Understanding DDoS Attacks: A 2024 Guide for Small Business Cybersecurity
DDoS attacks are surging, posing a real threat to businesses big and small. In this guide, you’ll learn how to defend against a DDoS attack effectively. We’ll delve into types, tactics, and tools that fortify your network security. So, let’s arm you with the knowledge you need to outsmart cybercriminals.
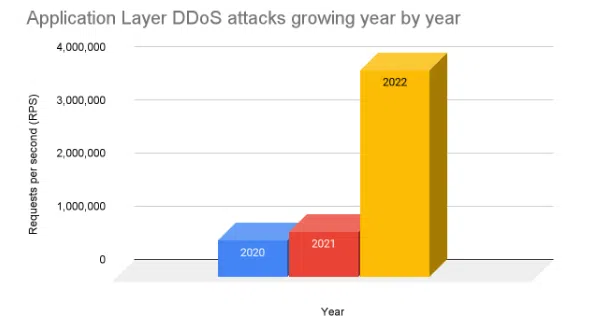
(source: https://www.imperva.com/blog/imperva-releases-its-global-ddos-threat-landscape-report-2023/)
Key Takeaways
- Understand the Enemy: Knowing the types of DDoS attacks and how they operate is the first step in defense.
- Equip Yourself: Utilize firewalls, Intrusion Detection Systems, and other tools to fortify your network.
- Plan and Prepare: A well-thought-out strategy is your best defense against DDoS attacks.
- Monitor and Adapt: The cybersecurity landscape is ever-changing. Continuous monitoring and adaptation are crucial.

(click image to expand)
Understanding DDoS Attacks: Know Your Enemy
DDoS, or Distributed Denial of Service attacks, are malicious attempts to make a targeted server, service, or network unavailable. They flood the target with excessive internet traffic, causing financial losses and damaging brand reputation.
The OSI Model: A Framework for Understanding
The OSI (Open Systems Interconnection) Model is a comprehensive framework for understanding where DDoS attacks can occur. It has seven layers, each with unique functions and vulnerabilities. Knowing these layers aids in crafting an effective defense strategy.
Physical Layer Attacks (Layer 1)
Attacks at the Physical Layer target hardware components like routers, switches, and network cables. Methods include signal jamming and physical tampering to disrupt network signals.
Data Link Layer Attacks (Layer 2)
Here, MAC flooding and ARP poisoning are prevalent. Attackers flood the network switch with fake MAC addresses, overwhelming its memory and causing system failure.
Network Layer Attacks (Layer 3)
This layer is vulnerable to Ping of Death and Smurf Attacks. These exploit ICMP (Internet Control Message Protocol) vulnerabilities, sending malformed or oversized packets that freeze or crash the target system.
Transport Layer Attacks (Layer 4)
SYN Flood and UDP Reflection attacks exploit the TCP handshake process. They send multiple SYN requests but never complete the handshake, tying up server resources and preventing legitimate requests.
Session Layer Attacks (Layer 5)
Session hijacking and token kidnapping can occur here. Attackers take control of a user session to gain unauthorized access to protected network areas or applications.
Presentation Layer Attacks (Layer 6)
SSL Stripping and MIME Confusion attacks focus on data encryption and decryption. These can allow attackers to intercept sensitive information.
Application Layer Attacks (Layer 7)
HTTP Flood and Slowloris attacks target web applications. They overwhelm the application with HTTP requests, making it slow or entirely inaccessible to legitimate users.
Understanding these layers and their vulnerabilities equips you to craft a robust DDoS defense strategy. This is crucial for small businesses with limited cybersecurity resources but still at risk of DDoS attacks.
Why No Business is Too Small to be Targeted
Contrary to popular belief, small businesses are not immune to DDoS attacks. In fact, they often become easy targets for several reasons.
Limited Cybersecurity Resources
Small businesses often operate on tight budgets, limiting their investment in cybersecurity measures. This makes them attractive targets for attackers who see them as low-hanging fruit.
Lack of Awareness
Many small business owners lack cybersecurity awareness. They may not even know what a DDoS attack is, let alone how to defend against one. This lack of knowledge increases their vulnerability.
No Dedicated IT Team
Unlike larger corporations, small businesses usually don’t have a dedicated IT team to monitor and defend against cyber threats, including DDoS attacks.
Business Continuity Risks
A DDoS attack can halt business operations. For small businesses, even a short period of downtime can result in significant financial losses and damage to customer trust.
Data as a Target
Small businesses often hold valuable data but lack the robust security measures to protect it. This makes them prime targets for attackers seeking to steal or ransom data.
Third-Party Risks
Small businesses often rely on third-party services for various operations. If one of these services is compromised, it can indirectly affect the business.
Understanding these vulnerabilities is the first step in crafting a robust defense strategy against DDoS attacks. Small businesses may not have extensive cybersecurity resources, but awareness and strategic planning can go a long way in mitigating risks.
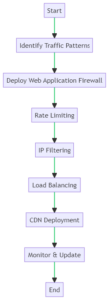
(click image to expand)
Seven Proven Tactics to Mitigate DDoS Attacks
Mitigating DDoS attacks is crucial for any business, small or large. The flowchart above outlines a strategic approach to DDoS defense. Let’s delve into each tactic in detail.
Identify Traffic Patterns
The first step, as shown in the flowchart, is to identify normal traffic patterns. Knowing what’s typical allows you to spot anomalies, which could be indicative of a DDoS attack.
Increase Bandwidth
While not a standalone solution, increasing bandwidth can offer some level of protection against volume-based attacks. It’s like widening a highway to accommodate more traffic.
Deploy Web Application Firewall (WAF)
A WAF sits between your website and incoming traffic, filtering out malicious requests. This is the second step in our flowchart and a crucial component of any DDoS mitigation strategy.
Leverage CDN Solutions
Content Delivery Networks (CDNs) distribute web content across multiple locations, reducing server load. They can absorb excess traffic during a DDoS attack, making them invaluable.
Rate Limiting
Rate limiting controls the number of requests a server will accept from a single IP address. It’s the third step in our flowchart and can effectively mitigate certain types of DDoS attacks.
IP Filtering
This tactic involves blocking IP addresses known to be malicious. It’s the fourth step in our flowchart and can be particularly effective against smaller-scale attacks.
Load Balancing
Load balancers distribute incoming traffic across multiple servers, preventing any single server from becoming overwhelmed. This is the fifth step in our flowchart.
Implement Server-Level DDoS Protection
Server-level protection can identify and mitigate DDoS attacks before they reach your network. This adds an extra layer of security.
CDN Deployment
As the sixth step in our flowchart, deploying a CDN can further distribute traffic, making DDoS attacks less effective.
Monitor and Update
The final step in our flowchart is continuous monitoring and updating of your DDoS mitigation strategies. Cyber threats evolve, and so should your defenses.
By implementing these seven tactics, along with increasing bandwidth, leveraging CDN solutions, and server-level protection, you’ll be well-equipped to defend against DDoS attacks.
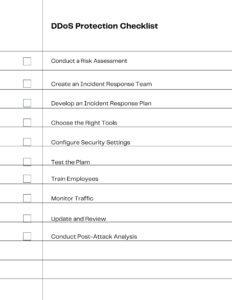
(click image to expand)
Planning for DDoS Attacks: A Step-by-Step Guide
Preparing for a DDoS attack is not just about implementing the right technology; it’s about crafting a comprehensive strategy. Here’s a step-by-step guide to help you plan effectively.
Step 1: Conduct a Risk Assessment
Begin by assessing your network’s vulnerabilities. Identify critical assets and understand the potential impact of a DDoS attack on your business operations.
Step 2: Create an Incident Response Team
Assemble a team of experts responsible for managing DDoS incidents. Ensure they are trained and aware of their roles during an attack.
Step 3: Develop an Incident Response Plan
Draft a detailed plan outlining the steps to take during a DDoS attack. This should include communication protocols, emergency contacts, and recovery procedures.
Step 4: Choose the Right Tools
Invest in DDoS mitigation tools that align with your needs. This could include a Web Application Firewall (WAF), CDN solutions, and server-level DDoS protection.
Step 5: Configure Security Settings
Fine-tune the settings of your security tools. For example, set up rate limiting and IP filtering to minimize the impact of an attack.
Step 6: Test the Plan
Conduct simulated DDoS attacks to test your incident response plan. Make necessary adjustments based on the outcomes.
Step 7: Train Employees
Educate your staff about DDoS attacks and how to recognize signs of an attack. This can be crucial in early detection.
Step 8: Monitor Traffic
Constantly monitor network traffic for unusual patterns. Use analytics tools to set up alerts for suspicious activity.
Step 9: Update and Review
Regularly update your incident response plan and security tools. Cyber threats evolve, and your defenses should too.
Step 10: Conduct Post-Attack Analysis
After an attack, analyze what went well and what didn’t. Use this information to refine your plan and better prepare for future attacks.
By following this step-by-step guide, you’ll be better prepared to defend against DDoS attacks, minimizing both risks and potential damage.
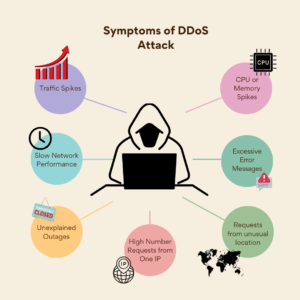
How to Recognize a DDoS Attack: Signs and Symptoms
(click image to expand)
Recognizing a DDoS attack early is crucial for effective mitigation. Here are key indicators to help you identify abnormal traffic patterns and other signs of an attack.
Sudden Traffic Spikes
A sudden surge in traffic is often the first sign of a DDoS attack. Monitoring tools can alert you to these spikes, allowing for quick action.
Slow Network Performance
If your network or website is unusually slow, it could be under a DDoS attack. Sluggish performance is often a red flag.
Unexplained Outages
Random outages or frequent server reboots can indicate a DDoS attack. These disruptions can severely impact business operations.
High Number of Requests from a Single IP
Multiple requests from a single IP address in a short period can be a sign of a targeted attack. Rate limiting can help mitigate this.
Unusual Geographic Traffic Sources
If you notice traffic from regions where you don’t usually have customers, be cautious. This could be a sign of a DDoS attack.
Error Messages
Excessive 503 and 504 error messages can indicate server overload, often a symptom of a DDoS attack.
CPU and Memory Spikes
Unusual spikes in CPU and memory usage can signal an ongoing attack. Monitoring these metrics can aid in early detection.
By understanding these signs and symptoms, you can act swiftly to mitigate the impact of a DDoS attack. Early recognition is key to minimizing damage and downtime.
Tools and Technologies: Equip Yourself
Defending against DDoS attacks requires a multi-layered approach. Here’s an expanded look at the tools and technologies you should consider.
Web Application Firewall (WAF)
A WAF not only filters out malicious traffic but also provides detailed analytics. It can identify and block specific types of attacks, such as SQL injection and cross-site scripting, adding an extra layer of security.
Content Delivery Network (CDN)
Beyond distributing web content, CDNs also offer DDoS protection features. They can detect and mitigate attacks close to the source, reducing the load on your origin server.
Rate Limiting Tools
Rate limiting is more than just controlling traffic. Advanced tools can differentiate between human and bot traffic, allowing you to set different rate limits for each, thus enhancing protection.
Load Balancers
Modern load balancers do more than just distribute traffic. They can also perform SSL termination and application-level security, making them a versatile tool in your DDoS defense arsenal.
DDoS Protection Services
Specialized services like Cloudflare and Akamai offer machine learning algorithms that adapt to new attack methods. They provide real-time analytics and instant alerts, allowing for quick response.
Intrusion Detection Systems (IDS)
An IDS not only monitors traffic but also analyzes it against a database of known attack vectors. It can automatically block or flag suspicious activity, providing real-time defense.
Anti-DDoS Software
Software solutions like FortGuard and D-Guard offer features like traffic scrubbing, where malicious traffic is separated from legitimate traffic, ensuring uninterrupted service.
VPN Services
Using a VPN can add an extra layer of security by encrypting your data. This makes it harder for attackers to exploit vulnerabilities in your network.
Analytics Tools
Advanced analytics tools can set up custom alerts based on specific traffic patterns or behaviors, allowing for proactive defense measures.
Server-Level Protection
Server-level DDoS protection often includes features like IP reputation lists and rate-based or behavior-based blocking, offering a comprehensive defense strategy.
By diving deeper into these tools and technologies, you’ll gain a nuanced understanding of how to build a robust DDoS defense strategy.
| DDoS Protection Tool | Key Features |
|---|---|
| Web Application Firewall (WAF) | Filtering, Analytics |
| Content Delivery Network (CDN) | Traffic Distribution, Attack Mitigation |
| Rate Limiting Tools | Traffic Control, Bot Detection |
| Load Balancers | Traffic Distribution, SSL Termination |
| DDoS Protection Services | Real-time Analytics, Machine Learning |
| Intrusion Detection Systems (IDS) | Traffic Monitoring, Real-time Defense |
| Anti-DDoS Software | Traffic Scrubbing, Real-time Monitoring |
| VPN Services | Data Encryption, IP Masking |
| Analytics Tools | Custom Alerts, Traffic Monitoring |
| Server-Level Protection | IP Reputation, Rate-based Blocking |
Firewall Settings and Configurations
Firewalls serve as the gatekeepers of your network, and their configuration is paramount for robust DDoS defense.
The Role of Firewalls in DDoS Defense
Firewalls scrutinize incoming and outgoing traffic, filtering out malicious or suspicious packets. This makes them a cornerstone in your DDoS defense strategy.
Types of Firewalls
Network-Based Firewalls
These hardware devices guard your network’s perimeter. They’re particularly effective against volumetric attacks where the goal is to overwhelm network bandwidth.
Host-Based Firewalls
Installed on individual servers, these software solutions offer granular control. They excel in defending against application-layer attacks targeting specific services.
Key Firewall Settings
IP Blocking
Blocking known malicious IPs prevents them from flooding your network with requests, mitigating the risk of a targeted attack.
Rate Limiting
By limiting the number of requests from a single IP, you can thwart attackers attempting to exhaust your system resources.
Port Security
Disabling unused ports reduces the attack surface, making it harder for attackers to exploit vulnerabilities.
Packet Filtering
This mechanism inspects data packets for known attack patterns. It’s effective against protocol attacks that exploit weaknesses in network protocols.
Advanced Configurations
Geo-Blocking
By restricting access based on geographic location, you can prevent large-scale attacks originating from specific regions.
Maintain a List of Trusted IP Addresses
Maintain a list to ensure that during an attack, legitimate traffic isn’t mistakenly blocked.
Block Known Bad IP Addresses
Be sure that known malicious IPs are blocked, adding another layer of defense against known threats.
There are services out there that maintain lists of known bad IP addresses. One of my personal favorites is AbuseIPDB. For a small monthly fee, one can find out what IP addresses are bad, why, and a confidence level. You also have the ability to find this through an API, making it possible to automate the blocking process.
By meticulously configuring these firewall settings, you not only fortify your network but also make it agile in adapting to evolving DDoS attack strategies.
Intrusion Detection Systems: Your Silent Guardians
Intrusion Detection Systems serve as your network’s watchful eyes, silently monitoring traffic for any signs of malicious activity.
What is an Intrusion Detection System?
An IDS is a device or software application that scans your network and system activities for security threats or violations.
Types of IDS
Network Intrusion Detection Systems (NIDS)
NIDS monitor the traffic between devices on your network. They’re particularly effective against attacks that aim to exploit network vulnerabilities.
Host Intrusion Detection Systems (HIDS)
HIDS are installed on individual hosts or devices in your network. They excel in detecting attacks that target system-level vulnerabilities.
How IDS Works
Signature-Based Detection
Signature-based detection uses predefined signatures of known attacks to identify malicious activity. It’s quick but may not detect new, unknown attacks.
Anomaly-Based Detection
This approach establishes a baseline of typical behavior and flags deviations. It’s effective against zero-day attacks but may produce false positives.
Policy-Based Detection
Here, the IDS flags violations of corporate security policies, adding an extra layer of protection.
IDS in DDoS Defense
Real-Time Monitoring
IDS provide real-time analysis of network packets, allowing for immediate detection of DDoS attacks.
Alert Mechanisms
Upon detecting an attack, IDS can send alerts or even initiate predefined defense mechanisms.
Data Logging
IDS keep detailed logs of security incidents, aiding in post-attack analysis and future prevention strategies.
By understanding and deploying Intrusion Detection Systems, you add a robust layer to your DDoS defense strategy, making your network more resilient against various types of attacks.
Real-Life Stories and Tips to Defend against a DDoS Attack
In a past life, I was a cybersecurity analyst/programmer. I had worked with IT and engineering to configure software whereby when a bad IP was detected by our Datadog monitoring system, a program would detect this and block the IP (there are much better ways of doing this through AWS but we hadn’t implemented it yet).
One day I noticed a blast of over 30,000 requests in a 30 minute period from a location in Belgium. Not only don’t we do business there, but none of the requests made sense. We were being scanned. Our system worked. Within the first 15 seconds, the IP was blocked. All they were getting was a 404.
Still not the best solution. A better solution which we were working on was to create a firewall at the internet gateway and block everything there. Or use a tool like Snort in the network to catch and stop such attacks.
Act Now to Protect Your Business from DDoS Threats: Essential Takeaways
DDoS attacks are not just a big-business problem; they’re a universal threat that can cripple any organization, big or small. As our hypothetical case study on Acme Corp illustrates, the consequences of inadequate cybersecurity can be devastating.
Your Next Steps
Don’t wait for an attack to happen to take action. Start implementing these strategies today to safeguard your business.
Engage with Us
Found this article helpful? Share it with your network to help others defend against DDoS attacks. Have questions or insights? Drop a comment below. Your engagement helps us create better content and fosters a community of like-minded professionals.
Questions? We Have Answers.
Get answers to a list of the most Frequently Asked Questions.

Experienced cybersecurity analyst, software engineer, patent attorney, worked with Linux, Windows, AWS, lots of security tools. Hope to help people do the right things and do the things right!