Snort IDPS: What is it?
Snort IDPS is a widely used open-source tool for network intrusion detection and prevention. This article delves into Snort, explaining its rules and various use cases. Whether you’re new to cybersecurity or looking to enhance your network security knowledge, this article is a must-read.

Key Takeaways
- Snort is a powerful open-source intrusion detection and prevention system.
- Snort analyzes network traffic in real time, detecting potentially malicious packets.
- Snort rules define the conditions for detecting threats.
- Organizations use Snort for network intrusion detection, real-time alerting, and network forensics.

Surviving the Firestorm
This is our new book on Cybersecurity for small businesses. Written in an entertaining format, it is meant for to guide non-technical business owners through the concepts of cybersecurity, planning, and defense tactics. Currently available in Kindle Format.
What is Snort IDPS?
Snort is an open-source intrusion detection and prevention system (IDPS) created by Martin Roesch. It monitors network traffic in real time, detecting potentially malicious packets. Snort is based on a rule-based language that combines protocol analysis, content searching, and various inspection methods to detect a wide range of attacks and malicious activities.
Key Features of Snort
Snort offers several key features that make it a powerful tool in the realm of cybersecurity:
- Real-time traffic analysis and packet logging: Snort captures network traffic and logs packets for further analysis.
- Detection of various attack vectors: Snort can detect a wide range of attacks, including buffer overflows, stealth port scans, and OS fingerprinting attempts.
- Open-source flexibility: As an open-source tool, Snort can be customized and extended to meet the specific needs of an organization.
Importance of Snort in Cybersecurity
In today’s threat landscape, network security is paramount. Snort provides a critical layer of defense by detecting and alerting administrators to suspicious network activity. By identifying and mitigating threats in real-time, Snort helps prevent data breaches and other cyberattacks.
How Does Snort IDPS Work?
How Does Snort Analyze Network Traffic?
Snort analyzes network traffic by capturing packets and comparing them against predefined rules. It uses libpcap, a packet capture library, to sniff network traffic. Snort’s detection engine then inspects the packet’s content and headers to identify potential threats.
What are the Different Modes of Snort?
Snort can operate in several modes, each serving a different purpose:
- Sniffer Mode: In this mode, Snort captures and displays network packets in real time. This is useful for network diagnostics and troubleshooting.
- Packet Logger Mode: Snort logs packets to disk for further analysis. This mode is useful for auditing and forensic investigations.
- Network Intrusion Detection System (NIDS) Mode: This is the most powerful mode, where Snort analyzes network traffic against a set of rules and generates alerts for suspicious activities.
Snort’s Detection Capabilities
Snort can detect a wide range of network threats, including:
- Malicious packets: Snort identifies and alerts on packets that match known attack signatures.
- Port scans and stealth port scans: Snort detects and alerts on port scanning activities, which are often a precursor to more significant attacks.
- Buffer overflows and other vulnerabilities: Snort identifies attempts to exploit known vulnerabilities in network protocols and applications.
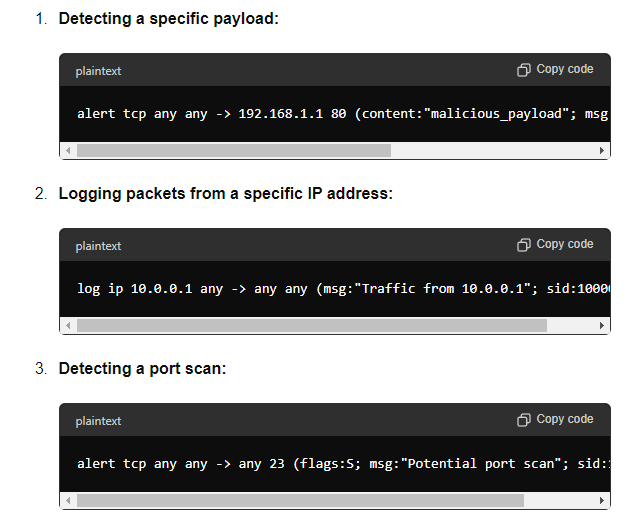
What Are Snort Rules?
Snort rules are predefined instructions that tell Snort what to look for in network traffic. These rules are written in a rule-based language and can specify a wide range of conditions, such as specific IP addresses, port numbers, and payload contents.
How to Create and Use Snort Rules
Creating Snort rules involves defining conditions that match specific network traffic patterns. A typical Snort rule consists of:
- Header: Specifies the action (alert, log, pass), protocol (TCP, UDP, ICMP), source and destination IP addresses, and port numbers.
- Options: Define the specific conditions to match, such as payload content, packet size, and other attributes.
Examples of Snort Rules
Here are a few examples of Snort rules:
What are some Use Cases for Snort IDPS?
How Organizations Leverage Snort
Organizations use Snort in various ways to enhance their network security:
- Network intrusion detection and prevention: Snort can be deployed as an intrusion detection system (IDS) or intrusion prevention system (IPS) to monitor and protect against malicious activities.
- Real-time alerting: Snort generates real-time alerts for suspicious network traffic, allowing administrators to respond quickly to potential threats.
- Network forensics: By logging network packets, Snort provides valuable data for forensic investigations.
Real-World Examples of Snort in Action
Many organizations have successfully used Snort to enhance their cybersecurity posture. For example:
- Financial institutions: Use Snort to detect and prevent fraudulent activities and data breaches.
- Educational institutions: Deploy Snort to protect sensitive student and staff data from cyberattacks.
- Healthcare providers: Leverage Snort to safeguard patient information and comply with regulatory requirements.
Benefits of Using Snort for Network Security
Using Snort provides several benefits for network security:
- Cost-effective: As an open-source tool, Snort is free to use and can be customized to meet specific needs.
- Comprehensive threat detection: Snort’s extensive rule set allows it to detect a wide range of network threats.
- Scalability: Snort can be deployed on networks of any size, from small home networks to large enterprise environments.
How do I Set Up Snort?
How to Install and Configure Snort
Installing and configuring Snort involves several steps:
- Download and install Snort: Snort can be downloaded from its official website and installed on various operating systems, including Linux and Windows.
- Configure Snort: Configuration involves setting up Snort’s configuration file (
snort.conf) to specify the network interface, rule sets, and logging options.
Best Practices for Deploying Snort
When deploying Snort, consider the following best practices:
- Regularly update rule sets: Keep Snort’s rule sets up to date to ensure it can detect the latest threats.
- Monitor logs and alerts: Regularly review Snort’s logs and alerts to identify and respond to potential threats.
- Fine-tune Snort’s configuration: Adjust Snort’s configuration to minimize false positives and ensure optimal performance.
Common Challenges and Troubleshooting Tips
Deploying Snort can present several challenges, including:
- Performance issues: Ensure Snort is running on hardware that can handle the volume of network traffic.
- False positives: Fine-tune Snort’s rules and configuration to reduce false positives.
- Integration with other tools: Ensure Snort integrates smoothly with other security tools and systems in your environment.
What did we learn about Snort and where do I go from here?
Snort is a powerful open-source intrusion detection and prevention system designed to monitor network traffic in real time and detect potentially malicious packets. Created by Martin Roesch, Snort analyzes network data by capturing packets and comparing them against predefined rules, making it an essential tool in cybersecurity. Snort operates in various modes, including Sniffer Mode, Packet Logger Mode, and Network Intrusion Detection System (NIDS) Mode, each serving different purposes.
Snort rules, which are predefined instructions, play a crucial role in identifying network threats such as buffer overflows, port scans, and OS fingerprinting attempts. Organizations leverage Snort to enhance their network security by deploying it for real-time alerting, network forensics, and comprehensive threat detection. The flexibility and scalability of Snort make it suitable for networks of all sizes.
Installing and configuring Snort involves setting up its configuration file and regularly updating rule sets to detect the latest threats. By following best practices, such as monitoring logs and alerts and fine-tuning the configuration, organizations can maximize Snort’s effectiveness.
Try Snort IDPS today to safeguard your network. Share your experiences with Snort in the comments below. Your insights could help others enhance their network security!
Frequently Asked Questions
What is Snort and how does it work?
Snort is an open-source intrusion detection and prevention system that monitors network traffic in real time. It captures packets and analyzes them against predefined rules to detect potentially malicious activity. Created by Martin Roesch, Snort helps enhance network security by identifying and mitigating threats.
How can Snort be used in network security?
Organizations use Snort for network intrusion detection, real-time alerting, and forensic analysis. By deploying Snort, they can monitor network traffic, detect malicious packets, and prevent cyberattacks. Snort’s flexibility and scalability make it suitable for networks of all sizes.
What are Snort rules and why are they important?
Snort rules are predefined instructions that tell Snort what to look for in network traffic. These rules help identify specific threats, such as buffer overflows and port scans. By creating and updating Snort rules, administrators can ensure that their network is protected against the latest cyber threats..
How do I install and configure Snort?
To install Snort, download it from the official website and follow the installation instructions for your operating system. Configuring Snort involves setting up its configuration file (snort.conf), specifying the network interface, rule sets, and logging options. Regularly updating rule sets and monitoring logs is essential for effective network security..
What are the different modes in which Snort operates?
Snort operates in several modes, including Sniffer Mode, Packet Logger Mode, and Network Intrusion Detection System (NIDS) Mode. Sniffer Mode captures and displays network packets in real time, Packet Logger Mode logs packets to disk for analysis, and NIDS Mode analyzes traffic against a set of rules to generate alerts for suspicious activities.
What are the benefits of using Snort for network security?
Snort provides comprehensive threat detection, real-time alerting, and network forensics. Its open-source nature makes it cost-effective and customizable. By leveraging Snort, organizations can enhance their network security posture, protect against various cyber threats, and ensure compliance with security regulations.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!