Introduction to Endpoint Security Management
Today, the need for endpoint security is more critical than ever. Ensuring your business’s endpoints are protected can prevent data breaches and maintain your organization’s security posture. This article will give you the essential features of endpoint management. We will highlight why it’s worth your time to learn about and implement these tools and strategies.
Our new book on cybersecurity for small business will help you get a leg up on hackers

Key Takeaways
- Protection and Detection: Antivirus, antimalware, and EDR provide essential security measures.
- Access and Control: MFA, NAC, and application/device control enhance security.
- Data Security: Data encryption, backup and recovery, and cloud security protect sensitive information.
- Network and Communication Security: VPN, web filtering, and email security secure network communications.
- Management and Compliance: MDM, patch management, and policy enforcement ensure compliance and security.
- User and Device Behavior: UEBA, security awareness training, and performance monitoring help detect and respond to threats.
Feature Summary
| Category | Feature | Description |
|---|---|---|
| Protection and Detection | Protection and detection are the foundation of endpoint security, crucial for defending against malicious activities and potential breaches. | |
| Antivirus and Antimalware | Essential tools that detect and remove malicious software from endpoint devices. | |
| Endpoint Detection and Response (EDR) | Provides continuous monitoring and quick response to potential security threats. | |
| Firewall | Monitors and controls network traffic, preventing unauthorized access and enhancing security. | |
| Intrusion Detection and Prevention Systems (IDPS) | Identifies and blocks potential security breaches, enhancing network security. | |
| Threat Intelligence | Gathers and analyzes data on emerging threats, enabling proactive protection against attacks. | |
| Access and Control | Access and control features manage network access and ensure only authorized users and devices can connect. | |
| Multi-Factor Authentication (MFA) | Adds an extra layer of security by requiring multiple forms of verification for access. | |
| Network Access Control (NAC) | Ensures only compliant and authorized devices can access the network. | |
| Application Control | Restricts unauthorized applications from running on endpoint devices. | |
| Device Control | Manages the use of external devices like USBs to prevent unauthorized data transfers. | |
| Data Security | Data security focuses on protecting sensitive information from unauthorized access and loss. | |
| Data Encryption | Protects data by making it unreadable to unauthorized users. | |
| Backup and Recovery | Ensures data availability by regularly backing up information and enabling quick restoration. | |
| Cloud Security | Protects data and applications hosted in the cloud from potential threats. | |
| Network and Communication Security | Securing network and communications prevents unauthorized access and data breaches. | |
| Virtual Private Network (VPN) | Secures remote connections to your network by encrypting data transmitted over the internet. | |
| Web Filtering | Blocks access to harmful websites, protecting the network from web-based threats. | |
| Email Security | Detects and blocks phishing attempts and malware-infected emails to protect against email-based attacks. | |
| Management and Compliance | Effective management and compliance ensure a strong security posture and regulatory adherence. | |
| Mobile Device Management (MDM) | Manages and secures mobile devices accessing the network, enforcing security policies. | |
| Patch Management | Regularly updates software with the latest security patches to protect against vulnerabilities. | |
| Policy Enforcement | Ensures security policies are consistently applied across all endpoints. | |
| Compliance Management | Ensures adherence to regulatory requirements, protecting sensitive data and maintaining trust. | |
| Centralized Management Console | Provides a single interface for managing all endpoint security measures, improving visibility and efficiency. | |
| User and Device Behavior | Monitoring user and device behavior is essential for detecting anomalies and preventing potential threats. | |
| Endpoint Hardening | Enhances security by configuring devices securely and minimizing their attack surface. | |
| User and Entity Behavior Analytics (UEBA) | Analyzes user behavior to detect anomalies and potential security threats. | |
| Security Awareness Training | Educates employees on security best practices to reduce the likelihood of human error. | |
| Performance Monitoring | Tracks the performance and health of endpoint devices to identify potential issues early. | |
| Incident Response | Plans and procedures for responding to security incidents to mitigate threats quickly and effectively. |
The Evolution of Endpoint Threats
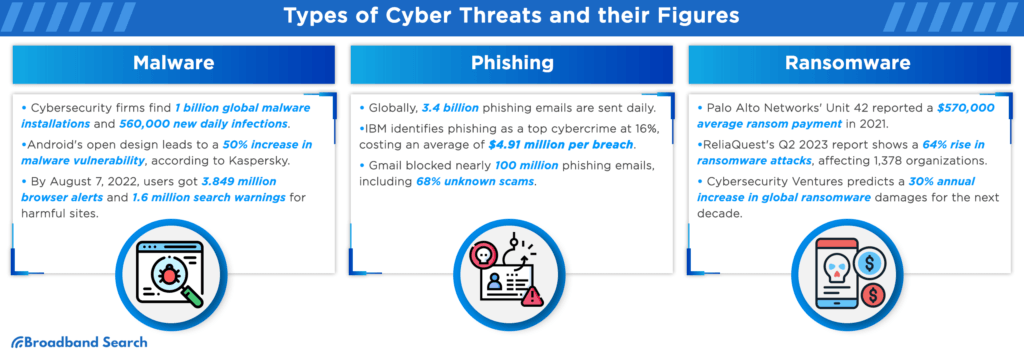
Source: Broadband Search
Endpoint threats include malware, phishing, and ransomware attacks.
In statistics reported by Broadband Search in 2023:
- Worldwide, reports indicate approximately 560,000 daily infections
- One in 4200 emails is a phishing attempt
- 1378 organizations fell victim to a ransomware attack in Q2 2023, a 64% increase from the previous quarter
The evolution of endpoint threats, particularly focusing on malware, phishing, and ransomware, reflects the rapidly changing landscape of cyber threats faced by organizations worldwide.
Malware: Where Threats Started
In the early days of computing, malware was relatively simple, often designed more for mischief than for serious harm. These initial forms of malware paved the way for more sophisticated and damaging variants. As internet connectivity became ubiquitous, the scale and complexity of malware attacks grew. This lead to widespread disruptions and significant financial damages.
Phishing: Social Engineering and the Internet
Phishing emerged as a significant threat in the late 1990s. It has evolved from basic email scams to highly sophisticated social engineering attacks. Early phishing attempts were often easy to spot due to poor language and obvious errors. However, today’s phishing emails can be indistinguishable from legitimate communications. Attackers now use personalized information, hijacked email accounts, and social media to craft convincing messages, making phishing one of the most prevalent and effective forms of cyberattacks.
Ransomware: A Sophisticated Attack
Ransomware, a more recent but equally significant threat, has evolved rapidly. Initial ransomware attacks were relatively basic, locking screens or encrypting files and demanding payment. However, modern ransomware has become highly advanced. It targets specific organizations, using robust encryption methods, and even exfiltrating data for double extortion. The rise of cryptocurrencies has further facilitated the proliferation of ransomware by providing attackers with a secure and anonymous means of receiving payments.
This evolution of endpoint threats underscores the necessity for continuous adaptation in cybersecurity strategies. Organizations must not only defend against current threats but also anticipate and prepare for the future tactics and techniques that cybercriminals will inevitably develop.
What are the Main Objectives of Endpoint Security Management?
The main objectives of endpoint security management are to ensure the security, integrity, and availability of endpoint devices within a network. The Security Triad is what we commonly refer to as the basic concept.
These objectives are fundamental in protecting both the endpoints themselves and the broader network and data they interact with.
Comprehensive Threat Detection Capabilities
Multi-Layered Threat Detection

In the realm of endpoint security management, multi-layered threat protection is a comprehensive approach that employs various defensive mechanisms at different levels to guard against a wide range of cyber threats. This strategy recognizes that no single defense can offer complete protection against the sophisticated and evolving nature of modern cyber threats, including malware, phishing, and ransomware.
The core principle behind multi-layered threat protection is “defense in depth,” which involves layering multiple security measures to create a robust security posture. The layers typically include perimeter defenses like firewalls and intrusion detection systems, network-level defenses such as traffic analysis and anomaly detection, and endpoint-specific protections like antivirus software, anti-malware solutions, and endpoint detection and response (EDR) systems.
Moreover, multi-layered protection also encompasses proactive measures like regular software updates and patches, employee cybersecurity training to recognize and avoid phishing attacks, and strong access control policies. These layers work in concert to identify, prevent, and mitigate threats at various stages of an attack, from initial entry through to post-breach activities.
Implementing multi-layered threat protection minimizes the risk of a successful breach and ensures a robust security stance. It provides comprehensive coverage against diverse threats, making it difficult for attackers to penetrate the network and reducing the potential impact of any single security failure. This approach is essential in today’s complex cybersecurity landscape, where relying on a single line of defense is no longer adequate.
Protection and Detection: Why is Protection and Detection Crucial for Endpoint Security?
Protection and detection are the foundation of endpoint security. By implementing robust antivirus, firewall, and threat intelligence measures, managers can proactively defend against malicious activities and potential breaches. Understanding these tools’ roles will help you enhance your organization’s security posture, ensuring continuous protection and quick response to threats.
1. How Do Antivirus and Antimalware Work?
Antivirus software and antimalware software are essential endpoint security tools that detect and remove malicious software from endpoint devices. They continuously monitor for threats, ensuring that unauthorized software doesn’t compromise your system’s security.
2. Why is Endpoint Detection and Response (EDR) Important?
Endpoint Detection and Response (EDR) is crucial because it provides continuous monitoring and detection of security threats. EDR systems offer visibility into endpoint activities, allowing for quick response to potential security breaches. This proactive approach helps maintain the security posture of your organization.
3. How Does a Firewall Enhance Endpoint Security?
A firewall is a fundamental component of endpoint security management. It monitors and controls incoming and outgoing network traffic based on predetermined security policies. Firewalls act as a barrier between your internal network and external sources, preventing unauthorized access and protecting against network security threats. By implementing a robust firewall, you can significantly reduce the risk of data breaches and malicious attacks on your endpoints.
4. What are Intrusion Detection and Prevention Systems (IDPS)?
Intrusion Detection and Prevention Systems (IDPS) are critical for identifying and preventing potential security breaches. These systems monitor network traffic for suspicious activities and policy violations, alerting administrators to potential threats. IDPS can also take proactive measures to block malicious traffic and prevent attacks. By incorporating IDPS into your endpoint security strategy, you enhance your ability to detect and respond to security incidents, protecting your network from unauthorized access and other security risks.
5. How Does Threat Intelligence Improve Security?
Threat intelligence is a vital aspect of endpoint security that involves gathering and analyzing data on emerging cyber threats. By staying informed about the latest threats and vulnerabilities, you can proactively protect your endpoints against potential attacks. Threat intelligence provides valuable insights into the tactics, techniques, and procedures used by cybercriminals, enabling you to implement more effective security measures. Incorporating threat intelligence into your endpoint security management helps you stay one step ahead of attackers and ensures the continuous protection of your network.
Access and Control: How Do Access and Control Features Enhance Endpoint Security?
Access and control are vital for managing who can access your network and what they can do. Implementing measures like Multi-Factor Authentication (MFA) and Network Access Control (NAC) helps prevent unauthorized access, while application and device control ensure that only authorized software and devices are used. These features are essential for maintaining tight security and protecting sensitive data from unauthorized users.
6. What is Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring multiple forms of verification for access to endpoints. This reduces the risk of unauthorized access and ensures that only authorized users can access sensitive information.
7. How Does Network Access Control (NAC) Enhance Security?
Network Access Control (NAC) enhances security by ensuring that only compliant and authorized devices can access the network. NAC systems enforce security policies, preventing unauthorized devices from connecting and potentially compromising network security.
8. The Role of Application Control in Endpoint Security
Application control restricts unauthorized applications from running, while device control manages the use of external devices like USBs. These measures help prevent the introduction of malware and unauthorized data transfers.
9. The Role of Device Control in Endpoint Security
Device control is critical for managing the use of external devices like USBs. By restricting unauthorized devices, you prevent the introduction of malware and unauthorized data transfers, maintaining the integrity of your endpoint security system.
Data Security: What Are the Best Practices for Ensuring Data Security?
Data security focuses on protecting sensitive information from unauthorized access and loss. Techniques like data encryption, regular backups, and cloud security measures are crucial for safeguarding data. Managers must prioritize these practices to ensure that data remains secure and available, even in the event of a breach or system failure.
10. The Importance of Data Encryption
Data encryption is essential for protecting sensitive information from unauthorized access. By encrypting data, you ensure that even if it is intercepted, it remains unreadable and secure. This is a fundamental aspect of endpoint security management.
11. Backup and Recovery: Ensuring Data Availability
Backup and recovery solutions are crucial for maintaining data availability in case of a breach or system failure. Regular backups ensure that your data can be restored quickly, minimizing downtime and data loss.
12. How Does Cloud Security Protect Your Data?
With the increasing use of cloud services, cloud security has become a vital component of endpoint security. Cloud security measures protect data and applications hosted in the cloud from potential threats, ensuring the integrity and confidentiality of your information.
Network and Communication Security: How Can Network and Communication Security Protect Your Business?
Securing your network and communications is essential to prevent unauthorized access and data breaches. Utilizing tools such as Virtual Private Networks (VPNs), web filtering, and email security can protect your network from various threats. These measures ensure that data transmitted across your network is secure and that employees are shielded from malicious web and email content.
13. Why Use a Virtual Private Network (VPN)?
A Virtual Private Network (VPN) secures remote connections to your network, encrypting data transmitted over the internet. This prevents unauthorized access and ensures that sensitive information remains protected during remote access.
14. How Does Web Filtering Protect Your Network?
Web filtering blocks access to harmful websites, protecting your network from web-based threats such as phishing and malware. By preventing users from visiting dangerous sites, web filtering enhances your overall security posture.
15. How Does Email Security Protect Your Network?
Email security solutions are essential for detecting and blocking phishing attempts and malware-infected emails. They protect against email-based attacks, which are common vectors for malware and data breaches.
Management and Compliance: What Are the Key Aspects of Management and Compliance in Endpoint Security?
Effective management and compliance are critical for maintaining a strong security posture and meeting regulatory requirements. Tools like Mobile Device Management (MDM), patch management, and a centralized management console help ensure that all endpoints are secure and compliant. By prioritizing these aspects, managers can streamline security processes and maintain control over their organization’s security infrastructure.
16. Mobile Device Management (MDM): Keeping Mobile Endpoints Secure
Mobile Device Management (MDM) is vital for securing mobile endpoints accessing your network. MDM solutions enforce security policies on mobile devices, ensuring that they comply with your organization’s security standards.
17. The Importance of Patch Management
Patch management ensures that all software is up-to-date with the latest security patches. Regular updates protect against known vulnerabilities, reducing the risk of security breaches and enhancing the overall security of your endpoints.
18. Ensuring Policy Enforcement
Policy enforcement is critical for maintaining a strong security posture. By ensuring that security policies are consistently applied across all endpoints, you reduce the risk of non-compliance and potential security threats. Policy management helps to standardize security measures and ensures that all endpoint devices adhere to the organization’s security protocols.
19. Compliance Management
Compliance management is essential for adhering to regulatory requirements and avoiding penalties. It ensures that your organization’s security measures align with industry standards and legal mandates, protecting sensitive data and maintaining trust with stakeholders.
20. Centralized Management Console
A centralized management console provides a single interface for managing all endpoint security measures. This centralized approach simplifies administration, improves visibility into endpoint security, and allows for more efficient management of security policies and updates.
User and Device Behavior: How Does Monitoring User and Device Behavior Enhance Endpoint Security?
Monitoring user and device behavior is essential for detecting anomalies and preventing potential threats. Techniques such as User and Entity Behavior Analytics (UEBA) and endpoint hardening can identify unusual activities and strengthen device security. Managers must focus on these practices to proactively address security risks and ensure that all endpoints are adequately protected.
21. How User and Entity Behavior Analytics (UEBA) Detect Anomalies
User and Entity Behavior Analytics (UEBA) analyze user behavior to detect anomalies and potential security threats. By identifying unusual activities, UEBA helps prevent insider threats and compromised accounts.
22. The Benefits of Security Awareness Training
Security awareness training educates employees on security best practices, reducing the likelihood of human error leading to a security incident. This training is an essential part of a comprehensive endpoint security strategy.
23. Performance Monitoring
Performance monitoring is essential for maintaining endpoint security. By tracking the performance and health of endpoint devices, you can identify potential issues before they become critical, ensuring the continuous protection and efficiency of your endpoint security system.
24. The Role of Incident Response
Incident response involves having plans and procedures in place for responding to security incidents. Effective incident response ensures quick and effective mitigation of security threats, minimizing damage and reducing recovery time. This proactive approach is crucial for maintaining the integrity of your endpoint security management strategy.
25. How Does Endpoint Hardening Improve Security?
Endpoint hardening involves enhancing the security of endpoint devices by configuring them securely and minimizing their attack surface. This process includes disabling unnecessary services, applying security patches, and configuring system settings to improve security. By hardening endpoints, you reduce the risk of exploitation and ensure that devices are less vulnerable to attacks.
Key steps in endpoint hardening include:
- Disabling Unnecessary Services: Turn off services and applications that are not required for the device’s primary function, reducing potential entry points for attackers.
- Applying Security Patches: Regularly update software and operating systems with the latest security patches to protect against known vulnerabilities.
- Configuring Security Settings: Adjust system settings to enforce strong security practices, such as enabling firewalls, using strong passwords, and implementing account lockout policies.
By systematically hardening endpoints, you can significantly enhance the overall security posture of your organization, making it more difficult for attackers to compromise your devices.
Our new book on cybersecurity for small business will help you get a leg up on hackers

Learn more about each Endpoint Security Feature!
Endpoint security is vital for protecting your business from cyber threats. By understanding and implementing these essential features, you can enhance your organization’s security posture, prevent unauthorized access, and safeguard sensitive data.
Key features include:
- Protection and Detection: Utilize antivirus, EDR, firewalls, IDPS, and threat intelligence for robust defense.
- Access and Control: Implement MFA, NAC, application control, and device control to manage access effectively.
- Data Security: Protect data with encryption, backup and recovery solutions, and cloud security.
- Network and Communication Security: Secure communications with VPNs, web filtering, and email security.
- Management and Compliance: Ensure security with MDM, patch management, policy enforcement, compliance management, and a centralized management console.
- User and Device Behavior: Enhance security with endpoint hardening, UEBA, security awareness training, performance monitoring, and incident response.
To delve deeper into each feature, check out the references provided at the end of each description. For more information and practical tips on enhancing your endpoint security, visit our detailed guides and resources.
Secure your business today by implementing these endpoint security measures. Learn more about each feature by exploring the detailed references provided!

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


