
What is VerifiedVisitors?
In today’s digital realm, the significance of robust security cannot be overstated. Small businesses and IT personnel are in a perpetual battle against malicious bots and other digital threats. Enter VerifiedVisitors, a comprehensive platform dedicated to bot management and digital security. This post delves into the core offerings of VerifiedVisitors. It explores how this product can be a game changer in your endpoint security strategy.
Bot Management Excellence
VerifiedVisitors stands out with its sophisticated bot management system. Its immunity protection against bots is tailored for teams managing security at scale. The platform boasts a “Virtual CISO” that automates rule generation based on visitor threats. It can pinpoint key risk paths for account takeovers and other potentially malicious traffic. One can set the governance policies once and then let the Virtual CISO manage the rest. This is a hallmark of simplicity and efficiency.
API Abuse Protection
In the realm of API security, VerifiedVisitors shines by employing behavioral machine learning. This proactive approach analyzes traffic to APIs. By doing so, the application can identify and thwart abuse of service attacks before they reach the APIs. Thus, providing a layer of preemptive security.
Fake Account Prevention
The digital world is rife with identity theft, fake registrations, and fraudulent account creations. VerifiedVisitors steps in to alleviate these issues by identifying and managing fake accounts created by bots. Thus, ensuring a significant reduction in fraudulent activities.
Bot Detection Capabilities
VerifiedVisitors extends its expertise to bot detection, offering tools that prevent account takeover, API abuse, and data mining. It’s a holistic approach to understanding and mitigating the impact of malicious bots. It can provide a robust defense against a variety of digital threats.
Seamless Integration
Integration is a breeze with VerifiedVisitors. Whether you prefer a manual setup or an automated integration through Cloudflare or AWS CloudFront, the platform accommodates your preferences. The Cloudflare integration is particularly seamless. This integration path taking care of worker scripts and route configurations, while manual setup provides flexibility for custom integration.
This was extremely easy for me to set this up for my WordPress site.
First, I created a Cloudflare account. Then I told Cloudflare which website I wanted to integrate with it and it gave me a global API key that was linked to that website and my email address.
Next, I installed a Cloudflare plugin on my website and gave it the global API.
Finally, I added the website to my VerifiedVisitors account along with the email I used on Cloudflare and the Global API key.
Command And Control
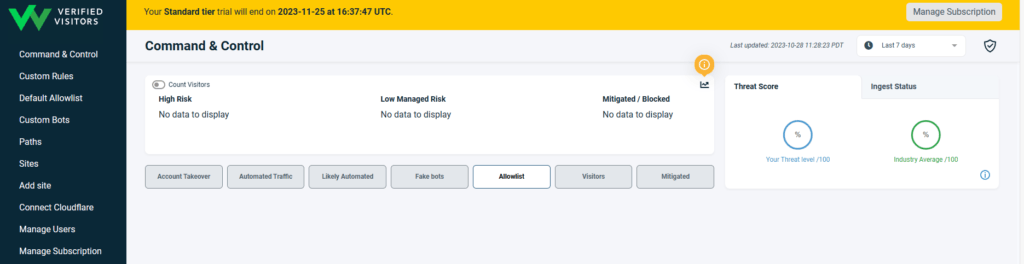
On logging in and selecting your website, the first thing you see is the Command & Control screen. That gives you a single pane-of-glass overview of the health of your website.
You may look at the ingest status after you set up the website and see something like this because the website is new. It should go away in several hours.
No logs being ingested. Please check your integration, see our documentation for setup guidance.
After a few hours, it will look something like this. The application should start vetting the traffic based on default rules.
Note: After reporting this to the developers, they updated the product so you may not see this anymore.
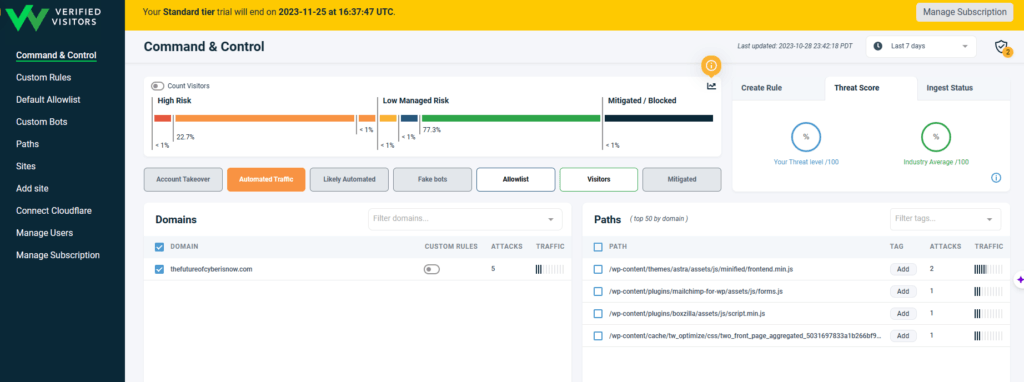
You notice the breakdown as high risk, low managed risk, and mitigated/blocked.
The High Risk are inputs that should be looked at. In my case, they appear to mostly be automated traffic.
Low managed risk are inputs that are looked at. Green are inputs that the app believes should get through, black are inputs on the allow list, and orange are believed to be fake bots.
Mitigated/blocked are inputs that are known bad actors, either because the app already knows this through its own sources or because I told it (which I haven’t)
Traffic Analysis
VerifiedVisitors allows you to view the traffic in each part of the breakdown as shown below.
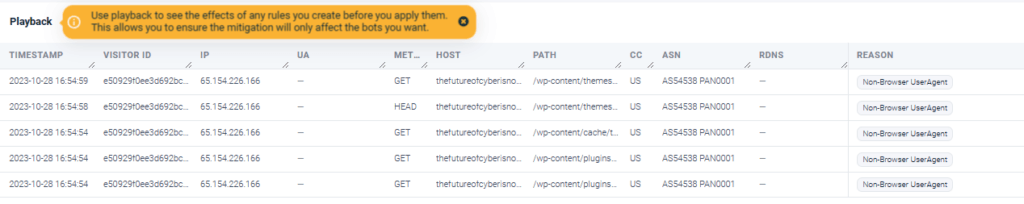
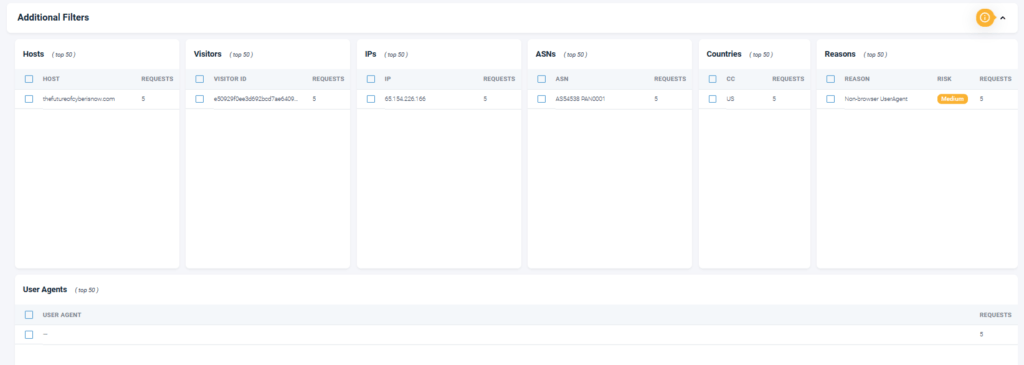
You can also filter this using the additional filters above the traffic:
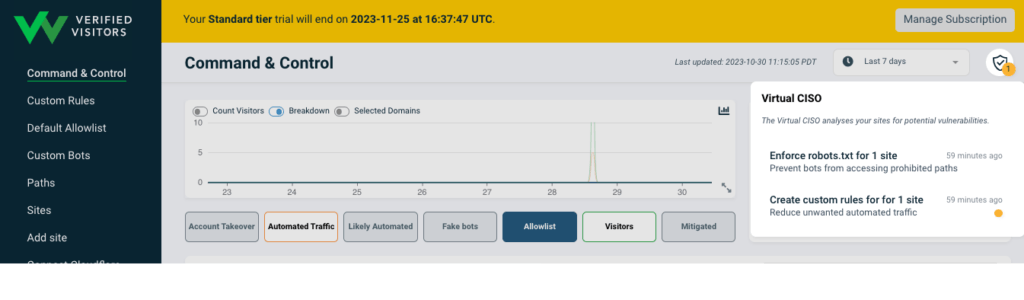
Alerts
VerifiedVisitors has a feature called Virtual CISO which analyzes your traffic and website and makes recommendations. As shown in the image below, as we started out it made two recommendations. First, as we had some bot traffic, we needed to block it. Second, our robots file was wide open and would allow prohibited paths.
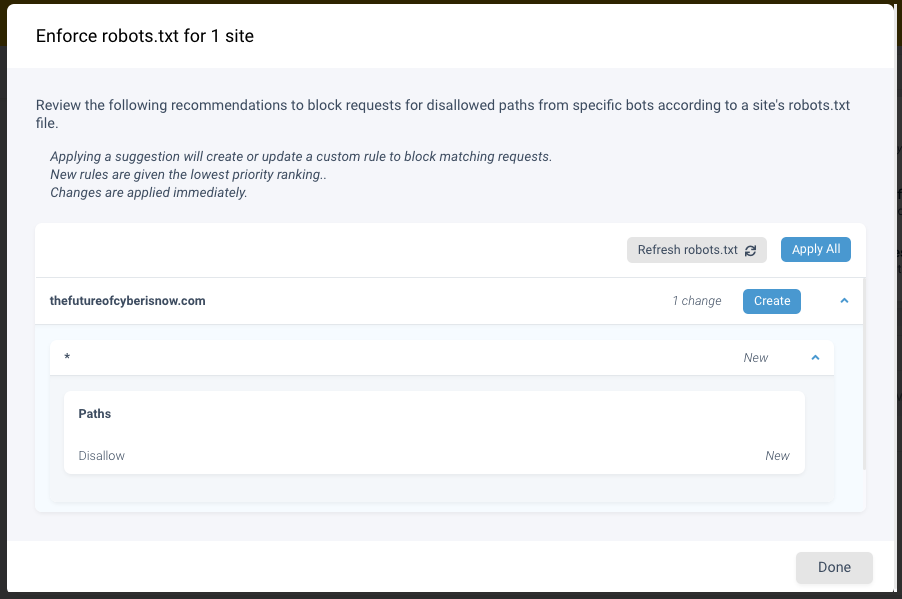
Clicking on the robots alert produces the recommendation shown in the image below. It disallows access to the robots file. Note the Apply All and Create buttons. The “Apply All” would update all site recommendations (in this case, there is only one), where the Create would apply the update to the one site.
Custom Rules
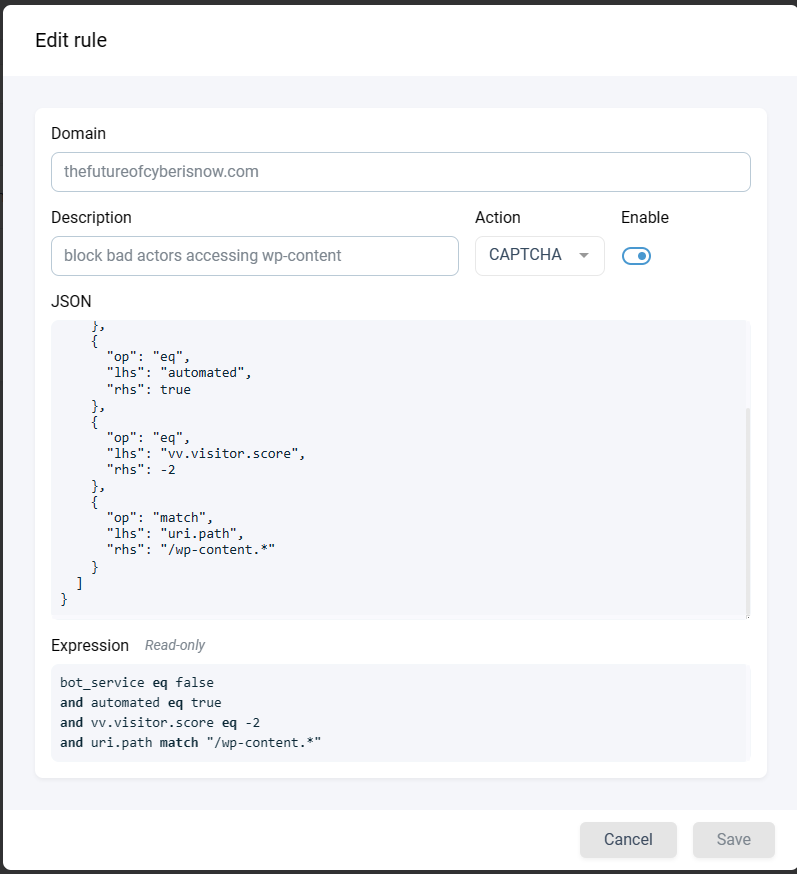
The second alert has to do with custom rules. We created that manually as shown in the image below. On analyzing the bot traffic, we found one IP address was trying to access /wp-content paths. As a cautious analyst, I believe in multiple sources to verify the IP is in fact a bad IP. So I used AbuseIPDB to verify it. This is a free service. With 100% confidence, it showed me the site was considered bad. By adding a rule that the uri path must match the regex, we changed the initial template for a custom rule against an automated bot. Thus, it would block any path starting with “/wp-content”.
To use custom rules on VerifiedVisitors for the first time, you must enable them for the specific site if you haven’t already.
There are two places you can do this:
- The list of Domains on the Command & Control Page
- The domain on the Sites page
You can manage the individual rules from the Custom Rules page, enabling or disabling each rule globally.
In my experience, I expect a request to come in that looks like a request for my site. For instance, if my site were a standard html site, I would expect requests for html, javascript, css, and maybe a few other types like xml or txt. I would not expect java server pages (jsp), php, or asp pages. Seeing those, I would assume the actor is bad and should be blocked.
There may be some traffic that I can block before I even see it. However, one will block a lot based on what they see.
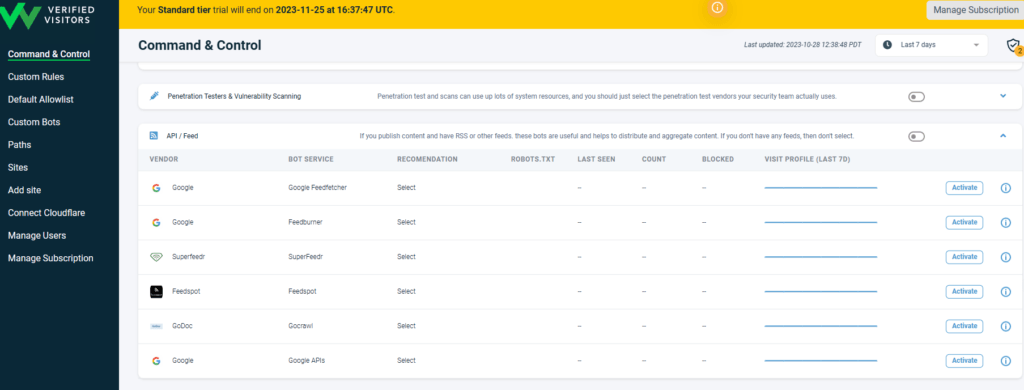
Bot Management
You have the ability to manage which bots are allows and which are blocked by default.
If you scroll down on the command and control page. You will see you have the ability to manage about two dozen different groups of bots. This allows you to either allow or block bots as a group.
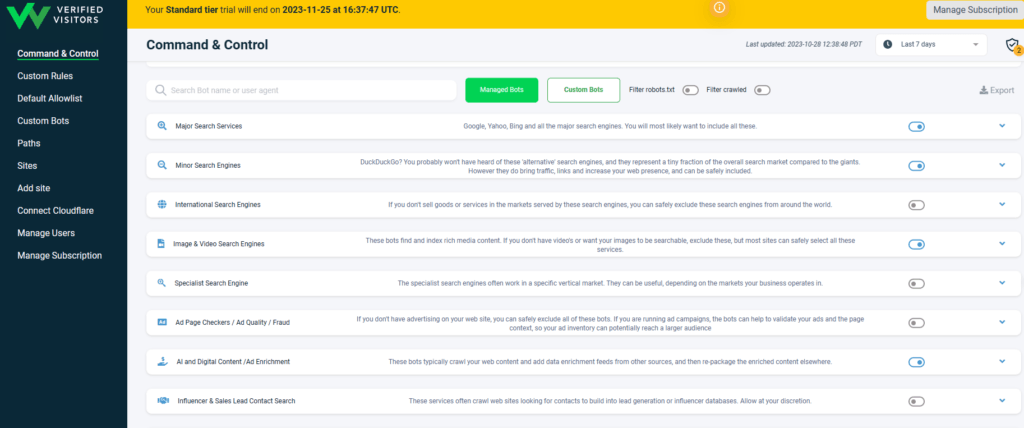
By clicking on the triangle to the right of the group, you can also block or allow individual bots.
Check This Product Out!
VerifiedVisitors presents a well-rounded solution for managing and mitigating risks associated with malicious bots and other automated threats. It blends automated and customizable security measures coupled with ease of integration. This makes it a noteworthy consideration for small businesses keen on bolstering their digital security. Explore VerifiedVisitors and take a stride towards a more secure digital presence.
This seems to be a young product, but I found it works well. The IPs that it reports as bad actors can be verified as such through AbuseIPDB. Enabling the rules is just a click! The documentation seemed to be a little sparse in places, but after making a few comments I found them to be very responsive. In just a few weeks’ time the documentation for the command & control page has greatly improved.
This post only scratches the surface of what VerifiedVisitors offers. For a deeper dive into its functionalities and how it can be tailored to meet your specific needs, visit the company website.
Engage with us in the comments below and share your thoughts or experiences with digital security solutions. Your insights are valuable in fostering a community of knowledge sharing and continuous learning among small business managers and IT personnel.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!

