TL;DR: This comprehensive guide explores the intricacies of firewalls, from their foundational principles to the cutting-edge endpoint firewalls of 2025. Delve into the evolution of firewall technologies, understand the pivotal differences between endpoint and cloud-based firewalls, and arm yourself with knowledge to fortify your business against modern cyber threats.

Introduction
In the rapidly evolving digital landscape of 2023, safeguarding business assets from cyber threats has never been more crucial. As small businesses increasingly rely on technology, understanding the tools that protect their networks becomes paramount. Enter the world of firewalls—a frontline defense in cybersecurity. But what exactly is a firewall, and why is there a growing buzz around “endpoint firewalls”?
This comprehensive guide delves into the essentials of firewalls, their transformative journey, and the rising prominence of endpoint firewalls. Whether you’re a small business manager or an IT professional, this article will equip you with the knowledge you need in today’s cyber-centric world.
| Section | Summary |
|---|---|
| Introduction | Explores the importance of firewalls in 2023, emphasizing the rise of endpoint firewalls and their significance in the evolving digital landscape. |
| Introduction to Firewalls | Describes what a firewall is, its role as a gatekeeper for network traffic, and the benefits of using firewalls, including network integrity protection and unauthorized access blocking. |
| How Firewalls Work | Explains the mechanisms of firewalls, such as packet filtering and application layer filtering. |
| Types of Firewalls | Breaks down various firewall types, including network firewalls (hardware vs. software), proxy firewalls, stateful inspection firewalls, and next-generation firewalls. |
| Endpoint Security vs. Firewall | Distinguishes between endpoint security and firewalls, highlighting the scope, protection layer, and functionality differences. |
| Firewall Basics | Covers the foundational principles of firewalls, their role in monitoring network traffic, and their protection mechanisms and features. |
| Understanding Endpoint Firewall | Defines endpoint firewall, its importance in 2023, and its evolution from traditional firewalls. |
| Endpoint vs. Cloud-Based Firewall | Differentiates between endpoint and cloud-based firewalls, discussing the advantages and disadvantages of cloud-based firewalls. |
| Why Endpoint Firewall is Crucial for Small Businesses | Emphasizes the importance of endpoint firewalls for small businesses, highlighting the rise in cyber threats in 2023 and the benefits of implementing endpoint firewalls. |
Three Thought-Provoking Questions/Insights
- Endpoint vs. Traditional Firewalls: With the rise of remote work and BYOD policies, how have endpoint firewalls evolved to address the unique challenges posed by these trends?
- The Role of Machine Learning in Firewalls: How are modern endpoint firewalls leveraging machine learning for adaptive threat detection and predictive analysis?
- Small Business Cybersecurity: Given that 68% of small businesses have experienced a cyberattack in the past year, how can endpoint firewalls serve as a crucial defense mechanism for these businesses?
Introduction to Firewalls: The First Line of Defense
What is a Firewall?
A firewall is a cybersecurity system designed to act as a barrier between a trusted network (like a company’s internal network) and untrusted networks (such as the internet). Its primary function is to monitor, filter, and control incoming and outgoing network traffic based on predetermined security policies.
Think of a firewall as a virtual gatekeeper, allowing or denying data packets to pass through based on specific criteria. This ensures that malicious data, such as viruses or hacking attempts, is blocked, while legitimate traffic is allowed. Firewalls can be implemented in both hardware and software forms, or a combination of both, offering layers of protection against potential cyber threats.
Benefits of Using Firewalls

(click to enlarge)
Protecting Network Integrity
A firewall ensures that the integrity of a network remains uncompromised by filtering out malicious data packets and unauthorized requests. For example, consider a local bakery that has an online ordering system. A firewall can prevent a cyber attacker from tampering with the system, ensuring that customers’ orders and payment details remain secure.
Blocking Unauthorized Access
Firewalls act as gatekeepers, denying unauthorized users and potentially harmful software from accessing the network. Consider the case of a small accounting firm stores sensitive financial data of its clients. With a firewall in place, attempts by hackers to gain unauthorized access to this data can be thwarted, keeping the information confidential.
Monitoring and Reporting Suspicious Activities
Firewalls continuously monitor network traffic, identifying and reporting any suspicious patterns or activities that might indicate a potential threat. As an example, consider an e-commerce website might experience a sudden surge in traffic from a specific location, indicating a potential DDoS attack. The firewall can detect this anomaly and alert the IT team, allowing them to take immediate action.
By understanding and leveraging these benefits, businesses can ensure a robust defense against a myriad of cyber threats, safeguarding their assets and reputation in the digital realm.
How Firewalls Work
Firewalls operate using a set of defined rules and mechanisms to scrutinize and control network traffic. Here’s a closer look at how they function.
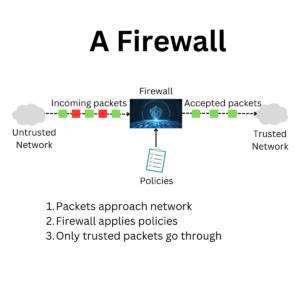
(click to enlarge)
Packet Filtering and Inspection
Packet filtering is one of the primary methods firewalls use to manage network traffic. They inspect data packets to determine whether they should be allowed or denied based on predefined rules.
Here is an example of the process of packet filtering and inspection:
- Data Transmission: A user sends or requests data over the network.
- Packet Analysis: The firewall examines the data packet’s source, destination, and other header information.
- Rule Matching: The firewall compares the packet details with its set of predefined rules.
- Decision: Based on the rule match, the firewall either allows the packet to pass through or blocks it.
- Notification (Optional): If a packet is blocked, the firewall might log the event or notify the network administrator.
Application Layer Filtering
This method focuses on filtering traffic based on the specific application or service it’s associated with, rather than just the packet details.
Here is an example of the process of Application Layer Filtering:
- Request Initiation: A user tries to access a specific application or service online.
- Application Identification: The firewall identifies the application or service being accessed.
- Policy Check: The firewall checks its rules to see if access to the application or service is permitted.
- Access Decision: Based on the policy, the firewall either grants or denies access to the application.
- Logging (Optional): The firewall may log the event, especially if access is denied, for future analysis or audit purposes.
By understanding these mechanisms, businesses can configure their firewalls more effectively, ensuring optimal protection against potential threats.
Types of Firewalls
As cyber threats have evolved, so have the types of firewalls designed to counter them. Each type has its unique features and is suited for different environments and threats. Here’s a breakdown:
Network Firewalls (Hardware vs. Software)
Network firewalls operate at the perimeter of a network, monitoring traffic between the internal network and external sources.
- Hardware Firewalls: These are standalone devices positioned between a network and its connection to the internet. They provide a physical barrier, often accompanied by their own operating system.
- Usage: Ideal for businesses that require high-performance and reliability.
- Protection Against: Unauthorized external access, DDoS attacks, and malware.
- Software Firewalls: Installed directly on servers or individual devices, they filter incoming and outgoing traffic on that specific device.
- Usage: Suitable for individual devices or smaller networks.
- Protection Against: Malware, spyware, and unauthorized application access.
Proxy Firewalls
Proxy firewalls act as intermediaries, processing requests from users by forwarding them to the destination server. They prevent direct contact between the user and the server.
- Usage: Commonly used in corporate environments to control and monitor web usage.
- Protection Against: Web-based threats like malicious websites, web application attacks, and content-based threats.
Stateful Inspection Firewalls
Also known as dynamic packet filtering, these firewalls monitor active connections and make decisions based on the context of the traffic.
- Usage: Widely used in larger networks and enterprises.
- Protection Against: Unauthorized access, port scanning, and application layer attacks by maintaining a table of active connections.
Next-Generation Firewalls (NGFWs)
NGFWs combine traditional firewall capabilities with advanced functionalities like application awareness and deep packet inspection.
- Usage: Suitable for environments that require advanced security features and granular control.
- Protection Against: Zero-day threats, advanced persistent threats (APTs), and application layer attacks by integrating intrusion prevention systems and user identity management.
By understanding the different types of firewalls and their functionalities, businesses can make informed decisions on the best fit for their specific needs, ensuring robust protection against a wide array of cyber threats.
Endpoint Security vs. Firewall: Clearing the Confusion
Endpoint Security Explained
As we navigate the intricate landscape of cybersecurity, terms like “endpoint security” and “firewall” often surface, sometimes used interchangeably. However, while they both play pivotal roles in safeguarding digital assets, they serve distinct functions. Let’s first delve into the realm of endpoint security.
Components of Endpoint Security:
Endpoint security is a holistic approach to protect individual network endpoints—devices like computers, smartphones, and tablets—from potential threats. Its components include:
- Antivirus and Antimalware Software: These tools scan devices for known threats, neutralizing them before they can cause harm.
- Endpoint Encryption: Encrypts data stored on endpoints, ensuring that even if a device is lost or stolen, its data remains inaccessible.
- Host Intrusion Prevention Systems (HIPS): Monitors and blocks malicious activities by analyzing system behavior and configurations.
- Application Control: Ensures only approved applications run on the device, preventing potentially harmful software from executing.
Importance of Endpoint Security:
- Device-Level Protection: With the proliferation of devices accessing business networks, endpoint security ensures each device is fortified against threats.
- Adaptability: Endpoint security solutions can adapt to the unique requirements of each device, offering tailored protection.
- Centralized Management: Allows IT teams to manage security policies and monitor threats across all endpoints from a single dashboard.
How Does It Differ from a Firewall?
While both endpoint security and firewalls aim to protect against cyber threats, their approach and focus differ:
- Scope: While endpoint security focuses on individual devices, firewalls typically protect network perimeters, monitoring and controlling incoming and outgoing traffic.
- Protection Layer: Endpoint security operates on the device level, ensuring threats are neutralized on the device itself. In contrast, firewalls act as barriers between internal networks and potential external threats.
- Functionality: Endpoint security encompasses a range of tools, from antivirus to encryption, tailored for device protection. Firewalls, on the other hand, primarily filter and monitor network traffic based on predefined rules.
Understanding the nuances between endpoint security and firewalls is crucial for businesses to deploy the right tools and strategies, ensuring a multi-layered defense against cyber threats.
Firewall Basics
While we’ve delved into the intricacies of endpoint security, it’s equally vital to understand the foundational principles of firewalls. Often visualized as the first line of defense in a network, firewalls have been instrumental in shaping the cybersecurity landscape. Let’s explore the basics of firewalls and their pivotal role in network protection.
Role in Monitoring Network Traffic:
At its core, a firewall acts as a gatekeeper, monitoring and controlling the flow of data between an internal network and external sources, such as the internet. Its primary function is to:
- Filter Traffic: Based on predefined rules, firewalls determine which traffic can enter or leave the network.
- Block Unauthorized Access: Prevent external entities from accessing the internal network without proper authorization.
- Log Activities: Maintain a record of all network traffic, helping administrators identify patterns and potential threats.
Protection Mechanisms and Features:
Firewalls come equipped with a range of mechanisms and features designed to bolster network security:
- Packet Filtering: Examines data packets to determine whether they align with the set rules, allowing or blocking them based on source, destination, and type.
- Stateful Inspection: Monitors active connections and makes decisions based on the context of the traffic, rather than just individual packets.
- Proxy Services: Acts as an intermediary, processing requests on behalf of users, ensuring direct contact between the user and the server is avoided.
- Network Address Translation (NAT): Masks user IP addresses, making it challenging for external entities to pinpoint individual devices within the network.
- Intrusion Detection and Prevention Systems (IDPS): Identifies and counters potential threats in real-time, ensuring malicious activities are halted before they can infiltrate the network.
Firewalls, with their multifaceted protection mechanisms, have long been the cornerstone of network security. By understanding their foundational principles and features, businesses can better appreciate their role in the broader cybersecurity ecosystem.
Understanding Endpoint Firewall
In the vast realm of cybersecurity, the term “endpoint firewall” has gained significant traction, especially in recent years. But what exactly does it entail, and why has it become so pivotal in today’s digital landscape?
Definition of Endpoint Firewall
An endpoint firewall is a security solution specifically designed to protect individual endpoints—like desktops, laptops, smartphones, and other devices—within a network. Unlike traditional firewalls that shield the network’s perimeter, endpoint firewalls focus on safeguarding each device from potential threats, ensuring that malicious activities are curtailed right at the source.
Importance in 2025
With the proliferation of remote work, BYOD (Bring Your Own Device) policies, and the increasing sophistication of cyber threats, the traditional network perimeter has become more porous. This shift has amplified the need for security at the device level. Endpoint firewalls address this by:
- Granular Protection: Offering device-specific protection, ensuring that threats are detected and neutralized on individual devices.
- Flexibility: Adapting to diverse device types and operating systems, making them suitable for heterogeneous network environments.
- Mitigating Advanced Threats: Countering modern threats like zero-day exploits and ransomware that can bypass traditional firewalls.
Evolution from Traditional Firewalls to Endpoint Firewalls
The journey from traditional to endpoint firewalls is a testament to the ever-evolving nature of cybersecurity. Here’s a brief overview:
- Traditional Firewalls: Initially, firewalls were designed to protect network perimeters. They acted as barriers between trusted internal networks and untrusted external sources, filtering traffic based on predefined rules.
- Rise of Mobile and IoT: As mobile devices and Internet of Things (IoT) gadgets became ubiquitous, the clear boundary of network perimeters began to blur. This introduced new vulnerabilities as these devices often accessed the network from outside the traditional perimeter.
- Advent of Endpoint Firewalls: Recognizing the need to protect individual devices irrespective of their location, endpoint firewalls emerged. They brought the concept of “security at the source,” ensuring that each device had its own protective shield against potential threats.
In a world where cyber threats are not confined to network boundaries, endpoint firewalls have become the vanguard, ensuring that every device, every endpoint, remains fortified against malicious activities.
- Definition and Importance in 2025
- Evolution from Traditional Firewalls to Endpoint Firewalls
Endpoint vs. Cloud-Based Firewall: The Key Differences
In the dynamic world of cybersecurity, the distinctions between different protective measures can often blur. As businesses grapple with the best strategies to safeguard their digital assets, understanding the nuances between endpoint and cloud-based firewalls becomes paramount. This section delves into the core differences between these two firewall types, shedding light on their unique features, advantages, and ideal use cases.
What is a Cloud-Based Firewall?
A cloud-based firewall, often referred to as Firewall-as-a-Service (FaaS), is a security solution hosted in the cloud rather than on-premises. It filters and monitors traffic that flows to and from cloud-based applications, ensuring that malicious data is blocked while legitimate traffic is allowed.
Advantages of Cloud-Based Firewalls:
- Scalability: Being cloud-native, these firewalls can easily scale up or down based on the traffic volume, ensuring efficient resource utilization.
- Cost-Effective: Businesses can avoid the capital expenditure of hardware and reduce maintenance costs, as updates and patches are managed by the service provider.
- Remote Access Security: With the rise of remote work, cloud-based firewalls offer protection for distributed workforces accessing resources from various locations.
- Always Updated: Cloud-based solutions are continuously updated to counter the latest threats, ensuring businesses are always protected against emerging vulnerabilities.
- Centralized Management: Businesses can manage security policies, monitor threats, and generate reports from a centralized dashboard, simplifying administration.
Disadvantages of Cloud-Based Firewalls:
- Latency Issues: Routing traffic through the cloud can introduce latency, potentially affecting application performance.
- Data Privacy Concerns: Storing logs and data in the cloud might raise data sovereignty and privacy concerns for some businesses.
- Reliance on Service Providers: Businesses are dependent on the service provider’s infrastructure. Any downtime or issues on the provider’s end can impact the firewall’s functionality.
- Potential Cost Overruns: While cloud-based firewalls can be cost-effective, unexpected spikes in traffic or additional features can lead to unforeseen expenses.
By understanding the nuances of cloud-based firewalls, businesses can make informed decisions on whether this solution aligns with their security needs and operational requirements.
Diving Deep into the Endpoint Firewall
Endpoint firewalls have emerged as a critical component in the cybersecurity toolkit, especially as the traditional network perimeter becomes increasingly fragmented. By focusing on individual devices, endpoint firewalls offer a more granular approach to security. Let’s explore this in more depth through real-world scenarios and weigh its pros and cons.
Real-World Scenarios:
- Remote Work: Imagine a marketing manager working from a café. While accessing company data, her laptop is exposed to potential threats from the public Wi-Fi. An endpoint firewall on her device ensures that malicious traffic is blocked, even outside the company’s primary network.
- BYOD Policies: A tech startup encourages employees to bring their own devices. While this boosts productivity, it introduces varied devices with different security postures. Endpoint firewalls ensure each device, whether a personal smartphone or tablet, is secured when accessing company resources.
- Traveling Executives: A CEO travels internationally for business meetings. Accessing company data from various global locations exposes his device to different threat landscapes. An endpoint firewall offers consistent protection, irrespective of geographical location.
Advantages of Endpoint Firewalls:
- Device-Level Protection: Offers security at the source, ensuring threats are neutralized on individual devices.
- Flexibility: Adapts to diverse device types and operating systems, making it suitable for varied network environments.
- Protection Beyond Perimeters: Safeguards devices even when they are outside the traditional network boundaries, such as during remote work.
- Real-time Threat Detection: With continuous monitoring, endpoint firewalls can detect and counter threats in real-time.
Disadvantages of Endpoint Firewalls:
- Management Complexity: With firewalls on every device, managing and updating policies can become complex, especially for large organizations.
- Potential Performance Impact: Running security checks on devices can sometimes impact their performance, especially if resources are limited.
- Reliance on End-Users: The effectiveness of endpoint firewalls can be compromised if end-users disable them or fail to update them regularly.
Endpoint firewalls represent a shift in how we approach cybersecurity, focusing on individual devices as potential entry points for threats. By understanding their strengths and limitations, businesses can deploy them effectively, ensuring robust protection in today’s diverse digital landscape.
Why Endpoint Firewall is Crucial for Small Businesses
In the digital age, businesses of all sizes are grappling with an ever-evolving threat landscape. For small businesses, the stakes are particularly high. Limited resources and a lack of dedicated cybersecurity teams often make them prime targets for cybercriminals. As we navigate through 2023, the surge in cyber threats has become palpable. Recent statistics reveal that:
- 68% of small businesses have experienced a cyberattack in the past year.
- Ransomware attacks have seen a 40% increase, with small businesses often being the primary victims.
- Data breaches have resulted in an average financial loss of $150,000 for affected small businesses.
Given these alarming figures, it’s evident that traditional security measures are no longer sufficient. This is where endpoint firewalls come into play. By focusing on individual devices as potential entry points for threats, endpoint firewalls offer a more granular and proactive approach to security. As we delve deeper into this section, we’ll explore the myriad benefits of implementing endpoint firewalls and why they are fast becoming an indispensable tool for small businesses in the fight against cyber threats.
Benefits of Implementing an Endpoint Firewall
In an era where cyber threats are becoming more sophisticated and targeted, the need for robust security solutions has never been more pressing. Endpoint firewalls, with their device-centric approach, offer a range of benefits that can significantly bolster a business’s defense mechanisms. Let’s delve into some of the key advantages of implementing endpoint firewalls.
Protection from Advanced Threats
Endpoint firewalls are designed to counter modern cyber threats that often bypass traditional security measures. These firewalls:
- Detect Zero-Day Exploits: With real-time monitoring, endpoint firewalls can identify and block threats that exploit previously unknown vulnerabilities.
- Counter Advanced Persistent Threats (APTs): These are prolonged and targeted cyberattacks. Endpoint firewalls can detect unusual behavior patterns, ensuring that such threats are neutralized before they can cause significant damage.
- Prevent Ransomware Attacks: By monitoring file behaviors and access patterns, endpoint firewalls can detect ransomware activities and halt them in their tracks.
Ensuring Business Continuity
A cyber breach can disrupt business operations, leading to financial losses and reputational damage. Implementing endpoint firewalls ensures:
- Uptime and Availability: By preventing cyberattacks, businesses can ensure that their services remain available to customers, maintaining trust and loyalty.
- Data Integrity: Endpoint firewalls protect against data tampering threats, ensuring that business data remains accurate and reliable.
- Quick Recovery: In the event of a security incident, endpoint firewalls can help businesses quickly identify the threat source, allowing for faster recovery and minimal downtime.
Incorporating endpoint firewalls into a business’s cybersecurity strategy not only fortifies its defenses against advanced threats but also ensures that operations run smoothly, even in the face of potential cyber challenges.
Components of a Robust Endpoint Firewall
In the intricate world of cybersecurity, the strength of a defense system is often determined by its individual components. An endpoint firewall, while powerful in its core function, is made up of several integral parts that work in tandem to provide comprehensive protection. As cyber threats become more sophisticated, it’s essential for endpoint firewalls to be equipped with advanced features that can counteract these challenges. Let’s break down the key components that make up a robust endpoint firewall:
Protection Mechanisms and Machine Learning Components
Modern endpoint firewalls go beyond basic rule-based filtering. They incorporate advanced protection mechanisms powered by machine learning. These components:
- Adaptive Threat Detection: Machine learning algorithms analyze network traffic patterns to identify and block unusual or malicious activities in real-time.
- Predictive Analysis: By studying past threats and understanding their evolution, machine learning components can predict and counter new variants of known threats.
Data Access Controls and Behavioral Analysis
Ensuring that only authorized individuals access sensitive data is paramount. Endpoint firewalls achieve this through:
- Role-Based Access Controls (RBAC): Define user roles and permissions, ensuring that individuals can only access data relevant to their role.
- Behavioral Analysis: Monitor user behavior to detect anomalies. For instance, if an employee suddenly downloads large amounts of data, the firewall can flag this as suspicious.
Integration with Other Security Solutions
A holistic security approach often involves multiple tools and solutions. A robust endpoint firewall:
- Seamless Integration: Can easily integrate with other security solutions like Intrusion Detection Systems (IDS) or Security Information and Event Management (SIEM) tools.
- Unified Dashboard: Provides a centralized platform where administrators can view threats detected by the firewall and other integrated solutions, streamlining the response process.
A truly effective endpoint firewall is more than just a barrier; it’s a multi-faceted tool equipped with advanced features designed to adapt and counter the ever-evolving world of cyber threats.
Best Practices for Implementing Endpoint Firewall
Implementing an endpoint firewall is a critical step in fortifying your business’s cybersecurity posture. However, the mere act of deployment isn’t enough. To truly harness its potential and ensure optimal protection, it’s essential to follow best practices from selection to continuous monitoring. Here’s a guide to help you navigate this process effectively:
Choosing the Right Solution for Your Business:
- Assess Your Needs: Before diving into the myriad of options available, take a moment to assess your business’s specific needs. Consider factors like the number of devices, types of devices, and the nature of data you handle.
- Research Vendors: Not all endpoint firewall solutions are created equal. Research various vendors, read reviews, and perhaps even consider a trial period to gauge the solution’s effectiveness.
- Scalability: As your business grows, so will your security needs. Opt for a solution that can scale with you, ensuring you’re always adequately protected.
Tips for Seamless Integration and Configuration:
- Centralized Management: Opt for solutions that offer a centralized dashboard. This allows for easier configuration, monitoring, and management of policies across all devices.
- Role-Based Configurations: Tailor firewall rules based on user roles. For instance, an IT administrator might need broader access compared to a sales executive.
- Test Before Full Deployment: Before rolling out the firewall to all devices, test it on a smaller group. This helps identify potential issues and ensures a smoother deployment process.
Ensuring Continuous Monitoring and Updates:
- Stay Updated: Cyber threats are ever-evolving. Ensure your endpoint firewall is always updated to the latest version to counter new threats effectively.
- Regular Audits: Periodically review and audit firewall logs. This not only helps in identifying potential threats but also in refining firewall rules for better protection.
- Educate End-Users: A firewall is only as effective as its weakest link. Regularly educate end-users about the importance of not disabling or tampering with the firewall settings.
Implementing an endpoint firewall is a significant investment in your business’s cybersecurity. By following these best practices, you ensure that this investment yields optimal returns, safeguarding your business from the myriad of cyber threats lurking in the digital shadows.
Conclusion
In the ever-evolving landscape of cybersecurity, understanding the nuances of protection tools like endpoint firewalls is paramount. As we’ve journeyed through this guide, we’ve unpacked the foundational principles of firewalls, delved deep into the world of endpoint security, and highlighted the critical differences between the two. With the rise in sophisticated cyber threats in 2023, businesses, especially small ones, can no longer afford to overlook the importance of robust security measures.
Endpoint firewalls, with their device-centric approach, offer a granular level of protection, ensuring that each device—be it in the office or a remote location—is fortified against potential threats. By integrating them into your security architecture, you not only bolster your defenses but also ensure business continuity, even in the face of advanced cyberattacks.
As you chart the future of your business’s cybersecurity strategy, consider the pivotal role endpoint firewalls can play. Don’t wait for a breach to underscore their importance. Act now, invest in a robust endpoint firewall solution, and fortify your business against the cyber challenges of tomorrow.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!