Unlocking the Power of Network Segmentation: A Comprehensive Guide for Enhanced Security
In the dynamic world of cybersecurity, network segmentation emerges as a pivotal strategy for safeguarding digital assets. This practice involves dividing a computer network into smaller, distinct segments or subnets. Each subnet acts as a separate entity, enhancing security and control within the network. By implementing network segmentation, organizations can isolate critical systems and data, significantly reducing the attack surface and minimizing the impact of potential breaches.
The benefits of network segmentation are manifold. It not only strengthens security but also improves network performance and management. Segmentation enables more targeted control over network traffic and resources, ensuring that sensitive information remains inaccessible to unauthorized users. Additionally, it plays a crucial role in compliance and audit processes, providing clear demarcation and control over different parts of the network. This methodical approach to network design is essential in creating a resilient and secure network infrastructure that can withstand the evolving threats in the digital landscape.
What is Network Segmentation?
Network segmentation is the process of dividing a computer network into multiple, smaller subnetworks, each acting as a distinct segment. This division is primarily aimed at enhancing security and managing network traffic more effectively. By segmenting networks, organizations can control which users and devices have access to specific parts of the network, leading to a more secure and efficient network environment.
Segmented vs. Flat Networks
The contrast between segmented and flat networks is crucial in understanding the significance of network segmentation. In a flat network, all devices are on the same network segment and can communicate freely with each other. This lack of barriers, while simple in design, can lead to significant security vulnerabilities. In contrast, a segmented network divides the network into multiple segments, with controls over how and what each segment communicates. This structure significantly reduces the risk of widespread network breaches and isolates potential threats.
The Role of Network Segmentation in Security
Dividing a computer network into segments plays a vital role in enhancing its overall security posture. Segmented networks restrict the lateral movement of threats, confining any security breaches to a limited area and thereby minimizing their impact. This compartmentalization is essential in today’s cybersecurity landscape, where the ability to quickly isolate and address security incidents can be the difference between a minor disruption and a major breach. Network segmentation, therefore, becomes a cornerstone of robust network security strategies..
The Need for Network Segmentation in Small Businesses
Network segmentation is not just a concern for large enterprises; it’s crucial for small businesses too. Small businesses often operate with limited resources and may lack the extensive security measures of larger corporations. This makes them attractive targets for cybercriminals. Network segmentation offers a practical and effective layer of defense, limiting the potential damage of a breach by isolating critical systems and data.
Why Small Businesses Need to Segment
For small businesses, network segmentation is essential for safeguarding sensitive information and maintaining operational integrity. By dividing the network into segments, small businesses can control access to different parts of the network based on need and authority. This segmentation reduces the risk of a widespread attack and limits the potential damage should a breach occur. It’s a cost-effective solution that can significantly improve a small business’s security posture.
Real-World Breach Examples
The importance of network segmentation becomes clear when examining real-world breaches. One such incident is the massive 2013 Target data breach, which started from a phishing email in a small HVAC company’s unsegmented network. The malware eventually moved to Target’s network, leading to a significant breach.
Another example involves a casino where hackers exploited a vulnerability in an Internet-connected fish tank thermometer. This breach allowed them to access the casino’s high-roller database and extract data through the network. These incidents underscore the risks associated with unsegmented networks and highlight the crucial role of network segmentation in cybersecurity.
Benefits of Network Segmentation
Network segmentation provides numerous advantages beyond basic network management. It is a strategic approach that enhances overall network security and operational efficiency. Small businesses, in particular, can leverage these benefits to create a more secure and controlled network environment
Enhanced Access Control and Audit
One of the key benefits of network segmentation is the enhancement of access control and audit capabilities. By dividing the network into segments, businesses can assign access rights based on user roles and requirements. This targeted access control not only strengthens security but also simplifies compliance and auditing processes. It allows for detailed monitoring and logging of activities within each segment, enabling more effective detection and investigation of anomalies.
Mitigating Breaches
Network segmentation plays a vital role in mitigating breaches. By isolating network segments, it limits the ability of attackers to move laterally within the network. This containment significantly reduces the impact of breaches, confining them to a single segment rather than allowing unfettered access to the entire network. Segmentation, therefore, is crucial in both preventing breaches and minimizing their consequences, providing an essential layer of defense in the cybersecurity arsenal of small businesses.
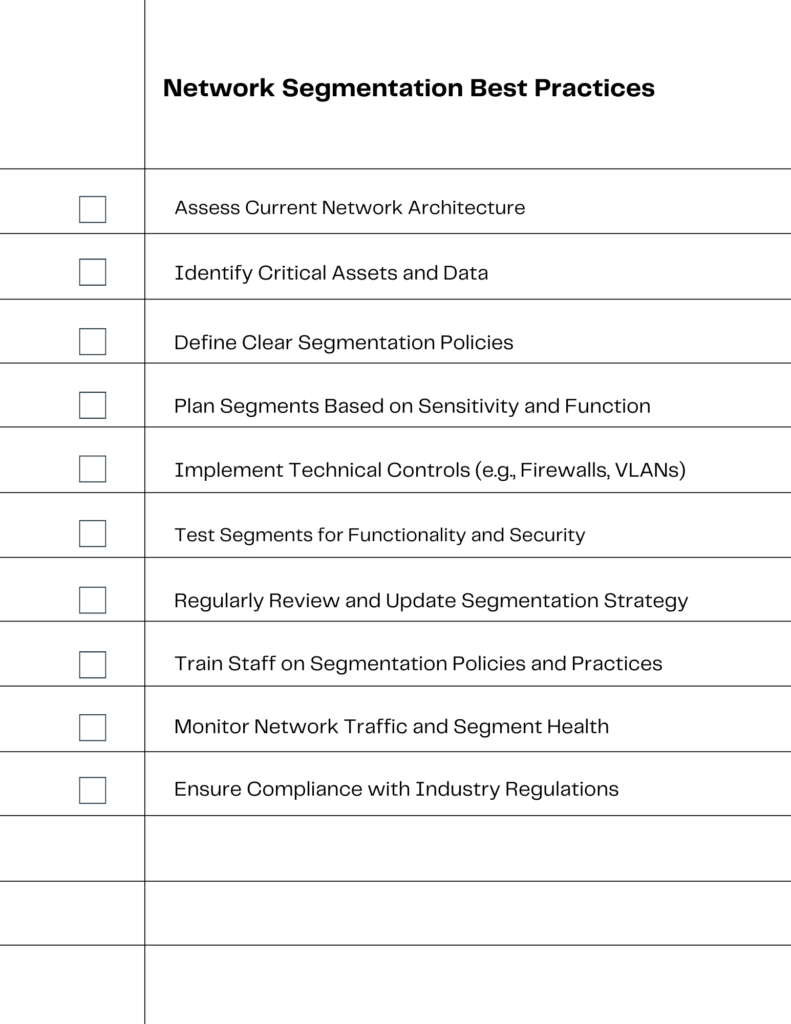
Best Practices in Network Segmentation
Implementing network segmentation effectively requires adherence to certain best practices, ensuring that the process not only enhances security but also aligns with the business’s operational needs. These practices are crucial for small businesses looking to maximize the benefits of segmentation.
Guidelines for Effective Segmentation
Effective network segmentation begins with a clear understanding of the network’s structure and security needs. Best practices include starting with a detailed network map, defining clear security policies, and segmenting the network based on sensitivity and functionality of different areas. It’s also crucial to establish mechanisms to enforce segmentation, ensuring that the defined policies are adhered to consistently across the network. Regular reviews and updates of the segmentation strategy are also essential to adapt to changing security landscapes and business requirements.
Understanding Network Flows
Understanding network flows is integral to effective segmentation. It involves analyzing how data moves across the network and identifying critical points that require enhanced protection. Recognizing these flows helps in designing segments that optimize security without hindering network performance. This understanding is vital for implementing segmentation that is both secure and efficient, ensuring that security measures do not impede the necessary flow of data and operations within the business.
Steps to Implement Network Segmentation
Implementing network segmentation is a strategic process that requires careful planning and execution. For small businesses, this process can be broken down into manageable steps, ensuring a smooth transition to a segmented network that enhances security and operational efficiency.
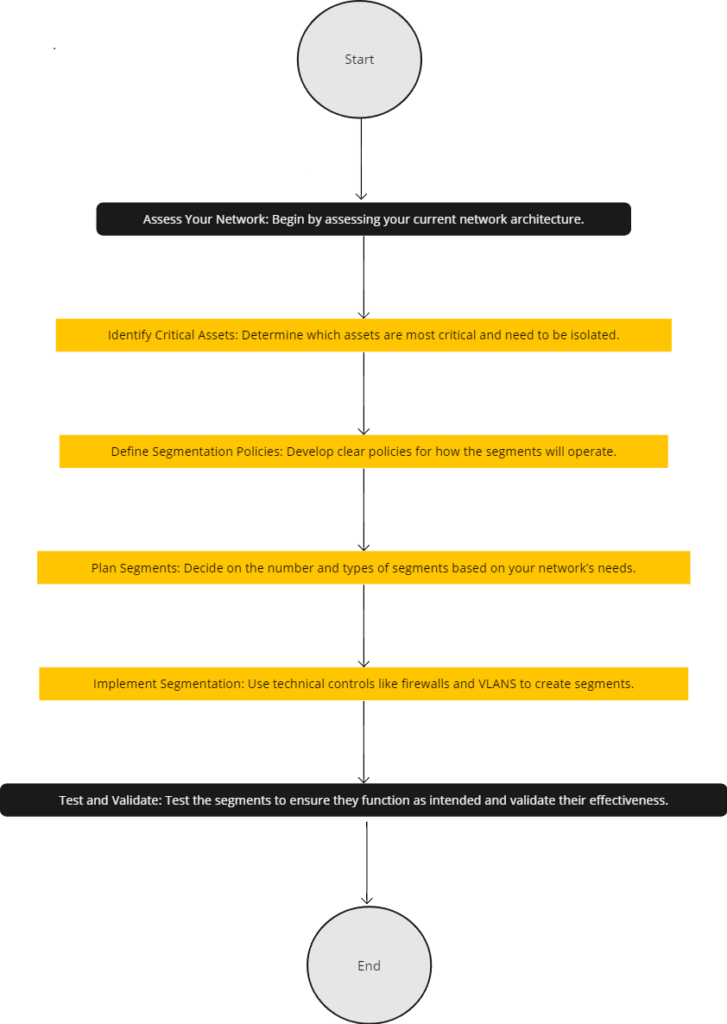
Step-by-Step Implementation Guide
- Assess Your Network: Begin by assessing your current network architecture.
- Identify Critical Assets: Determine which assets are most critical and need to be isolated.
- Define Segmentation Policies: Develop clear policies for how the segments will operate.
- Plan Segments: Decide on the number and types of segments based on your network’s needs, focusing on how to create smaller network segments for more granular control and security.
- Implement Segmentation: Use technical controls like firewalls and VLANS to create segments.
- Test and Validate: Test the segments to ensure they function as intended and validate their effectiveness.
Network Isolation and Partitioning
Network isolation and partitioning are essential aspects of network segmentation. This involves creating distinct segments that are isolated from each other, preventing unauthorized access between them. The use of VLANS and subnets are common methods for achieving this. The goal is to ensure that critical assets are separated from less sensitive areas of the network, thereby reducing the risk of a breach spreading across the entire network. Proper partitioning is key to a secure and well-functioning segmented network.
Segmenting Your Network: Key Considerations
Effective network segmentation requires careful consideration of various factors to ensure that it meets both security and operational needs. It’s not just about dividing the network; it’s about doing so in a way that adds value and enhances security.
Factors to Consider
When segmenting your network, consider factors such as the nature of your business operations, the types of data you handle, compliance requirements, and the existing network architecture. Understanding these elements helps in creating a segmentation strategy that is tailored to your specific business needs.
Balancing Security and Functionality
While security is the primary focus of network segmentation, it’s vital to balance this with network functionality. Over-segmentation can lead to complications in network management and hinder business operations. A key aspect of this balance is endpoint security, which is crucial for small businesses. Effective endpoint security measures, integrated within the segmented network, help in protecting individual network entry points while maintaining the flow of legitimate traffic and operations. This integration is a critical step in ensuring that the network remains both secure and functional.
Network Segmentation for Compliance and Audit
Network segmentation is not just a technical measure; it’s a strategic tool for compliance and audit readiness, especially crucial for small businesses navigating complex regulatory environments.
Compliance Benefits
Network segmentation significantly aids in meeting compliance and audit requirements. By segmenting the network, businesses can ensure sensitive data is isolated, making it easier to enforce compliance-related security policies. This isolation is particularly important in industries governed by strict data protection regulations. It also simplifies the audit process, as auditors can focus on specific segments rather than the entire network.
Case Studies and Examples
Here are 3 case studies of how network segmentation affects compliance:
- ServiceNow: Enhanced compliance with client audits and protected core services in a multicloud environment using Illumio Secure Cloud.
- Oil and Gas Refinery: Overcame data loss and improved compliance with industry regulations through effective network segmentation.
- Modern Woodmen of America: Improved security against unknown traffic and ensured secure 24/7 access to applications by adopting VMware NSX-T for network segmentation.
Overcoming Challenges in Network Segmentation
While network segmentation offers significant security benefits, implementing it can present challenges, especially for small businesses with limited IT resources. Understanding these challenges is key to successful implementation.
Identifying Common Challenges
Common challenges in network segmentation include complexity in planning and implementation, particularly when dealing with a variety of network devices, potential disruptions to business operations, and difficulty in balancing security with accessibility Additionally, small businesses might face challenges in terms of technical expertise and resource allocation for ongoing management of a segmented network.
Strategies for Overcoming Challenges
To overcome these challenges, businesses can adopt a phased approach to segmentation, starting with the most critical areas. Leveraging automated tools and seeking expert consultation can simplify the process. Regular training and awareness programs for staff can help mitigate operational disruptions. It’s also crucial to continuously monitor and adjust the segmentation strategy to align with changing business needs and evolving security threats.
Advanced Segmentation Practices
As network security evolves, so do the practices and techniques of network segmentation. Staying ahead of the curve requires an understanding of advanced segmentation strategies and future trends.
Exploring Advanced Techniques
Advanced techniques in network segmentation include the use of software-defined networking (SDN) to create dynamic segments, automation for efficient management, and the integration of machine learning for adaptive security policies. Implementing virtual local area networks (VLANs) and subnetting, which often involves allocating specific IP addresses to different network segments, are also part of advanced strategies, allowing for greater granularity and control.
Future Trends in Network Security
Future trends in network security point towards increased automation and the use of artificial intelligence to predict and respond to threats. The integration of IoT and edge computing with network segmentation strategies is also on the rise, requiring more sophisticated segmentation approaches. As networks continue to grow in complexity, the need for advanced segmentation practices that can adapt and scale will become increasingly important.
Securing Your Future: Embracing Network Segmentation Best Practices for Optimal Cybersecurity
In conclusion, network segmentation stands as a fundamental component in fortifying a business’s cybersecurity defenses. It not only limits the impact of potential breaches but also enhances overall network management and compliance. Small businesses, in particular, can gain significant security advantages by implementing proper segmentation strategies.
We encourage our readers to either implement or review their existing network segmentation practices, using this article as a complete guide. In an era where cyber threats are constantly evolving, adopting network segmentation is essential not only as a best practice but also as a key strategy in mitigating various security risks, securing your digital future.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!