This article will help you understand the zero-trust model in the context of endpoint security.
The importance of endpoint security cannot be overstated. There is an ever-increasing number and types of devices connecting to business networks. The potential entry points for cyber threats have multiplied. For small business managers responsible for their company’s computer systems, this presents a pressing challenge.
Enter the Zero Trust model, a revolutionary approach to cyber security. Traditional methods operate on the assumption of trust for internal networks. On the other hand, Zero Trust operates on a simple principle: “never trust, always verify.” This means every access request, whether coming from inside or outside the organization, is treated as potentially harmful until proven otherwise.
Unlike traditional models that assume internal networks are safe, this model treats every access request as potentially harmful until proven otherwise.
It focuses on continuous verification of users and devices, employing multi-factor authentication and data loss prevention techniques.
The model is particularly crucial for modern businesses that use a variety of endpoints like IoT devices and mobile phones, which can be vulnerable entry points for cyber threats.
Adopting Zero Trust is not just a recommendation but a necessity for safeguarding business assets and reputation in an increasingly digital world.
Key Takeaways
- Never Trust, Always Verify: Every access request is treated as potentially harmful until proven otherwise.
- Least Privilege Access: Grant only the necessary access to users and devices.
- Continuous Monitoring: Regular validation of users and devices to ensure ongoing security.
- Multi-Factor Authentication: Use multiple verification methods to enhance security.
- Data Loss Prevention: Monitor and control data transfers to protect sensitive information.
Understanding Zero Trust Endpoint Security
The Zero Trust model is a cyber security approach that revolves around the belief that no entity should be automatically trusted. This is true whether inside or outside an organization. Instead, every access request should be rigorously verified before granting permissions.
Click to expand
This approach is rooted in three core principles:
- Never trust, always verify: Every user, device, or system must prove its legitimacy.
- Least privilege access: Grant only the necessary access and nothing more.
- Continuous monitoring: Regularly validate the security status of ongoing connections.
Traditional security models often operate under the assumption that threats predominantly come from outside the organization. They focus on building strong perimeter defenses, like firewalls, to keep threats out. Once inside, users and devices typically have broad access. In contrast, Zero Trust assumes potential threats can originate both externally and internally.
One example is the approach to remote access. Traditional models might require VPNs and complex configurations. On the other hand, Zero Trust solutions offer secure, direct access without assuming the remote device is safe.
Why Zero Trust is Crucial for Modern Businesses
Modern businesses face a unique set of challenges. This is especially true with the proliferation of diverse endpoints like IoT devices, mobile phones, and tablets. These devices, while enhancing operational efficiency, exponentially increase the potential entry points for cyber threats. Without a Zero Trust security strategy, businesses leave themselves vulnerable to a myriad of risks.
For instance, a seemingly harmless smart thermostat, if compromised, could serve as a gateway for hackers to access sensitive company data.
The variety of endpoints within an organization’s network is expanding. From desktop computers and laptops to mobile phones and IoT devices, each endpoint presents its own set of risks. To give you a clearer picture, let’s delve into a table that outlines the different types of endpoints and the specific risks they pose. More importantly, the table also highlights how Zero Trust measures can mitigate these risks.
| Endpoint Type | Risks | Zero Trust Measures |
|---|---|---|
| Desktop Computers | Malware, Unauthorized Access | Continuous Monitoring, MFA |
| Laptops | Data Theft, Unsecured Networks | Least Privilege Access, Continuous Monitoring |
| Mobile Phones | Phishing Attacks, Malware | MFA, Continuous Monitoring |
| IoT Devices | Unsecured Access, Data Interception | Least Privilege Access, MFA |
| Network Printers | Unauthorized Access, Data Interception | Least Privilege Access, Continuous Monitoring |
| Servers | DDoS Attacks, Unauthorized Access | MFA, Continuous Monitoring |
| Cloud Storage | Data Leakage, Unauthorized Access | Least Privilege Access, MFA |
| Virtual Environments | Inadequate Isolation, Unauthorized Access | Continuous Monitoring, Least Privilege Access |
An employee’s personal mobile device needs to be continuously verified. If not, it might introduce malware into the network. Thus, leading to data breaches and significant financial losses. Today, cyberthreats are rapidly evolving.
Adopting Zero Trust isn’t just a recommendation: it’s a necessity for safeguarding business assets and reputation.
Core Components of Zero Trust Endpoint Security
At the heart of the Zero Trust model lie several pivotal components that ensure its efficacy.
Continuous verification stands as a cornerstone. Rather than a one-time validation, it mandates that the legitimacy of users and devices be consistently re-evaluated. Imagine an employee accessing company data from a coffee shop. Even if their initial login is verified, continuous monitoring can detect unusual data transfers, prompting immediate action.
Multi-factor authentication (MFA) further bolsters security. MFA requires multiple forms of verification. One example is a password combined with a fingerprint. MFA ensures that even if one security layer is breached, unauthorized access remains blocked.
Lastly, Data Loss Prevention (DLP) plays a crucial role. It monitors and controls data transfers across the company network, ensuring sensitive information doesn’t fall into the wrong hands. In the Zero Trust framework, DLP acts as a vigilant guard, ensuring data remains protected at all times.
Click To Expand
The Evolution of the Zero Trust Model
Historically, security models operated on a foundation of trust. Once inside the company’s network, users and devices were generally deemed trustworthy, leading to the coined term “trust networks.” However, as cyber threats grew more sophisticated, this trust-based approach revealed its vulnerabilities.
Enter the Zero Trust model. This model is a paradigm shift emphasizing that no user or device should be implicitly trusted. This is true regardless of its location relative to the company’s network.
This evolution gave birth to Zero Trust Network Access (ZTNA). ZTNA ensures that only authenticated users and devices can access specific applications, rather than the entire network.
This granular approach significantly reduces the potential attack surface, making it a cornerstone in modern security strategies. In today’s digital age, where threats lurk at every corner, ZTNA offers businesses a robust shield against potential breaches.
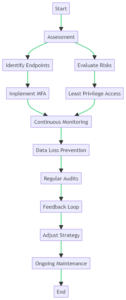
Implementing Zero Trust: A Step-by-Step Guide
Embarking on the journey to implement Zero Trust can seem daunting. However, by breaking it down into manageable steps, the process becomes clearer and more achievable.
Initial Steps:
Start with registering endpoints with cloud identity providers. This foundational step ensures that every device connecting to your network is recognized and cataloged. By doing so, you lay the groundwork for more advanced security measures. Thus, ensuring that only known and verified devices can access your business’s critical data.
Advanced Steps:
Once endpoints are registered, it’s time to elevate your security game. Incorporate endpoint threat detection to continuously scan for potential vulnerabilities or malicious activities on devices. Pair this with real-time monitoring, which keeps a vigilant eye on network activities.
If any unusual behavior or unauthorized access attempts are detected, immediate alerts allow for swift action. For instance, an employee’s device starts downloading large amounts of data unexpectedly. If this occurs, real-time monitoring can flag this, prompting further investigation.
Click to Expand
By methodically implementing these steps, small business managers can ensure a robust Zero Trust environment. Thus. safeguarding their company’s assets and reputation in an increasingly digital world.
Challenges in Adopting Zero Trust
Transitioning to a Zero Trust model is not without its challenges. Many businesses struggle shifting to an approach of continuous verification. Employees, accustomed to unrestricted access, might find the new model restrictive or cumbersome.
One of the primary challenges is the complexity of implementation, which can be mitigated by breaking the process down into manageable phases. This approach is known as phased implementation.
Another obstacle is resistance to change from employees and stakeholders. The key here is to educate them on the benefits of Zero Trust, enhancing both security and compliance.
High initial costs can also be a deterrent, but a thorough cost-benefit analysis can justify the investment.
Compatibility issues may arise when integrating Zero Trust solutions with existing systems. To avoid this, ensure that the chosen solutions are compatible with your current infrastructure.
Managing multiple endpoints can be cumbersome, but centralized management tools can streamline this process.
Another major concern is access control. Managers often worry about hindering productivity by implementing stringent access controls. However, the key lies in balancing security with accessibility. Implementing least privilege access and multi-factor authentication (MFA) can simplify it.
Lastly, continuous monitoring and regular audits are essential but can be resource-intensive. Automated tools can ease this burden, making the transition to a Zero Trust model smoother.
Businesses can ensure that employees have access to the tools they need by using role-based access controls. At the same time, keeping sensitive data under wraps.
Challenges of Implementing Zero Trust
| Challenge | Solution | Zero Trust Measures |
|---|---|---|
| Complexity of Implementation | Simplify by breaking down into phases | Phased Implementation |
| Resistance to Change | Educate stakeholders on the benefits | Stakeholder Education |
| High Initial Costs | Calculate ROI and long-term savings | Cost-Benefit Analysis |
| Compatibility Issues | Ensure Zero Trust solutions integrate well with existing systems | System Integration |
| Managing Multiple Endpoints | Use centralized management tools | Centralized Management |
| Access Control | Implement least privilege access and strong authentication | Least Privilege Access, MFA |
| Monitoring and Auditing | Use automated tools for continuous monitoring and regular audits | Continuous Monitoring, Regular Audits |
Businesses can smoothly transition to a Zero Trust model by anticipating these challenges and proactively addressing them. Thus, reaping its security benefits without compromising on operational efficiency.
Case Study: Akamai’s Shift to Zero Trust: A Game-Changer
Akamai Technologies, a leading cloud service provider, had a significant data breach in 2009. They recognized the need for a more secure approach.
They explored the Zero Trust model, focusing on application-level security rather than just network barriers. Their goal? Ensure employees could access vital tools without exposing the entire network.
In their journey, Akamai collaborated with Soha Systems, a company offering a unique access model. This model granted employees role-based access to specific applications. Thus, limiting potential damage even if hackers got their hands on login details.
The result? A robust system where each user only saw what they needed, nothing more.
By integrating this approach, Akamai not only fortified its own defenses but also enhanced its Enterprise Application Access service for clients. This move reduced dependence on traditional VPNs, ushering in a new era of security.
For small businesses, Akamai’s story highlights the power of the Zero Trust framework. It’s not just about blocking threats but ensuring safe, efficient access for every team member.
Future of Zero Trust: What’s Next?
The Zero Trust model, while transformative, is still evolving. Predictions suggest that the architecture will become even more granular, focusing on individual data packets rather than just applications or endpoints. This means businesses will have unparalleled control over their data flow.
Emerging technologies, especially Artificial Intelligence (AI) and Machine Learning (ML), are set to play pivotal roles in this evolution. These technologies can analyze vast amounts of data in real-time, detecting anomalies and potential threats with incredible accuracy. As a result, Zero Trust systems of the future might auto-adjust access permissions based on real-time threat analysis. Thus, ensuring optimal security without human intervention.
Embrace the Future of Security with Zero Trust
The digital landscape is ever-changing, and with it, the threats businesses face. Zero Trust endpoint security stands as a beacon. It can guide companies towards a safer future. Its principles of continuous verification and least privilege access ensure that every interaction is scrutinized, leaving no room for complacency.
For small business managers, the message is clear: the traditional trust-based models are no longer sufficient. The Zero Trust framework offers a proactive, robust approach, ensuring that your business’s data and assets remain protected from evolving cyber threats.
Embracing Zero Trust isn’t just about adopting a new security model: it’s about future-proofing your business. As we move forward in this digital age, let’s prioritize security, ensuring our businesses not only survive but thrive in a world filled with challenges. Adopt, adapt, and let Zero Trust be your guide.
Frequently Asked Questions
What is Zero Trust Endpoint Security?
Zero Trust Endpoint Security is a cybersecurity model that continuously verifies the legitimacy of every access request, whether from inside or outside the organization..
How does Zero Trust differ from traditional security models?
Traditional models assume internal networks are safe. Zero Trust, however, treats every access request as potentially harmful and requires continuous verification..
Why is Zero Trust important for modern businesses?
With diverse endpoints like IoT devices and mobile phones, Zero Trust helps mitigate risks by continuously verifying each device and user, protecting business assets.
What are the core principles of Zero Trust?
The core principles are “never trust, always verify,” least privilege access, and continuous monitoring.
How can businesses implement Zero Trust?
Start by registering endpoints with cloud identity providers, then incorporate endpoint threat detection and real-time monitoring.
What are the challenges of adopting Zero Trust?
Challenges include complexity of implementation, resistance to change, high initial costs, compatibility issues, managing multiple endpoints, access control, and the need for continuous monitoring and audits.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
