-time threat detection, behavioral analysis, and a management console.
Why Small Businesses Should Prioritize Endpoint Security
Endpoint security is not just for large enterprises. Small businesses are often targeted by cybercriminals because they are seen as an easy target. By investing in a good endpoint security tool, you can protect your business from these threats and ensure your business’s continuity.
Conclusion
Endpoint security tools are an essential part of any small business’s cyber security strategy. They provide a comprehensive solution to protect your business from a wide range of threats and ensure the security of your network and devices. By investing in a good tool, you can focus on growing your business without worrying about cyber threats.
Frequently Asked Questions
Q1: What do endpoint protection tools do? Endpoint protection tools are cyber security software that protects the endpoints in your network from cyber threats. They provide a range of security features, including real-time threat detection, behavioral analysis, and a management console.
Q2: What needs to be protected in endpoint security? In endpoint security, all devices connected to your business network need to be protected. This includes traditional endpoints like computers, as well as mobile and IoT devices.
Q3: What are the components of an endpoint protection platform? An endpoint protection platform includes several components, such as antivirus and anti-malware, firewall, intrusion prevention systems, and a management console.
Q4: Why endpoint protection is not enough? While endpoint protection is crucial, it’s not enough on its own. It needs to be part of a comprehensive cybersecurity strategy that includes other elements like user education, regular updates and patches, and a robust incident response plan.
Q5: How does endpoint security work? Endpoint security works by continuously monitoring the endpoints in your network for any signs of malicious activity

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


