
Introduction
Securing your business’s computer systems is not just an option but a necessity. Endpoint Detection and Response (EDR) tools are a powerful ally in this endeavor. They offer a wide range of capabilities to detect, analyze, and respond to potential threats in real-time.
This article will explore the unique features of EDR tools and their pros and cons. Finally, how EDR tools can enhance your business’s cybersecurity posture.
Understanding Endpoint Detection and Response: A Game-Changer in Cybersecurity Tools
Endpoint Detection and Response (EDR) is a cybersecurity solution. It continuously monitors end-user devices to detect and respond to cyber threats such as ransomware and malware. It provides advanced threat detection, investigation, and response capabilities. These capabilities include incident data search, suspicious activity validation, threat hunting, and malicious activity detection.
Implementing EDR can be a significant investment, both in terms of cost and time. However, the value it brings in terms of threat detection and response can far outweigh these costs. It can alert and stop various threats, thereby potentially saving your business from costly data breaches and downtime.
On the flip side, not all threats can be stopped. Also, there may be false positives that could lead to unnecessary investigations.
As part of this implementation, you should create an Endpoint Detection and Response policy.
An Endpoint Detection and Response (EDR) policy is a set of rules and procedures. This policy guides how an organization uses EDR tools to protect its network and devices from cyber threats. It is a crucial component of a business’s cybersecurity strategy. The policy provides guidance on how the organization should provide EDR features.
Why a Business Needs an EDR Policy
There is an increasing sophistication of cyber threats and the growing number of network endpoints. Therefore, businesses need an EDR policy to ensure the security of their networks and devices. EDR tools provide security teams with ongoing and comprehensive visibility into endpoint activities. Thus, enabling the detection of otherwise hidden incidents.
Endpoint Detection and Response tools also offer advanced threat detection, investigation, and response capabilities. This involves incident data search, alert triage, validation of suspicious activities, threat hunting, and containment of malicious behavior.
Moreover, an EDR policy is essential for businesses that have adopted remote or hybrid work environments. With more devices connected to the network, securing endpoints becomes crucial.
Components of an EDR Policy
An EDR policy typically includes the following components:
Monitoring and Analysis
The policy should outline how the EDR solution will monitor and analyze endpoint activity data to identify potential threats.
Automated Response
The policy should specify how the EDR solution will respond automatically to contain threats. Further, the policy should specify tools for forensic research and analysis of suspicious activities.
Incident Detection and Containment
The policy should detail how the EDR solution will:
- detect security incidents
- contain them at the endpoint
- investigate incidents
- offer remediation guidance
Threat Remediation
The policy should explain how the Endpoint Detection and Response tools will take appropriate actions like:
- creating alerts
- isolating hosts
- deleting files
- killing processes
- initiating scans
- restoring systems
Integration with Other Systems
The policy should describe how the EDR solution will be integrated with other security systems. This includes how it will gather security-related data from various IT infrastructure layers. Also, how it will enrich its analytics with context.

Diving Deep into the Capabilities of Endpoint Detection and Response Tools
Selecting Endpoint Detection and Response Tools is all about three things: capabilities, cost, and value.
Capabilities because you need to prevent your business from being attacked.
Cost because you have limited resources. Resources include time as well as money.
Value because you may not be vulnerable to certain types of attack. Also, value because one may be willing to accept the risk if you are.
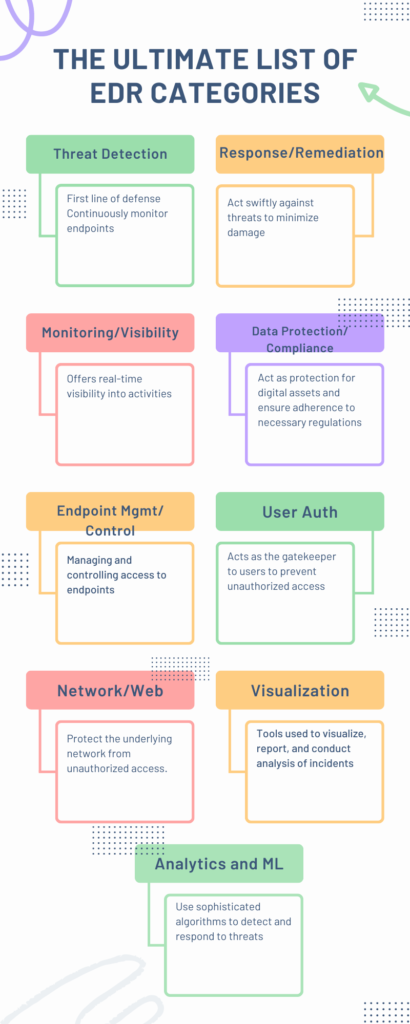
Threat Detection and Analysis: Your First Line of Defense
Features under this category serve as the first line of defense in an Endpoint Detection and Response (EDR) system. They continuously monitor endpoint devices, detect suspicious activities, and respond to cyber threats in real time.
Pros
- Proactive Defense: These features actively search for threats, enabling early detection and prevention of potential attacks.
- Real-Time Response: They provide real-time visibility into endpoint activities, allowing immediate response to detected threats.
- Threat Intelligence Integration: They can integrate with threat intelligence services, providing up-to-date information on cyber threats and tactics.
Cons
- Complexity: Implementing and maintaining these features can be complex, requiring skilled personnel and resources.
- False Positives: They may generate false positives, leading to unnecessary investigations and resource usage.
Costs
The costs of implementing and maintaining these features can vary widely. It depends on:
- the specific EDR solution chosen
- the size of the organization
- the complexity of its network
These costs include:
- the price of the EDR solution
- the costs of training staff
- maintaining the system
- responding to alerts
Value
Features in this category can detect a wide range of threats, including malware, ransomware, and advanced persistent threats. The value is to detect and responding to these threats in real time. Because of this, threat detection and analysis can:
- prevent potential breaches
- protect sensitive data
- maintain the integrity of the organization’s network
1. Real-Time Threat Detection: The Watchful Guardian
Real-Time Threat Detection is a key feature of Endpoint Detection and Response (EDR) tools. It allows the tool to monitor endpoint activities continuously. Thus, identifying and addressing threats instantly.
Pros:
- It allows immediate threat identification, minimizing potential damage from cyberattacks.
- It can automatically respond to threats, preventing their spread.
- It provides ongoing visibility into endpoint activities, uncovering hidden incidents.
Cons:
- It can lead to false positives, wasting resources on unnecessary investigations.
- Its implementation and management can be complex, requiring specialized skills.
Costs:
The costs of implementing and maintaining this feature can vary. This includes the price of the EDR software, hardware costs, and staff training. Despite these costs, it can prevent costly cyberattacks.
Value:
The value is in protecting valuable data and systems by detecting and responding to threats in real-time. Threats like malware, ransomware, and advanced persistent threats (APTs).
2. Behavioral Analysis: Unmasking the Cyber Intruders
Behavioral Analysis is a key feature in Endpoint Detection and Response (EDR) systems. It focuses on scrutinizing patterns, activities, and trends among programs and users. It works by creating a user’s typical behavior profile and promptly identifying any deviations from this norm.
For instance, a user who usually downloads a certain amount of data suddenly downloads significantly more. With Behavioral Analysis, this behavior change would be flagged by the system.
Pros:
The advantages of Behavioral Analysis in EDR systems are manifold. It can detect threats that might otherwise go unnoticed, enhancing overall cybersecurity. By actively monitoring and analyzing user behavior, the system can identify potentially malicious activities that traditional security measures might miss. It also facilitates accurate and timely threat hunting and empowers organizations to regain control over their endpoints.
Cons:
However, there are certain disadvantages. One potential concern is the need to track and monitor user activities, which may raise privacy issues. Additionally, there is a possibility that legitimate changes in user behavior may be flagged as suspicious, leading to unnecessary investigations.
Costs:
Behavioral Analysis has extensive use cases. It can be used to detect insider threats, where employees or authorized users may engage in malicious activities. Behavioral Analysis can also safeguard against external cyber-attacks. It does this by detecting and responding to suspicious activities that may indicate an ongoing breach attempt.
The cost of implementing and maintaining a Behavioral EDR system can vary. It depends on the specific solution and the size of the organization.
Value:
The value provided by Behavioral EDR in terms of enhanced threat detection and response capabilities can outweigh these costs. This is especially true considering the potential financial and reputational damage that can result from a major cybersecurity incident.
3. Anomaly Detection: Spotting the Odd One Out
Anomaly Detection in EDR tools uses advanced analytics and machine learning to spot deviations from typical behavior, indicating potential threats. This feature is crucial for detecting unknown threats that don’t match known patterns.
Pros:
enhanced threat detection and proactive security, allowing for threat hunting before a breach occurs.
Cons:
it may lead to false positives and requires complex implementation.
Costs:
vary, including the initial purchase, maintenance, and potential training costs.
Use cases:
- detecting zero-day attacks
- identifying insider threats.
4. Threat Hunting: The Proactive Protector
This feature is a proactive approach to identifying potential threats before they can cause harm. It involves actively searching for, investigating, and advising on threat activity in your environment. When a threat is found, the EDR tool works alongside your team to triage, investigate, and remediate the incident. Thus, preventing it from escalating into a full-blown breach.
Pros:
- Proactive Defense: Threat hunting allows for early detection of potential threats, reducing the risk of a successful attack.
- Swift Response: It enables quick action on identified threats, minimizing potential damage.
Cons:
- Requires Expertise: Effective threat hunting requires a skilled security team with knowledge of potential threats and attack patterns.
- Time-Consuming: It can be a time-intensive process, especially in large networks.
Costs:
Implementing a threat hunting feature may require investment in skilled personnel and advanced EDR tools.
Value:
However, the value it provides in terms of early threat detection and prevention of potential breaches can outweigh the costs. It can alert or stop threats that are not yet known or have not been encountered before. Thus, providing an additional layer of security.
Use Cases:
- Detecting Advanced Persistent Threats (APTs). Threat hunting can help identify signs of APTs, which are often sophisticated and can remain undetected for a long time.
- Identifying Insider Threats. Unusual behavior from legitimate users, which could indicate an insider threat, can be detected through threat hunting.
- Uncovering Zero-Day Exploits. Threat hunting can help identify the use of zero-day exploits, which take advantage of unknown vulnerabilities.
5. Threat Intelligence Integration: The Power of Collective Knowledge
Threat intelligence integration in the EDR toolkit bolsters real-time threat detection by correlating endpoint data with threat intelligence services. These services supply up-to-date information on emerging cyber threats, their tactics, and exploited vulnerabilities. This integration aids in pinpointing indicators of compromise (IOCs) and indicators of attack (IOAs). These are actions or events tied to known cyber threats or cybercriminals.
Pros:
- Enhanced Threat Detection. The integration with threat intelligence services boosts the EDR’s ability to effectively identify and respond to known threats.
- Real-Time Updates. Threat intelligence services offer real-time updates on new and emerging threats, enabling EDR to stay ahead of potential attacks.
- Improved Visibility. The integration provides a comprehensive view of the threat landscape, facilitating easier identification and response to threats.
Cons:
- Cost: The implementation and maintenance of threat intelligence integration can be costly, particularly for small and medium-sized businesses.
- Complexity: The integration process can be intricate and may necessitate skilled IT personnel for management.
- False Positives: The system may generate false positives, leading to unnecessary investigations.
Use cases:
- Detecting Zero-Day Attacks. The integration can help identify zero-day attacks by correlating endpoint data with information about new and emerging threats.
- Preventing Data Breaches. By identifying IOCs and IOAs, the system can detect potential data breaches and initiate preventive measures.
- Enhancing Incident Response. The integration offers valuable information that can be used to improve incident response strategies and remediation efforts.
6. Fileless Malware Detection: Catching the Invisible Threats
The feature of fileless malware detection in an Endpoint Detection and Response (EDR) toolkit is crucial in today’s cybersecurity landscape. Fileless malware is a type of malicious software that uses legitimate programs to infect a computer. leaving no footprint and making it challenging to detect and remove.
Pros:
- Enhanced Security. It can detect stealthy threats that traditional antivirus solutions might miss. This is because fileless malware operates in memory and does not rely on files.
- Real-Time Protection. This feature can identify and halt fileless attacks in real-time, preventing the spread of the infection.
- Mitigation of Advanced Threats. It can detect sophisticated threats like PowerShell exploits, which are commonly used in fileless attacks.
Cons:
- Complex Implementation. Implementing this feature might require advanced technical knowledge and resources, as it involves monitoring and analyzing in-memory processes.
- Potential False Positives. It could potentially flag legitimate processes as threats, leading to false positives.
Costs:
The cost of implementing and maintaining this feature could be high, depending on the EDR solution chosen.
Value:
The value of having this feature in your EDR toolkit is significant. It can alert and stop advanced threats that traditional security solutions might miss. These are threats such as attacks that exploit PowerShell or other scripting engines. This feature is particularly effective against attacks that do not rely on files, making them difficult to detect.
Use Cases of Fileless Malware Detection
- Preventing Data Breaches. An organization could use this feature to detect and stop a fileless malware attack that is attempting to steal sensitive data.
- Securing Remote Work. With the rise of remote work, an organization could use this feature to protect remote workers’ devices from fileless malware attacks.
- Protecting Critical Infrastructure. A utility company could use this feature to protect its network from fileless malware attacks that could disrupt essential services.
The fileless malware detection feature in an EDR toolkit might require significant investment and technical expertise to implement and maintain. However, its ability to detect and stop advanced, fileless threats makes it a valuable addition to any organization’s cybersecurity arsenal.
7. Intrusion Detection System (IDS)
The Intrusion Detection System (IDS) feature in an Endpoint Detection and Response (EDR) toolkit is vital for identifying and halting threats. It scrutinizes network traffic and pinpoints suspicious activities or known threats. The IDS offers improved security, real-time detection, and aids in compliance, which are significant advantages. However, it may incorrectly flag legitimate network traffic as suspicious, leading to false positives.
Additionally, the costs of implementation and upkeep can be substantial. IDS finds use in detecting zero-day attacks, identifying malware, and ensuring compliance. Implementing and maintaining the IDS has potential drawbacks. However, the enhanced security and compliance benefits outweigh the challenges.
8. Intrusion Prevention System (IPS)
The Intrusion Protection System (IPS) feature in EDR tools is a critical defense mechanism against cyber threats. It identifies and halts malicious activities in real-time. Thus, enhancing security by detecting a wide array of threats, including zero-day attacks and advanced persistent threats.
Pros:
real-time protection and aiding in regulatory compliance
Cons:
it may generate false positives, leading to unnecessary investigations.
its complexity may pose challenges for organizations without a dedicated IT security team.
Costs:
The costs of deploying and maintaining an IPS can be high.
Use cases:
- preventing data breaches by detecting and stopping attempts to exploit network vulnerabilities.
- It aids in compliance for industries where data security is regulated.
- provides an additional security layer for employees accessing the network from various remote locations and devices.
9. Botnet Detection
Botnet detection in EDR tools identifies networks of compromised computers (botnets) used to carry out attacks.
Pros:
- It can detect large-scale, coordinated attacks.
- It can also identify compromised systems within the network, allowing for targeted remediation.
- it can prevent large-scale attacks that could result in significant financial loss.
Cons:
- Botnet detection may struggle to identify decentralized botnets or those using advanced evasion techniques.
Costs:
- Implementing botnet detection can be moderately costly, requiring specialized tools and potentially additional personnel training.
Value:
Botnet detection can protect against distributed denial-of-service (DDoS) attacks, spam campaigns, and other large-scale threats.
Use Cases:
- Detecting and mitigating DDoS attacks.
- Identifying compromised systems within the network for targeted remediation.
10. Phishing Detection
Phishing detection is a feature that identifies phishing attempts. These events are fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity.
Pros:
- Enhances security by identifying and blocking phishing attempts.
- Protects sensitive data from being stolen.
Cons:
- May generate false positives, blocking legitimate communications.
- Requires regular updates to keep up with evolving phishing techniques.
Costs: Implementation and maintenance costs depend on the specific EDR solution.
Value: Helps prevent data breaches and unauthorized access to sensitive information.
Use Cases:
- Detecting and blocking phishing emails.
- Identifying suspicious websites that mimic legitimate ones.
11. Ransomware Protection
Ransomware protection is a feature that detects and blocks ransomware attacks. These are attacks which involve encrypting a user’s data and demanding a ransom for its release.
Pros:
- Protects data from being encrypted and held hostage.
- Can often reverse the effects of a ransomware attack if one occurs.
Cons:
- May not be able to stop all types of ransomware.
- Can be resource-intensive, potentially slowing down system performance.
Costs: Costs vary depending on the EDR solution.
Value: Protects valuable data and prevents financial loss from paying ransoms.
Use Cases:
- Blocking a ransomware attack in progress.
- Reversing the encryption of files in a ransomware attack.
12. Advanced Persistent Threat (APT) Detection
APT detection is a feature that identifies and mitigates advanced persistent threats. Advanced Persistent Threats are stealthy and continuous hacking processes often orchestrated by groups targeting a specific entity.
Pros:
- Provides protection against sophisticated, targeted attacks.
- Allows for early detection and mitigation of threats.
Cons:
- May not detect all APTs, especially new or evolving ones.
- Requires significant resources and expertise to manage effectively.
Costs: Costs can be high due to the complexity of APTs and the need for advanced detection capabilities.
Value: Protects against serious threats that can lead to significant data breaches and financial loss.
Use Cases:
- Detecting suspicious patterns of network traffic.
- Identifying and blocking communication with known malicious IP addresses.
13. Insider Threat Detection
Insider threat detection is a feature that identifies threats originating from within the organization. These are actors such as employees or contractors with access to the internal network.
Pros:
- Helps identify malicious or negligent activity from insiders.
- Can prevent data breaches and unauthorized access to sensitive information.
Cons:
- May generate false positives, leading to unnecessary investigations.
- Requires careful management to balance security with privacy concerns.
Costs: Costs depend on the specific EDR solution and the size and complexity of the organization’s network.
Value: Protects against threats that traditional external defenses might miss.
Use Cases:
- Identifying an employee downloading large amounts of data.
- Detecting unauthorized access to sensitive systems or information.
14. Rootkit Detection
Rootkit detection is a vital feature in an Endpoint Detection and Response (EDR) toolkit. It identifies and eliminates rootkits, a type of stealthy malware that provides unauthorized control over a network or application. Rootkits can deliver additional malware, such as ransomware, bots, keyloggers, or trojans. Rootkits are challenging to detect due to their ability to block some antivirus software and malware scanner software.
Pros:
- Enhanced Security. It provides an additional layer of security by identifying and eliminating stealthy threats.
- Protection Against Advanced Threats. Rootkits are sophisticated threats that can bypass traditional security measures. Rootkit detection can identify these threats and prevent them from causing damage.
- Early Detection. Rootkits can remain undetected for years. Rootkit detection can identify these threats early, preventing long-term damage.
Cons:
- Implementation Complexity. Rootkit detection requires sophisticated technology and expertise, which can be complex to implement.
- Cost. The cost of implementing and maintaining rootkit detection can be high, especially for small and medium-sized businesses.
- False Positives. Rootkit detection can sometimes result in false positives, leading to unnecessary investigations.
Use Cases:
- Preventing Data Breaches. Rootkit detection can identify and eliminate rootkits before they can cause a data breach.
- Protecting Against Advanced Persistent Threats (APTs). Rootkits are often used in APTs. Rootkit detection can identify these threats and prevent them from causing long-term damage.
- Compliance. Many regulations require businesses to implement advanced security measures, including rootkit detection.
15. Exploit Prevention
The Exploit Prevention feature is designed to proactively identify and block attempts to exploit system vulnerabilities. This feature is crucial for preventing cyber threats from accessing a system through known vulnerabilities.
Pros:
- Enhanced Security. It adds an extra layer of security by preventing the exploitation of known system vulnerabilities.
- Proactive Defense. It enables proactive defense against threats, reducing the likelihood of successful attacks.
- Cost-Effective. It can be more cost-effective in the long run as it can prevent costly breaches.
Cons:
- Maintenance: Keeping the exploit prevention feature updated with the latest threat information can be resource-intensive.
- False Positives: There is a possibility of false positives, which can lead to unnecessary actions and disruptions.
- Limited Scope: It can only prevent known exploits, and new or unknown exploits may still pose a threat.
Costs:
The costs of implementing and maintaining this feature can vary. It depends on the specific EDR solution and the size of the organization. However, the cost is often justified by the enhanced security and potential cost savings from preventing breaches.
Value:
This feature can alert or stop threats that attempt to exploit known vulnerabilities in the system. It can be particularly effective against threats like ransomware and advanced persistent threats (APTs) that often use exploit techniques.
Use Cases:
- Use this feature to prevent a known vulnerability in their server software from being exploited by a ransomware attack.
- An organization could use exploit prevention to block an attempted exploit of a known vulnerability in a widely used software application. Thus, preventing potential data loss or system compromise.
16. Memory Protection
The Memory Protection feature in an EDR toolkit is a crucial defense mechanism against advanced threats. It safeguards the system memory from unauthorized access and alterations, thereby preventing attacks that exploit memory vulnerabilities.
Pros:
- Enhanced Security. Memory Protection can detect and prevent memory-based attacks. These are attacks such as buffer overflow and injection attacks. Traditional antivirus solutions might miss these.
- Real-time Protection. It offers real-time defense by continuously monitoring memory usage patterns and blocking suspicious activities.
Cons:
- Performance Impact: Continuous monitoring of memory can consume system resources, potentially slowing down operations.
- False Positives: It may sometimes flag legitimate processes as malicious, leading to unnecessary alerts.
Costs: Implementing Memory Protection involves the initial cost of the EDR solution and ongoing maintenance costs. However, these costs can be offset by the potential savings from averting major security breaches.
Value: Memory Protection can alert or stop advanced threats that exploit memory vulnerabilities, enhancing the overall security posture.
Use Cases:
- Preventing Buffer Overflow Attacks. Memory Protection can prevent buffer overflow attacks where an attacker tries to overflow the buffer memory to execute malicious code.
- Stopping Injection Attacks. It can stop injection attacks where an attacker injects code into a program’s memory to alter its execution.
Remember, while Memory Protection enhances security, it should be part of a comprehensive security strategy, not a standalone solution.
Response and Remediation: The Counterattack
The ‘Response and Remediation: The Counterattack’ category in an Endpoint Detection and Response (EDR) system is vital for cybersecurity. These features act swiftly against threats, minimizing damage.
Pros:
- Swift action: These features isolate compromised hosts, containing the threat.
- Real-time response: They offer enhanced visibility, enabling direct threat remediation without impacting performance.
- Incident resolution: They speed up investigation and remediation, thanks to cloud-stored endpoint data for rapid analysis.
Cons:
- Implementation cost: These features require significant investment in finances and time.
- Maintenance: Regular updates and maintenance are needed to combat evolving threats.
- Expertise: A skilled security team is needed to interpret data and act appropriately.
These features alert and stop a range of threats, from ransomware and malware to advanced persistent threats (APTs). They provide an additional protection layer, responding to and neutralizing threats, safeguarding the organization’s network and data.
17. Incident Response: Your Rapid Reaction Force
Incident Response in EDR involves the system’s ability to respond to detected threats. This can include creating alerts, isolating hosts, deleting files, killing processes, initiating scans, or restoring systems2.
Pros: It allows for quick response to threats, minimizing potential damage. It also automates the response process, reducing the workload on security teams.
Cons: Automated responses can sometimes lead to false positives, which can disrupt normal operations.
Use Cases:
- Containing threats. If a threat is detected, the Incident Response feature can isolate the affected host to prevent the threat from spreading.
- Restoring systems. In the event of a successful attack, this feature can help restore systems to their pre-attack state.
18. Automated Threat Response: The Silent Sentinel
Automated Threat Response in EDR systems involves the use of predefined rules or machine learning algorithms to automatically respond to detected threats1.
Pros:
- It enables faster response times to threats, potentially preventing or minimizing damage
- It reduces the workload on security teams.
Cons: It may lead to false positives or negatives if the rules or algorithms are not accurately defined or trained.
Use Cases:
- Rapid threat response. If a known threat is detected, the system can automatically respond, preventing the threat from causing damage.
- Reducing workload. By automating responses, the system can handle a larger volume of threats, reducing the workload on security teams.
19. Remediation Tools: The Cleanup Crew
Remediation Tools in EDR systems are used to eliminate detected threats and restore affected systems.
Pros: They allow for the quick elimination of threats and restoration of systems, minimizing potential damage.
Cons: The effectiveness of these tools depends on the nature of the threat. Some advanced threats may be resistant to remediation efforts.
Use Cases:
- Eliminating threats. If a threat is detected, Remediation Tools can be used to eliminate the threat and prevent further damage.
- Restoring systems. In the event of a successful attack, Remediation Tools can help restore systems to their pre-attack state.
20. Risk Scoring: Prioritizing Your Battles
Risk scoring is a feature that assigns a risk level to each endpoint based on various factors such as the type of data it holds, its vulnerability to threats, and its importance to the organization.
Pros:
- Helps prioritize security efforts by identifying high-risk endpoints.
- Provides a quantifiable measure of risk, aiding in decision-making.
Cons:
- Requires continuous updating to reflect changes in the threat landscape.
- May not accurately reflect risk if not properly configured.
Costs:
- Implementation costs can vary depending on the complexity of the organization’s network.
- Maintenance costs include regular updates and adjustments to the scoring algorithm.
Value:
- Risk scoring can help prevent breaches by identifying and securing high-risk endpoints.
- It can alert to threats like malware or unauthorized access attempts.
Use Cases:
- An organization can use risk scoring to prioritize patching efforts, focusing first on high-risk endpoints.
- Risk scores can be used to justify security investments to stakeholders by demonstrating the level of risk in quantifiable terms.
21. Offline Protection: The Unseen Shield
Offline protection ensures that endpoints are secure even when they’re not connected to the organization’s network.
Pros:
- Provides security for remote or mobile endpoints.
- Protects against threats that exploit offline vulnerabilities.
Cons:
- Can be difficult to update or manage without a network connection.
- May not offer the same level of protection as online security tools.
Costs: Costs can include the purchase of specialized software and potential increases in endpoint resource usage.
Value: Offline protection can alert to or stop threats like malware that spreads via removable media or exploits offline vulnerabilities.
Use Cases:
- An organization with a large remote workforce can use offline protection to secure endpoints outside the office.
- Offline protection can secure endpoints in environments with unreliable internet connections.
22. Active Directory Integration: The Access Gatekeeper
Active Directory integration allows the EDR tool to use the organization’s Active Directory data for better visibility and control over endpoints.
Pros:
- Simplifies management of endpoint security by leveraging existing infrastructure.
- Can improve threat detection by incorporating user and endpoint data.
Cons:
- Requires a well-maintained Active Directory to be effective.
- Could expose more data to potential threats if the Active Directory is compromised.
Costs: Costs can include time and resources spent on integration and ongoing synchronization.
Value: Active Directory integration can alert to or stop threats like unauthorized access or privilege escalation.
Use Cases:
- An organization can use Active Directory integration to quickly apply security policies to new endpoints.
- Active Directory data can be used to identify unusual user behavior, such as login attempts outside of normal hours.
23. SIEM Integration
SIEM integration allows the EDR tool to send its data to a Security Information and Event Management (SIEM) system for further analysis.
Pros:
- Enhances threat detection and response by combining data from multiple sources.
- Allows for centralized logging and reporting of security events.
Cons:
- Requires a compatible SIEM system.
- Can increase the volume of data that the SIEM system must process.
Costs: Costs can include the purchase of a SIEM system (if not already in use) and resources spent on integration and data management.
Value: SIEM integration can alert to or stop complex threats that require correlation of events across multiple systems.
Use Cases:
- An organization can use SIEM integration to correlate endpoint data with network data to detect advanced threats.
- SIEM integration can aid in compliance by providing centralized logging and reporting of security events.
24. Threat Feed Integration
Threat Feed Integration is a feature that allows EDR systems to correlate endpoint data with real-time data from threat intelligence services, providing updated information on new and recent cyber threats. This feature enhances the ability of the EDR system to identify potential threats and suspicious activities.
Pros:
- It provides real-time updates on new threats, enhancing the system’s ability to detect and respond to threats.
- It helps in identifying patterns associated with known threats
Cons:
- The effectiveness of this feature depends on the quality of the threat intelligence feed.
- Poor quality feeds may lead to false positives or missed threats.
Use Cases:
- Detecting emerging threats: Threat Feed Integration can help identify new types of malware or attack patterns that are currently spreading across the internet.
- Enhancing threat response: By understanding the tactics used by cyber threats, the EDR system can better respond and mitigate these threats.
25. Self-Defense Mechanisms
Self-Defense Mechanisms in EDR systems are designed to protect the EDR system itself from being compromised by threats. This feature is crucial as attackers often target security systems to disable them.
Pros: It enhances the resilience of the EDR system, ensuring that it remains functional even when under attack.
Cons: Implementing robust self-defense mechanisms can be complex and may require additional resources.
Use Cases:
- Protecting EDR systems: Self-Defense Mechanisms can prevent attackers from disabling the EDR system, ensuring continuous protection.
- Mitigating targeted attacks: In the event of a targeted attack on the EDR system, Self-Defense Mechanisms can help to mitigate the attack and maintain system integrity.
Monitoring and Visibility: The All-Seeing Eye
The ‘Monitoring and Visibility’ category in an EDR toolkit offers real-time visibility into endpoint activities, enhancing threat detection and response.
Pros:
improved incident response and the ability to observe an adversary’s activities in real time. This leads to faster remediation of threats, enhancing the organization’s security.
Cons:
- implementing these features can be costly and resource intensive.
- They require significant data storage and processing capabilities.
- If not managed properly, this can lead to false positives or overlooked threats.
Value:
- They can alert and stop a wide range of threats, from malware to advanced persistent threats (APTs).
- By providing a comprehensive view of endpoint activities, they enable swift detection and response to threats.
26. Continuous Monitoring: The Constant Vigil
Continuous Monitoring is a vital feature of Endpoint Detection and Response (EDR) tools, providing real-time surveillance of endpoint devices to detect and counter cyber threats.
Pros:
- Enhanced Visibility: It offers real-time insight into all endpoints, enabling immediate detection and halting of adversary activities.
- Proactive Threat Detection: It identifies suspicious activities and threats in real time, facilitating swift response and mitigation.
Cons:
- Resource Intensive: It demands significant computational power and storage, potentially straining resources.
- False Positives: It may trigger unnecessary investigations due to false positives, potentially disrupting operations.
Costs: The costs of implementing and maintaining this feature can vary. It includes:
- the initial purchase or subscription cost of the EDR tool
- ongoing maintenance and update costs
- potential costs associated with additional hardware or infrastructure upgrades needed to support the feature.
Value: Continuous monitoring provides real-time visibility into endpoint activities, enabling the detection and mitigation of threats that may otherwise go unnoticed. This can include a wide range of threats, from malware and ransomware attacks to more sophisticated advanced persistent threats (APTs).
Use Cases:
- Detecting Malware: It can help detect malware infections in real time, allowing for immediate response and mitigation.
- Identifying Unauthorized Access: The feature can identify instances of unauthorized access to endpoint devices, enabling security teams to promptly respond and prevent potential data breaches.
- Monitoring Remote Workers: In today’s increasingly remote work environments, continuous monitoring can provide crucial visibility into the activities of remote workers, helping to identify and mitigate potential security risks.
27. Endpoint Activity Recording: The Chronicle of Endpoint Activities
Endpoint Activity Recording is a key feature of Endpoint Detection and Response (EDR) tools. It records activities and events on endpoints, providing security teams with the visibility they need to uncover incidents that might otherwise remain hidden [1].
Pros:
- Comprehensive Visibility: This feature offers a complete view of security-related endpoint activity, enabling real-time observation of an adversary’s activities.
- Incident Detection: By recording relevant activity, it helps catch incidents that might have evaded prevention.
- Historical Data: It provides historical data useful for retrospective analysis and investigation.
Cons:
- Resource Intensive: Recording and storing endpoint activities might require significant computational resources.
- Data Overload: The large amount of data generated could overwhelm security teams, making it challenging to identify relevant incidents.
- Cost: Implementing and maintaining this feature could be costly, depending on the network’s size and complexity.
Use Cases:
- Detecting Advanced Persistent Threats (APTs): Endpoint Activity Recording can help identify patterns of behavior associated with APTs.
- Incident Response: In a security incident, the recorded endpoint activities can provide valuable information for the incident response team.
- Compliance: For organizations subject to regulations requiring the logging and monitoring of endpoint activities, this feature can help meet those requirements.
28. Network Traffic Analysis: The Traffic Cop
Pros:
- provides visibility into network activity, helping to detect anomalies and potential threats.
- It can identify suspicious behavior, such as unusual data transfers, which could indicate a data breach or malware activity.
Cons:
- NTA can generate false positives, leading to unnecessary alerts.
- It also requires significant network resources and can slow down network performance.
Costs:
- Implementing NTA involves the cost of the EDR tool itself, as well as potential infrastructure upgrades to handle the increased network load.
- Ongoing costs include maintenance and monitoring.
Value:
- NTA can detect threats that bypass other security measures, such as advanced persistent threats (APTs) and insider threats.
- It can also provide valuable insights for incident response and forensic analysis.
Use Cases:
- Detecting data exfiltration attempts by monitoring for large data transfers
- Identifying command and control (C&C) traffic associated with botnets.
29. Process Monitoring: The Process Patrol
Pros:
- Process Monitoring allows for real-time visibility into all processes running on an endpoint.
- It can detect malicious processes, such as those associated with malware or ransomware.
Cons:
- It can generate false positives.
- It can also impact system performance, particularly on endpoints with limited resources.
Costs:
- Costs include the price of the EDR tool and potential system upgrades.
- Ongoing costs involve maintenance and monitoring.
Value:
- Process Monitoring can detect threats that traditional antivirus solutions might miss, such as fileless malware.
- It can also provide valuable context for incident response and threat hunting.
Use Cases:
- Detecting and stopping ransomware by monitoring for processes that start encrypting files;
- Identifying stealthy malware that injects malicious code into legitimate processes.
30. Log Collection and Analysis: Watching Systems Under Attack
Pros:
Log Collection and Analysis provides a record of events on an endpoint, which can be invaluable for detecting threats and investigating incidents.
Cons:
- The volume of log data can be overwhelming, making it difficult to identify relevant events.
- Storing and processing log data can also require significant storage and computational resources.
Costs:
- Initial Costs include the EDR tool, potential infrastructure upgrades to handle the data volume, and storage costs for log data.
- Ongoing costs involve maintenance, monitoring, and potentially additional staff to analyze log data.
Value:
- Log Collection and Analysis can provide insights into past and ongoing threats, aiding in incident response and threat hunting.
- It can also support compliance efforts by providing an audit trail of events.
Use Cases:
- Investigating a security incident by analyzing log data to determine what actions were taken by an attacker
- Identifying a brute force attack by analyzing log data for numerous failed login attempts.
31. User Activity Monitoring: The User Watchdog
Pros: User Activity Monitoring provides visibility into user actions, helping to detect insider threats and compromised accounts.
Cons:
- It can be seen as invasive, potentially leading to privacy concerns.
- It can also generate false positives, particularly in environments where user behavior is not consistent.
Costs:
- Costs include the EDR tool and potential system upgrades.
- Ongoing costs involve maintenance, monitoring, and addressing privacy concerns.
Value:
- User Activity Monitoring can detect threats that other measures might miss, such as insider threats and compromised user accounts.
- It can also support compliance efforts by providing a record of user actions.
Use Cases:
- Detecting a malicious insider by monitoring for unusual user activity, such as accessing sensitive data they don’t normally interact with
- Identifying a compromised account by detecting unusual login activity, such as logging in at odd hours or from unusual locations.
Data Protection and Compliance: The Guardian of Your Treasure
Data Protection and Compliance features in an EDR toolkit act as protectors of your digital assets, ensuring the security of your data and adherence to necessary regulations.
Pros:
- They offer enhanced security by adding an extra layer of protection against breaches and unauthorized access to sensitive data.
- They assist organizations in meeting regulatory requirements, thereby reducing the risk of non-compliance penalties.
- Implementing these features can enhance trust among customers and partners, ultimately boosting your organization’s reputation.
Cons:
- The initial cost of implementing these features can be high, especially for small and medium-sized businesses.
- Ongoing maintenance costs and updates can also be substantial.
- The complexity of these features might necessitate specialized staff to manage them, which adds to the overall expenses.
Nonetheless, these features are essential in today’s digital landscape, where data breaches are prevalent, and regulations are becoming increasingly stringent.
Cost: It is crucial to carefully evaluate the cost and complexity of implementing and maintaining these features.
Value: Ultimately, the value they provide will largely depend on the nature of your organization’s data and the specific regulations it needs to comply with.
32. Data Loss Prevention: The Data Lifeguard
Data Loss Prevention (DLP) is a feature that aims to protect sensitive data from being exposed. This is true whether the data was exposed accidentally or through malicious intent. It provides visibility and control over your information, wherever it resides or travels, and prevents insiders from exfiltrating sensitive data, such as customer records and product designs.
Pros:
- Protection of Sensitive Data: DLP keeps your confidential data safe from accidental exposure or malicious breaches.
- Visibility and Control: It provides accurate visibility into where your sensitive data lives and moves, offering control over your information.
- Regulatory Compliance: DLP facilitates compliance with global data protection laws and regulatory requirements.
Cons:
- Complex Implementation: Setting up DLP can be complex, requiring a deep understanding of the data that needs to be protected.
- Potential for False Positives: DLP systems can sometimes flag benign activities as suspicious, leading to unnecessary investigations.
- Cost: The cost of implementing and maintaining a DLP system can be high, depending on the scale of the organization and the complexity of its data.
Use Cases:
- Preventing Data Exfiltration: DLP can prevent sensitive information, such as intellectual property or customer data, from being leaked or stolen by enforcing policies that control where sensitive data can live and travel.
- Regulatory Compliance: Organizations dealing with sensitive data, such as healthcare or financial institutions, can use DLP to ensure they are compliant with data protection laws and regulations.
- Insider Threat Management: DLP can help organizations monitor and control data access and usage by employees, helping to prevent insider threats.
Costs:
- the exact figures can vary widely depending on the specific DLP solution, the size and complexity of the organization, and the nature of the data being protected.
- It’s also important to consider the potential cost savings from avoiding data breaches and regulatory fines.
33. Full Disk Encryption: The Vault Keeper
Full Disk Encryption (FDE) is a key EDR feature. It encrypts all data on a hard drive, including the operating system, applications, and user data. Thus, providing a robust defense against data theft. If a device is lost or stolen, the data remains secure without the encryption key.
Pros:
- Enhanced Data Security: FDE secures data even if a device is lost or stolen.
- Compliance: FDE aids organizations in meeting data protection regulations.
Cons:
- Performance Impact: Encryption can slow down system performance, especially on older devices.
- Key Management: Managing encryption keys can be challenging. Lost keys can make data irretrievable.
Costs: Costs for FDE implementation and maintenance vary, including licensing fees, hardware upgrades, and ongoing costs.
Value: FDE protects against data theft from lost or stolen devices and unauthorized data access, making it a valuable tool for organizations handling sensitive data.
Use Cases:
- Sensitive Data Protection. Firms like financial institutions or healthcare providers can use FDE to secure customer and patient data.
- Compliance. Organizations under regulations like HIPAA or GDPR can use FDE for data protection requirements.
- Remote Work Security. With remote work on the rise, FDE secures devices outside the traditional office, protecting data even if a device is lost or stolen.
34. Data Classification: The Data Librarian
Data Classification in EDR involves categorizing data based on its sensitivity and value to the organization. It helps in identifying what data needs protection and the level of protection required.
Pros: It enhances data security, aids in compliance with regulations, and helps in data management.
Cons: It can be time-consuming and complex, especially for large volumes of data. Incorrect classification can lead to data breaches.
Costs: Costs include the initial setup, ongoing maintenance, and potential costs for misclassification.
Value: It can alert or stop threats targeting sensitive data, thus preventing data breaches.
Use Cases:
- Identifying and protecting customer’s personal data.
- Classifying corporate financial data for enhanced security.
35. Data Sanitization: The Data Shredder
Data sanitization is the process of deliberately, permanently, and irreversibly removing or destroying the data stored on memory devices to make it unreadable and irrecoverable.
Pros:
- It ensures that sensitive data cannot be retrieved, protecting against unauthorized access [1].
- It aids in compliance with data protection regulations, reducing legal risks.
Cons:
- If not done correctly, data may still be recoverable, posing a security risk.
- It can be resource-intensive and may require specialized tools or software.
Costs: Implementing data sanitization might involve purchasing specialized software or services. Maintenance costs include regular updates and training.
Value: Despite these costs, the value lies in ensuring data privacy, reducing the risk of data breaches, and aiding in regulatory compliance.
Use Cases:
- Device Decommissioning: Before disposing of or repurposing devices, organizations use data sanitization to ensure no residual data remains.
- Data Breach Response: After a breach, affected devices undergo data sanitization to prevent further unauthorized data access.
- Regulatory Compliance: Companies in regulated industries sanitize data to meet data protection standards and avoid hefty fines.
- Threat Mitigation: Data sanitization can prevent unauthorized data retrieval, safeguarding against potential data breaches and cyberattacks targeting residual data.
36. Compliance Reporting: The Compliance Conductor
Compliance Reporting in EDR is the process of generating reports to demonstrate adherence to regulatory standards.
Pros: It helps in maintaining regulatory compliance, avoiding penalties, and enhancing trust with stakeholders.
Cons: It can be time-consuming and requires a thorough understanding of regulations.
Costs: Costs include the time and resources required to generate and maintain reports.
Value: It can alert on non-compliance issues, helping to avoid penalties and reputational damage.
Use Cases:
- Demonstrating GDPR compliance through reports.
- Reporting on HIPAA compliance in healthcare organizations.
37. Endpoint Management and Control: The Puppet Master
Endpoint Management and Control in EDR involves managing and controlling access to network endpoints to prevent security threats.
Pros: It enhances network security, allows for centralized control, and aids in detecting and responding to threats.
Cons: It requires continuous monitoring and can be complex to manage in large organizations.
Costs: Costs include the initial setup, ongoing monitoring, and maintenance.
Value: It can alert on unauthorized access attempts and stop potential threats at the endpoint level.
Use Cases:
- Controlling access to a corporate network in a large organization.
- Managing endpoints in a BYOD (Bring Your Own Device) policy scenario.
38. Endpoint Inventory: The Device Census Taker
Endpoint Inventory in EDR involves maintaining a record of all network endpoints, aiding in the management and security of devices.
Pros: It aids in device management, enhances security, and helps in identifying unauthorized devices.
Cons: It can be challenging to maintain in dynamic environments with many devices.
Costs: Costs include the time and resources required to maintain the inventory.
Value: It can alert on the presence of unauthorized devices, helping to prevent potential threats.
Use Cases:
- Maintaining an inventory of devices in a large organization.
- Identifying unauthorized devices in a network.
39. Device Control: The Device Dictator
Device Control in EDR involves managing the use of external devices to prevent data breaches and malware infections.
Pros: It enhances data security, prevents data theft, and stops malware spread via external devices.
Cons: It can be seen as restrictive by users and requires careful management to avoid hindering productivity.
Costs: Costs include the time and resources required for management and potential productivity loss.
Value: It can alert on unauthorized device usage and stop potential data breaches or malware infections.
Use Cases:
- Preventing data theft via USB drives in an organization.
- Stopping the spread of malware via external devices.
40. Geolocation Tracking: The Device Locator
Geolocation tracking is a feature that allows the EDR system to track the physical location of endpoints. This can be useful in identifying unusual or suspicious activity based on the location of the device.
Pros:
Geolocation tracking can help identify potential threats based on unusual location activity. For example, if a device is suddenly accessed from a location that is not typical for the user, it could indicate a potential security breach.
Cons:
- Geolocation tracking can raise privacy concerns, as it involves tracking the physical location of devices.
- It also requires additional resources to implement and maintain.
Costs:
- The costs of implementing geolocation tracking can vary depending on the specific EDR solution and the size of the organization.
- These costs could include the initial implementation costs, ongoing maintenance costs, and potential costs associated with addressing privacy concerns.
Value:
- Geolocation tracking can provide valuable insights into potential security threats based on location data.
- It can help identify unusual activity that could indicate a potential security breach, allowing for quicker response and mitigation.
Use Cases:
- Geolocation tracking can be useful in situations where devices are being used in multiple locations, such as in a remote work environment.
- It can also be useful in identifying potential security breaches based on unusual location activity.
41. Unified Endpoint Management (UEM) Integration
Unified Endpoint Management (UEM) integration allows the EDR system to be integrated with a UEM solution, providing a unified platform for managing and securing all endpoints.
Pros:
- UEM integration can provide a more streamlined and efficient approach to endpoint management and security.
- It can also provide a more comprehensive view of the organization’s IT infrastructure.
Cons:
- UEM integration can be complex to implement and may require additional resources.
- It may also require additional training for IT staff.
Costs:
- The costs of implementing UEM integration can vary depending on the specific EDR and UEM solutions.
- These costs could include the initial implementation costs, ongoing maintenance costs, and potential training costs for IT staff.
Value:
- UEM integration can provide a more comprehensive and efficient approach to endpoint management and security.
- It can provide a unified platform for managing and securing all endpoints, improving visibility and control over the organization’s IT infrastructure.
Use Cases:
- UEM integration can be useful in situations where the organization has a large number of endpoints to manage and secure.
- It can also be useful in providing a more comprehensive view of the organization’s IT infrastructure.
42. Secure Configuration Management: The Configuration Custodian
Secure Configuration Management is a feature that allows the EDR system to manage configurations on endpoints to comply with policies and industry practices.
Pros:
- Secure Configuration Management can help ensure that all endpoints are configured securely, reducing the risk of security breaches.
- It can also help ensure compliance with industry practices and regulations.
Cons:
- Secure Configuration Management can be complex to implement and may require additional resources.
- It may also require ongoing maintenance to ensure that all endpoints remain securely configured.
Costs:
- The costs of implementing Secure Configuration Management can vary depending on the specific EDR solution and the size of the organization.
- These costs could include the initial implementation costs, ongoing maintenance costs, and potential costs associated with ensuring compliance with industry practices and regulations.
Value:
- Secure Configuration Management can provide valuable insights into the security of the organization’s endpoints.
- It can help ensure that all endpoints are configured securely, reducing the risk of security breaches and helping to ensure compliance with industry practices and regulations.
Use Cases:
- Secure Configuration Management can be useful in situations where the organization has a large number of endpoints to manage and secure.
- It can also be useful in ensuring compliance with industry practices and regulations.
43. Patch Management Integration: The Patchwork Quilter
Patch Management Integration is a feature that allows the EDR system to be integrated with a patch management solution, providing a unified platform for managing and securing all endpoints.
Pros: Patch Management Integration can provide a more streamlined and efficient approach to managing and securing all endpoints. It can also provide a more comprehensive view of the organization’s IT infrastructure.
Cons: Patch Management Integration can be complex to implement and may require additional resources. It may also require additional training for IT staff.
Costs: The costs of implementing Patch Management Integration can vary depending on the specific EDR and patch management solutions. These costs could include the initial implementation costs, ongoing maintenance costs, and potential training costs for IT staff.
Value: Patch Management Integration can provide a more comprehensive and efficient approach to endpoint management and security. It can provide a unified platform for managing and securing all endpoints, improving visibility and control over the organization’s IT infrastructure.
Use Cases: Patch Management Integration can be useful in situations where the organization has a large number of endpoints to manage and secure. It can also be useful in providing a more comprehensive view of the organization’s IT infrastructure.
44. IoT Device Protection
Internet of Things (IoT) Device Protection safeguards Internet of Things devices from cyber threats. It’s crucial as IoT devices often lack built-in security, making them easy targets.
Pros: Enhances overall network security by protecting vulnerable devices. Reduces the risk of botnet attacks.
Cons: Can be costly and complex to implement due to the diversity of IoT devices.
Use Cases: Protecting smart home devices from being used in DDoS attacks. Securing industrial IoT devices in a manufacturing plant.45.
45. Mobile Device Protection
Mobile Device Protection secures smartphones, tablets, and other mobile devices from threats.
Pros: Protects against data breaches and malware. Enables secure remote work.
Cons: Can impact device performance. Requires user cooperation for effectiveness.
Use Cases: Enabling secure access to corporate data on personal devices. Protecting customer data on business-owned devices.
46. Virtual Machine Protection
Virtual Machine Protection secures virtual environments from cyber threats.
Pros: Protects against malware and attacks targeting virtual environments. Enhances data security in cloud deployments.
Cons: Can add complexity to cloud management. May impact virtual machine performance.
Use Cases: Securing cloud-based applications. Protecting data in virtualized data centers.
User Authentication and Access Control: The Doorkeeper
“User Authentication and Access Control” is a crucial category in Endpoint Detection and Response (EDR) systems. It serves as the gatekeeper, ensuring only authorized users can access endpoint devices and network resources. This feature is vital in preventing unauthorized access and potential cyber threats.
Pros:
- Enhanced Security. It strengthens security by ensuring only authorized users can access the network, reducing the risk of unauthorized access and potential data breaches.
- Compliance. It helps businesses comply with regulations that require strict access control measures.
- User Accountability. It provides a clear audit trail of user activities, promoting accountability.
Cons:
- Complexity: Implementing and managing access controls can be complex, requiring expertise and continuous management.
- Potential for Misconfiguration: Incorrect settings can inadvertently grant access to unauthorized users or block access to legitimate users.
- Costs: There are costs associated with purchasing, implementing, and maintaining these systems.
Implementing features in this category can help mitigate threats related to unauthorized access, such as data breaches and insider threats. However, the costs involved can be significant, including the initial purchase, implementation, and ongoing maintenance costs. Despite these costs, the value of these features in preventing unauthorized access and potential cyber threats makes them a worthwhile investment for businesses.
47. User Behavior Analytics: The Behavior Detective
User Behavior Analytics (UBA) uses machine learning to identify atypical behavior that could indicate a threat.
Pros: Can detect insider threats and compromised accounts. Enhances overall threat detection capabilities.
Cons: Can generate false positives. Requires significant data for effectiveness.
Use Cases: Identifying compromised user accounts. Detecting data exfiltration attempts.
48. Two-Factor Authentication: The Double Check
Two-factor authentication (2FA) is a security measure that requires two methods to verify your identity before granting access. It’s an additional layer of authentication to a username and password, often involving a smartphone app for verification.
Pros: 2FA significantly strengthens security, protecting against phishing, credential theft, social engineering, and password brute-force attacks. It’s effective even if a password is compromised, as the attacker would still need the second factor to gain access.
Cons: The main drawback is the added inconvenience to the user, as they must go through an extra step each time they log in. There could also be potential issues if the second factor, such as a mobile device, is lost or inaccessible.
Costs: The cost of implementing 2FA can vary depending on the solution chosen. Some methods, like SMS or email verification, may have minimal costs, while hardware tokens or biometric systems can be more expensive. Ongoing costs include user training and potential support for lost or malfunctioning second factors.
Value: 2FA is invaluable in protecting against unauthorized access, even if login credentials are stolen or guessed. It’s particularly useful for protecting sensitive data and systems.
Use Cases:
- Protecting user accounts in a corporate environment: If an employee’s password is compromised, 2FA prevents unauthorized access.
- Securing online banking: Banks often use 2FA to protect customers’ accounts, requiring a second factor (like a text message or hardware token) in addition to a password.
49. Network and Web Security: The Web Weaver
Network and Web Security involves protecting the underlying networking infrastructure from unauthorized access, misuse, or theft. It includes safeguarding devices, applications, and users, and implementing policies and controls to block malicious actors.
Pros: This feature provides robust protection against various threats, including malware, phishing, and DDoS attacks. It also offers granular control over web traffic, allowing organizations to block risky behaviors without hindering productivity.
Cons: Implementing comprehensive network and web security can be complex and may require significant resources. It may also require ongoing updates and maintenance to stay ahead of evolving threats.
Costs: Costs can vary widely depending on the specific solutions implemented. These might include firewalls, intrusion prevention systems, secure web gateways, and more. Ongoing costs include maintenance, updates, and potentially additional staff for management and response.
Value: Network and Web Security is crucial for protecting an organization’s data and maintaining the integrity of its systems. It can help prevent data breaches, protect proprietary information, and maintain a company’s reputation.
Use Cases:
- Protecting a corporate network: Network and web security can help prevent unauthorized access and protect sensitive data.
- E-commerce: For businesses that handle online transactions, network and web security can help protect customer data and maintain trust.
50. Wireless Security: The Airwave Guardian
Wireless Security involves protecting wireless networks from unauthorized access or damage. It includes implementing security measures like encryption and authentication protocols to secure wireless communications.
Pros: Wireless Security protects against threats like unauthorized access, data theft, and network interference. It’s essential for businesses that rely on wireless networks, as these can be more vulnerable than wired networks.
Cons: Wireless Security can be complex to implement and maintain, especially with the variety of devices and operating systems that may connect to a wireless network. It may also require regular updates to stay ahead of evolving threats.
Costs: Costs can vary depending on the security measures implemented. These might include secure access points, encryption software, and network monitoring tools. Ongoing costs include maintenance, updates, and potentially additional staff for management and response.
Value: Wireless Security is crucial for protecting an organization’s data and maintaining the integrity of its wireless networks. It can help prevent data breaches, protect proprietary information, and maintain a company’s reputation.
Use Cases:
- Securing a corporate wireless network: Wireless Security can help prevent unauthorized access and protect sensitive data.
- Protecting customer data in a retail environment: For businesses that offer customer Wi-Fi, Wireless Security can help protect customer data and maintain trust.
51. Virtual Private Network (VPN) Integration: The Tunnel Guide
Virtual Private Network (VPN) Integration involves incorporating VPN capabilities into the EDR solution. VPNs provide secure, encrypted connections, which are crucial when accessing a network from a remote or unsecured location.
Pros: VPN integration enhances security for remote workers or those using public Wi-Fi, as it encrypts data in transit, protecting it from interception. It also allows secure access to network resources from anywhere.
Cons: VPNs can sometimes slow down network speeds due to the encryption process. They also require management and updates to ensure security, which can add to the workload of IT teams.
Costs: The costs of VPN integration can vary depending on the chosen solution. Costs may include the initial setup, licensing fees, and ongoing maintenance and updates.
Value: VPN integration is invaluable for businesses with remote workers or multiple locations. It allows secure access to network resources, protecting data and maintaining productivity.
Use Cases:
- Remote Work: VPNs allow employees to securely access company resources from home or while traveling.
- Secure Data Sharing: Businesses can use VPNs to securely share sensitive data between different locations or with partners.
52. Secure Web Gateway (SWG): The Web Gatekeeper
SWG is a security solution that prevents unsecured traffic from entering an internal network of an organization. It filters out bad traffic and allows good traffic.
Pros: SWG provides real-time protection against web-based threats, such as malware, phishing, and botnets. It also offers URL filtering, application control, and data loss prevention.
Cons: Implementing SWG can be costly, and it may slow down network speeds due to the inspection of all incoming traffic.
Use Cases: SWG is useful in preventing employees from accessing malicious websites and ensuring secure browsing in an organization.
53. Web Filtering: The Web Editor
Web filtering involves blocking access to websites based on a set of security rules.
Pros: It helps protect the network from web-based threats and can be used to enforce internet usage policies.
Cons: Overly restrictive web filtering can hinder employee productivity and morale. It also requires regular updates to keep up with the ever-changing internet landscape.
Use Cases: Web filtering is used in schools to block access to inappropriate content and in businesses to prevent employees from accessing non-work related sites.
54. Email Security: The Mailman’s Shield
Email security involves protecting email accounts and content from cyber threats.
Pros: It protects against phishing, spam, malware, and ransomware attacks that are commonly delivered via email.
Cons: It can sometimes flag legitimate emails as spam, leading to important emails being missed.
Use Cases: Email security is crucial for businesses to protect sensitive information and maintain the integrity of their communication systems.
55. Email Filtering: Making the Spammers Disappear
Email filtering is the process of allowing software to categorize, organize, and manage email messages.
Pros: It reduces the risk of phishing and spam emails reaching the user’s inbox.
Cons: Legitimate emails can sometimes be marked as spam, leading to missed communications.
Use Cases: Email filtering is used in businesses to sort incoming emails, prioritize them, and protect against spam and phishing attacks.
Visualization, Reporting, and Forensics: The Storyteller
This involves the use of tools to visualize, report, and conduct forensic analysis of security incidents.
Pros: It provides a clear and understandable view of security incidents, aiding in quicker response and resolution.
Cons: These tools can be complex to use and require skilled personnel to interpret the data.
Use Cases: These tools are used in incident response to understand the scope of a security incident and to aid in the investigation and remediation process.
56. Dashboard Visualization: The Security Storyboard
Dashboard visualization involves the use of dashboards to present data in a visual and easily understandable format.
Pros: It provides a quick overview of the security posture of an organization, helping to identify trends and patterns.
Cons: If not properly configured, dashboards can present misleading information.
Use Cases: Dashboard visualization is used in security operations centers (SOCs) to monitor the security status of an organization in real-time.
57. Detailed Reporting: The Chronicle of Security Events
Detailed Reporting in EDR tools refers to the comprehensive documentation of all activities and incidents detected by the system. It includes information about threat detection, response actions, system vulnerabilities, and more.
Pros: Detailed reporting provides a clear understanding of the security landscape, aids in compliance with regulations, and helps in identifying trends and patterns in threats. It also supports post-incident analysis and learning.
Cons: It may require significant storage space and can be time-consuming to analyze due to the volume of data. Also, without proper filtering, important details can be lost in the noise of irrelevant information.
Costs: Costs may include storage and management of large data volumes, and potentially additional personnel to analyze and interpret the reports.
Value: Detailed reporting can help in identifying security gaps, improving response strategies, and maintaining regulatory compliance. It can alert to both external threats and internal vulnerabilities.
Use Cases:
- Compliance Audits: Detailed reports can provide necessary documentation for compliance audits.
- Incident Response: Post-incident reports can aid in understanding the attack vector and improving future responses.
58. Forensic Analysis: The Crime Scene Investigator
Forensic Analysis in EDR involves the detailed investigation of cyber threats and incidents. It includes analyzing malware, understanding attack vectors, and identifying the source of the threat.
Pros: It aids in understanding the nature of threats, identifying vulnerabilities, and improving security measures. It also helps in gathering evidence for legal proceedings.
Cons: It requires specialized skills and can be time-consuming. Also, it may not always lead to conclusive results.
Costs: Costs include investment in specialized forensic tools and skilled personnel.
Value: Forensic analysis can help in mitigating future threats, improving security posture, and providing legal evidence.
Use Cases:
- Post-Incident Analysis: Forensic analysis can help in understanding how a breach occurred and how to prevent similar incidents in the future.
- Legal Proceedings: Forensic evidence can be used in legal proceedings against cybercriminals.
59. Historic Data Retention: They’re back again!
Historic Data Retention in EDR involves storing past security data and incident reports for future reference and analysis.
Pros: It allows for trend analysis, aids in identifying recurring threats, and supports post-incident investigations.
Cons: It requires significant storage space and effective data management strategies. Also, it raises concerns about data privacy and compliance with data retention policies.
Costs: Costs include data storage and management, and compliance with data privacy regulations.
Value: Historic data retention can help in identifying patterns in cyber threats, improving security strategies, and supporting forensic investigations.
Use Cases:
- Trend Analysis: Historic data can be used to identify trends in cyber threats and improve security measures.
- Forensic Investigations: Past data can aid in forensic investigations of security incidents.
Advanced Analytics and Machine Learning: The Oracle
Advanced Analytics and Machine Learning in EDR involves using sophisticated algorithms and AI to detect and respond to threats. It includes predictive analytics, anomaly detection, and automated response actions.
Pros: It can detect previously unknown threats, reduce response times, and lessen the workload on security personnel.
Cons: It requires significant computational resources and can generate false positives. Also, it may be vulnerable to AI-specific attacks.
Costs: Costs include investment in advanced analytics tools, computational resources, and skilled personnel.
Value: Advanced analytics and machine learning can enhance threat detection capabilities, improve response times, and automate routine tasks.
Use Cases:
- Anomaly Detection. Machine learning algorithms can detect unusual patterns that may indicate a cyber threat.
- Predictive Analytics. Advanced analytics can predict potential threats based on past data and trends.
60. Machine Learning Algorithms: The Learning Machine
Machine Learning Algorithms in EDR tools analyze data in real-time, identifying patterns that indicate known threats or suspicious activity. They can learn over time, improving their ability to detect threats and reduce false positives.
Pros:
- Enhanced threat detection. Machine learning can identify complex patterns and anomalies that might be missed by human analysts.
- Reduction in false positives. Over time, machine learning algorithms can learn to distinguish between normal and atypical behavior, reducing the number of false alarms.
Cons:
- Initial setup and tuning. Machine learning algorithms require initial setup and continuous tuning to perform optimally.
- Dependence on quality of data. The effectiveness of machine learning is highly dependent on the quality and quantity of data it’s trained on.
Costs: Implementing machine learning in EDR tools can be costly, particularly in terms of computational resources. However, the cost can be offset by the improved threat detection and reduction in false positives.
Value: Machine learning can detect a wide range of threats, including zero-day attacks and advanced persistent threats. It can also adapt to evolving threats, providing long-term value.
Use Cases:
- Detecting zero-day attacks: Machine learning algorithms can identify unusual patterns of behavior that may indicate a zero-day attack.
- Reducing false positives: Over time, machine learning can learn to distinguish between normal and atypical behavior, reducing the number of false alarms.
61. Artificial Intelligence Integration: The Intelligent Protector
AI integration in EDR tools enhances threat detection by learning from patterns and adapting to new threats. It automates threat analysis, reducing the workload on security teams.
Pros: AI can detect unknown threats, reduce false positives, and improve response times. It can adapt to evolving threats, providing robust security.
Cons: AI integration can be complex and requires skilled personnel to manage. It may also lead to over-reliance on technology, potentially missing threats that require human intuition to detect.
Costs: Implementing AI can be expensive due to the need for advanced hardware and skilled personnel. However, it can reduce long-term costs by automating threat detection and response.
Value: AI can detect and respond to sophisticated threats that traditional methods might miss. It can adapt to new threats, providing robust, future-proof security.
Use Cases:
- Detecting zero-day threats by analyzing patterns and anomalies.
- Automating threat response, reducing the burden on security teams.
62. Predictive Analytics: The Fortune Teller
Predictive analytics in EDR tools use past and current data about security activities to forecast potential threats.
Pros: It can identify threats before they occur, allowing for proactive defense. It reduces false positives, focusing on genuine threats.
Cons: Predictive analytics may not always be accurate and can miss new, unprecedented threats. It also requires a large amount of data to be effective.
Costs: Implementing predictive analytics can be costly due to the need for advanced algorithms and data storage. However, it can reduce costs by preventing attacks before they occur.
Value: Predictive analytics can provide an early warning system for threats, allowing organizations to respond proactively. It can reduce the impact of attacks by identifying them in the early stages.
Use Cases:
- Identifying potential threats based on unusual user behavior or network activity.
- Forecasting future threats based on trends in the threat landscape.
Why Small Businesses Need Endpoint Detection and Response Tools: The Final Verdict
In conclusion, the evolving landscape of cyber threats necessitates robust security measures. An Endpoint Detection and Response (EDR) policy is no longer a luxury but a necessity for businesses of all sizes. It provides comprehensive visibility into endpoint activities, enables swift detection and response to threats, and enhances overall cybersecurity posture.
Implementing an EDR strategy can seem daunting, but the benefits far outweigh the initial investment and effort. From real-time threat detection to user authentication and access control, EDR tools offer a wide range of features to safeguard your business against cyber threats.
Don’t wait for a cyber incident to disrupt your operations. Take action now. Start by creating an EDR policy that aligns with your business needs and risk profile. Then, choose an EDR solution that best fits your organization’s requirements. You might also consider a more inclusive small business cybersecurity checklist for the entire enterprise.
Remember, the cost of reacting to a cyber-attack is often much higher than proactively investing in a robust EDR strategy. Secure your business today for a safer tomorrow.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!
