The Critical Role of Firewalls in Modern Network Security
In the digital age, robust network security stands paramount against the common and devastating data breaches and cyber attacks. At the forefront of defense mechanisms are firewalls, the stalwart guardians of the digital perimeter. But what makes firewalls so fundamental to network security? And what is firewall protection? Let’s delve into their critical role in safeguarding our digital assets.
Choosing the right firewall for a network hinges on understanding specific business needs and network demands.
– Start by evaluating the size and complexity of your network, and the level of security required.
– Consider both software and hardware options—software firewalls are flexible and cost-effective for individual devices, while hardware firewalls serve as a robust barrier for the entire network.
– Look for key features like VPN support, intrusion prevention, and the ability to handle deep packet inspection.
– Ensure the firewall is scalable, manageable, and compatible with your existing infrastructure.
– Factor in budget constraints but avoid compromising on essential security features.
– Always check for compliance with industry standards and gather insights from user reviews.
– Vendor support is crucial for ongoing updates and threat protection.
Balancing these factors will lead to a well-informed decision, ensuring optimal network protection.

Why Firewalls are Fundamental to Network Security
Firewalls serve as the first line of defense in network security. They act as a filter between your network and the vast, often perilous, expanse of the internet. By monitoring incoming and outgoing traffic, firewalls enforce a set of rules that block or permit data packets. Thus, preventing unauthorized access to your network. This barrier is about keeping malicious actors out. But it’s also about ensuring that sensitive data does not leave without proper authorization, making firewalls an indispensable tool for any organization.
The Evolution of Cyber Threats and Firewall Response
As cyber threats have evolved, becoming more sophisticated and insidious, so too have firewalls. Early firewalls were simple and static, designed to protect against the threats of their time. However, as cybercriminals have honed their tactics, firewalls have had to adapt. Advanced features like deep packet inspection, intrusion prevention systems, and artificial intelligence equip today’s firewalls to stay ahead of threats. This constant evolution is a testament to the dynamic nature of cyber security. It also is that the need for firewalls that are as reactive as they are proactive.
Understanding the Shield: How Firewalls Protect Your Data
Firewalls do more than just stand guard; they analyze the data passing through them to identify and stop potential threats. By setting up a firewall, you’re not just erecting a wall; you’re deploying a sophisticated security system that scrutinizes each packet of data
. It’s a shield that not only blocks but also understands what it’s blocking and why, which is crucial for protecting against the myriad of cyber threats that businesses face today.
In the following sections, we will explore the history of firewall technology, the various types of firewalls, and how to select and manage the right firewall for your business needs. Understanding these fundamentals is the first step in fortifying your network against the ever-growing wave of cyber threats.
Why are firewalls important for the protection of a network?
– Firewalls act as a fundamental shield for network security, actively monitoring incoming and outgoing traffic based on predetermined security rules.
– Amidst increasingly sophisticated cyber threats, firewalls establish a critical barrier that actively thwarts unauthorized access to private networks.
– From basic packet filtering to advanced next-generation firewalls, they have evolved to offer layered security against complex cyberattacks.
– Integrating firewalls with other security measures like antivirus software creates a synergistic defense, enhancing overall network protection.
– As remote work becomes commonplace, the importance of robust firewall protection extends beyond the office to home networks.
– By keeping up with the best practices in firewall management and adopting emerging trends like AI and machine learning, you can strengthen your network’s defense, ensuring that both businesses and individuals remain protected against the constantly evolving cyber threats.
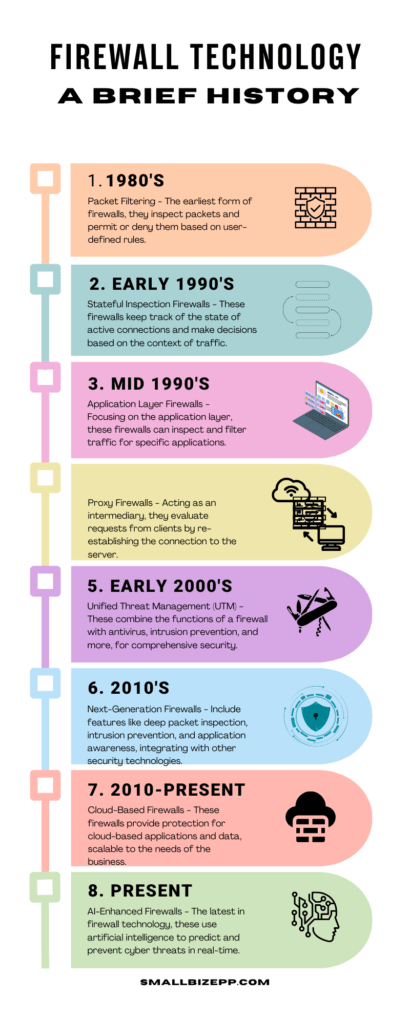
A Brief History of Firewall Technology
The history of firewall technology is a fascinating journey through the evolution of cybersecurity. From rudimentary filtering systems to sophisticated guardians against advanced threats, firewalls have undergone significant transformation. Let’s trace the path of this pivotal technology from its inception to the present day.
The Inception of Firewalls: Tracing Back to the 1980s
The concept of a firewall originally stemmed from the need to limit access between network segments. In the late 1980s, as the internet began to burgeon, the first firewalls were simple packet filters. They operated on a set of defined rules to allow or block data based on IP addresses and ports, which, at the time, provided adequate protection against the level of threats encountered.
The Advancement of Firewalls Through the Decades
As the internet grew, so did the complexity and volume of cyber threats. The 1990s and early 2000s saw the development of stateful inspection firewalls that could track the state of active connections and make more informed decisions about which packets to allow through. This era also introduced the concept of proxy firewalls, which added a layer of abstraction and security by not allowing direct connections between networks.
Key Milestones in Firewall Development
Several key milestones have marked the advancement of firewall technology. The integration of intrusion prevention systems (IPS) allowed firewalls to block attacks. Further, this integration actively detects and prevent attacks. The rise of next-generation firewalls (NGFWs) brought capabilities like application awareness. Application awarenes enables firewalls to control traffic based on application data, and threat intelligence. Threat intelligence uses global insights to improve security measures. Today, firewalls are more than just barriers. Firewalls are complex systems that offer deep network visibility, threat prevention, and a foundation for future security innovation.
This historical perspective sets the stage for understanding the current landscape of firewall technology and its critical role in modern cybersecurity strategies. As we continue, we’ll delve into the specifics of how these technologies protect data and what the future holds for firewall protection.
Why You Need One: Explaining the Use of Firewalls
In the vast and complex world of internet security, firewalls stand as essential sentinels. Their critical role stands undisputed, yet comprehending their function need not be complicated. Let’s break down what firewalls do and why they are an indispensable part of our daily internet use.
Defining Firewall Protection in Simple Terms
At its core, a firewall is a security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. Think of it as a digital gatekeeper that decides which traffic is safe to enter or leave your network. It’s the digital equivalent of a bouncer at a club, checking IDs and deciding who gets in and who doesn’t, ensuring the safety of those inside.
Core Functions of a Basic Firewall
A basic firewall operates on a set of defined rules to filter traffic. Its primary functions include packet filtering, which inspects each packet that crosses the firewall, and blocking or allowing them based on the rules. It also performs monitoring tasks, keeping logs of network traffic to help identify patterns or potential security breaches. This basic functionality is the foundation upon which all other firewall features are built.
Why You Need a Firewall: The Importance in Everyday Internet Use
In our everyday internet use, we are constantly exchanging data with the outside world. A firewall protects sensitive personal and business information from unauthorized access while allowing legitimate communication to flow. It’s not just about guarding against external threats; it’s also about preventing potentially harmful applications from sending out sensitive data from within. With the increasing sophistication of cyber attacks, a firewall is not just recommended; it’s a critical component of any network security strategy, serving as the first line of defense in protecting your digital information.
Understanding the fundamental necessity of firewalls is the first step in recognizing their value in our interconnected world. As we move forward, we’ll explore the different types of firewalls available and how they can be tailored to meet specific needs and threats.
Different Types of Firewalls: How to Use Firewall Protection
Firewalls have evolved into various forms, each designed to serve specific security needs and network environments. From the original packet filters to more advanced solutions, understanding the different types of firewalls is key to deploying the right protection. Let’s examine the primary firewall technologies and their uses.
This table outlines the core functionalities and typical use-case scenarios for each type of firewall, along with a visual suggestion that could be used to represent each one graphically.
| Firewall Type | Functionality | Use-case Scenario | Visual Suggestion |
|---|---|---|---|
| Packet Filtering | Examines packets in isolation, checks against a set of filters. | Suitable for small networks with low security risk. | Icon of a filter with packets passing through. |
| Stateful Inspection | Inspects packet state, context, and makes decisions based on state and rules. | Ideal for businesses that need more security than packet filters can provide. | Diagram of a packet with a state checkmark. |
| Proxy Firewall | Acts as an intermediary, receives requests from clients to connect to servers. | Used in high-security environments to protect against application-specific attacks. | Illustration of a shield with a proxy server icon. |
| Web Application Firewall | Protects web applications by filtering and monitoring HTTP traffic. | For businesses that run critical web applications exposed to the internet. | Graphic of a web app with a protective barrier. |
| Next-Generation Firewall | Includes deep packet inspection, intrusion prevention, and application awareness. | For organizations requiring advanced security features and deep network visibility. | Image of a futuristic shield with multiple layers. |
Packet Filtering Firewalls: The First Line of Defense
Packet filtering firewalls are the most basic type of firewall. They inspect each data packet that attempts to enter or leave the network and make decisions based on user-defined rules. These firewalls check the packet’s source and destination IP addresses, port numbers, and other surface-level information without opening up the packet to inspect its contents. They are fast and efficient but lack the ability to make more sophisticated security decisions.
Stateful Inspection Firewalls: Intelligent Security Monitoring
Stateful inspection firewalls take packet filtering a step further by keeping track of the state of active connections. They not only examine packet headers but also the state of the connection to which the packet belongs, ensuring that only packets matching a known active connection are allowed through. This allows for a more nuanced approach to security, blocking packets that may appear legitimate but are part of a suspicious traffic pattern.
Proxy Firewalls: The Gatekeepers of Network Traffic
Proxy firewalls act as intermediaries between users and the services they access. Instead of allowing direct connections, these firewalls establish a connection to the source of the traffic and then a separate connection to the recipient, effectively ‘proxying’ the traffic. This provides a high level of security as it can prevent direct attacks on the network and allows for deep content inspection and user authentication.
Additional Firewall Variants: Understanding Your Options
Beyond these primary types, there are specialized firewalls designed for specific purposes. Web application firewalls (WAFs), for instance, are tailored to protect web servers from application-layer attacks like SQL injection and cross-site scripting (XSS). Other variants include database firewalls for protecting against database-specific attacks and next-generation firewalls (NGFWs), which we will discuss in a later section, that combine several types of firewall and additional security functions into one solution.
Each type of firewall offers unique benefits and may be suited to different environments or security requirements. By understanding the capabilities and functions of each, businesses can make informed decisions about which firewall protection to use to best safeguard their network assets.
Firewalls and Antivirus Software: Complementary Layers to Protect Your Assets
In the realm of cybersecurity, firewalls and antivirus software are two fundamental components that work in tandem to fortify your digital assets against various threats. While they serve different functions, their integration is crucial for a comprehensive security posture. Let’s explore their distinct roles and how they complement each other.
The Preventive Barrier: How Firewalls Filter Network Traffic
Firewalls act as a preventive barrier at the network’s edge, controlling access to and from your network based on predefined security rules. They filter incoming and outgoing network traffic to prevent unauthorized access, blocking potentially harmful data before it reaches your system. This network-level protection is essential in safeguarding your digital infrastructure from external threats.
The Internal Guardian: Antivirus’ Role in Endpoint Protection
Antivirus software serves as the internal guardian of your system, scanning files and applications for malware and other malicious code. It operates within the endpoints of your network—such as workstations and servers—to detect, quarantine, and eliminate threats that may have bypassed other defenses or originated from internal sources, like a USB drive or an email attachment.
Synergistic Defense: Integrating Firewalls and Antivirus for Optimal Security
For optimal security, firewalls and antivirus programs should not be viewed as either-or options but rather as complementary layers of defense. A firewall’s network traffic filtering, combined with an antivirus’s endpoint protection, creates a synergistic defense mechanism. This multi-layered approach ensures that even if a threat bypasses one layer, another stands ready to thwart the attack, providing a robust security system that addresses a wide array of vulnerabilities.
Employing both firewalls and antivirus software is a best practice in cybersecurity, offering a more dynamic and effective defense against the ever-evolving landscape of cyber threats. Together, they form a comprehensive shield, protecting your assets from the network perimeter to the individual endpoints.
How Firewalls Work: A Deep Dive
Understanding how firewalls manage and secure network traffic is crucial for any small business manager or IT personnel. Let’s delve into the mechanics of packet filtering and stateful inspections, two core functions of firewall operation.
Packet Filtering Explained: The Basics of Network Traffic Management
Packet filtering is the process by which firewalls examine the “envelope” of data packets. Like a mail sorter, the firewall looks at the source and destination addresses, as well as other header information, to determine whether to forward the packet to its destination or block it. This decision is based on a set of predefined security rules.
Stateful Inspections: Advanced Network Security Tactics
Stateful inspections build upon packet filtering by monitoring the state of active connections. The firewall not only checks the packet’s headers but also ensures that the packet is part of an established and trusted connection. This adds a layer of security by recognizing and allowing legitimate packets that are part of an ongoing conversation, while blocking unsolicited packets that could be harmful.
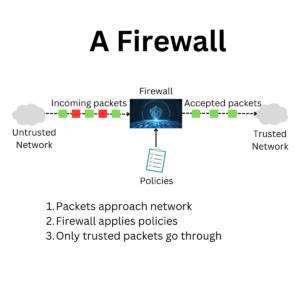
The Inner Workings of a Firewall: A Technical Overview
To illustrate the process, let’s refer to the flow chart below:
In this flow chart, a data packet reaches the firewall, which then applies packet filtering to check the packet headers against its security rules. If the packet matches allowed rules, it’s forwarded to its destination within the internal network. If not, it’s blocked. For packets that pass the initial filter, stateful inspection verifies the connection state before allowing the packet through. All this activity is logged by the firewall, providing a record of traffic for security monitoring.
This technical overview provides a glimpse into the sophisticated nature of firewalls and underscores their importance in network security. By understanding these processes, small businesses can better configure and manage their firewalls for optimal protection.
State-of-the-Art Firewall Features for Small Businesses
For small businesses navigating the complex cybersecurity landscape, next-generation firewalls (NGFWs) offer a suite of advanced capabilities that go far beyond traditional firewalls. These NGFWs incorporate a variety of new technologies to provide robust protection tailored to the needs of modern businesses.
Next-Generation Firewalls (NGFW): A Leap in Cybersecurity
NGFWs represent a significant advancement in firewall technology. They integrate traditional firewall functions with quality of service (QoS) capabilities, intrusion prevention systems (IPS), and even advanced threat detection and remediation. This integration allows for a more granular control of network traffic, bolstering the security framework of small businesses.
Advanced Capabilities of NGFWs for Robust Protection
The advanced capabilities of NGFWs include deep packet inspection (DPI), application awareness, and threat intelligence. These features enable NGFWs to detect and block sophisticated attacks by analyzing the behavior and nature of the traffic, not just the packet headers and ports.
Tailoring NGFW Features to Small Business Needs
Small businesses must consider which features of NGFWs align with their specific security requirements. Below is a table that compares traditional firewalls with NGFWs, highlighting the enhanced features that can be leveraged by small businesses for improved security.
| Feature | Traditional Firewall | Next-Generation Firewall (NGFW) |
|---|---|---|
| Packet Filtering | Yes | Yes |
| Stateful Inspection | Yes | Yes |
| Deep Packet Inspection | No | Yes |
| Application Awareness | No | Yes |
| Intrusion Prevention System | No | Yes |
| Quality of Service (QoS) | No | Yes |
| Threat Intelligence | No | Yes |
| Identity Management | No | Yes |
| SSL and SSH Inspection | No | Yes |
| Customizable Controls | Limited | Extensive |
This feature list matrix showcases the enhanced capabilities of NGFWs compared to traditional firewalls. Small businesses can leverage these features to not only protect their network resources but also to gain deeper insights into their traffic patterns and to enforce more nuanced security policies. The right NGFW can serve as a cornerstone of a small business’s cybersecurity strategy, providing a level of protection that keeps pace with the evolving threat landscape.
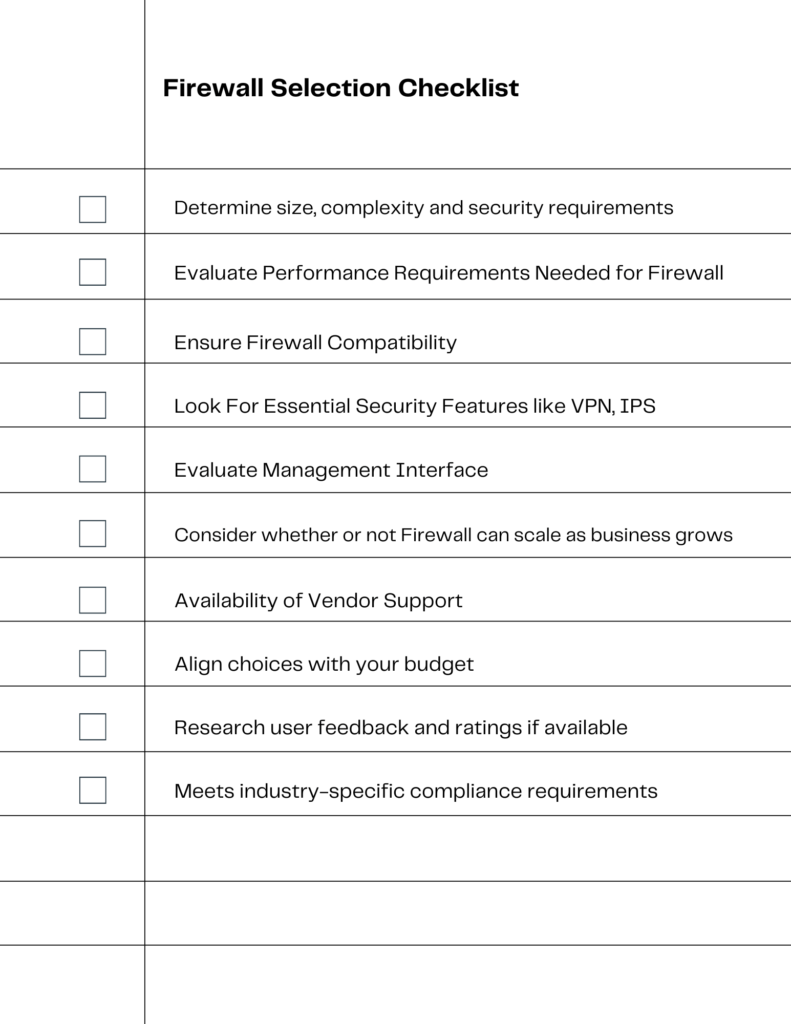
Software Firewall or Hardware Firewall? Selecting the Right for Your Business
In the quest for robust cybersecurity, small businesses and IT managers often face the decision between software and hardware firewalls. Each type offers distinct advantages and considerations that must be weighed carefully to ensure the right fit for a business’s specific needs.
Understanding the Differences: Software vs. Hardware Firewalls
Software firewalls are installed on individual devices, providing protection at the endpoint level. They are particularly adept at controlling outbound traffic and can be customized extensively. Hardware firewalls, on the other hand, are standalone appliances that protect an entire network. They are typically more powerful and can handle the traffic of multiple devices simultaneously.
Key Considerations for Small Businesses When Choosing Firewalls
When selecting a firewall, small businesses should consider factors such as the size of their network, the level of traffic, the sensitivity of the data being protected, and the in-house technical expertise available. Budget constraints also play a crucial role, as hardware solutions may require a larger upfront investment, while software firewalls might be more cost-effective in the short term.
Customizing Firewall Solutions to Fit Your Business Needs
Ultimately, the choice may not be binary. A layered approach, utilizing both software and hardware firewalls, can offer comprehensive protection. Software firewalls can guard individual endpoints against threats that bypass the hardware firewall, while hardware firewalls can manage and secure the broader network traffic. Small businesses must assess their unique circumstances, perhaps consulting with cybersecurity experts, to tailor a firewall solution that aligns with their operational requirements and security goals.
This checklist can guide small business managers and IT personnel in making an informed decision when selecting a software or hardware firewall solution.
Do you Need a Firewall At Home? Security Beyond the Office
The shift to remote work has blurred the lines between office and home, bringing corporate data into personal spaces. This transition necessitates a reevaluation of home network security, particularly the need for firewalls to protect sensitive work-related information.
The Rising Importance of Home Network Security in Remote Work
As more employees work from home, the security of home networks becomes as critical as that of office networks. Home networks often lack the sophisticated security measures found in business environments, making them more vulnerable to cyberattacks. This vulnerability can have direct implications for the security of business data and systems.
Step-by-Step Guide to Securing Your Home Office Network
Implementing a robust firewall at home is a key step in securing a remote work environment. Here’s a practical approach:
- Assess Your Network: Understand the devices connected to your home network and their security needs.
- Choose the Right Firewall: Decide between a software or hardware firewall based on the complexity of your network and the level of protection required.
- Configuration: Set up your firewall with strong security settings, ensuring that it covers all connected devices.
- Regular Updates: Keep your firewall software or firmware up to date to protect against the latest threats.
- Monitoring: Regularly monitor your firewall’s logs to detect and respond to any unusual activity promptly.
By following these steps, you can create a secure home office network that safeguards both personal and work-related data, ensuring that the integrity of your professional activities remains uncompromised even outside the traditional office setting.
Firewall Configuration and Management Best Practices
Proper configuration and management of firewalls are pivotal for achieving optimal protection. A well-configured firewall acts as a formidable barrier against cyber threats, while poor management can lead to vulnerabilities within a network.
Essential Steps for Effective Firewall Configuration
To set up a firewall effectively, follow these steps:
- Initial Setup: Begin with a default-deny rule that blocks all traffic, then selectively enable permissions based on necessity.
- Define Access Control Lists (ACLs): Specify which traffic is allowed or denied based on IP addresses, domains, and ports.
- Implement Zone-Based Policies: Organize your network into zones and define policies that govern the traffic between them.
- User Authentication: Set up rules that require user authentication for accessing certain network resources.
- Testing: After configuration, test the firewall to ensure it operates as intended and modify as necessary.
Best Practices in Firewall Management for Long-Term Security
For sustained security, adhere to these management best practices:
- Regular Updates: Apply updates and patches to your firewall software to protect against new vulnerabilities.
- Log Analysis: Regularly review logs to identify and investigate suspicious activities.
- Rule Auditing: Periodically review and prune firewall rules to ensure they remain relevant and secure.
- Backup Configurations: Maintain backups of your firewall configurations to recover quickly from hardware failures or breaches.
- Educate Users: Train staff on safe internet practices to prevent security breaches that bypass firewalls.
Common Configuration Mistakes and How to Avoid Them
Avoid these common pitfalls in firewall configuration:
- Overly Permissive Rules: Minimize risks by only allowing necessary traffic and services.
- Neglecting to Update: Stay vigilant with updates to protect against the latest threats.
- Ignoring Logs: Regular log reviews are crucial for detecting breaches early.
- Complex Configurations: Keep configurations as simple as possible to avoid errors and misconfigurations.
- Lack of Redundancy: Implement redundant firewall setups to ensure continuous protection in case one fails.
By following these guidelines, businesses can ensure their firewalls are not only well-configured upon setup but also effectively managed to provide ongoing protection against cyber threats
The Future of Firewall Security: What’s Next?
The cybersecurity landscape is constantly evolving, with new threats emerging that challenge the status quo of network security. Firewalls, as a critical component of cybersecurity, are also undergoing significant advancements to counter these threats effectively.
Emerging Trends in Firewall Technology for Enhanced Security
The future of firewall technology is being shaped by the need to combat increasingly sophisticated cyber threats. Innovations include the development of firewalls with advanced predictive capabilities, the integration of cloud-based intelligence, and the adoption of stricter identity management and access controls. These advancements aim to provide more proactive and dynamic network defense mechanisms.
The Next Frontier: AI and Machine Learning in Firewalls
Artificial Intelligence (AI) and Machine Learning (ML) are at the forefront of the next wave of firewall technology. By leveraging AI, firewalls can now analyze patterns, detect anomalies, and predict potential threats with greater accuracy. Machine Learning enables firewalls to adapt to new threats in real-time, learning from the network traffic patterns and user behavior to continuously improve security measures. This integration of AI and ML into firewall technology heralds a new era of automated, intelligent cyber defense capable of withstanding the threats of tomorrow.
Conclusion: Your Next Steps in Firewall Protection
Firewalls stand as vigilant sentinels, guarding the entry points to our digital domains. Their role in securing network perimeters cannot be overstated, as they are often the first line of defense against the myriad of cyber threats that businesses and individuals face daily.
In the ever-evolving landscape of cybersecurity, staying informed and proactive is key. It is not enough to install a firewall; understanding its functions, keeping it updated, and tailoring it to specific needs are all critical steps in fortifying security measures.
As we look to the future, the integration of advanced technologies like AI and machine learning promises even more robust firewall protection. These innovations will enable us to predict and preempt cyber attacks more effectively than ever before.
I encourage you to join the conversation on firewall security. Share your insights, ask questions, and engage with the community. By pooling our knowledge and experiences, we can all contribute to a safer and more secure digital world.
Remember, cybersecurity is a shared responsibility, and every proactive measure counts. Let’s work together to ensure our networks are not only protected by firewalls but also by the collective effort of an informed and vigilant community.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


