
Introduction
Understanding data security and data privacy is vital for small business managers. Let’s explore these concepts with real-world examples.
Key Terms Defined:
Data Security: Protecting information from unauthorized access.
Data Privacy: Controlling access to personal information
Understanding the Basics
Data security protects information from unauthorized access, while data privacy controls who can access personal information. For example, data security prevents hackers from accessing customer credit card numbers. Data privacy ensures that only authorized employees can view customer addresses.
TLDR – Understanding the difference between data security and data privacy is crucial.
– Data security focuses on safeguarding your data from unauthorized access, employing methods like encryption and multi-factor authentication.
– Data privacy, on the other hand, deals with how your data is legally collected, stored, and shared.
– Both are governed by various regulations like GDPR and CCPA, and non-compliance can result in hefty fines.
– As technology evolves, so do the challenges and solutions in this space, making user education and staying ahead of future trends essential.
Data Security: Protecting Your Business
What is Data Security?
Data security is about safeguarding information from threats, both internal and external. It involves techniques to prevent unauthorized access or data loss, including enforcing authorization, access control, data encryption, and offline backups. For example, a small accounting firm implementing firewalls and encryption tools to block unauthorized access to client financial records.
Data Security Tools for Small Businesses
Utilizing data security tools is essential for protecting sensitive data. These tools include automatic protection on file servers. They also include integrated protection with Data Loss Prevention (DLP) and information discovery solutions.
For example, a local retail store using classification and metadata-based protection to secure customer purchase history. Thus ensuring that only authorized sales representatives can access this information.
Preventing Unauthorized Access
Preventing unauthorized access is a core aspect of data security. It involves implementing access controls, such as passwords and biometric authentication, to ensure that only authorized personnel can view sensitive information. For example, a small medical clinic requiring fingerprint authentication for accessing patient medical records. Thus preventing unauthorized staff from viewing sensitive health information.
Data Loss Prevention
Data loss can be devastating to a small business. Implementing measures like offline backups and employee management policies can prevent scenarios like accidental deletion or malicious attacks.
For example, a local photography studio regularly backing up client photos to an encrypted offline server. Thus, ensuring that even in the event of a ransomware attack the data remains safe and accessible.
Understanding Data Technologies and Databases
Understanding the evolution of data technologies and databases is crucial for implementing proper security measures. Modern companies adopt various models like the one-tier, two-tier, or three-tier model to enhance performance and security.
For example, a small e-commerce business uses a three-tier data model. Thus, introducing a middle-tier server to isolate end-users from the database and control access. This prevents potential SQL vulnerabilities.
Human Factor in Data Security
Surprisingly, human touch is often the biggest threat to data security, causing 90% of data breaches. Training and awareness among employees are vital to minimize this risk.
For example, a small marketing agency conducting regular training sessions on phishing and social engineering tactics. Thus ensuring that employees can recognize and report suspicious emails or requests.
Compliance with Regulations
Compliance with regulations like GDPR, HIPAA, and CCPA is essential for data security. Understanding and adhering to these laws can prevent legal consequences and fines. For example, a local dental practice implements measures to protect patient information. Thus ensuring compliance with HIPAA regulations and preventing potential legal issues.
Data Privacy: Ensuring Compliance
In today’s interconnected world, data privacy has become a critical concern for individuals and organizations alike. Ensuring compliance with various regulations and protecting sensitive information is not just a legal obligation. It is also a prerequisite to data security and trust-building. Here’s a closer look at the importance of data privacy and how it can be achieved.
Complying with Regulatory Requirements
Different industries must comply with specific regulatory requirements. These include the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). In the US, various data privacy laws are taking effect in different states throughout 2023, making compliance a complex task. Businesses must stay updated on these developments and implement measures for preventing unauthorized access to ensure compliance.
Protecting Personal Data
Personal identifiable information (PII) must be safeguarded to prevent identity theft and financial fraud. PII includes such items as such as names, addresses, and credit card numbers. For example, the healthcare sector’s digitization has led to advancements in patient care monitoring but also raised privacy and security concerns. Implementing robust data security tools like encryption and access controls can protect sensitive data and maintain customer trust.
Balancing Security and Privacy
Striking a balance between data security and data privacy is essential. For example, a small law firm must secure client information. At the same time ensuring that only authorized lawyers can access specific case details.
Type of Data and Its Importance
Understanding the type of data collected is vital. For instance, a local bakery must protect customer payment information (data security). At the same time, it must control who can access customer dietary preferences (data privacy).
Addressing Customer Concerns
Customers are increasingly worried about access to data and how it’s used. A Pew Research Center’s survey found that a majority of Americans feel a lack of control over their personal information. Businesses should prioritize data privacy and use tools and technologies to ensure data security. By doing so, businesses can stand out from competitors and demonstrate serious commitment to privacy.
Mitigating Financial Loss and Safeguarding Reputation
A data breach can lead to significant financial loss and severe damage to a business’s reputation. Businesses should take data security seriously and employ data loss prevention strategies. By doing so, organizations can reduce the risk of financial harm and preserve their reputation.
National Security Considerations
Data privacy is also seen as a critical national security matter. The access of foreign companies to American citizens’ data has raised concerns. Thus, causing a push for federal privacy legislation and additional measures to enhance data security.
Data Governance and Compliance Standards
Data governance is an overarching concept that plays a pivotal role in both data security and data privacy. It involves the establishment of policies, procedures, and responsibilities that ensure high data quality and data management within an organization.
Compliance standards such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the U.S. are legal frameworks that dictate how data should be handled. These standards not only protect consumers but also guide businesses in maintaining ethical and secure data practices.
Understanding and adhering to these compliance standards is not just a legal requirement but also a cornerstone in building trust with your customers. Non-compliance can result in hefty fines and a tarnished reputation, making it imperative for businesses to stay updated on these regulations.

Risk Management in Data Security and Privacy
Risk management is an integral part of both data security and data privacy. It involves identifying, assessing, and prioritizing risks related to unauthorized data access, leaks, and breaches. By implementing a robust risk management strategy, businesses can proactively mitigate these risks and protect sensitive information.
Below is a flowchart that outlines the essential steps in a typical risk management process for data security and privacy.
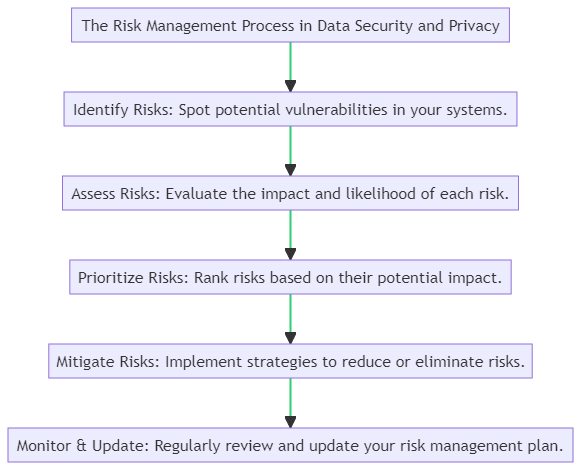
Effective risk management goes beyond installing firewalls and antivirus software. It includes regular risk assessments, employee training, and the use of advanced technologies like Artificial Intelligence and Machine Learning to detect anomalies.
Staying ahead of potential threats requires a multi-layered approach that combines technology, processes, and people. This ensures that both the data and the systems that house them are secure and private.
Encryption Methods and Data Integrity
Encryption methods are the backbone of data security, ensuring that unauthorized parties cannot access sensitive information. There are various types of encryption, such as symmetric and asymmetric, each with its own set of advantages and disadvantages.
Here’s a quick overview of some common encryption methods and how they contribute to data integrity.

- Symmetric Encryption: This method uses the same key for both encryption and decryption. While it’s faster and requires less computational power, the key must be kept secret and shared only with authorized parties.
- Asymmetric Encryption: In this method, different keys are used for encryption and decryption. It’s more secure but requires more computational resources, making it slower for large data sets.
- Hashing: This is a one-way encryption method used primarily for verifying data integrity. It transforms data into a fixed-size string of characters, making it nearly impossible to reverse-engineer.
- Digital Signatures: These are used to verify the authenticity of data. A digital signature assures that the data has not been tampered with and confirms the identity of the sender.
Data integrity, on the other hand, ensures that the data remains accurate and consistent over its lifecycle. This is crucial for both security and privacy, as tampered data can lead to misleading information and potential breaches.
Understanding the different encryption methods and the importance of data integrity can significantly enhance your data security and privacy measures.
Data Breaches and Identity Management
Data breaches are a constant threat in the digital world, often resulting in the unauthorized access of sensitive information. Effective identity management can serve as a first line of defense against such breaches. It involves the use of multi-factor authentication, regular password updates, and stringent access controls.
Below is a diagram outlining the key steps in managing data breaches and maintaining effective identity management.

Here are some key aspects to consider:
- Prevention: Utilize multi-factor authentication and firewalls to prevent unauthorized access.
- Detection: Monitor systems for unusual activity and set up alerts for suspicious actions.
- Response: In case of a breach, isolate affected systems and inform stakeholders immediately.
- Recovery: Restore compromised data and analyze the breach to prevent future incidents.
Ethical Data Handling and Data Storage Solutions
Ethical data handling is a cornerstone of both data security and data privacy. It involves obtaining explicit consent for data collection and minimizing the amount of data gathered to only what is necessary.
Here’s a diagram that succinctly captures the essentials of ethical data handling and various data storage solutions.

When it comes to data storage, there are multiple solutions to consider:
- Ethics: Always obtain explicit consent before collecting data and aim to minimize data collection to what is strictly necessary.
- Cloud Storage: Offers secure, scalable, and cost-effective storage solutions. Ideal for businesses that need flexibility.
- On-Premise Storage: Provides greater control over data but comes with higher costs and maintenance requirements.
- Hybrid Storage: Combines the benefits of cloud and on-premise solutions, offering both flexibility and control.
User Education and Training Programs
User education is often the most overlooked aspect of data security and privacy. However, it’s crucial for reducing human error, which is a common cause of data breaches. Training programs can equip users with the knowledge and skills they need to protect data effectively.
Below is a diagram highlighting the key components of effective user education and training programs.

Here are some key areas to focus on:
- Awareness: Educate users about the risks associated with data handling and the importance of following security protocols.
- Training: Conduct regular workshops and offer online courses to keep users updated on the latest security measures.
- Phishing: Teach users how to recognize and avoid phishing scams that aim to steal sensitive information.
- Best Practices: Encourage password management, secure browsing, and other best practices to enhance data security and privacy.
Legal Implications and Regulatory Compliance
Understanding the legal landscape is crucial for both data security and privacy. Various laws and regulations govern how data should be handled, stored, and protected. Non-compliance can result in hefty fines and legal consequences.
Here’s a diagram that outlines key legal frameworks and potential penalties for non-compliance in data security and privacy.

Here are some key regulations to be aware of:
- GDPR: The General Data Protection Regulation is a European law that sets strict guidelines for data protection.
- CCPA: The California Consumer Privacy Act focuses on the rights of California residents regarding their personal data.
- HIPAA: The Health Insurance Portability and Accountability Act governs the protection of health data in the U.S.
- Penalties: Non-compliance with these regulations can result in fines and other legal consequences.
Practical Tips for Small Business Managers
Small business managers have a crucial role in ensuring both data security and data privacy. Here are actionable tips and recommendations.
Implementing Best Practices
Understanding and implementing best practices in data protection is essential for small businesses.
- Use Secure Channels: Always use secure channels like VPNs for sharing sensitive information to protect sensitive data.
- Access Controls: Implement access controls to prevent unauthorized access to data.
- Regular Audits: Conduct regular audits to ensure data security tools are up to date and effective.
- Action Recommendation: Assess your current data handling practices and implement necessary security measures. Training sessions can be organized to educate employees about the importance of data security.
Employee Training and Awareness
Training employees in data security best practices is vital. It ensures that everyone in the organization understands the importance of protecting personal data.
- Regular Training Sessions: Conduct regular training sessions on data privacy and data security.
- Clear Guidelines: Provide clear guidelines on handling personal identifiable information and other sensitive data.
- Simulated Attacks: Consider simulated cyber-attacks to test employee awareness and responsiveness.
- Action Recommendation: Create a comprehensive training program that includes real-world examples, guidelines on regulatory requirements like the General Data Protection Regulation (GDPR), and strategies for preventing unauthorized access.
Data Loss Prevention
Preventing data loss is a key aspect of data security.
- Backup Solutions: Implement backup solutions to safeguard essential information.
- Monitoring Tools: Use monitoring tools and technologies to detect potential data breaches.
- Action Recommendation: Regularly back up essential data, including customer information, and use monitoring tools to detect and respond to any suspicious activities promptly.
Protecting Personal Data
Protecting personal data, including personal identifiable information, is essential.
- Encryption: Use encryption to protect personal and sensitive information.
- Compliance with Laws: Ensure compliance with laws like the California Consumer Privacy Act (CCPA).
- Action Recommendation: Regularly review and update privacy policies to comply with laws and regulations. Implement encryption and other security measures to protect personal data.
Future Trends in Data Security and Privacy
The landscape of data security and privacy is ever-evolving, influenced by technological advancements and changing regulations. Staying ahead of these trends can provide a competitive edge and better prepare you for challenges.
Here are some future trends to watch:
- AI and Machine Learning: Predictive analytics and automated systems will play a significant role in identifying vulnerabilities and threats.
- Blockchain: This technology offers enhanced security features, making it a promising solution for secure transactions.
- IoT: The Internet of Things brings increased vulnerabilities due to the sheer number of connected devices.
- Legislation: Expect evolving laws and regulations that will impact how data is handled and protected.
Conclusion and Key Takeaways
Data security and data privacy are distinct but interconnected concepts. Small business managers must understand these differences to mitigate data breaches and ensure comprehensive data protection. This article has covered various facets, from encryption methods to legal implications, aiming to provide a comprehensive guide.
Here are the key takeaways:
- Importance: Data security and privacy are crucial for protecting sensitive information and complying with laws.
- Best Practices: Implement multi-factor authentication, regular training, and adhere to legal frameworks.
- Future: Stay updated on emerging technologies and evolving regulations to remain competitive and compliant.
Real-world examples like securing customer payment information or controlling access to patient records highlight the importance of these concepts. Assess your current practices and take proactive steps to protect against potential threats. Your business’s reputation and legal standing depend on it.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!


