Introduction
In the digital age, cyber security is no longer a luxury, but a necessity for businesses of all sizes. Small businesses, just like large enterprises, are vulnerable to cybercrime. In fact, small businesses often become targets due to their lack of resources and support, multiple interfaces, and inadequate training. This article aims to guide small business managers through the complex world of advanced endpoint security.
Understanding Endpoint Security
Endpoint security refers to the protection of internet-connected devices, such as computers and mobile devices, from cyber threats. Known as endpoints, these devices serve as entry points for threats, and we need to secure them to prevent breaches. Advanced threats, such as sophisticated malware attacks and unknown threats, require advanced endpoint security solutions.
The Threat Landscape for Small Businesses
Cyber threats are evolving, becoming more sophisticated and harder to detect. Small businesses face a variety of threats, including malware attacks and phishing. Advanced endpoint security solutions offer malware protection, helping to safeguard your business from these threats.
Advanced Endpoint Security: Key Features
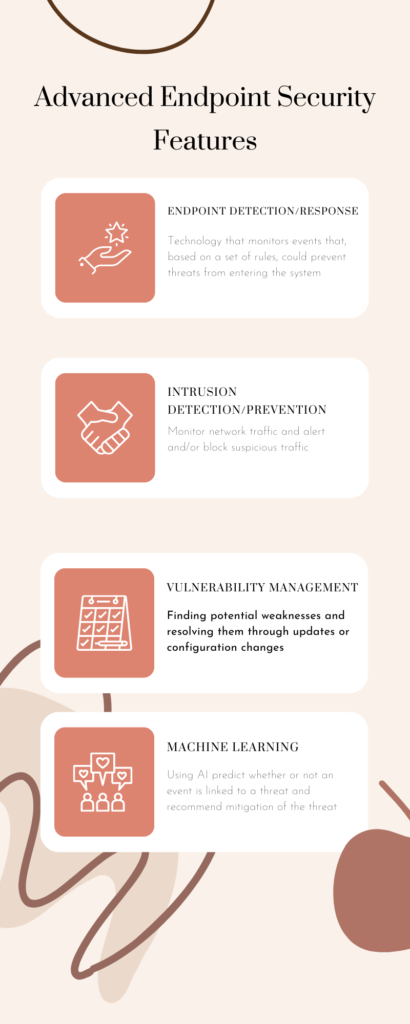
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a technology that monitors endpoints and network events. A central database records the events. The database enables data analysis, leading to the detection, investigation, and reporting of threats.
This real-time threat detection is crucial in identifying and mitigating threats before they can cause significant damage.
Behavioral Analysis
Behavioral analysis identifies advanced threats.. By monitoring the behavior of endpoints, it can detect unusual activity that may indicate a threat. This method proves particularly useful in detecting unknown threats that traditional security measures might not identify.
Vulnerability Management
Vulnerability management involves identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. It’s a proactive approach to managing network security. It acts to reduce the likelihood that weaknesses in code or design compromise the security of an endpoint or network.
Machine Learning and Endpoint Security
Machine learning is a type of technology which includes artificial intelligence (AI). It allows software applications to become more accurate in predicting outcomes. It can do this even without being explicitly programmed to do so. In the context of endpoint security, machine learning can enhance the detection and mitigation of threats. Thus, making your security measures more effective.
The Benefits of Advanced Endpoint Protection
Advanced endpoint protection offers numerous benefits, particularly for small businesses that may not have extensive IT resources. Moreover, these tools also provide comprehensive reports about the threats they’ve detected and the actions they’ve taken. This keeps you informed about your security status. It also helps you comply with regulations that require businesses to monitor and report on their cybersecurity.
Key advantages of Advanced Endpoint Protection
Improved Threat Intelligence and Threat Hunting Capabilities
Advanced endpoint protection solutions come equipped with improved threat intelligence capabilities. This means they can gather and analyze information about a wide range of existing and emerging threats. This intelligence is used to protect your network from known threats and to predict and prevent potential future attacks.
Moreover, these solutions also offer threat hunting capabilities. Threat hunting involves proactively looking for signs of malicious activity within your network.
That malicious activity may have gone undetected by your initial security measures. It’s like having a dedicated security guard who is always on the lookout for suspicious activity. Thus helping you stay one step ahead of cybercriminals.
Enhanced Protection for Mobile Devices
In today’s digital age, the office no longer confines work. Employees often use mobile devices such as smartphones and tablets to access company resources. This makes these devices a potential entry point for threats.
Advanced endpoint protection solutions provide enhanced protection for these mobile devices. Thus ensuring that they are secured against malware, phishing attacks, and other cyber threats.
This allows your employees to work securely from anywhere, without putting your business data at risk.
Managing Threats
One of the key benefits of advanced endpoint protection is its ability to manage threats effectively. This involves identifying potential threats, containing them, and eliminating them from the network. Advanced endpoint security tools are equipped with features like automated threat detection and response. These features can significantly reduce the time it takes to respond to a threat, minimizing potential damage.
Cloud-Based Endpoint Security Solutions
Cloud-based endpoint security solutions offer the same level of protection as traditional on-premise solutions. The difference is that the software is not hosted on the provider’s infrastructure. This offers several benefits for small businesses, including reduced costs, easy scalability, and access to the latest security technologies.
Choosing the Right Endpoint Security Solution for Your Business
Choosing the right endpoint security solution for your business is crucial. Consider factors such as the size of your business, the nature of your data, and your budget. Remember, the best solution is one that fits your specific needs and resources.
Conclusion
Advanced endpoint security is a crucial component of a robust cyber security strategy for small businesses. By understanding the threats you face and the solutions available, you can make informed decisions to protect your business. Don’t wait until it’s too late – invest in advanced endpoint security solutions today.
Frequently Asked Questions
- What is advanced endpoint security?
Advanced endpoint security is a type of cyber security solution that protects internet-connected devices (endpoints) from threats. It uses advanced methods to detect and mitigate threats. Methods such as machine learning and behavioral analysis,. - What are the three main steps of endpoint security?
The three main steps of endpoint security are detection, response, and prevention. Detection involves identifying threats, response involves taking action to mitigate detected threats, and prevention involves taking proactive measures to prevent threats. - What are the limitations of endpoint security?
Endpoint security can’t protect against threats that it doesn’t know about or can’t detect. This includes zero-day threats (threats that exploit previously unknown vulnerabilities) and sophisticated threats that use advanced techniques to evade detection. - What is the most common challenge for endpoint security deployments?
The most common challenge for endpoint security deployments is managing the large number of endpoints in a network. This can be particularly challenging for small businesses with limited IT resources. - How does advanced endpoint security help small businesses?
Advanced endpoint security helps small businesses by providing robust protection against a wide range of threats. It uses advanced techniques to detect and mitigate threats. Advanced endpoint security can be tailored to the specific needs of a small business.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


