
What is Small Business Endpoint Security and why do small businesses need it?
The role of endpoint security for small businesses is increasingly evident. A report from IT Governance highlighted stastitics for March 2023. In just that month, cybercriminals compromised an alarming 41.9 million records worldwide. This marked a 951% increase from the previous year. These alarming figures underscore the escalating cybersecurity threats. In addition, they also amplify the need for robust endpoint security solutions to safeguard sensitive data.
Key Takeaways
- Critical Need for Endpoint Security: Cyber threats are escalating. This makes robust endpoint security essential to safeguard sensitive data.
- Vulnerabilities from Unexpected Sources: Every connected device can be a potential entry point for cyberattacks. Even a smart thermometer.
- Unique Challenges for Small Businesses: Limited budgets and IT resources make small businesses attractive targets for cybercriminals.
- Advanced Protection Over Traditional Antivirus: Modern endpoint security offers comprehensive solutions. This includes real-time threat detection and response, tailored to combat sophisticated cyber threats.
Consider the unusual case from 2017. A casino fell prey to a sophisticated cyberattack. It wasn’t through its complex IT infrastructure. It was through an unexpected vector – a smart thermometer in an aquarium. Connected to the casino’s network, this seemingly innocuous device became the hacker’s gateway. By exploiting this vulnerability, cybercriminals were able to navigate through the casino’s network. They remained undetected as they exfiltrated 10GB of sensitive data. This data likely included details about high-value patrons. This data breach was orchestrated via the fish tank thermometer. It was transmitted to a server in Finland, exemplifying the ingenious tactics of modern cyberattacks.
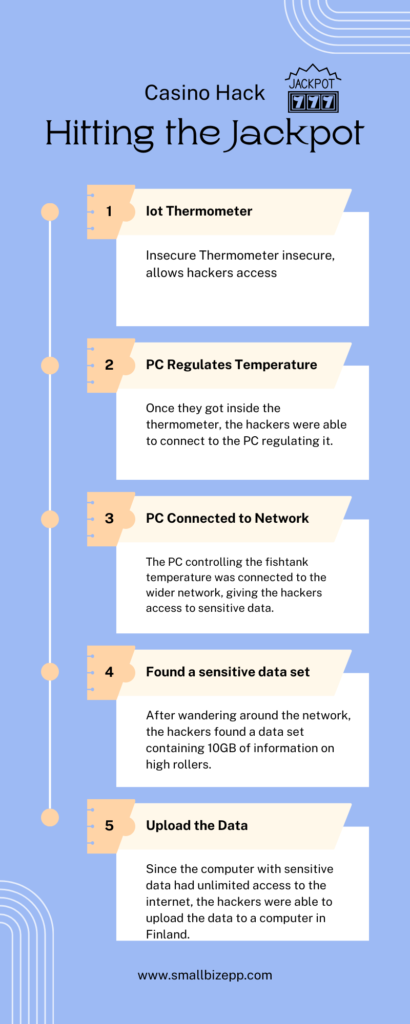
This incident vividly illustrates the risks posed by connected devices, often considered benign. It serves as a powerful reminder that every endpoint can be a potential vulnerability if not secured meticulously. Any endpoint is vulnerable, from laptops and mobile devices to smart thermometers. For small businesses, this is a clarion call. They need to recognize their susceptibility to cyberattacks. They need to embrace comprehensive endpoint protection measures. Implementing effective endpoint security is essential. At least to protect against traditional viruses and malware. In addition, businesses need to defend against sophisticated cyberattacks. Attacks that exploit every possible entry point, including the least expected ones.
Why Endpoint Security Is Important for Small Businesses?
Today, small businesses face unique security challenges. This makes the role of endpoint security more critical than ever. Larger corporations have extensive resources and dedicated cybersecurity teams. On the other hand, small businesses often operate with limited budgets and IT expertise. This disparity does not diminish the risks they face; in fact, it often makes them more attractive targets for cybercriminals.
Targeted by Cybercriminals: Small businesses are increasingly becoming targets for cyberattacks. This is due to perceived lower defense mechanisms. Cybercriminals exploit vulnerabilities in endpoint devices. Endpoint devices are devices such as laptops, mobile devices, and even Internet of Things (IoT) devices. This allows hackers to gain unauthorized access to sensitive business data.
Increased Risk with Remote Work and BYOD: There is an increase in remote work and Bring Your Own Device (BYOD) policies. This has expanded the range of endpoint devices connecting to business networks. Each device that connects to your network potentially introduces vulnerabilities. Thus, making endpoint security essential to protect against unauthorized access and data breaches.
Vital for Business Continuity: A breach can be devastating for a small business. It can lead to significant financial losses, reputational damage, and in some cases, the end of business operations. Implementing effective endpoint security is about protecting data. But more than that, it’s about ensuring business continuity and maintaining trust with customers.
How Endpoint Security Differs from Traditional Antivirus Software?
Traditional antivirus software plays a role in defending against malware and viruses. However, endpoint security provides a more comprehensive solution for the modern small business.
| Feature/Aspect | Traditional Security Software | Endpoint Security Protection |
|---|---|---|
| Detection Method | Relied on a database of known malware signatures. Couldn’t detect new or modified malware. | Uses behavioral analysis and heuristics to monitor for suspicious behaviors. It can detect previously unseen threats. For example, a new malware variant would be identified by EPP based on suspicious behavior. |
| Management | Required manual updates and individual configurations for each device. | Provides a centralized dashboard for monitoring all devices. It also helps to deploy updates and enforcing security policies uniformly. For example, an IT team would not face the same challenges when manually updating traditional software across multiple devices versus the ease of centralized management with EPP. |
| Defense Mechanism | Primarily reactive. Detected and removed threats after infiltration. | Proactive approach with preventive measures like application allowlisting and sandboxing. For example, EPP would proactively prevent the malware from accessing a system that traditional software would try to remove after infiltration. |
| Integration Capabilities | Operated as standalone solutions with limited integration capabilities. | Seamlessly integrates with other security tools like firewalls, intrusion detection systems, and SIEM platforms for holistic protection. For instance, EPP’s integration with a firewall would enhance the overall security posture of a business. |
Beyond Virus Protection
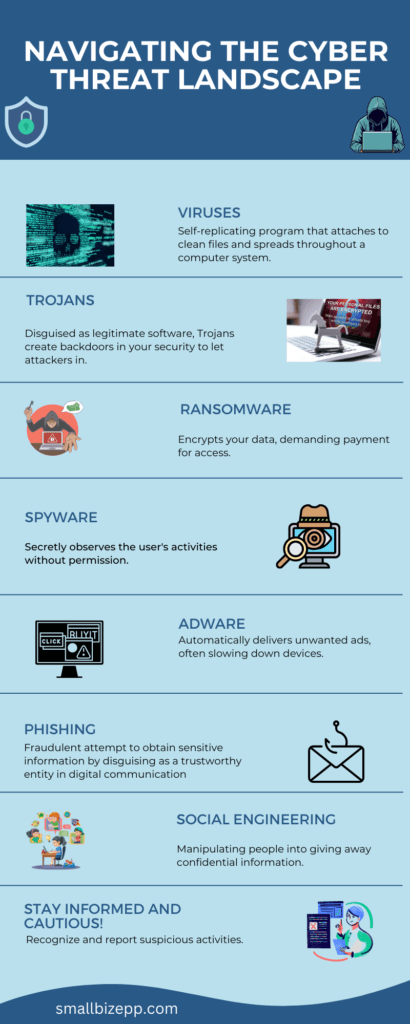
Traditional antivirus software is designed to detect and remove known viruses and malware. However, today’s cyber threats are more advanced than ever. With tactics like ransomware, phishing, and zero-day attacks. These are tactics that traditional antivirus may not effectively counter.
Integrated Security Approach
Endpoint security solutions offer an integrated approach. They combine the basic functions of antivirus with advanced protection mechanisms. This includes real-time threat detection, endpoint detection and response (EDR), and firewalls. Thus providing a holistic defense against a wider range of cyber threats.
Tailored for Modern Threats
Endpoint security solutions are tailored to address modern threats. These threats include advanced persistent threats (APTs) and sophisticated cyberattacks. These solutions provide a level of security that adapts to the evolving landscape. Thus ensuring small businesses are protected against the latest threats.
What are the Key Components of an Endpoint Security Solution?
The robustness of an endpoint security solution is pivotal for small businesses. These solutions are designed to protect a range of endpoint devices. These devices range from laptops and desktops to mobile devices. They encompass several essential features that work in tandem. Thus, they offer comprehensive defense against cyber threats.
Comprehensive Threat Detection. Central to endpoint security is the capacity for advanced threat detection. This involves ongoing surveillance of endpoint activities. This surveilance can identify any unusual or suspicious behavior. Behaviors that could indicate malware, ransomware, or other cyber threats. Threat detection can leverage machine learning and behavior-based detection. With that, these systems can dynamically adapt to new and evolving cyberattack strategies.
Proactive Response and Remediation. Beyond detection, effective endpoint security solutions actively engage in responding to threats. This includes automated actions such as isolating compromised devices and halting malicious activities. Remediation processes are then initiated to contain and neutralize threats. This is essential in limiting damage and preventing an attack from proliferating within the network.
Endpoint Protection Platform (EPP). An EPP integrates various security technologies. These are technologies such as antivirus, anti-malware, data encryption, and intrusion prevention systems. This multi-layered approach constructs a holistic defense against diverse security risks.
Regular Updates and Patch Management. Endpoint security software must receive regular updates. These updates ensure the system’s readiness against emerging threats. Efficient patch management addresses vulnerabilities in software and applications. Thus, curtailing the potential for exploitation.
User Education and Access Control. Equally important is the focus on user education. Also maintaining access control. Educating staff and enforcing stringent access controls enhances the overall security of a business.
Enhancing Detection: Advanced Endpoint Security Features
The evolution of threat detection capabilities helps to safeguard small businesses. Advanced endpoint security systems go beyond the traditional antivirus solutions. They incorporate real-time monitoring and proactive threat detection. This offers a more robust defense against cyber threats.
Real-Time Monitoring and Response
Modern endpoint security technologies are equipped with real-time monitoring tools. These tools continuously scan and analyze endpoint activities. This continuous vigilance ensures immediate detection of atypical behavior or suspicious activities. These activities are indicative of a potential cyberattack or malware intrusion. These systems can initiate prompt response measures on detecting events. Thus, significantly reducing the window of opportunity for hackers to cause damage.
Advanced Threat Detection Techniques
Contemporary endpoint security solutions employ a variety of sophisticated techniques for threat detection. These include heuristic analysis, behavior-based detection, and machine learning algorithms. Heuristic analysis allows for the identification of new, previously unseen viruses and malware. It does this by analyzing code behaviors and properties. Behavior-based detection focuses on the actions of applications and endpoints. Thus, flagging activities that deviate from normal patterns. Machine learning algorithms enhance the system’s ability to learn from new threats. These algorithms constantly improve its detection capabilities.
Endpoint Detection and Response (EDR)
A critical component in modern endpoint security is Endpoint Detection and Response. EDR systems provide a comprehensive analysis of threat patterns. They offer investigative capabilities post-detection. This feature is particularly valuable for small businesses. This is because it helps in mitigating the immediate threat. Further, it also aids in understanding the nature of the attack. Thus, it bolsters defenses against future incidents.
Enhancing Small Business Cybersecurity Posture
For small businesses, these advanced features translate to a heightened level of security. Small businesses have limited resources and less technical expertise compared to larger enterprises. Therefore, small businesses benefit immensely from endpoint security solutions. Especially those that offer a sophisticated, multi-layered approach to cybersecurity. This protection is crucial as cyber threats are becoming increasingly complex and multifaceted.
How Does Endpoint Protection Works in Small Businesses?
Endpoint protection plays a pivotal role in maintaining a secure digital environment. Understanding the mechanisms and technologies behind this protection is key. It allows one to appreciate its practical implications and effectiveness.
Fundamentals of Endpoint Protection. Endpoint protection in small businesses begins with the deployment of an EPP. This platform typically includes antivirus programs, anti-malware software, firewalls, and other security tools. It works by continuously scanning endpoint devices for malicious activities and known threats.
Centralized Management and Control. Small businesses benefit from the centralized management consoles. These consoles come with modern endpoint protection solutions. They provide a unified view of all endpoint activities. This makes it easier to monitor, manage, and respond to potential threats across the entire enterprise network. This centralization is crucial for small businesses with limited IT resources.
Layered Defense Strategy. Endpoint protection incorporates a layered defense strategy. This includes the basic protection against viruses and malware. Further, it includes advanced techniques for detecting and mitigating sophisticated cyber threats. Features like real-time threat detection and EDR play a crucial role in this layered approach.
Adapting to the Small Business Context. Endpoint protection is designed to be efficient and resource-conscious. Thus, ensuring that it doesn’t overwhelm the business’s IT infrastructure. These solutions are tailored to fit the specific business needs. Thereby, providing a level of security that aligns with the size and nature of the business.
How do we Balance Security and Usability in Endpoint Protection?
Security is paramount. However, it is equally important to ensure that endpoint protection solutions are user-friendly. They should not hinder employee productivity.
User-Friendly Interfaces. Ensuring that the endpoint protection software has a user-friendly interface is key. This includes intuitive dashboards and straightforward controls. These items allow employees to navigate the system effectively. Even with limited technical expertise,
Minimal Impact on Performance. Endpoint protection should secure the business. It should do this without significantly impacting the performance of endpoint devices. Solutions that are too resource-intensive can slow down devices, hampering employee productivity. Opting for lightweight, efficient software is essential.
Regular Training and Awareness. Conducting regular training sessions for employees is crucial. It will allow you to achieve a balance between security and usability. You need to educate them about:
- the importance of cybersecurity
- safe online practices
- how to use security tools effectively
This can go a long way in securing the business while maintaining ease of use.
Customizable Security Policies. Implementing customizable security policies allows businesses to tailor the level of security. They can even do this based on specific roles or departments. This ensures that security measures are stringent where necessary. However, they are not overly restrictive to the point of impeding workflow.
How to choose the Right Endpoint Protection for Your Business?
Selecting an appropriate EPP is crucial for small businesses. This platform significantly impacts their security and operational efficiency. Key considerations include:
- Assessing Business Needs. Understand your specific requirements based on business size, industry, and data types handled.
- Understanding the Threat Landscape. Identify the prevalent security risks in your industry and choose a solution that addresses these threats.
- Ease of Management and Scalability. Opt for solutions that are easy to manage and scalable.
- Budget Considerations. Balance cost-effectiveness with comprehensive security features.
- Vendor Reputation and Support. Consider the vendor’s reputation and the support services they offer.
Endpoint Security Solutions: Case Studies and Examples
Here are two real-world case studies of small businesses. They show how they effectively use endpoint security solutions:
- E-Bebek – Retail Sector. E-Bebek is a leading Turkish retailer specializing in products for expectant parents and children. They depend heavily on IT systems to manage sensitive customer and financial data. Their robust endpoint security solution is crucial for maintaining high-quality services. It also helps to protect them against cyber threats. E-Bebek Case Study
- AZ Sint-Jan – Healthcare Provider. AZ Sint-Jan provides advanced healthcare services. They must ensure the confidentiality of patient data. Further, they need to comply with health data protection regulations. Their endpoint security solution offers clarity, control, and optimum security. These are essential for their IT infrastructure supporting patient care. AZ Sint-Jan Case Study
These case studies show how businesses can implement endpoint security solutions. It helps them to protect sensitive data and adhere to industry regulations.
What is the Future of Endpoint Security?
Endpoint security for small businesses is poised to evolve significantly. It is driven by technological advancements and changing cyber threat landscapes.
Integration with Emerging Technologies. The integration of endpoint security with AI and IoT is expected to enhance threat detection capabilities. AI can provide predictive analytics. It can identify potential threats before they materialize. IoT security will become increasingly important as more devices connect to business networks.
Focus on Zero Trust Security Models. The concept of ‘zero trust’, where no entity within or outside the network is automatically trusted, is likely to gain prominence. This model ensures continuous verification. It can be effective in protecting businesses from insider threats and sophisticated cyberattacks.
Increased Use of Automation. Automation in endpoint security is expected to rise, reducing the reliance on manual processes. This can be particularly beneficial for small businesses with limited IT resources. It allows for more efficient threat detection and response.
Enhanced Customization and Scalability. Future endpoint security solutions will likely offer greater customization and scalability. This will cater to the diverse and evolving needs of small businesses. Tailored security strategies will enable businesses to address their specific security challenges effectively.
Evolving Security Risks and Endpoint Protection
As cybersecurity risks continue to evolve, so must the approach to endpoint protection.
Adapting to Advanced Threats. Small businesses will need to stay vigilant against increasingly sophisticated threats. This includes advanced persistent threats (APTs) and ransomware. Endpoint security solutions must continually adapt, offering advanced detection and response capabilities.
Emphasis on Comprehensive Security Education. Educating employees about evolving cyber threats will become more important. A well-informed workforce can significantly bolster a business’s overall security posture.
Regular Software Updates and Vulnerability Assessments. Keep endpoint security software updated and regularly assess vulnerabilities. This will be critical in staying ahead of new threats. A proactive approach is essential for small businesses. It will help them to protect their digital assets and maintain business continuity.
Collaboration with Security Experts. Small businesses may increasingly collaborate with cybersecurity experts to enhance their security strategies. This collaboration can provide access to specialized knowledge and resources. This is especially valuable for businesses with limited in-house cybersecurity expertise.
In conclusion, the future of endpoint security for small businesses involves a blend of:
- advanced technology
- adaptive strategies
- continuous education.
Stay abreast of these developments. Embrace proactive security measures. These will be key to safeguarding against evolving cyber threats.
Frequently Asked Questions
What is endpoint security for business?
Endpoint security, also known as business endpoint protection, is a type of security software used to protect a network’s endpoints, such as laptops, desktops, and mobile devices, from cyber threats.
What is the importance of endpoint security to small businesses?
Endpoint security is crucial for small businesses as it provides protection against cyber threats, ensuring the safety of sensitive business data. It also helps in maintaining customer trust by preventing data breaches.
What is an example of endpoint security?
An example of endpoint security is a security software like Avast Business Antivirus that protects a network’s endpoints, such as laptops, desktops, and mobile devices, from cyber threats.
Is endpoint security worth it?
Yes, endpoint security is worth the investment. It provides comprehensive protection against cyber threats, ensuring the safety of your business data and maintaining customer trust.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


