What is an Endpoint Protection Platform?
What is an Endpoint Protection Platform (EPP)? It is like a security guard for your business’s computers and mobile devices. It helps protect your sensitive information by detecting and blocking cyber threats such as malware. The EPP can also fix (remediate) any issues that occur.
Imagine your business as a large, bustling mansion with many rooms. There are multiple entry points like doors, windows, and even secret passages. Each of these entry points represents an “endpoint” in the digital world, such as computers, smartphones, tablets, and servers.
You wouldn’t leave your mansion’s doors and windows wide open for anyone to enter. Just like that, you wouldn’t want unauthorized access to your business’s digital devices. That’s where an Endpoint Protection Platform (EPP) comes into play.
Think of EPP as a state-of-the-art security system for your mansion. It doesn’t just lock the doors and windows. The EPP also monitors for any suspicious activity. It can alert you if someone tries to break in. It even automatically takes action to prevent intruders.
A security system might use cameras, motion sensors, and alarms to protect your mansion. Similarly, an EPP uses tools like malware protection, real-time threat intelligence, and behavioral analysis to safeguard your digital devices. And the best part? Everything is managed from a centralized control room (or console). Thus, allowing you to have a bird’s-eye view of the entire mansion’s security.
So, in essence, an Endpoint Protection Platform is a sophisticated security system for your digital mansion. It ensures that all entry points are monitored and protected 24/7.

Key Takeaways:
- Comprehensive Security: EPP acts as a holistic security guard for digital devices, blocking malware and monitoring threats.
- Real-time Protection: It uses real-time threat intelligence and behavioral analysis to proactively detect and respond to cyber threats.
- Centralized Management: A central console allows for streamlined oversight and management of all security measures.
- Remediation Capabilities: EPP includes the ability to fix issues as they arise, ensuring continuous protection against potential damages.
An EPP is Important of EPP for Businesses
The EPP defends your system from threats like malware, including invisible fileless malware. EPP uses real-time detection and response to spot unusual behavior. This can prevent intrusions before they can harm your business. It also has remediation capabilities to fix issues, and a central console that makes managing this security easier. Think of it as a 24/7 digital watchdog for your business
What is Endpoint Protection?
Endpoint Protection is a specialized cyber security solution. It safeguards your business’s computers and mobile devices from threats like malware. It uses real-time detection and response mechanisms to identify and neutralize threats. By doing so, it protects sensitive information and prevents data loss.
Explanation of Endpoint Security Solutions
Endpoint security solutions protect your business’s computers and mobile devices from cyber threats. They offer malware protection, detect suspicious behavior in real-time, and help prevent data loss. With a central console, you can manage security across all devices. This helps to safeguard your sensitive information.
How Does an Endpoint Protection Platform Protects Endpoints?
An EPP uses real-time threat intelligence to spot dangers, including sneaky fileless malware. If it detects a threat, it takes action to fix the problem (remediation) and prevent data loss. It’s all managed from a central console. This makes it easier for you to keep your business’s sensitive information safe.
What Is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is like a security camera for your business’s computers and mobile devices. It constantly watches for suspicious activities. Activities such as attempts to install harmful software (malware). Or unauthorized access to sensitive information. When it spots something unusual, it alerts you in real time. Then it can take steps to fix the problem (remediation).
The EDR functions are all managed from a central console. This makes it easy for you to keep an eye on your business’s digital security. EDR is a crucial part of an Endpoint Protection Platform (EPP). EDR provides comprehensive protection for your business’s digital assets.
What is the difference between an EPP and an EDR?
Imagine your business as a store. An EPP is the security measures you put in place to prevent theft. For instance, locks on the doors, security tags on items, and surveillance cameras. Its primary job is to stop threats before they can cause harm.
On the other hand, an EDR (Endpoint Detection and Response) is like having a team of security experts. These experts constantly watch the surveillance footage. They study patterns, and investigate if they see someone acting suspiciously. A thief could manage to bypass the initial security measures. However, the EDR team is there to quickly spot and handle the situation.
In technical terms:
- EPP provides proactive security measures. It’s designed to prevent cyber threats from harming your business’s computers and devices. Think of it as your first line of defense.
- EDR is more reactive. It continuously monitors and analyzes data from endpoints (like your computers and smartphones). It does this to detect, investigate, and respond to any suspicious activities. It’s your backup team, ensuring that if something slips past the initial defenses, it’s caught and dealt with swiftly.
Having both EPP and EDR means you’re preventing potential threats. In addition, you’re also actively monitoring and responding to any that might find their way in. It’s a comprehensive approach to ensure your business’s digital safety.
What Is the Role of EPP and EDR in Endpoint Security?
EPP and EDR (Endpoint Detection and Response) work together to keep your business safe. EPP is like a security guard, It protects your computers and mobile devices from threats. EDR is the detective. It spots unusual behavior and responds in real-time to stop attacks. Together, they offer a complete security solution for your business.
Key Features of an Effective Endpoint Protection Platform
Malware Protection
Malware protection acts like a security guard. It scans and checks every piece of data that enters or leaves your business’s digital devices. It ensures harmful software, like viruses or ransomware, is caught and removed before causing damage.
For example, a local bakery’s computer was infected with ransomware after an employee clicked on a suspicious email link. The malware encrypted their customer database, demanding a ransom to unlock it. The ransomware could have been detected and removed before encrypting any files.
So, an EPP constantly watches for harmful software, known as malware. If it spots anything suspicious, it uses its detection and response capabilities to stop the threat in real time. It’s also smart, learning from each encounter to better protect your devices.
Besides this, it helps keep your sensitive information safe with data encryption. The central console manages all of this. Thus, making it easy for you to oversee your business’s cyber security.
Understanding Fileless Malware
Fileless malware is a sneaky intruder. Instead of hiding in files, it resides in a computer’s memory, making it harder to detect. Think of it as a thief who doesn’t leave footprints. EPPs are trained to spot and stop these elusive threats.
For example, a small law firm experienced slow computer performance. Unknown to them, fileless malware was using their system’s resources. It was using them to launch attacks on other businesses. An EPP with fileless malware detection would have identified the unusual behavior. Then it could have stopped the hidden threat.
In technical terms:
An EPP watches for sneaky fileless malware, which doesn’t use traditional files to harm your systems. Using real-time detection and response, EPP spots unusual behavior.
Once the threat is detected the EPP stops the threat and fixes the damage. It does all this from a central console. It’s a vital tool for protecting your sensitive information.
Multiple Detection Techniques
Relying on one method to catch threats is like using only one type of net to catch all kinds of fish. Some will slip through. EPPs use multiple techniques. This ensures a broader and more effective catch of potential threats.
For example, a family-owned store used basic antivirus software. Antivirus software can cattch older, known threats. However, a new type of malware would bypassed it. It can then steal customer credit card details. An EPP with multiple detection techniques would have recognized the new threat and blocked it
In technical terms:
These multiple detection techniques in an EPP act like a team of security guards. They use different methods to spot and stop cyber threats. For instance, one technique might look for known threats (like a guard checking a ‘most wanted’ list). Another technique might analyze behavior to spot suspicious activity.
A combination of multiple detection techniques can provide robust protection. Thus, ensuring your business’s sensitive information stays safe.
.
Real-Time Threat Intelligence
Real-time threat intelligence is like a guide for the security guard so it knows what to look for. This intelligence comes from various sources. These include global cyber security databases and local detection and response (EDR) systems. It’s like getting instant updates about new types of burglars and their tactics. Thus, allowing your EPP to prevent intrusions. EPP also protect your business’s valuable data in real-time.
Another way of looking at it is that threat intelligence is like having a network of lookouts. They are always watching for new threats and sharing information. When one lookout spots a danger, all others are alerted. EPPs use real-time intelligence to quickly identify and respond to emerging threats.
For example, a local clinic’s patient records were compromised by a new hacking technique. With real-time threat intelligence, their EPP could have been updated. It would have had information about this new technique. Thus, protecting before the breach occurred.
Behavioral Analysis
Behavioral analysis in an EPP is like a security guard who knows your daily routine. If you suddenly start acting differently, the guard becomes alert. Similarly, the EPP watches for unusual actions on your computer. Actions like a sudden download of large files, which could signal a malware attack.
For example, a small marketing agency downloaded a seemingly harmless software update. However, the update started sending confidential client data to an unknown location. Behavioral analysis would have noticed this unusual data transfer. It could have halted it, protecting the agency’s reputation and client trust.
With behavioral analysis, the EPP can take real-time action. These actions, such as blocking suspicious activity, can protect your sensitive information. This is a key part of EPP’s proactive defense strategy.
Intrusion Detection Systems
Think of an Intrusion Detection System (IDS) as a security camera for your business’s digital world. For instance, a camera monitors for any unauthorized individuals entering your physical store. In the same way, an IDS keeps an eye on your computer network. It watches for any suspicious activities or potential cyber threats. If it spots anything unusual, it sounds the alarm, alerting you to the potential danger.
In technical terms:
An Intrusion Detection System (IDS) in an EPP is like a security camera for your business’s computers. It watches for suspicious activities, such as attempts to access sensitive information or install harmful software (malware). For example, someone repeatedly tries to guess a password (behavioral analysis). In response, the IDS alerts you in real time, allowing for quick action (remediation) to prevent potential harm.
For example, a local bookstore had set up an online store to cater to more customers. One day, their IDS alerted them to multiple login attempts on their website. These attempts were coming from different countries in a short period. This was unusual because they primarily served local customers. Thanks to the IDS, they were able to quickly identify and block these unauthorized access attempts. In doing so, they prevented potential data breaches.
In another example, a popular cafe offered free Wi-Fi to its customers. One afternoon, their IDS detected an unusual spike in data transfer. This activity was from one of the devices connected to the network. They discovered a customer was trying to access and download the cafe’s customer database. The IDS’s alert allowed the cafe owner to disconnect the suspicious device and enhance their network security.
The Importance of a Central Console in An Endpoint Protection Platform
The central console of an Endpoint Protection Platform is like the control room for your business’s cyber security. It provides a unified view of all your devices (like computers and mobiles) and their security status. It’s where you can monitor for threats in real-time and manage malware protection. It can even control data encryption to protect sensitive information.
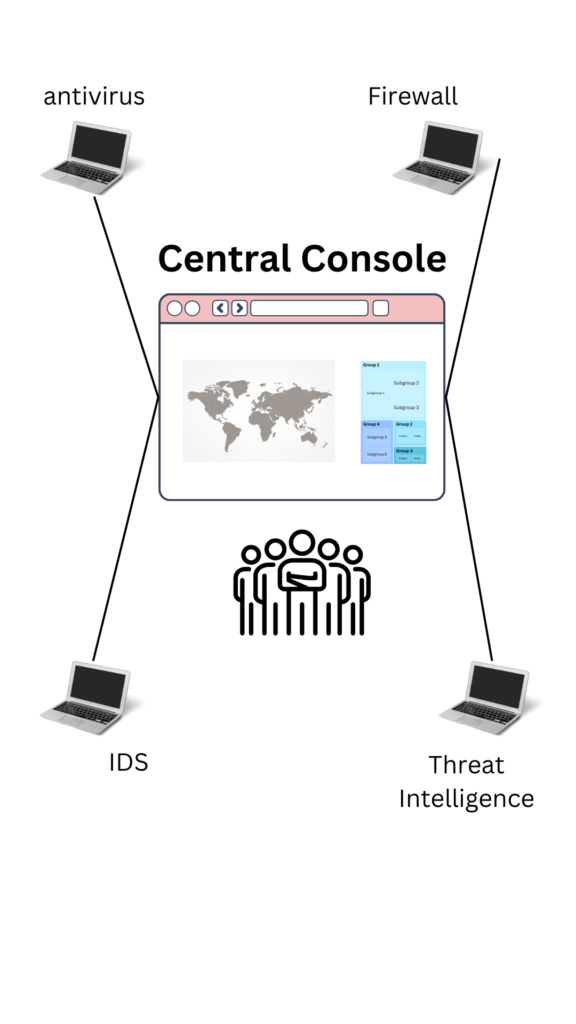
Benefits of Centralized Endpoint Security Management
Centralized Endpoint Security Management is a key feature of an EPP. It offers a single, unified console to monitor and manage your business’s cyber security. Centralizing management simplifies the process of protecting from threats like malware. It does this by providing real-time endpoint detection and response (EDR). This means it can quickly identify unusual behavior. Thus, it can stop potential attacks, and even fix (or “remediate”) any damage done.
Centralizing Management also helps secure sensitive information. It does this through data encryption and data loss prevention. In essence, it’s like having a 24/7 security guard all managed from one place.
Significance of a Centralized Console
Managing a business, especially a small one, is akin to juggling multiple tasks at once. Now, imagine adding multiple, separate security tools to that mix. Each tool has its own dashboard, alerts, and updates. It’s like trying to watch several TV shows at once – overwhelming and inefficient.
Challenges of Managing Multiple Security Products
- Overlapping Alerts. With different tools, you might receive multiple alerts for the same threat. This can lead to confusion and wasted time.
- Inconsistent Updates. Each tool might have its own update schedule. Keeping track of and implementing these updates can be a logistical nightmare.
- Complexity. Training staff to use multiple tools can be time-consuming. Plus, with different interfaces and protocols, the chances of human error increase.
- Cost. Without this, you need to purchase, renew, and maintain licenses for multiple products. This can strain a small business’s budget.
Advantages of an Integrated EPP Approach with a Centralized Console
- Unified View. A centralized console offers a single, comprehensive view of your business’s security posture. It’s like having a command center where you can see everything at a glance.
- Streamlined Alerts. With a centralized console, you receive consolidated and prioritized alerts. This helps you respond faster.
- Consistent Updates. With an integrated approach, updates are synchronized, ensuring that your security tools are always on the same page.
- Simplified Training. Staff only need to familiarize themselves with one system. This reduces the learning curve and potential mistakes.
- Cost-Efficient. Investing in an integrated solution is often more cost-effective in the long run. This is because it eliminates the need for multiple licenses and reduces administrative overhead.
In essence, a centralized console in an EPP streamlines your cybersecurity efforts. It makes it easier to monitor, respond, and protect your business from threats. It’s a smarter, more efficient approach. This is especially crucial for businesses that need to maximize resources and protection.
Data Protection Strategies
Safeguarding Sensitive Data: Why It’s Crucial for Small Businesses
Imagine your small business as a cozy, local cafe. Your regular customers trust you. They come in and share stories. Sometimes even personal details like upcoming vacation plans or their child’s graduation. Now, what if someone overheard these conversations and misused the information? Not only would it be a breach of trust, but your cafe’s reputation would be at stake.
Similarly, you hold valuable information – from customer details to financial records. This is your business’s lifeblood. Just like those personal conversations in the cafe, this data needs protection. If this information were to fall into the wrong hands, it could lead to financial losses, legal troubles, and a tarnished reputation. For businesses, where trust plays a pivotal role, such breaches can be devastating.
Moreover, data breaches aren’t just a concern for big corporations. Small businesses are often seen as easier targets by cybercriminals. This is because they might not have the same robust security measures in place. Safeguarding sensitive data isn’t just about preventing financial loss. Safeguarding sensitive data is about preserving trust and relationships.
So, just as you’d protect the personal conversations in your cafe, it’s vital to shield your business’s digital data. By doing so, you’re not only securing your business assets. You’re also upholding the trust and confidence that your community places in you.
Protecting Sensitive Information
An EPP safeguards your business’s sensitive information. It does this by using data encryption and data loss prevention techniques. It’s like a security guard for your digital data. It constantly monitors and blocks any suspicious activities.
If a threat is detected, the EPP takes immediate action to prevent harm. It can respond and fix issues in real-time. It’s a comprehensive security solution. It keeps your business’s digital doors locked and secure.
Data Encryption
Data encryption is a key feature of an EPP). It secures your business’s sensitive information by converting it into code. This prevents unauthorized access, even if a breach occurs.
Think of data encryption as a secret language only your system understands. Thus, keeping your data safe from threats like malware. It’s a crucial part of a comprehensive endpoint security solution that protects your business in real-time.
A more detailed but not technical explanation of encryption
Imagine you have a secret letter that you want to send to a friend. However, you’re worried that someone else might read it along the way. So, instead of sending the letter as it is, you use a special code to scramble the message. To anyone else, the scrambled message looks like random letters and symbols. It makes no sense at all. But your friend, who knows the special code, can easily decode it and read the original message.
Encryption works in a similar way. It’s like a protective shield for your information. Before this data is stored or sent, it’s scrambled using complex mathematical algorithms. Only someone with the right “key” (like the special code for your secret letter) can decode and access the original information.
So, in simple terms, encryption is a way to keep your digital secrets truly secret, ensuring they’re safe from prying eyes.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) in an Endpoint Protection Platform (EPP) is like a vigilant guard for your business data. It monitors and protects sensitive information from being exposed or stolen. DLP uses smart detection techniques and real-time responses. By doing so, it can spot potential threats and take immediate action.
Think of DLP as a safety net. It catches any data that might accidentally slip or be maliciously pushed out of your business.
A more detailed but non-technical explanation of data loss prevention
Imagine you run a store where you keep a special ledger with details of all your customers, sales, and inventory. This ledger is crucial for your business. Now, you wouldn’t want this ledger to be accidentally thrown away, left out in the rain, or taken by someone, would you? To prevent this, you might put the ledger in a secure drawer, make copies as a backup, and set rules like “Only the manager can take the ledger outside.”
Data Loss Prevention (DLP) is like those protective measures for your ledger, but for your electronic data. It’s a set of tools and practices that ensure important information doesn’t get accidentally deleted, exposed, or stolen. DLP systems can detect potential data breaches or leaks. It can then prevent them by monitoring, alerting, and blocking sensitive data while it’s being used, shared, or moved across the company’s network.
In simple terms, Data Loss Prevention makes sure data stays safe and sound.
Mobile Device Security
Navigating the Challenges in a BYOD Era
Today, the line between office and home has blurred. More employees are working remotely. The convenience of smartphones and tablets has made it possible to work from virtually anywhere. This is coupled with the growing trend of BYOD (Bring Your Own Device) policies. The combination has brought a new set of challenges for small businesses.
BYOD Challenges
- Diverse Devices. Employees might use a variety of devices. Each device has its own operating system, settings, and vulnerabilities. This diversity makes it harder to maintain a consistent security protocol.
- Unsecured Networks. Remote workers often connect to public Wi-Fi networks – in cafes, airports, or hotels. These networks are typically less secure. This makes it easier for cybercriminals to intercept data.
- Lost or Stolen Devices. Mobile devices are portable and can easily be misplaced or stolen. If not adequately protected, sensitive business data stored on these devices can fall into the wrong hands.
- Personal and Professional Data Overlap. On personal devices, there’s often a mix of business files with personal photos, apps, and data. This overlap can pose risks if personal apps or sites become a gateway for malware.
BYOD Solutions
- Mobile Device Management (MDM). MDM solutions allow businesses to remotely manage and monitor devices connected to their network. This means you can enforce security protocols, update software, or even wipe data from a device if it’s lost or stolen.
- Virtual Private Networks (VPNs). Encourage employees to use VPNs when accessing business data. VPNs create a secure tunnel for data transmission, ensuring that even if someone intercepts the data, they can’t read it.
- Regular Training. Periodically train your staff on mobile security best practices. This can include guidance on setting strong passwords, recognizing phishing attempts, and ensuring apps are downloaded from trusted sources.
- Separation of Personal and Professional Data. Use apps or software that create a distinct workspace on personal devices. This ensures business data is cordoned off and adds an extra layer of protection.
- Immediate Reporting. Establish a protocol for employees to quickly report lost or stolen devices. The faster you know, the quicker you can take protective actions.
Today, mobile device security isn’t just an IT concern; it’s a business imperative. It’s important to understand the challenges and implement robust solutions. This ensures that you are protecting your data. Furthermore, you are also empowering their employees to work flexibly and efficiently.
Importance of Mobile Device Protection in an Endpoint Protection Platform
Mobile device protection in an EPP safeguards your business phones and tablets from cyber threats. It uses malware protection and real-time detection to spot and block harmful activities. EPP also encrypts sensitive information on your devices, preventing data loss. It’s like a security guard for your mobile devices, keeping your business safe.
EPP Solutions for Mobile Devices
EPP solutions for mobile devices are like bodyguards for your phone or tablet. They protect your business data from threats like malware, including sneaky fileless malware. Using real-time detection and response, they spot unusual behavior and stop intrusions.
If a threat does slip through, remediation capabilities help fix the damage. A central console manages all of this, making it easy for you to keep your business safe. Think of it as a security system for your mobile devices, keeping your sensitive information secure.
Remediation Capabilities of An Endpoint Protection Platform
Remediation on an EPP is the process of fixing security issues detected on your devices. It’s like a cleanup crew that comes in after a threat is found. Thus ensuring your business’s digital safety by repairing any damage done by cyber threats.
Understanding Remediation in An Endpoint Protection Platform
Remediation in Endpoint Protection Platform (EPP) is like fixing a broken lock. When EPP detects a threat, like malware, it doesn’t just alert you. The EPP takes action to fix the problem. This could involve removing the threat or repairing affected files.
Remediation is a crucial part of an EPP’s real-time protection. It ensures your business data and devices stay safe from cyber threats. It’s like having a 24/7 cyber security team, all managed from a central console.
Role of EDR Solutions in Remediation
Today, businesses need more than just preventive measures. Enter EDR, or Endpoint Detection and Response.
What is EDR?
EDR solutions continuously monitor and gather data from endpoints. Endpoints are devices like computers, tablets, and smartphones. They analyze this data to detect suspicious patterns or behaviors. These behaviors might indicate a cyber threat. But EDR doesn’t stop at just detection. EDR also responds to these threats. It can respond either by isolating the affected device or by removing the malicious software. Thus, ensuring minimal damage.
Significance of EDR
- Real-time Monitoring: While traditional security tools might wait for a scheduled scan to identify threats, EDR is always on, offering real-time protection.
- Detailed Forensics: EDR provides in-depth insights into how a breach occurred, helping businesses understand the threat and prevent future attacks.
- Swift Response: Time is of the essence in cybersecurity. EDR solutions can automate responses, ensuring threats are dealt with immediately, often before they can cause significant harm.
Integration with EPP for a Comprehensive Security Solution
EPP is like the shield, offering a first line of defense against known threats. On the other hand, EDR is the watchful guardian, looking out for new, unknown threats. When integrated, EPP and EDR offer a three-pronged approach:
- Prevention and Detection. EPP prevents known threats using its database of recognized malware. EDR detects unusual behaviors, catching threats that might be new or previously unidentified.
- Automated Response and Remediation. If EDR detects a threat, it can leverage EPP’s tools to isolate or remove the threat. Thus, ensuring a seamless and swift response.
- Unified Management. With integrated EPP and EDR solutions, businesses benefit from a centralized console. This simplifies management and ensures consistent security protocols across all devices.
In conclusion, EPP provides a robust foundation for cybersecurity. By integrating EDR, businesses are not just reactive but proactive in their defense strategy. Together, they offer a comprehensive security solution. This ensures that businesses stay one step ahead of cyber threats.
Guidelines for Choosing an EPP: Finding the Right Fit for Your Small Business
Navigating the myriad variety of EPPs can feel like wandering through a maze. This is especially true when you’re trying to find the best fit for your small business. But fear not! Here’s a roadmap to guide you in making an informed decision.
Understanding Your Needs
Before diving into the sea of EPP options, take a moment to assess your business’s specific needs. How many devices do you need to protect? Do you have remote workers? What kind of data are you handling? Answering these questions will give you a clearer picture of what you’re looking for
Comprehensive Protection
Ensure the EPP offers a wide range of protection features. They vary from basic antivirus capabilities to more advanced features like fileless malware detection and behavioral analysis. Remember, cyber threats are evolving. You want to find a solution that’s prepared for both current and emerging threats
User-Friendly Interface
As a small business manager, you might not have a dedicated IT team. Opt for an EPP with an intuitive, user-friendly interface. This ensures that you or your team can easily manage and monitor security without a steep learning curve.
Scalability
Your business will grow, and so will your cybersecurity needs. Choose an EPP that’s scalable, allowing you to add more devices or features as your business expands.
Integration with Other Tools
Are you already using other security tools? Are you considering adding more layers of protection in the future? Then ensure the EPP you choose integrates well with other platforms. This ensures a seamless security experience and simplifies management.
Support and Training
Especially crucial for small businesses, ensure the EPP provider offers robust customer support. Whether it’s a technical glitch or a query about a feature, you want to know help is just a call or click away. Additionally, check if they provide training resources to help you make the most of the platform.
Cost Efficiency
While it’s essential to invest in good cybersecurity, small businesses also need to be mindful of budgets. Compare different EPP solutions, considering both their features and pricing. Look for solutions that offer a good balance of cost and comprehensive protection.
Reviews and Recommendations
Do a bit of homework. Look for reviews from other small businesses or industry experts. Personal recommendations can also be invaluable. Hearing about real-life experiences with the EPP can give you insights that product descriptions might miss.
So, choosing the right EPP for your small business is a crucial decision. However, with the right guidelines, it doesn’t have to be a daunting one. Prioritize your needs, do your research, and opt for a solution that offers robust protection. All the while aligning with your business’s unique requirements.
Conclusion: EPP is the Cornerstone of Cybersecurity for Small Businesses
The threats lurking in the shadows of the online world are ever-evolving. This makes the protection of your business’s data and devices paramount. We’ve traversed the landscape of Endpoint Protection Platforms (EPP).
We’ve highlighted their pivotal role in:
- Offering Comprehensive Protection. We have covered advanced features like behavioral analysis and malware detection. EPPs can serve as your business’s first line of defense against cyber threats.
- Facilitating Proactive Defense with EDR. By integrating EPP with EDR solutions, businesses can detect and prevent threats. This ensures a holistic security approach.
- Simplifying Security Management. EPP features like centralized consoles and EPP streamline the management of your cybersecurity. This makes it accessible even for those without a technical background.
- Adapting to Your Business Needs. The right EPP adapts to your business’s unique requirements, ensuring growth and flexibility. This is true whether it is scalability, integration with other tools, or user-friendly interfaces.
With all its opportunities, the digital world also brings challenges. But with the right EPP, businesses can navigate this realm confidently. They will know they’re shielded from potential threats. As you chart your business’s cybersecurity journey, remember that an EPP isn’t just a tool; it’s a cornerstone of your digital safety.
Take the Next Step!! The world of cybersecurity is vast, and there’s always more to learn. We encourage you to explore more resources here on this site. Empowering yourself with knowledge. Ensure your business remains a fortress in the digital age.
Frequently Asked Questions
What does an endpoint protection do?
What is endpoint security meant to protect?
What are examples of endpoint security?
What is the difference between endpoint protection and antivirus?

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!



This post was incredibly informative! I now have a much better understanding of what an Endpoint Protection Platform (EPP) is and how it plays a vital role in safeguarding businesses from cyber threats.I do have a question regarding the role of Endpoint Detection and Response (EDR) in remediation. How does EDR specifically fix issues that are detected on devices? Is it an automated process, or does it require manual intervention from the user or IT staff?Overall, I’m impressed with the level of detail provided in this post. Keep up the good work!
Good point, I will make sure the article talks about this. The answer is… both. (I used to do this). Some things are so darn obvious you can block it (traffic from North Korea or other countries where you have no intention of ever doing business, an improperly formatted request, a request that is obviously an attempt to attack your site, etc). Others are more subtle and may require that it alert the analyst who can then block the internet address it is coming from, research it online to see if it is a bad address, etc.